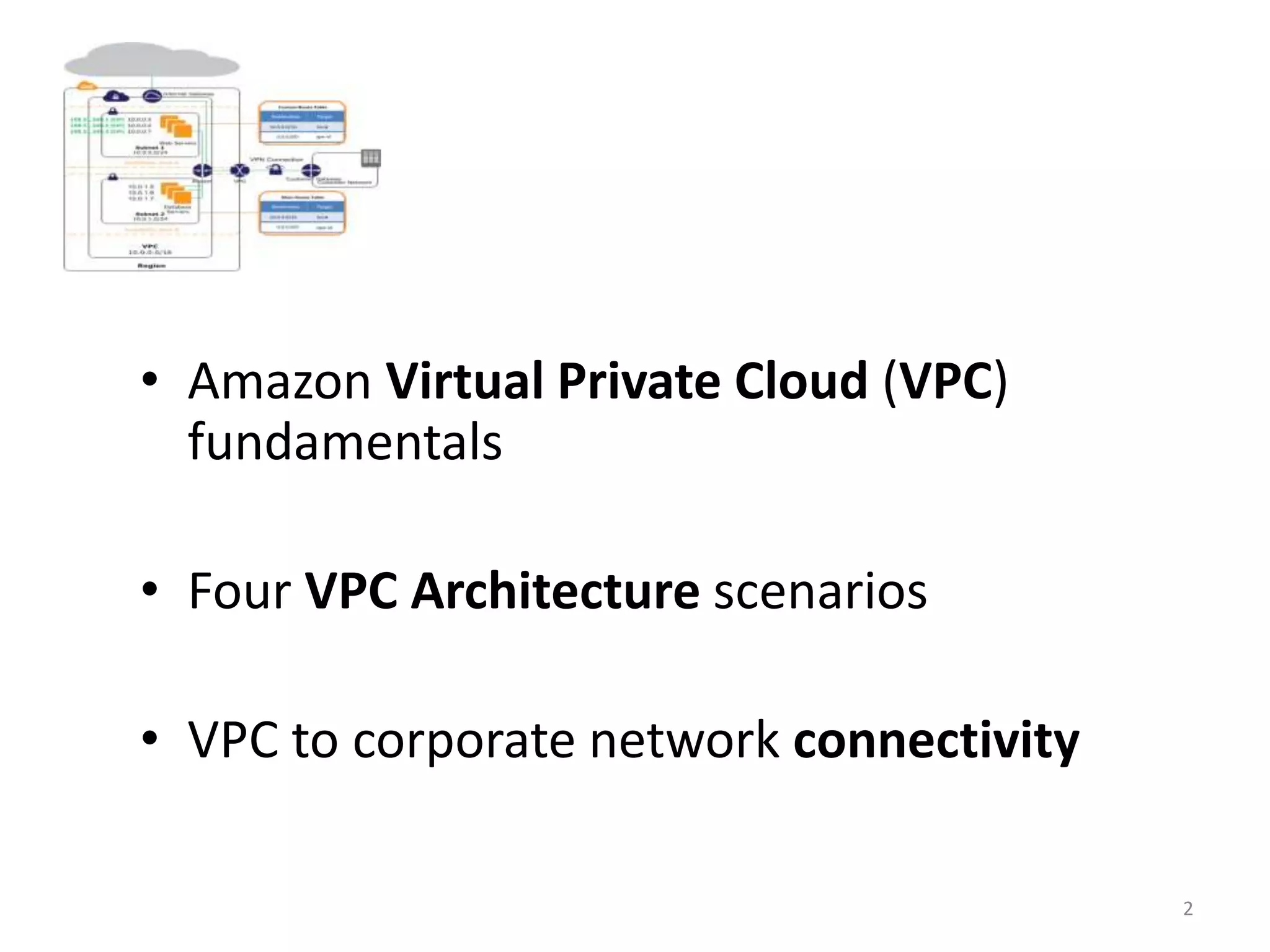
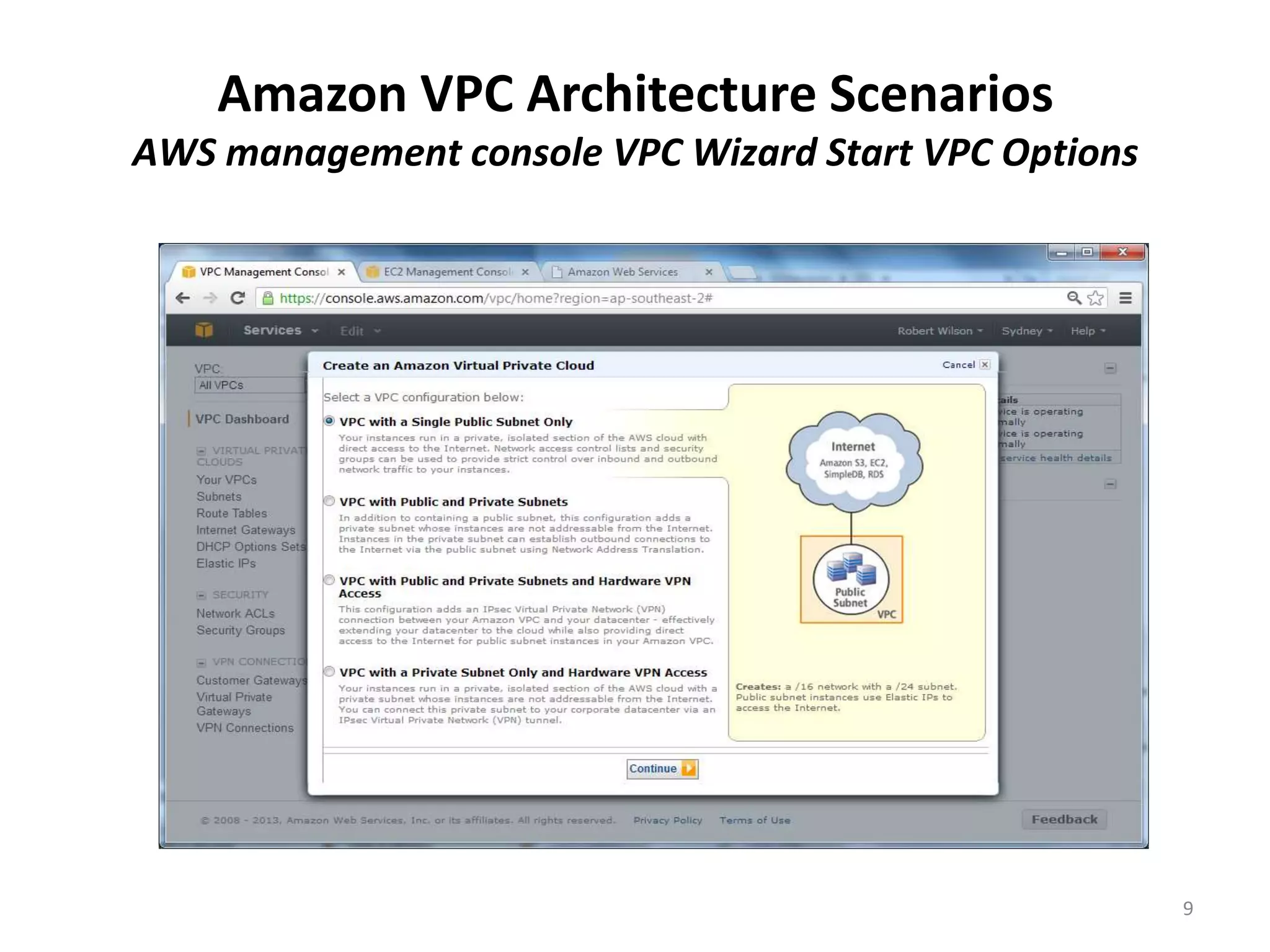
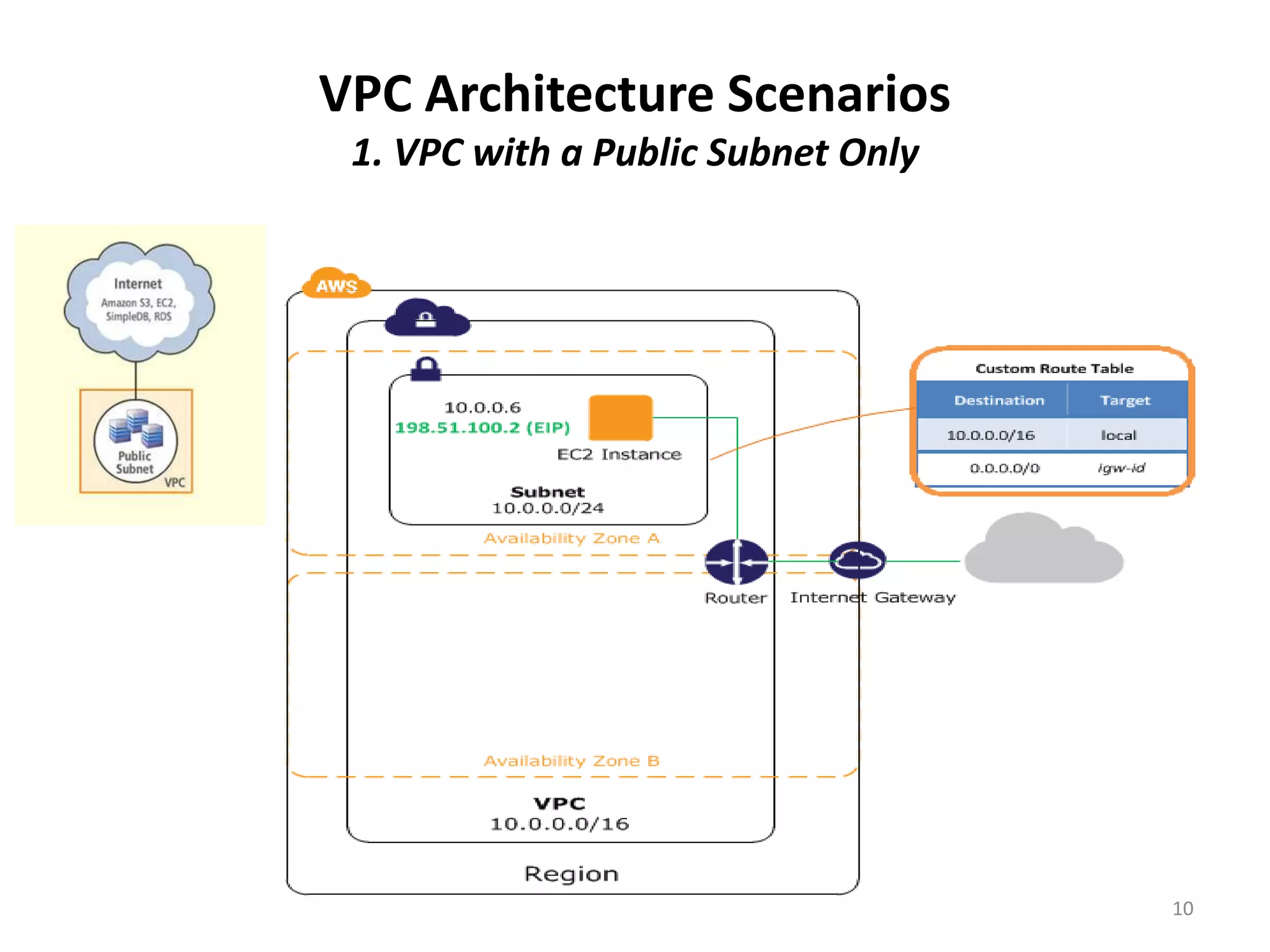
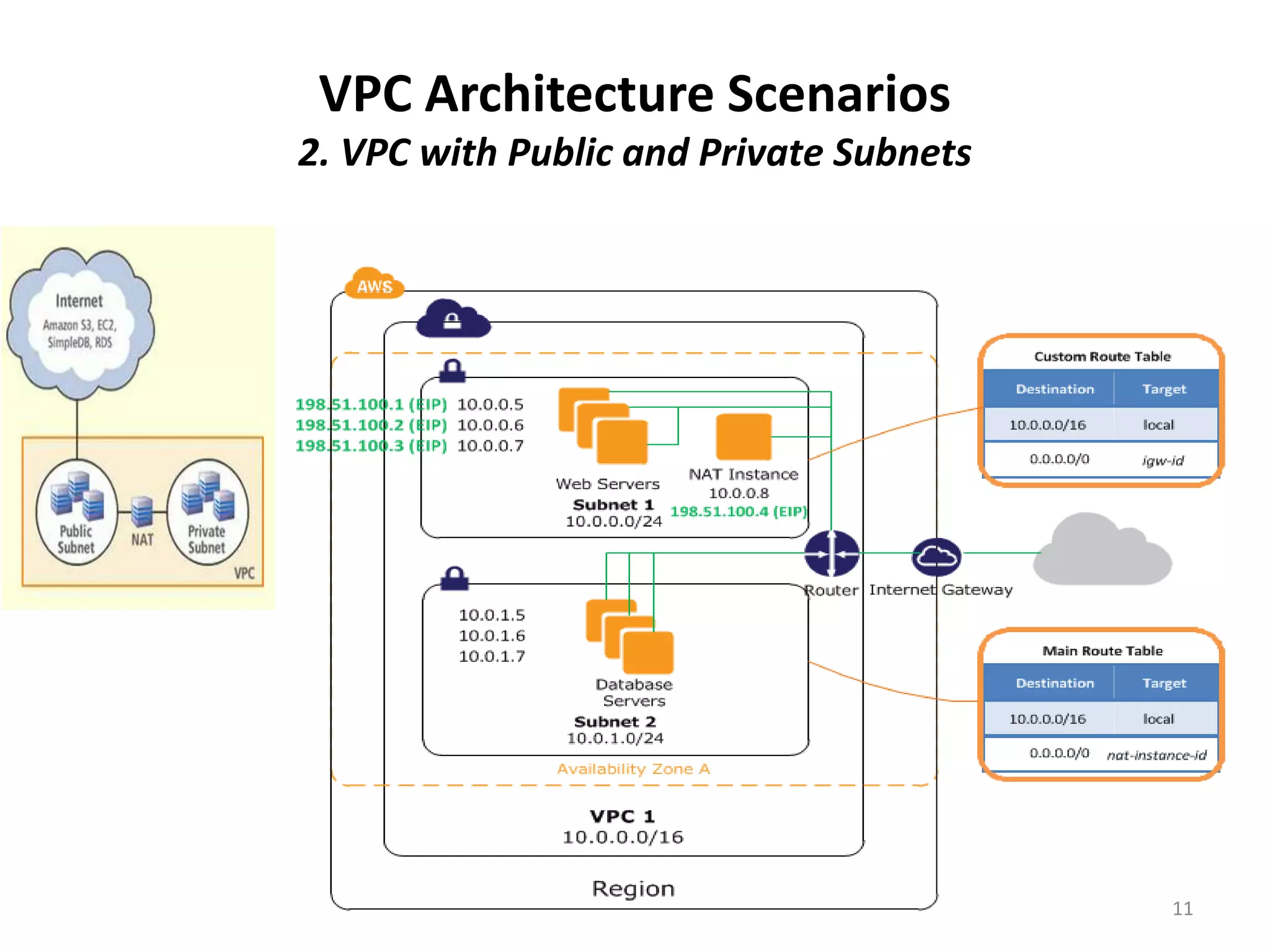
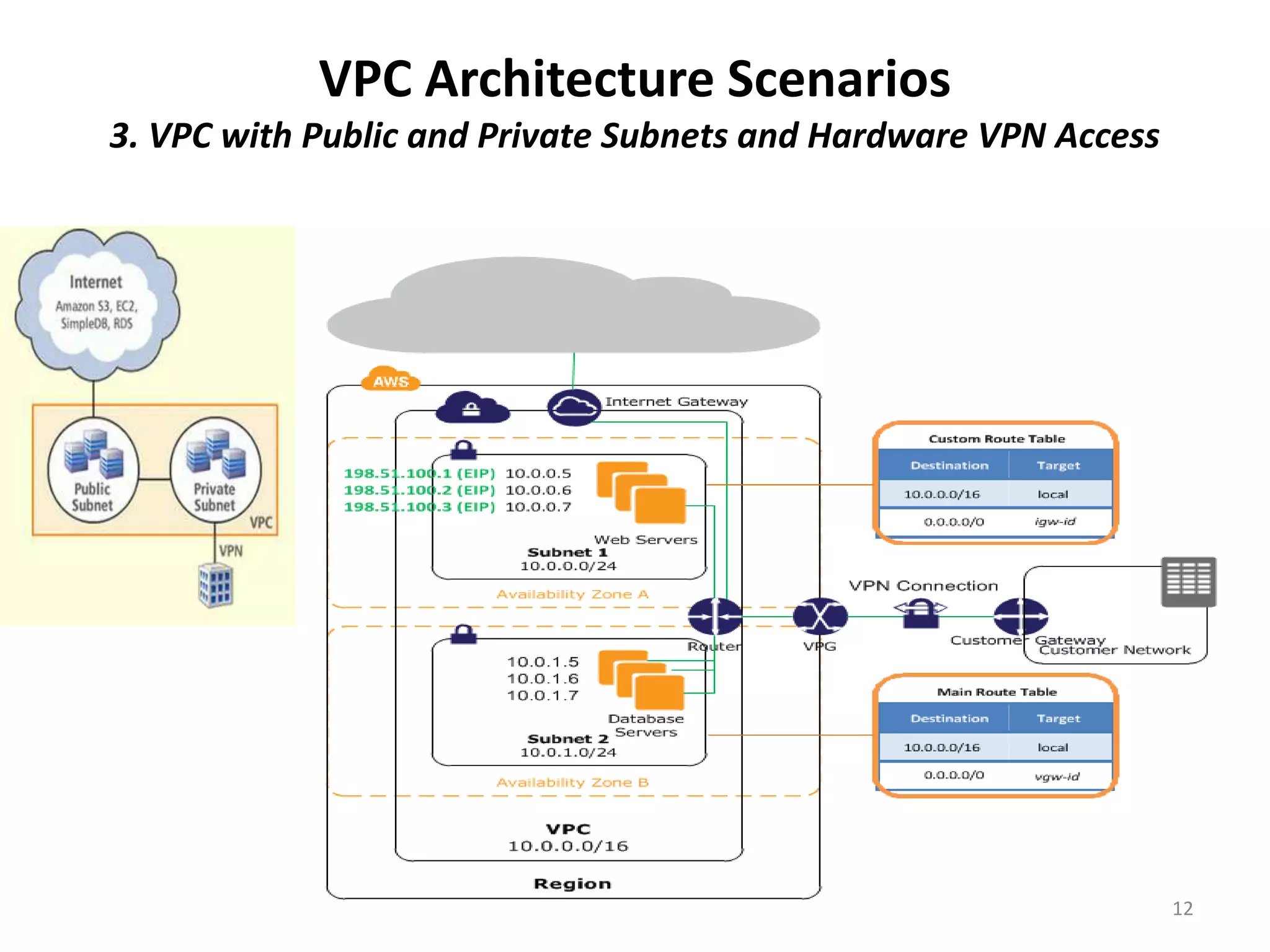
Amazon Virtual Private Cloud (VPC) allows users to create isolated virtual networks within AWS. The document discusses VPC fundamentals like subnets and security and provides examples of four common VPC architecture scenarios including VPC with public/private subnets and connecting VPC to an on-premise network with hardware VPN. It also outlines options for connecting a corporate network to a VPC like Direct Connect, VPN, and software VPN using EC2 instances.