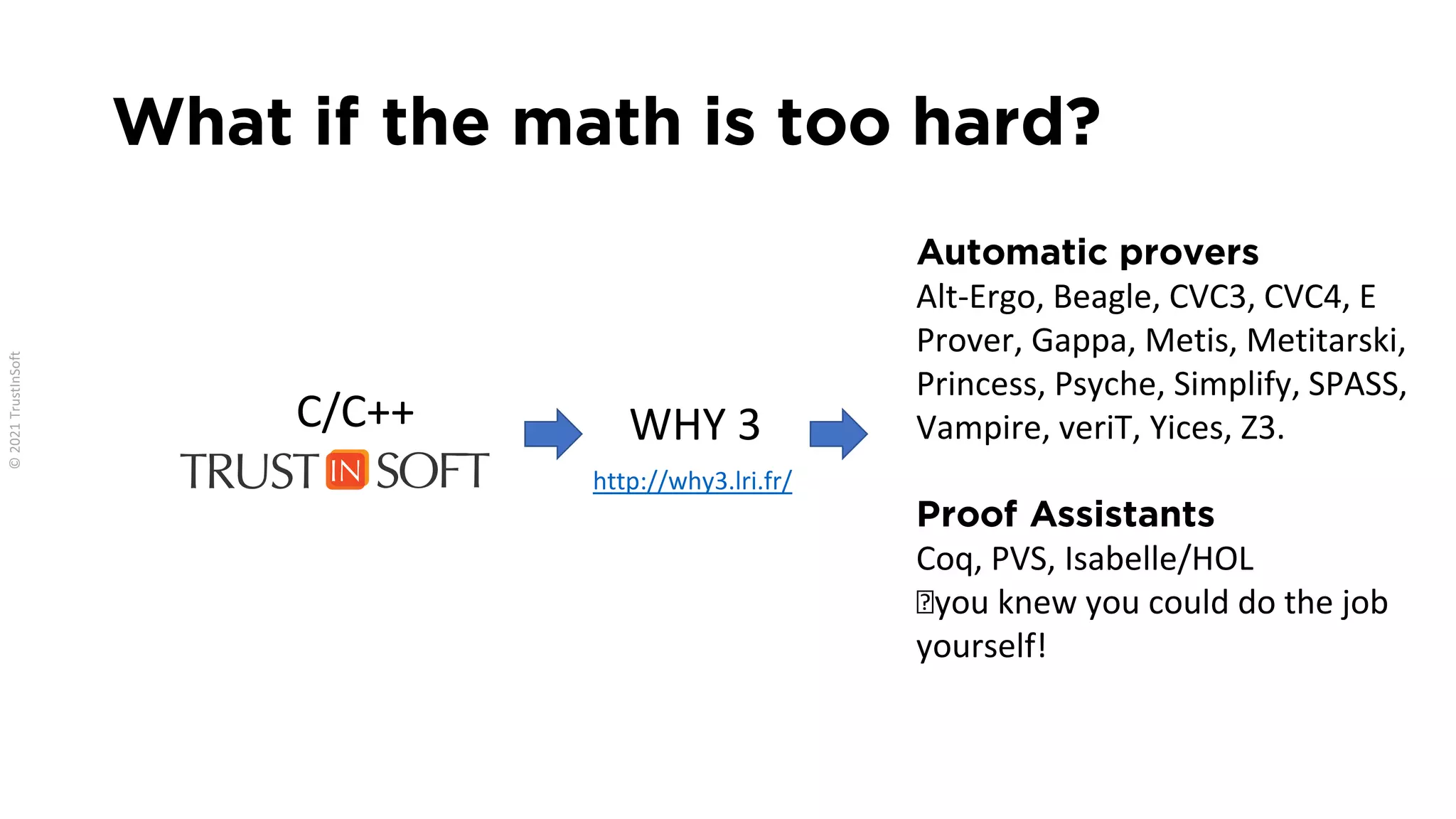
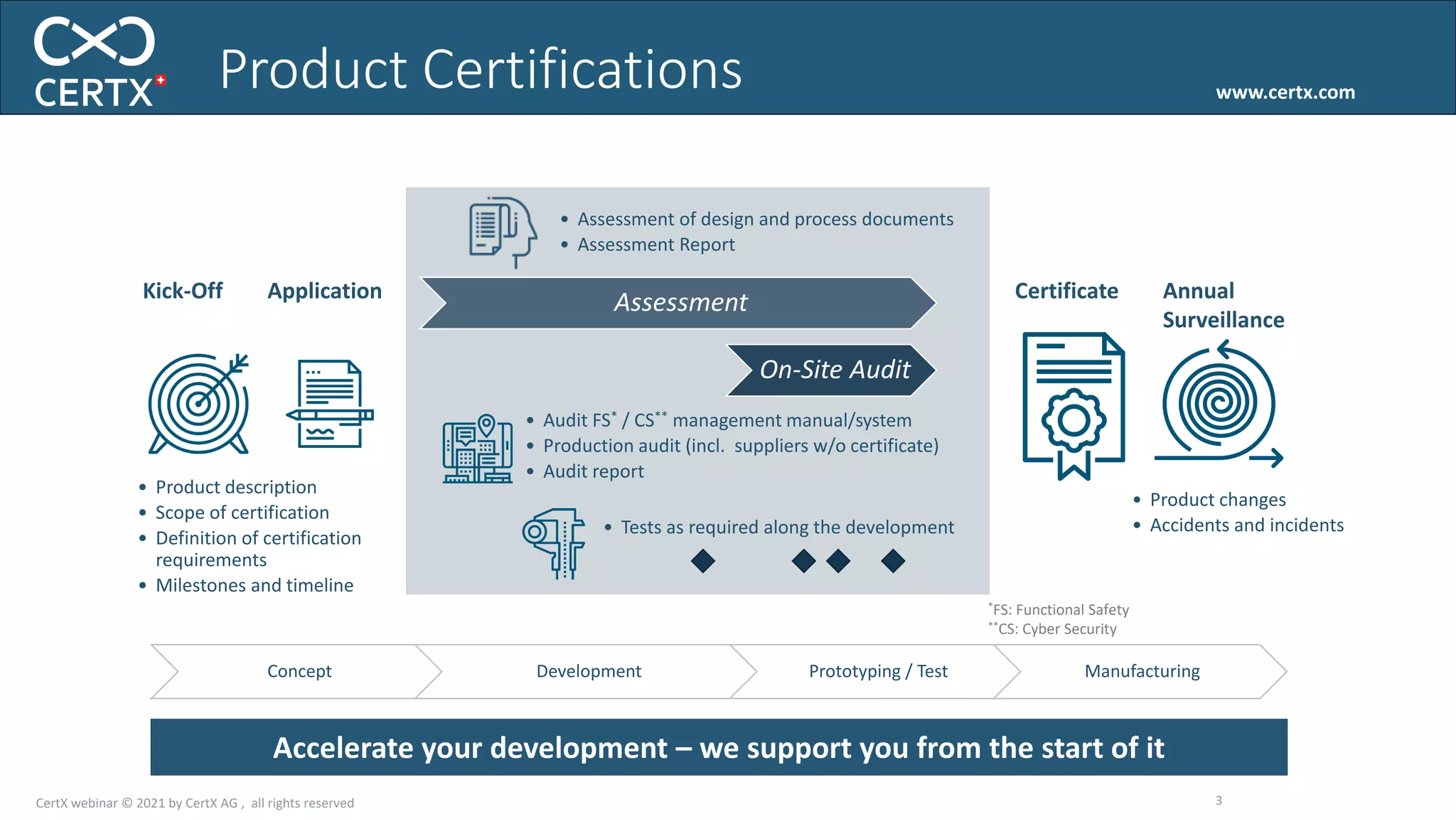
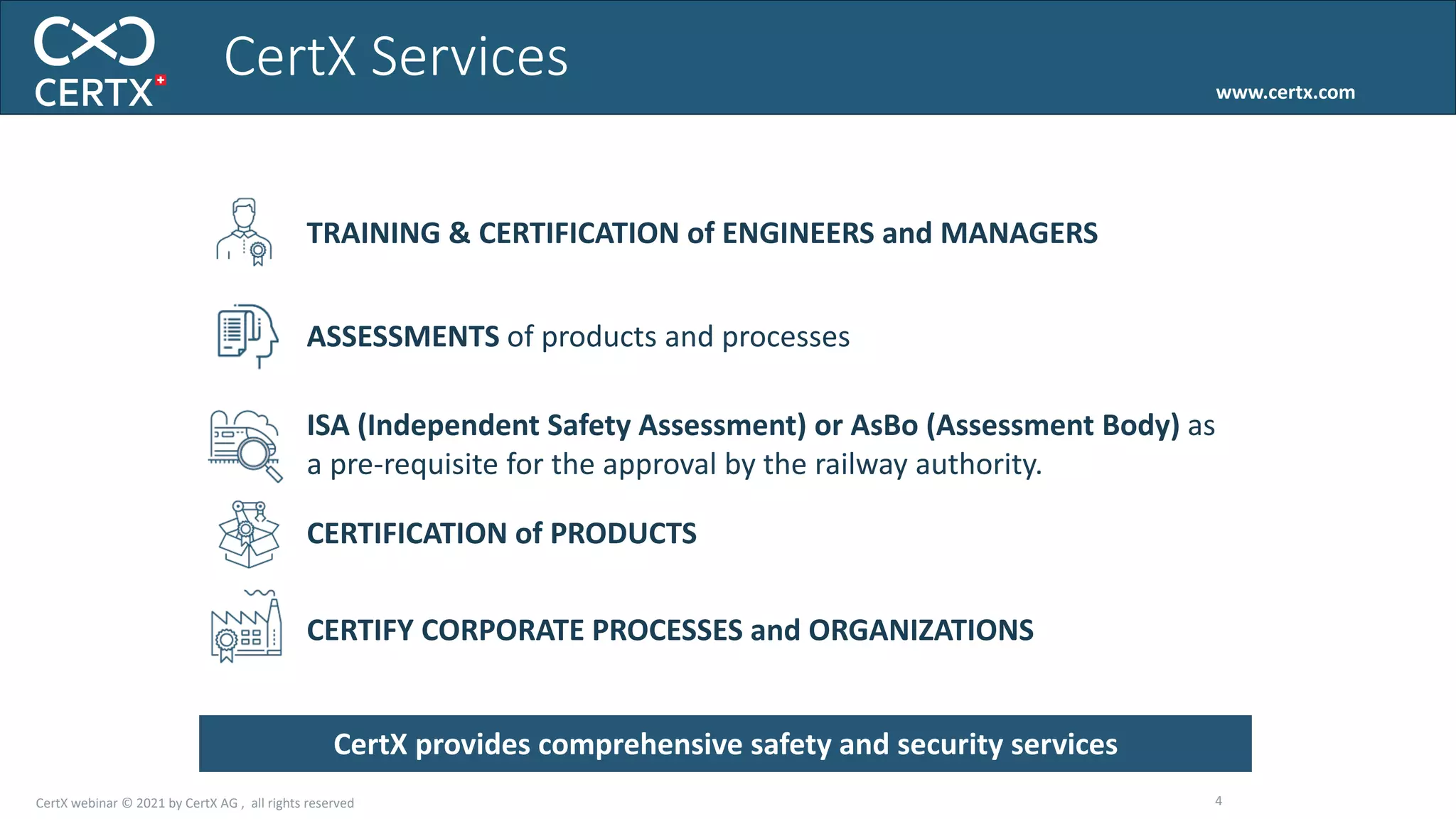
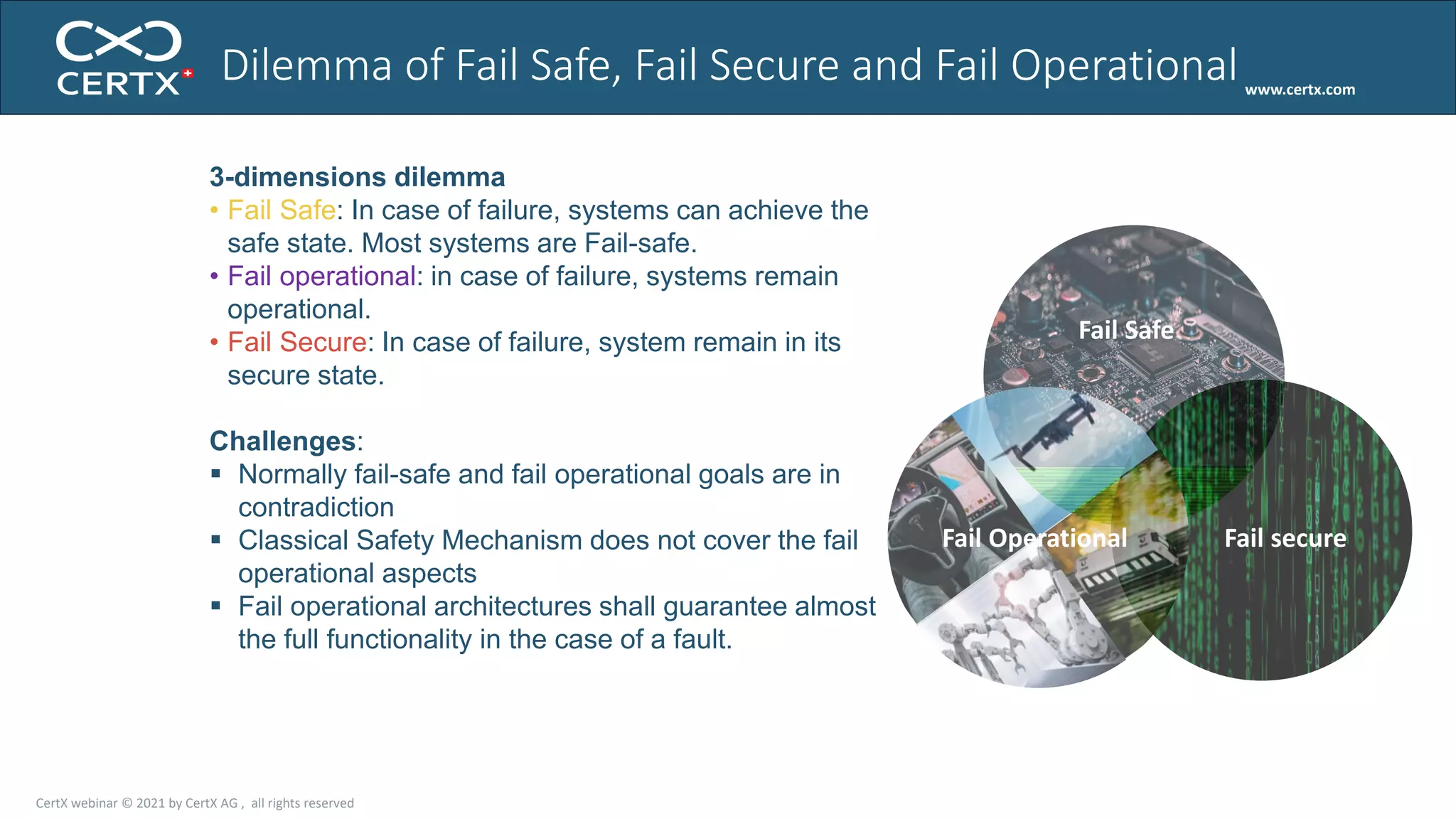
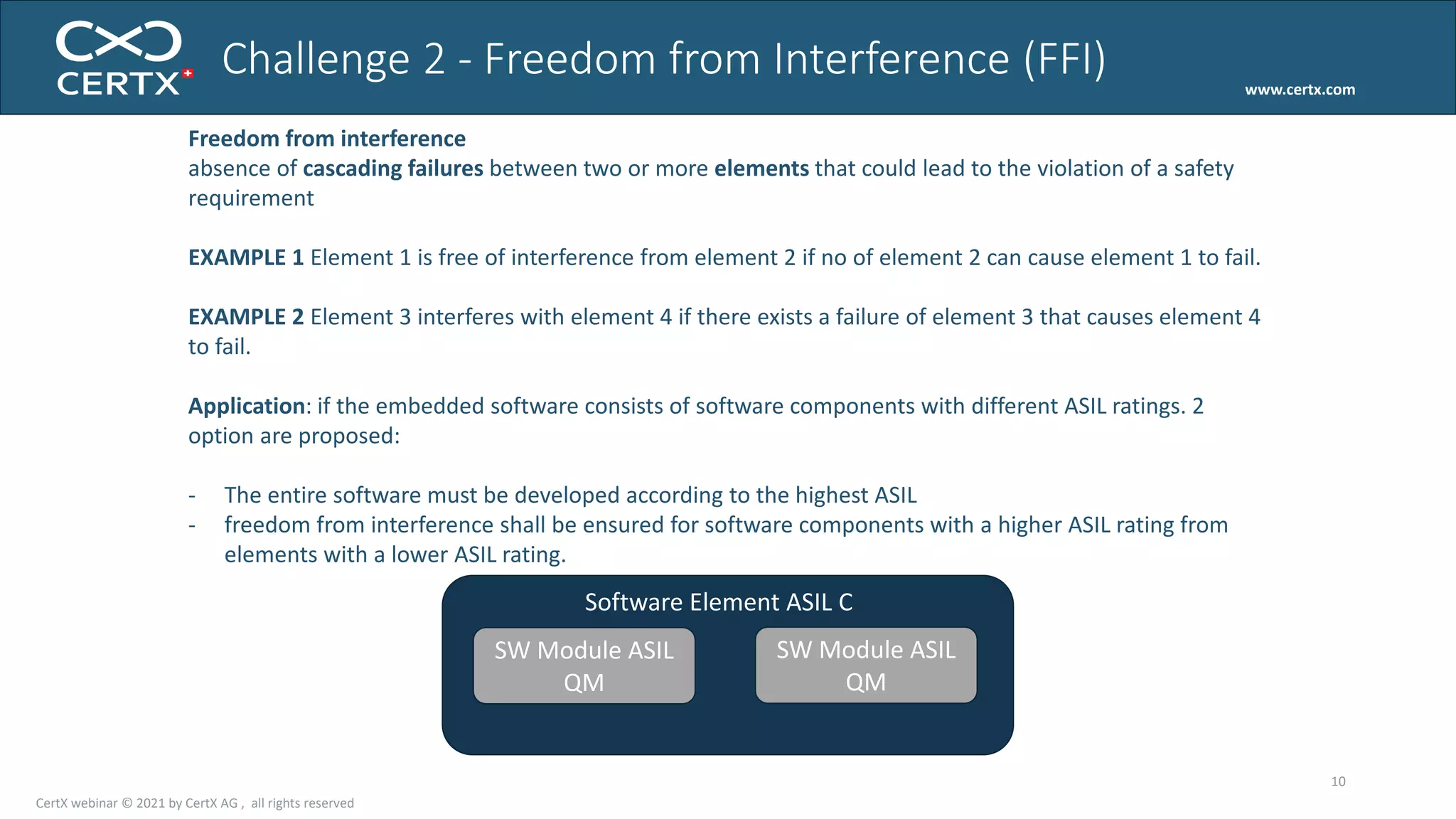
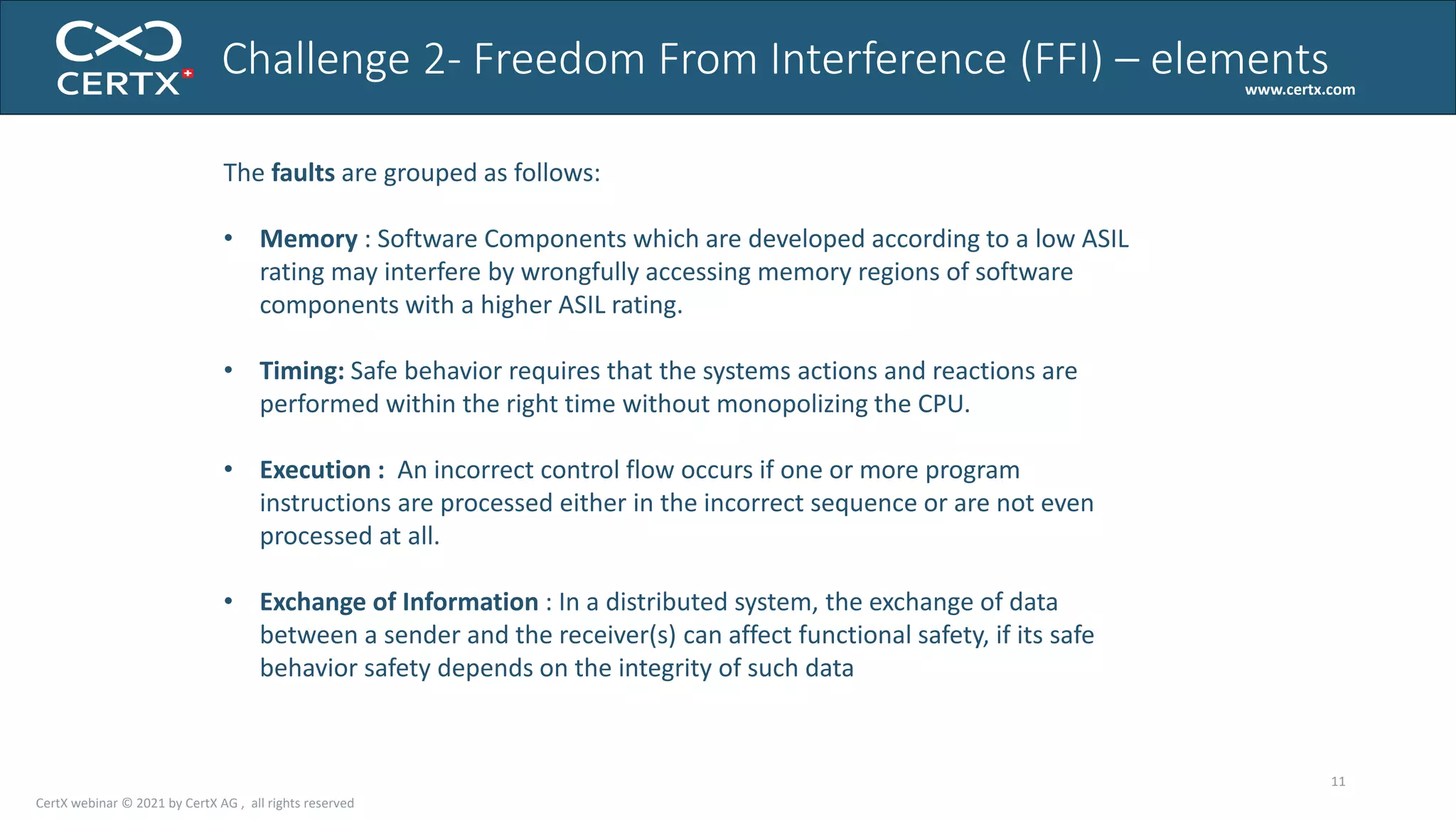
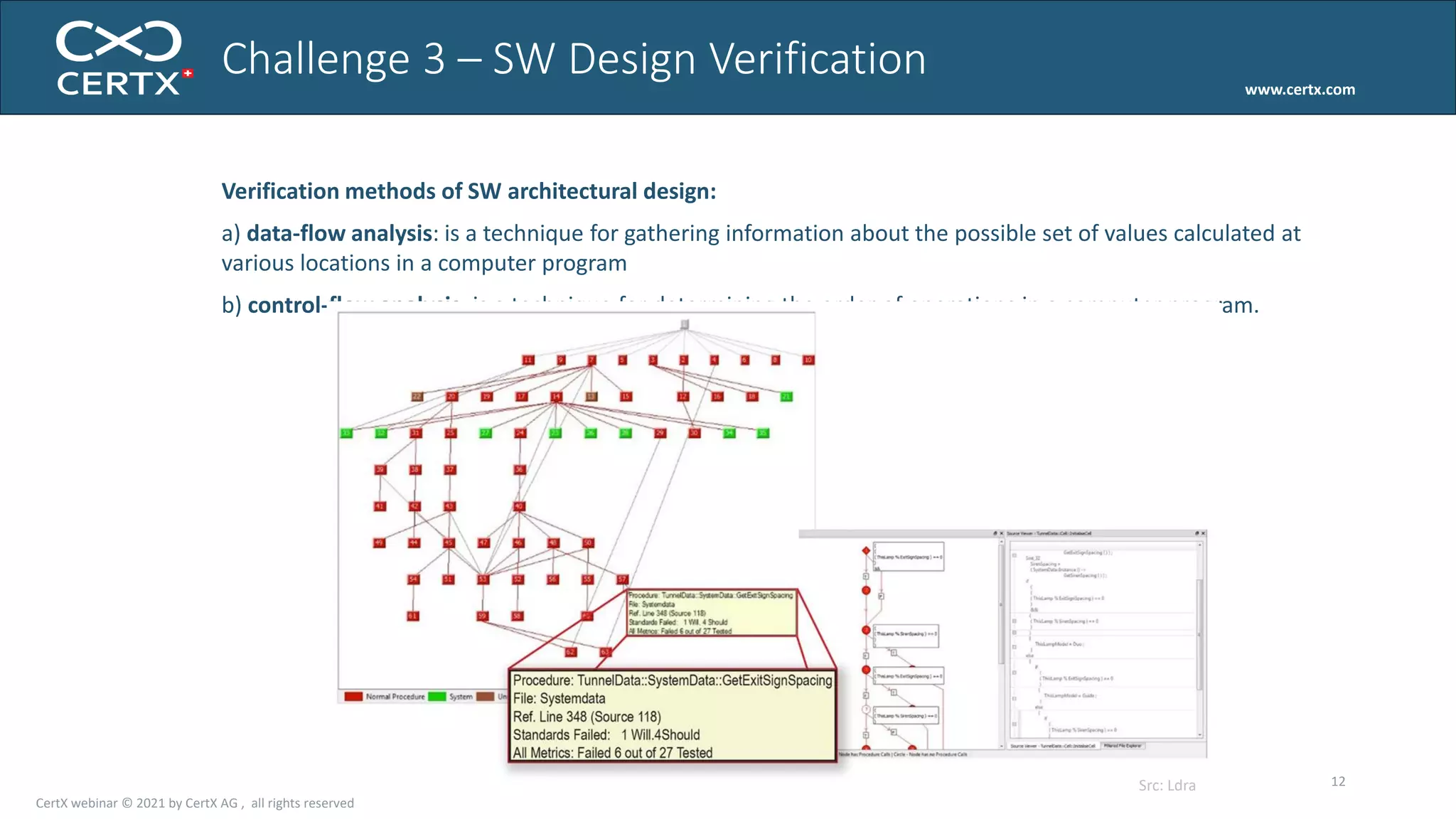
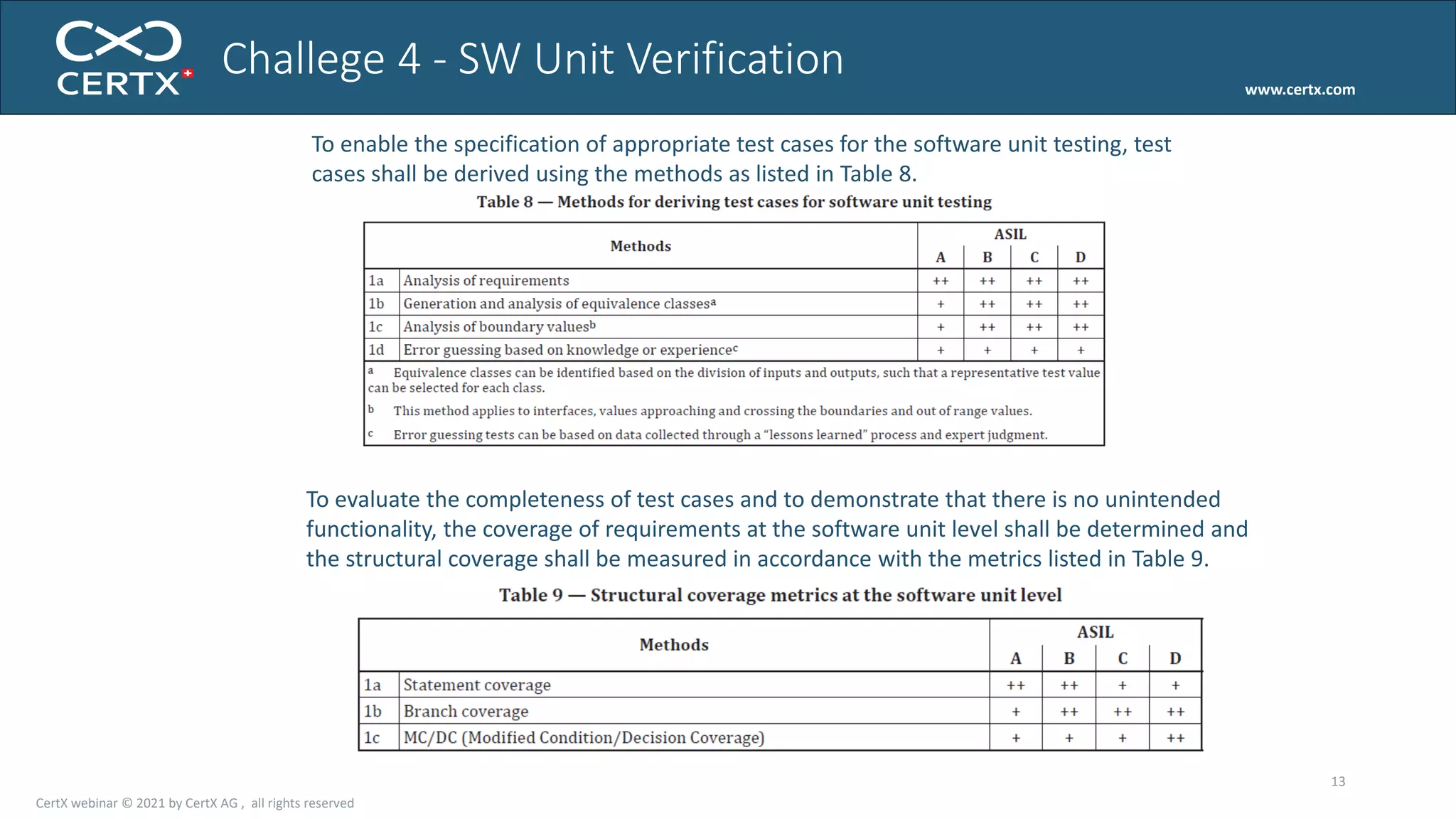
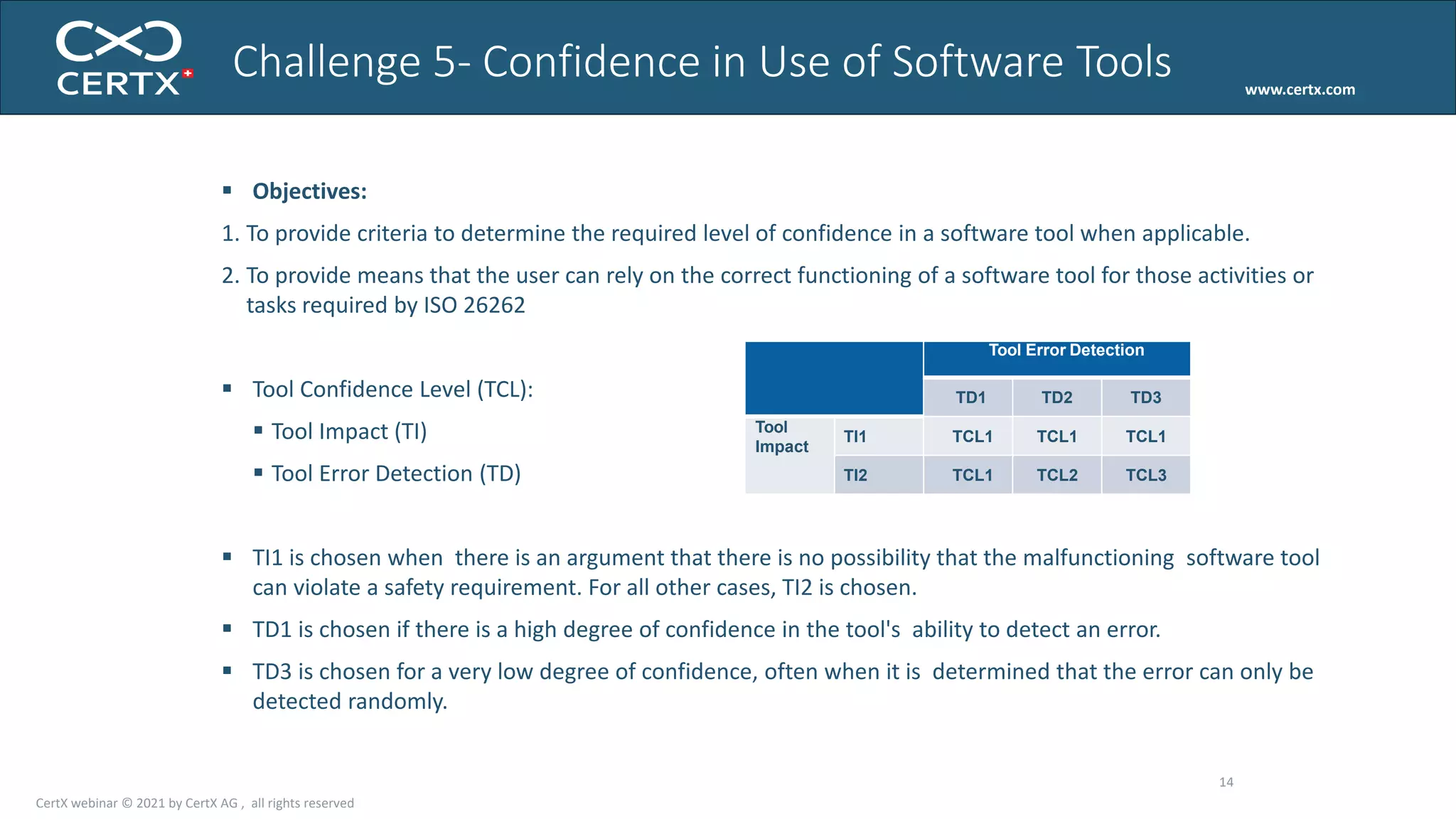
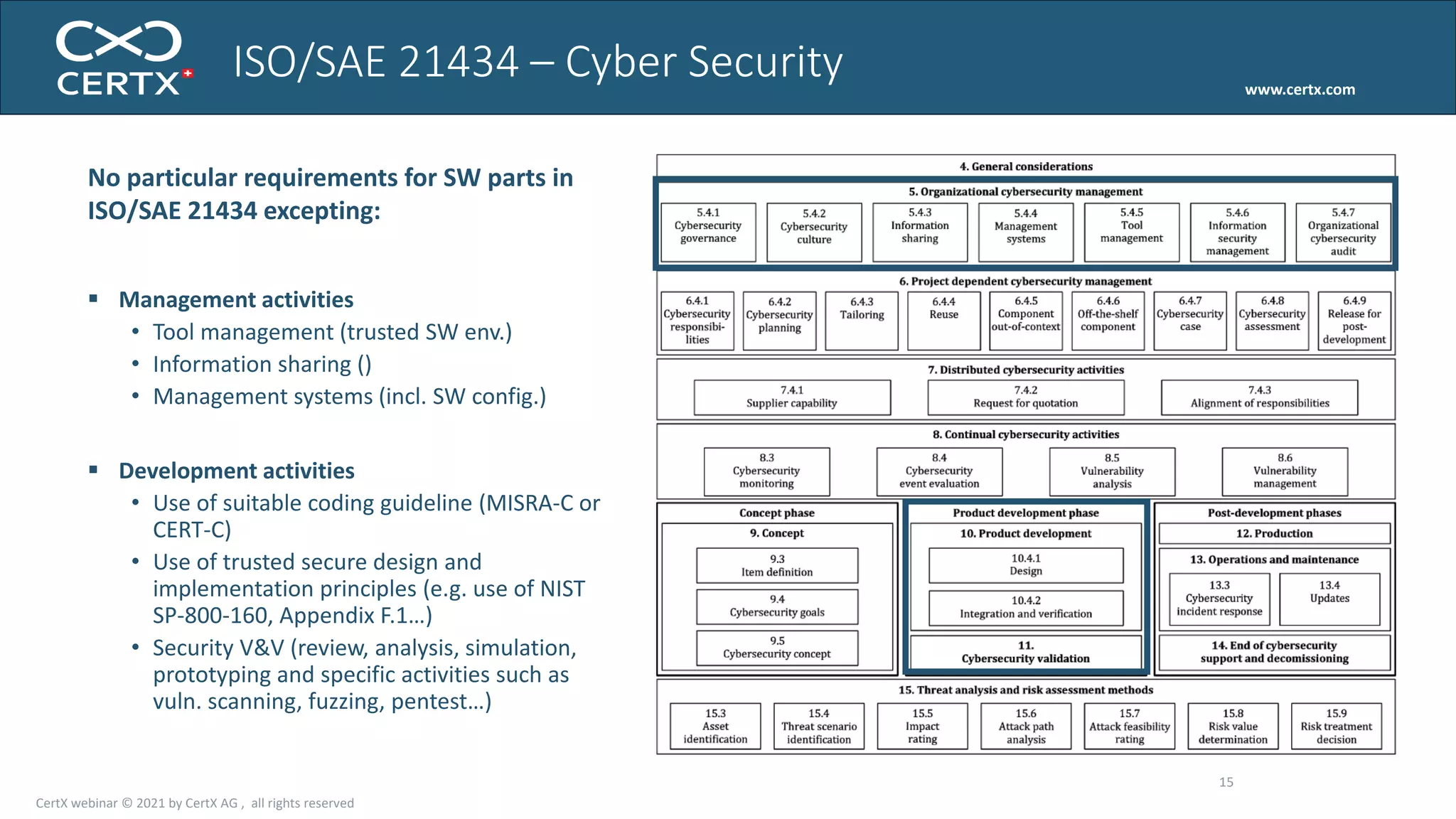
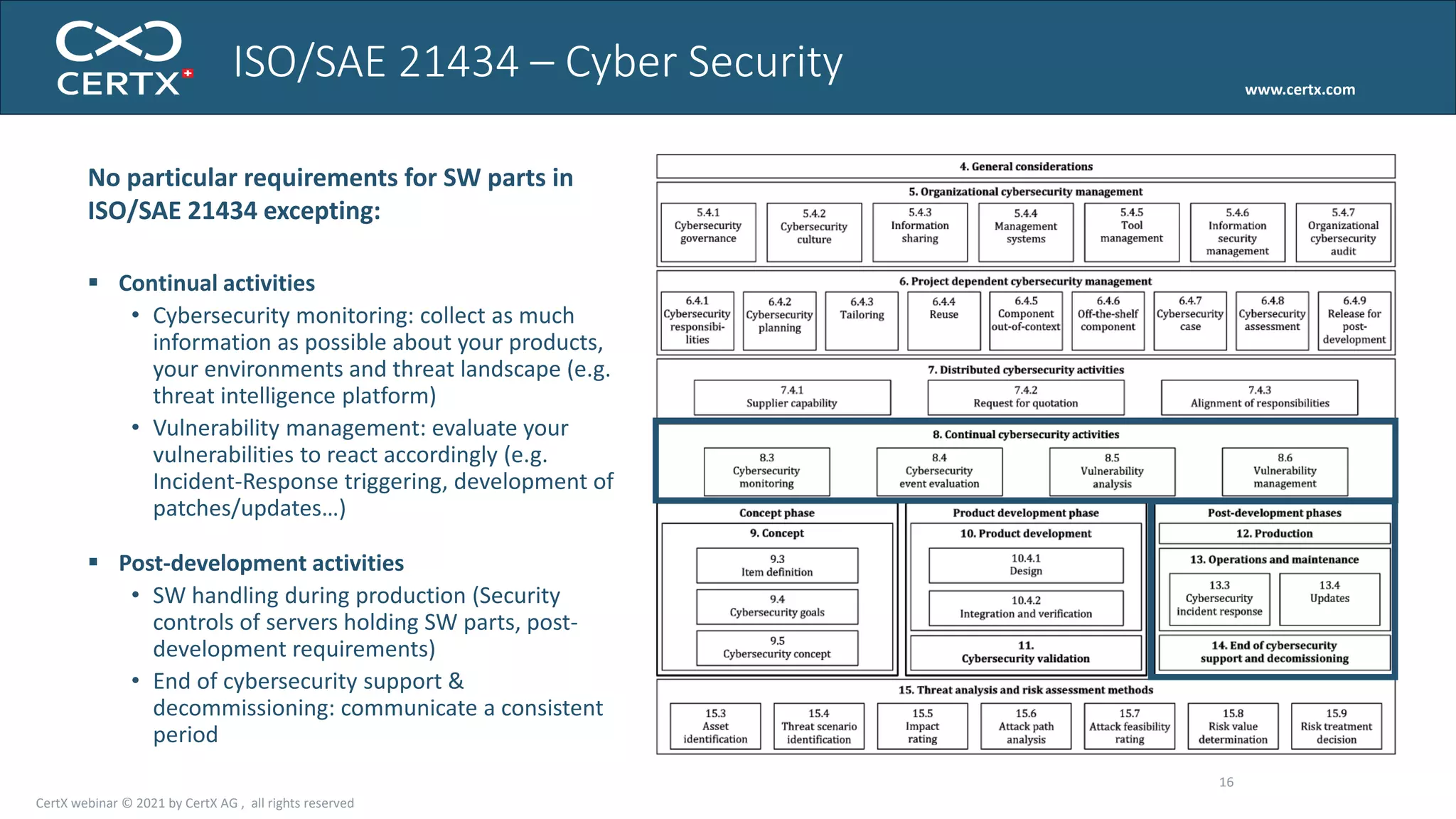
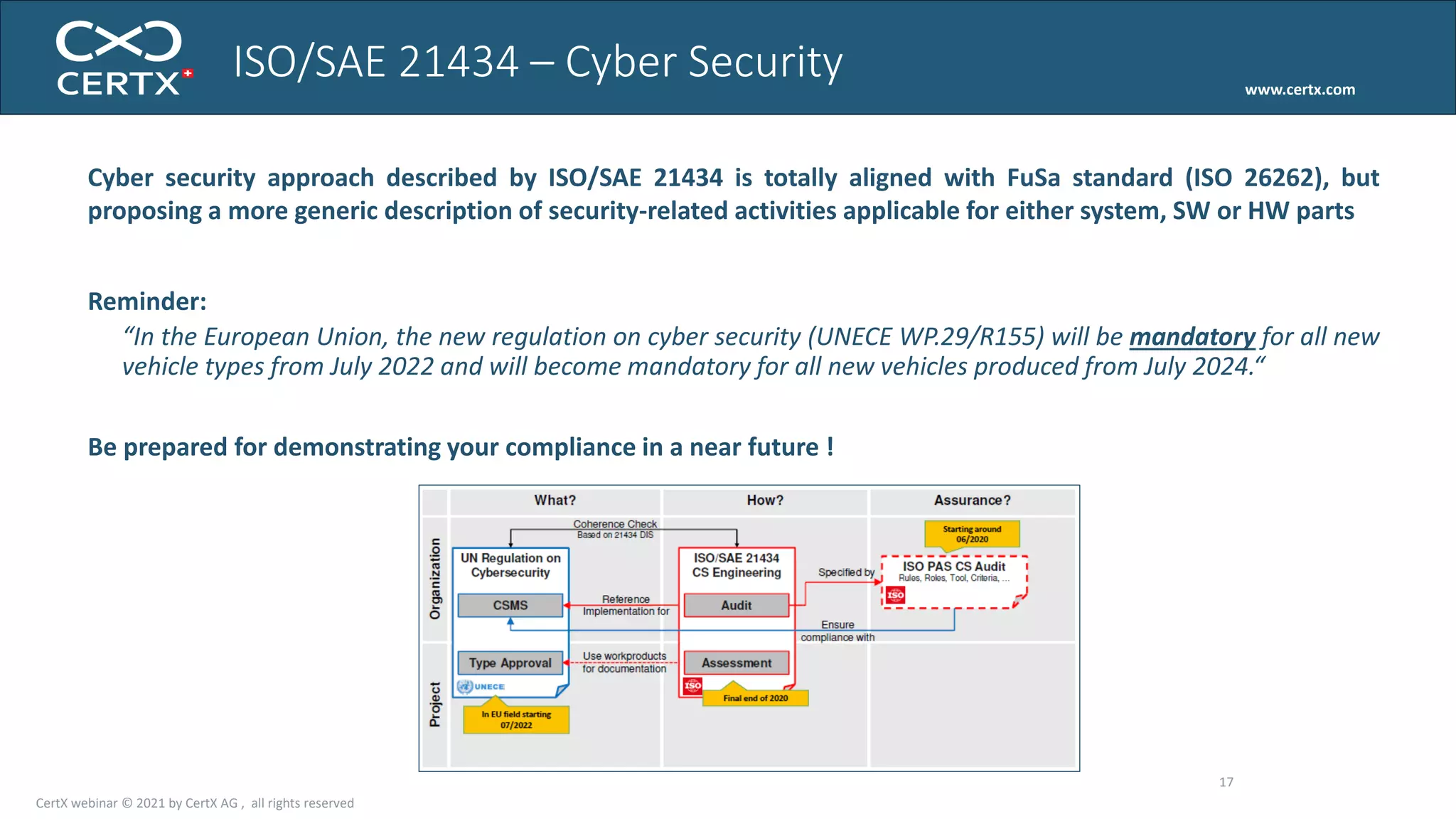
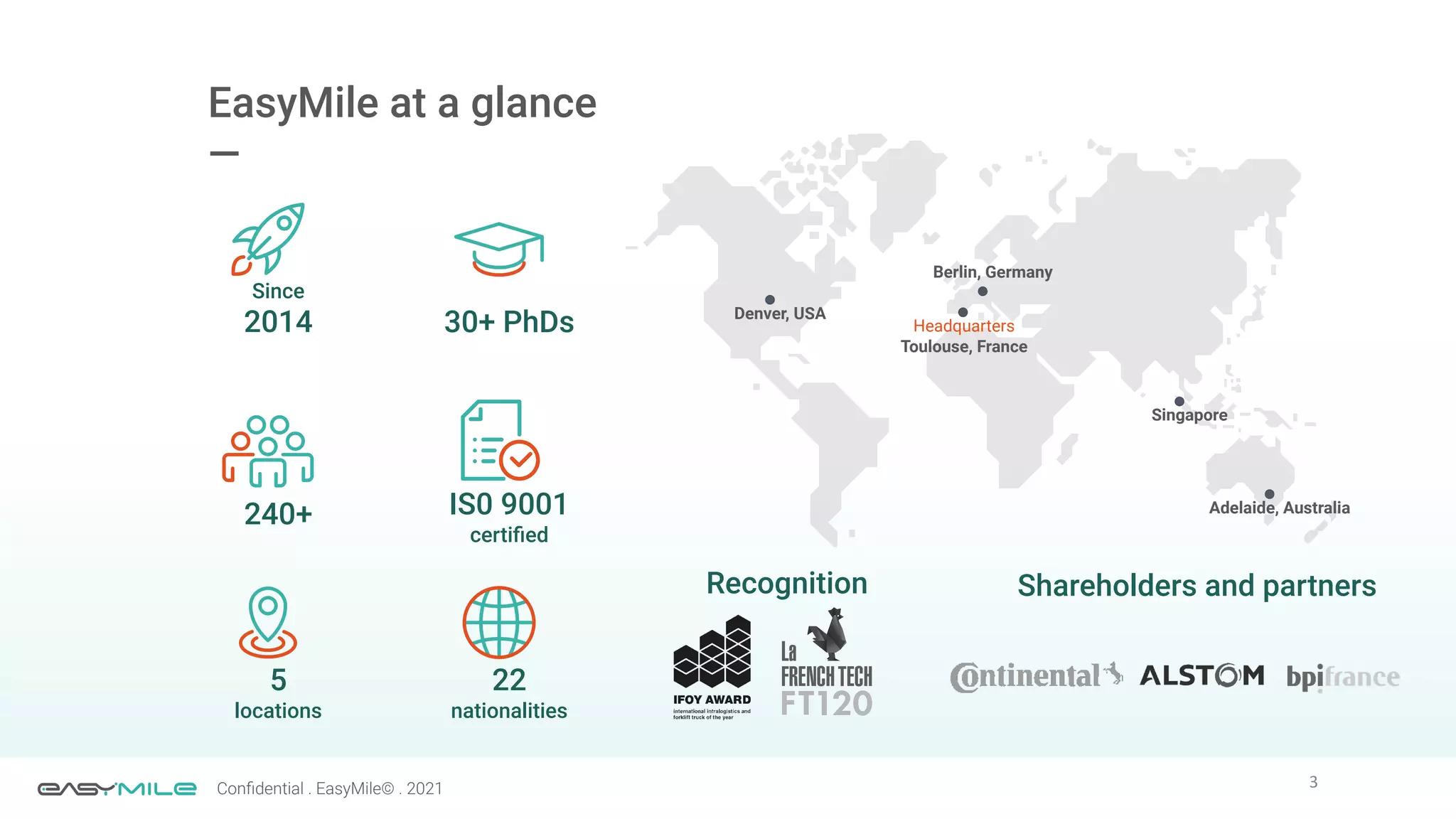
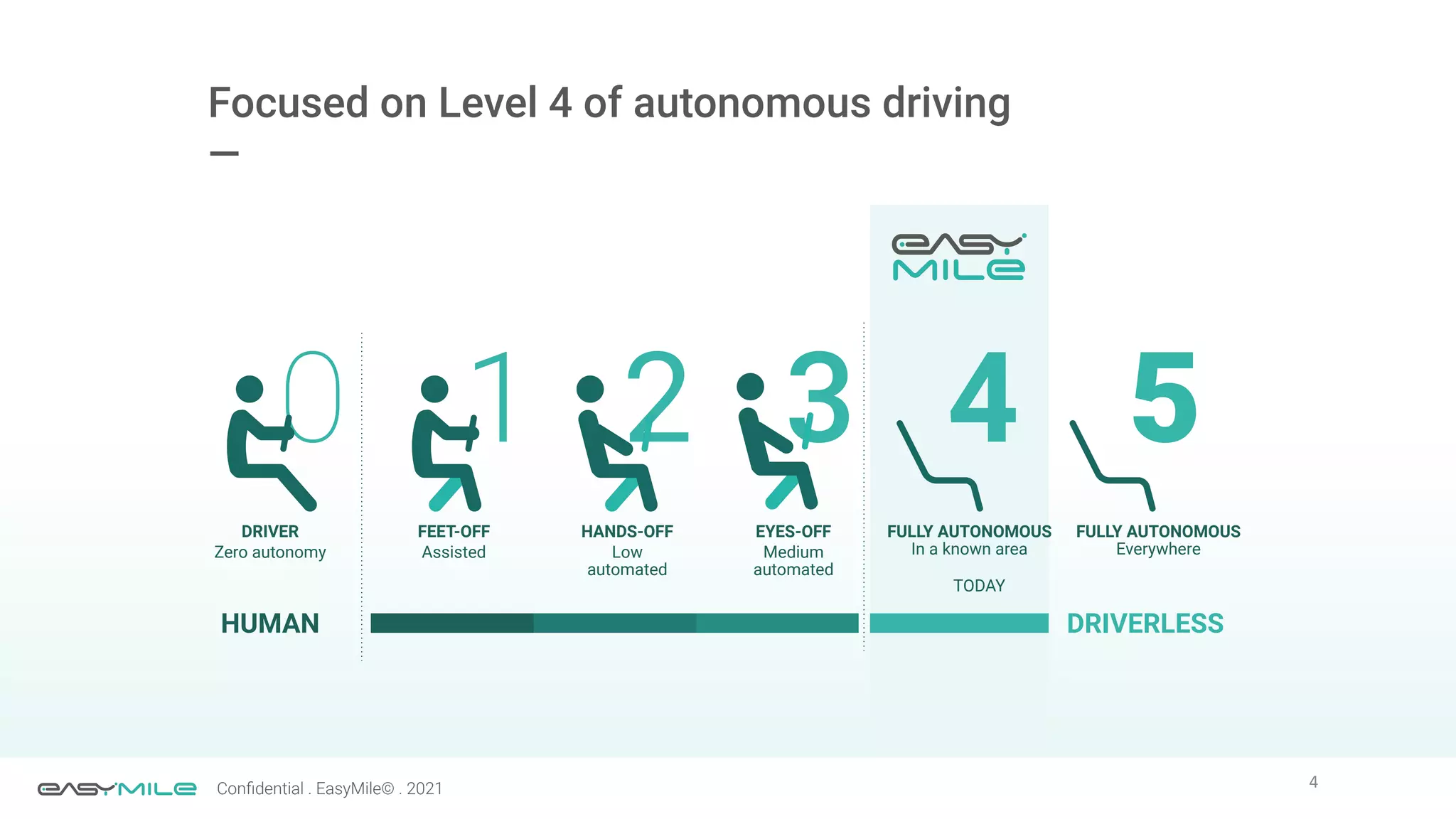
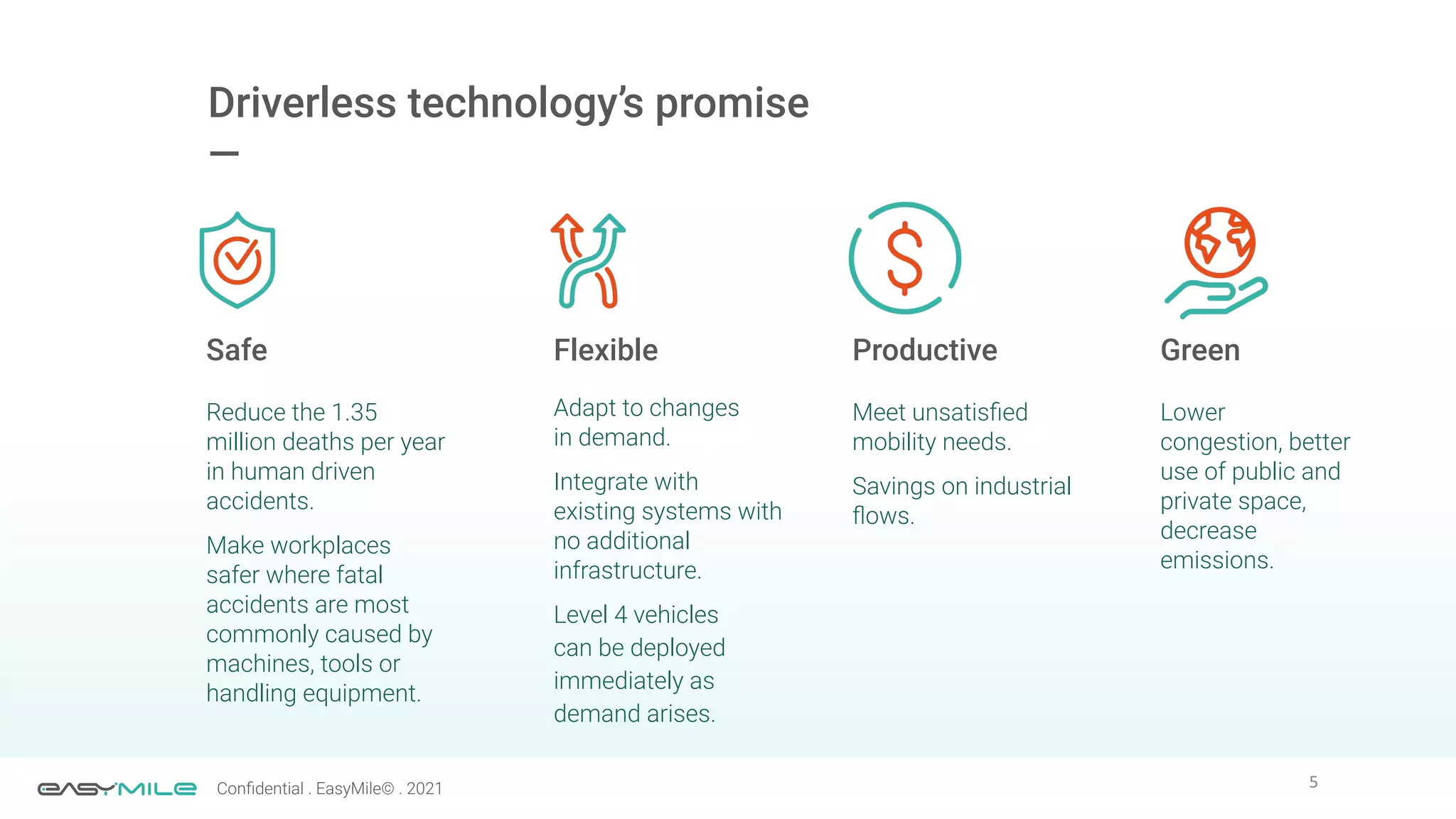
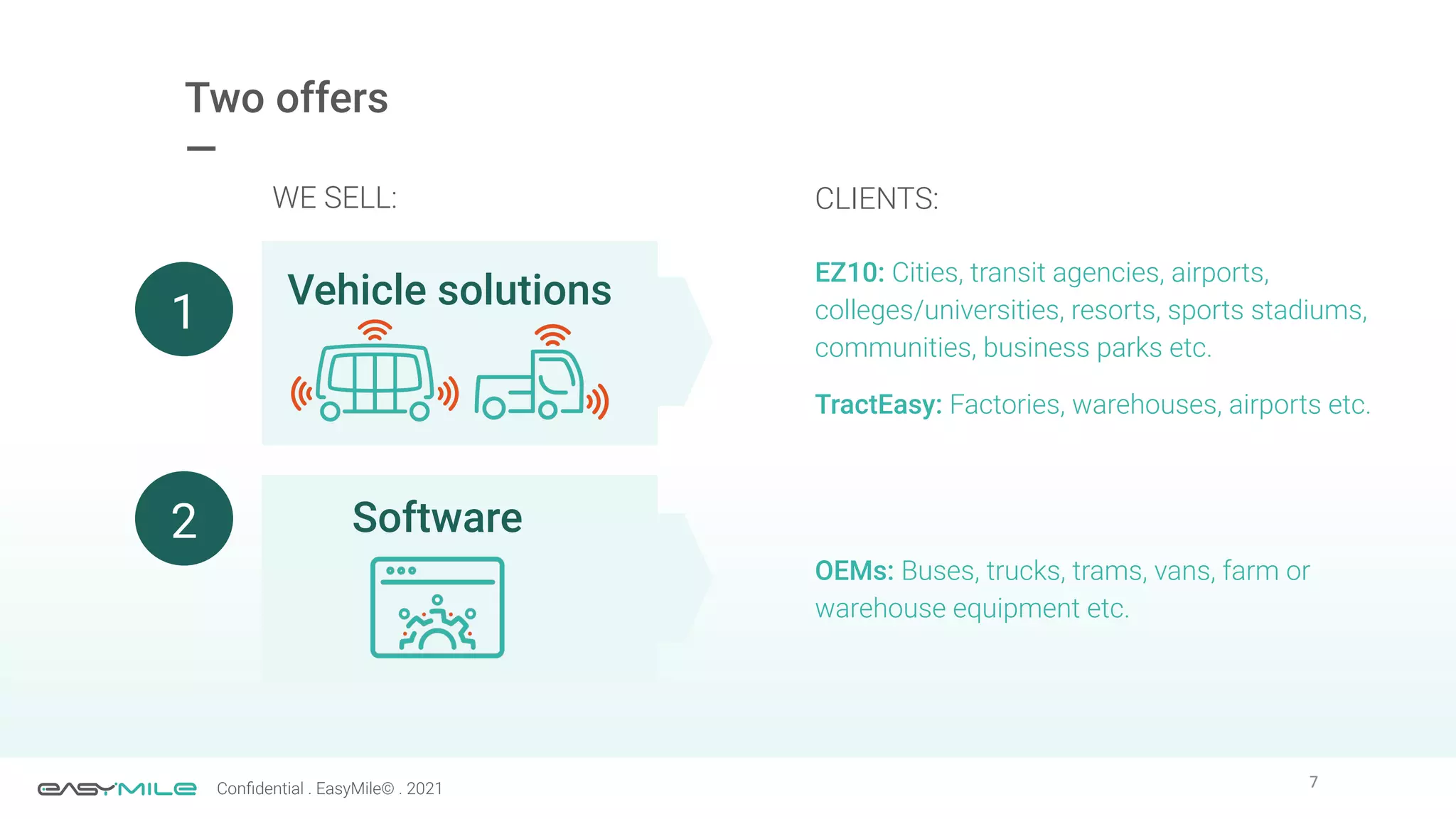
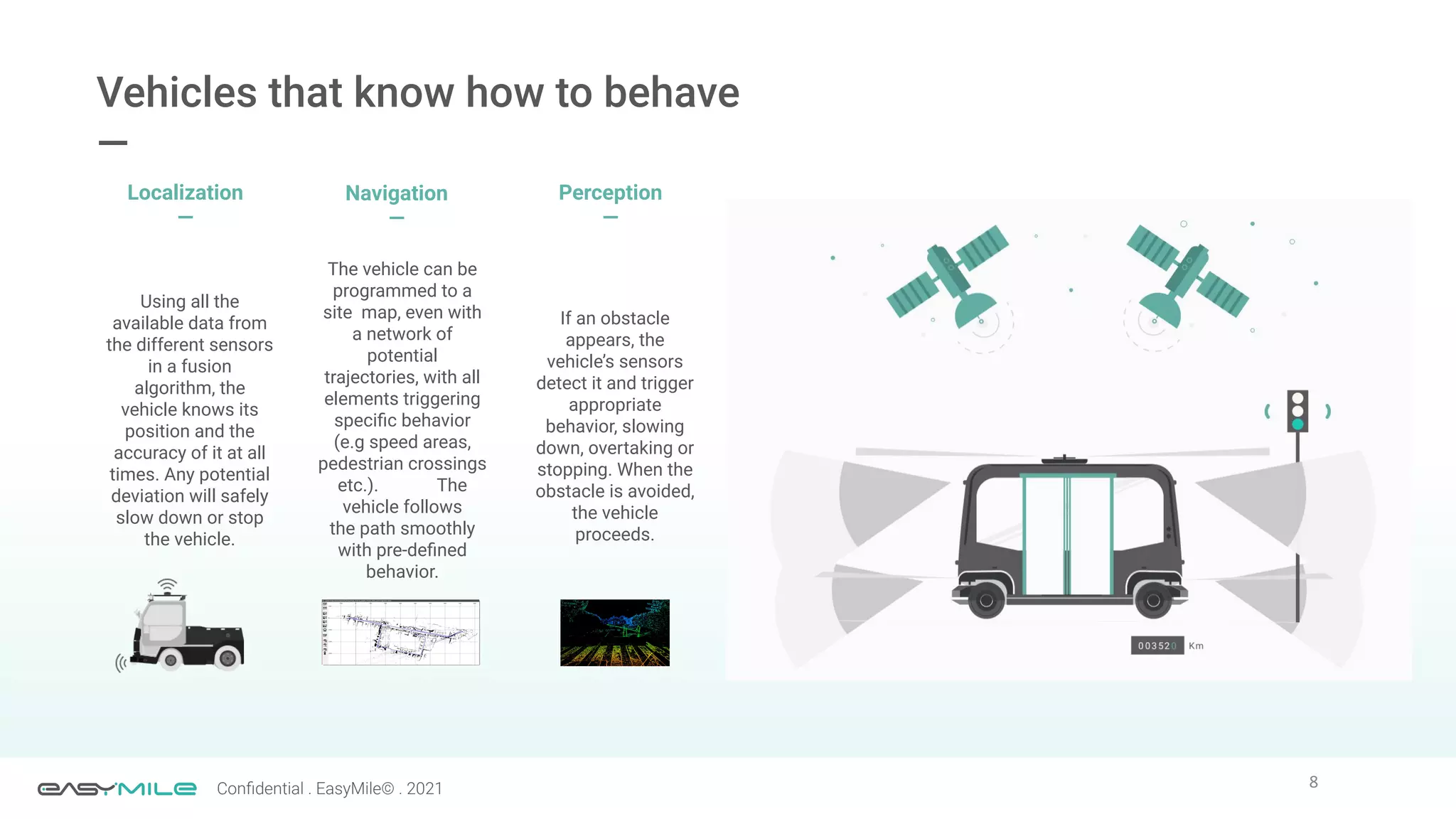
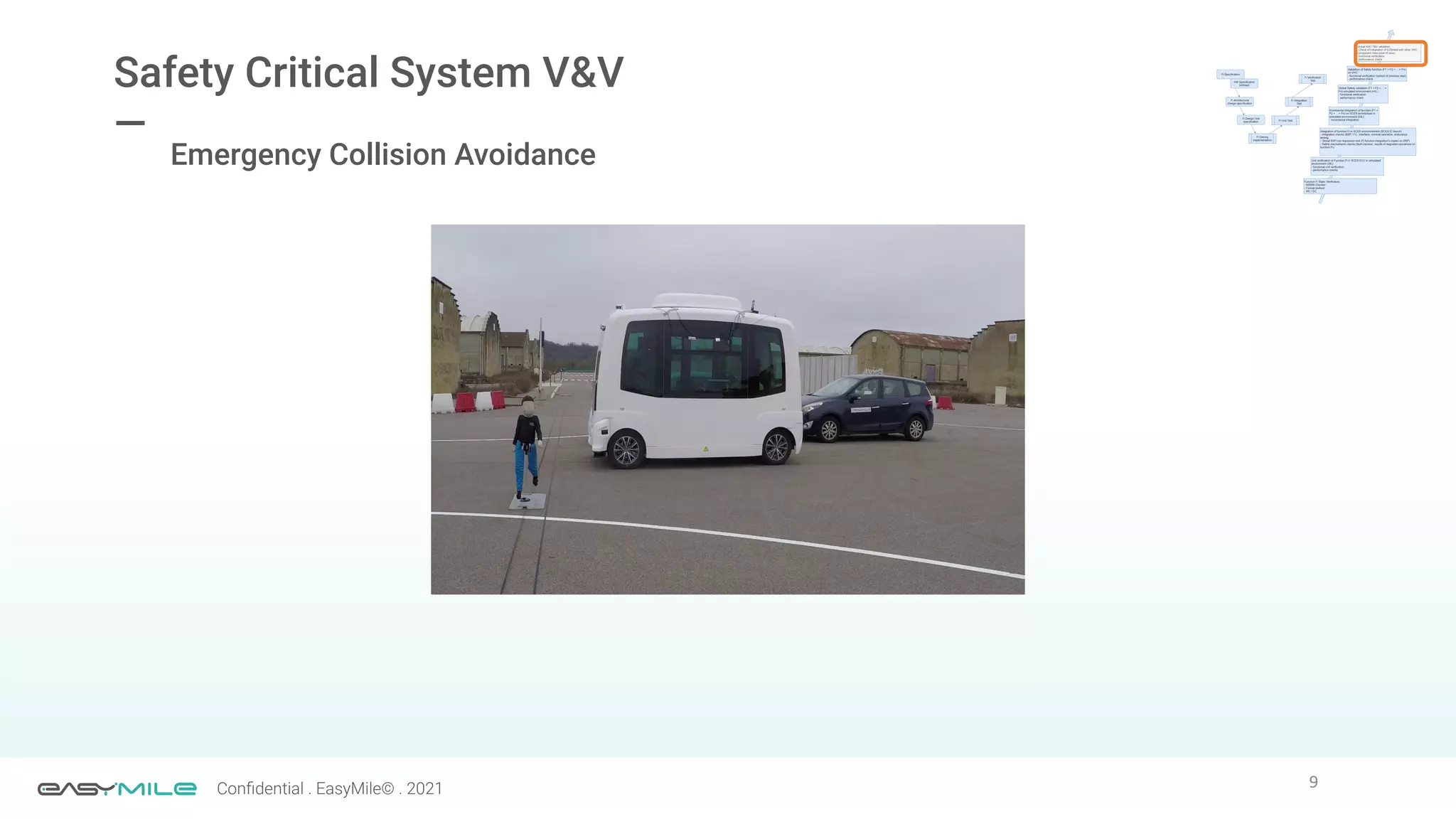
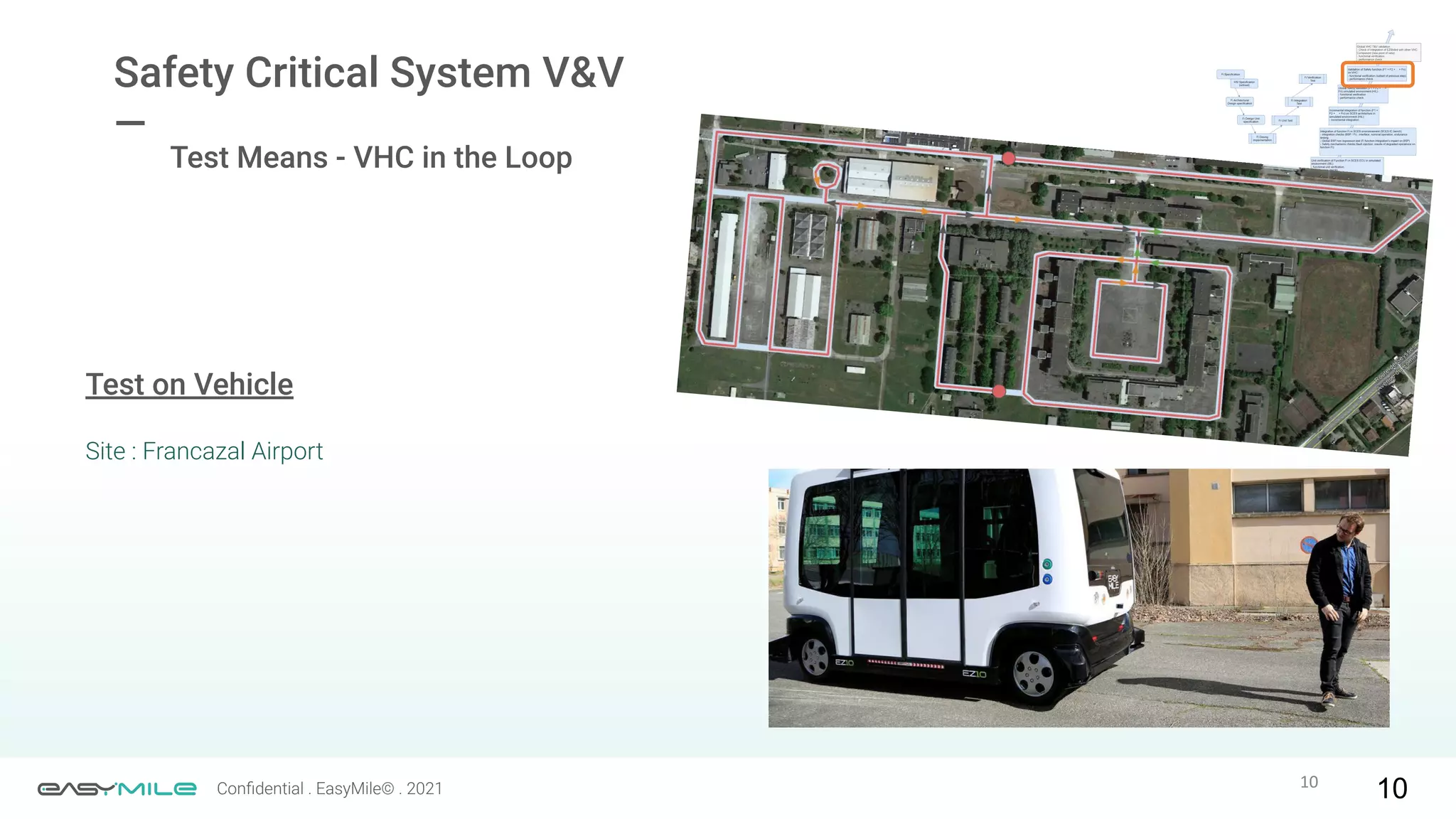
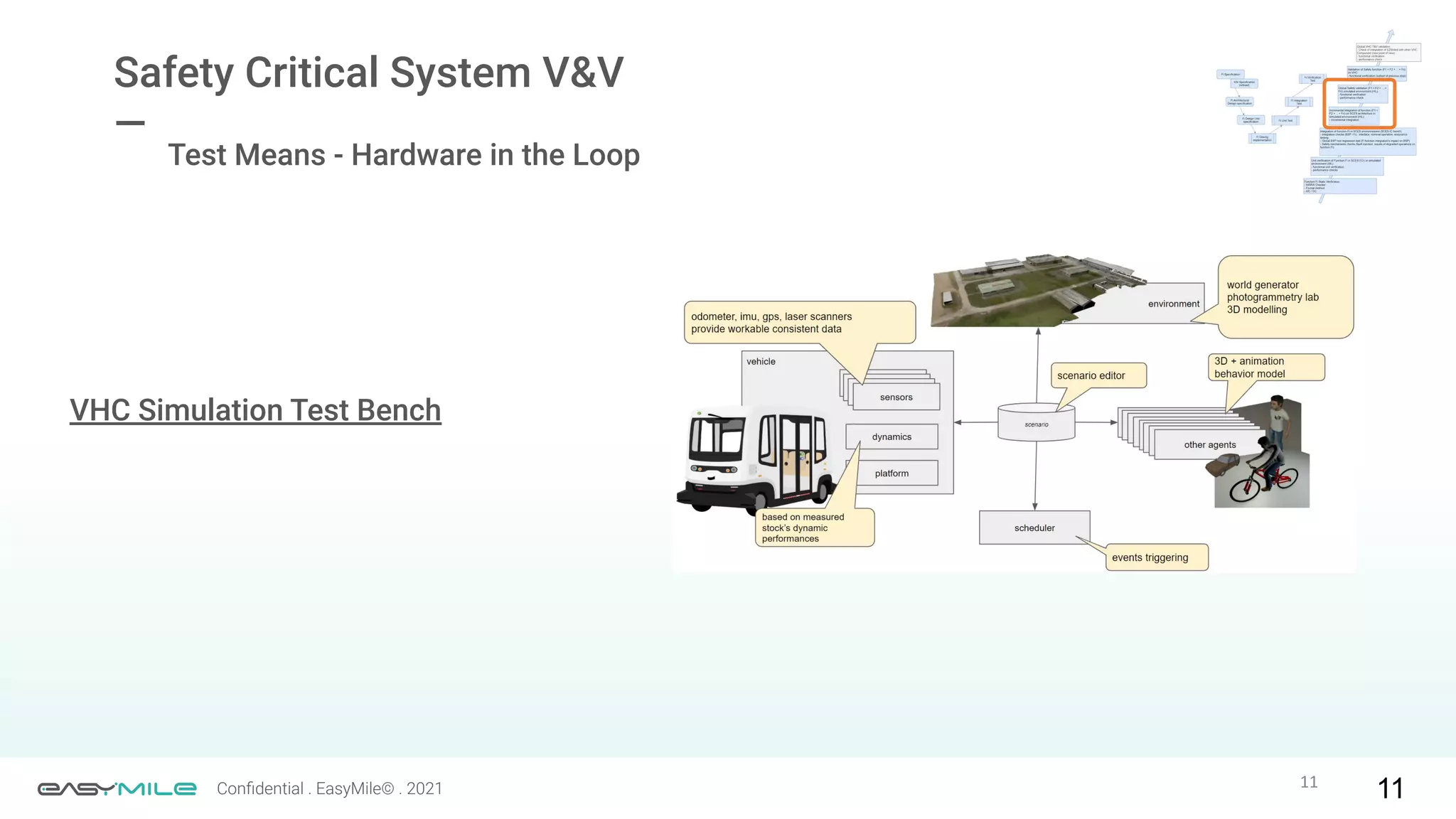
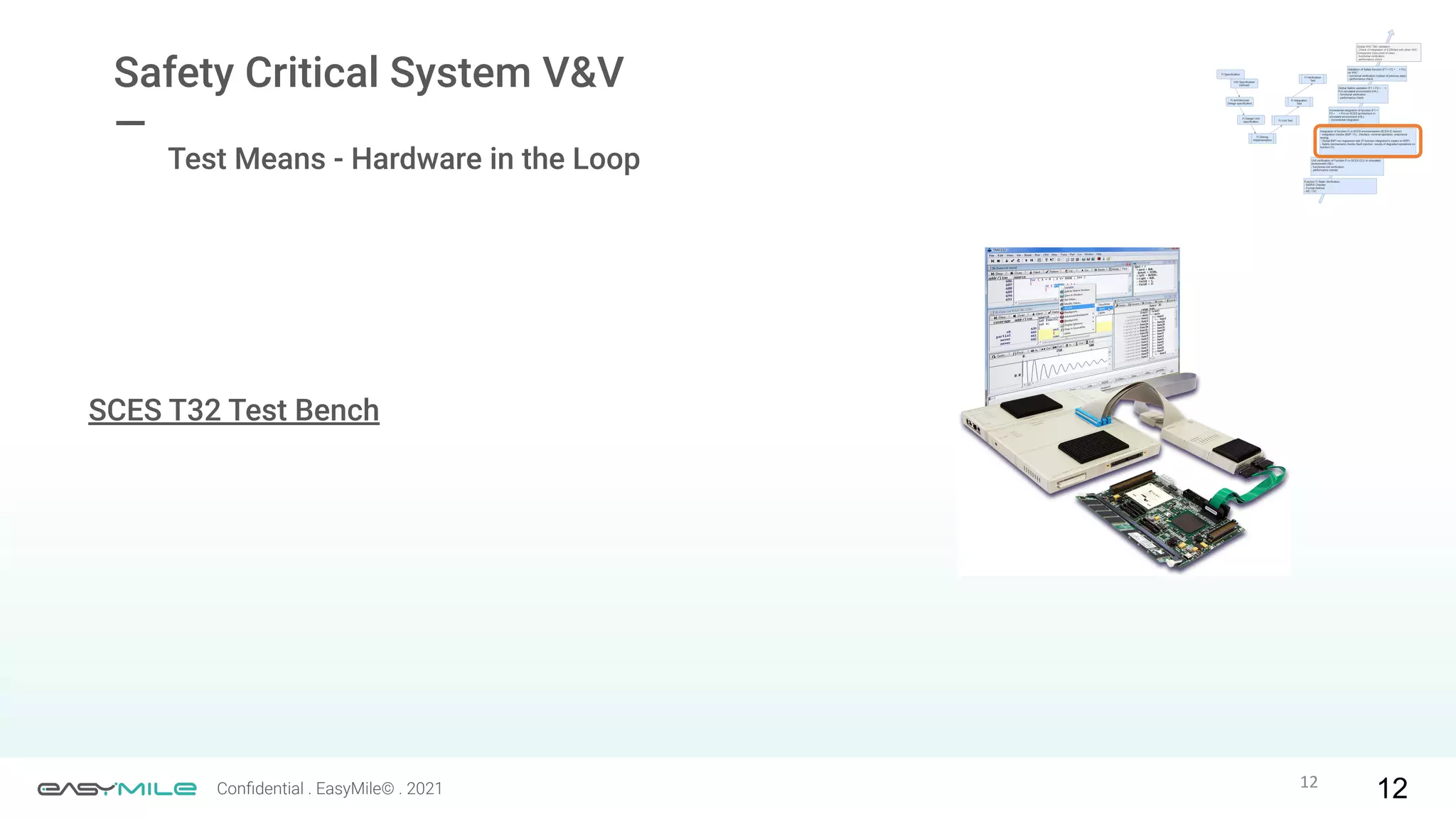
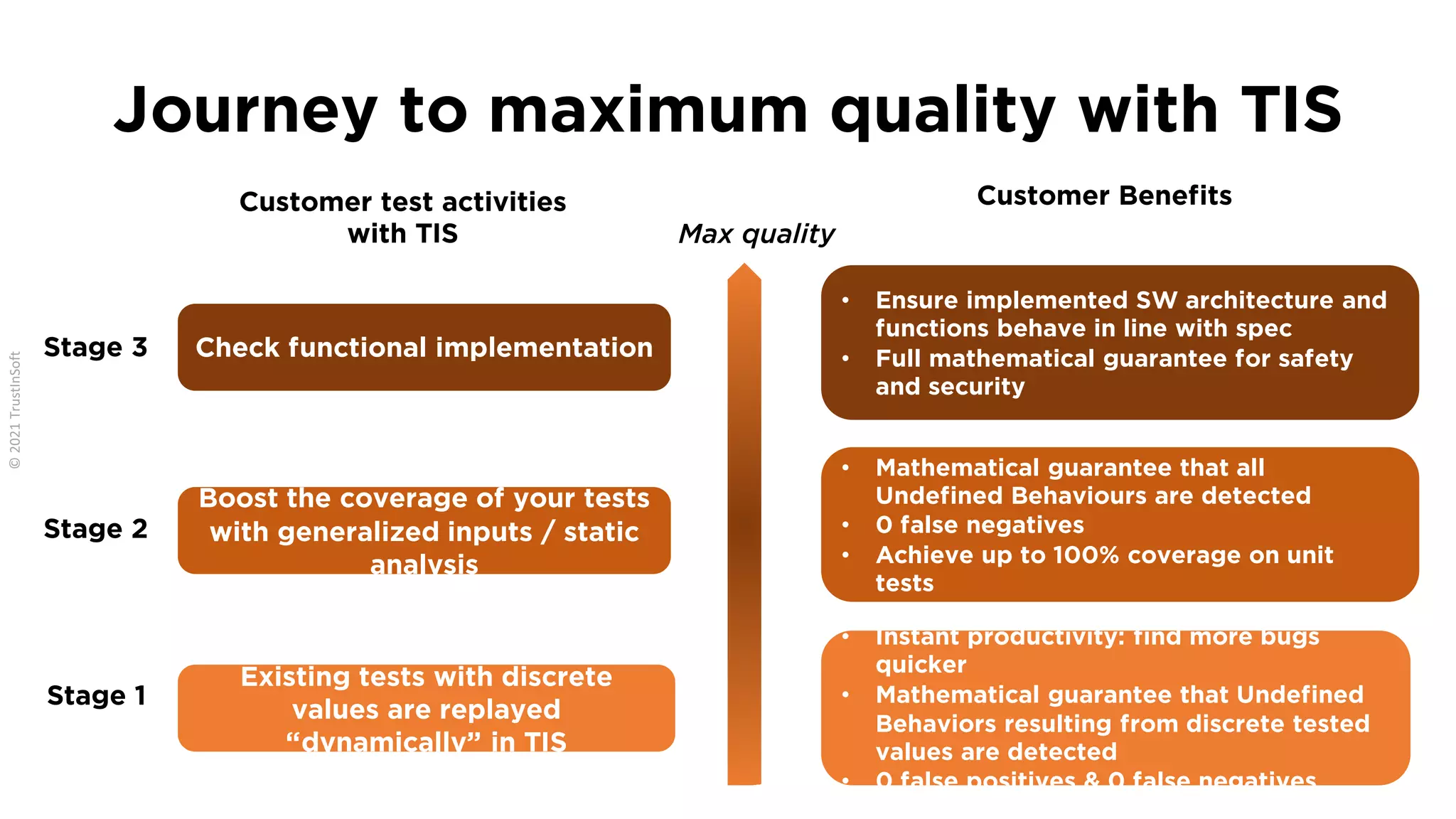
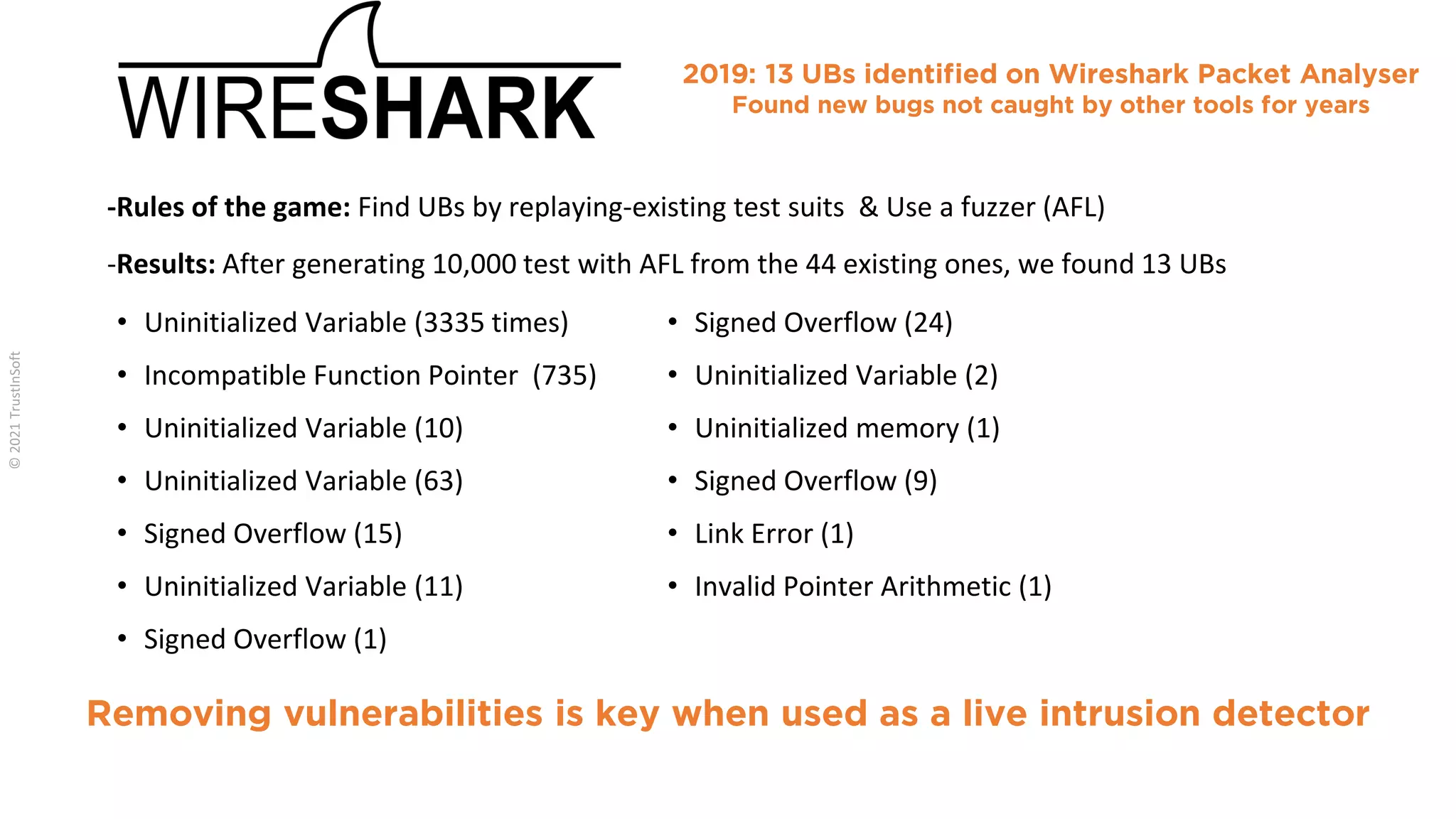
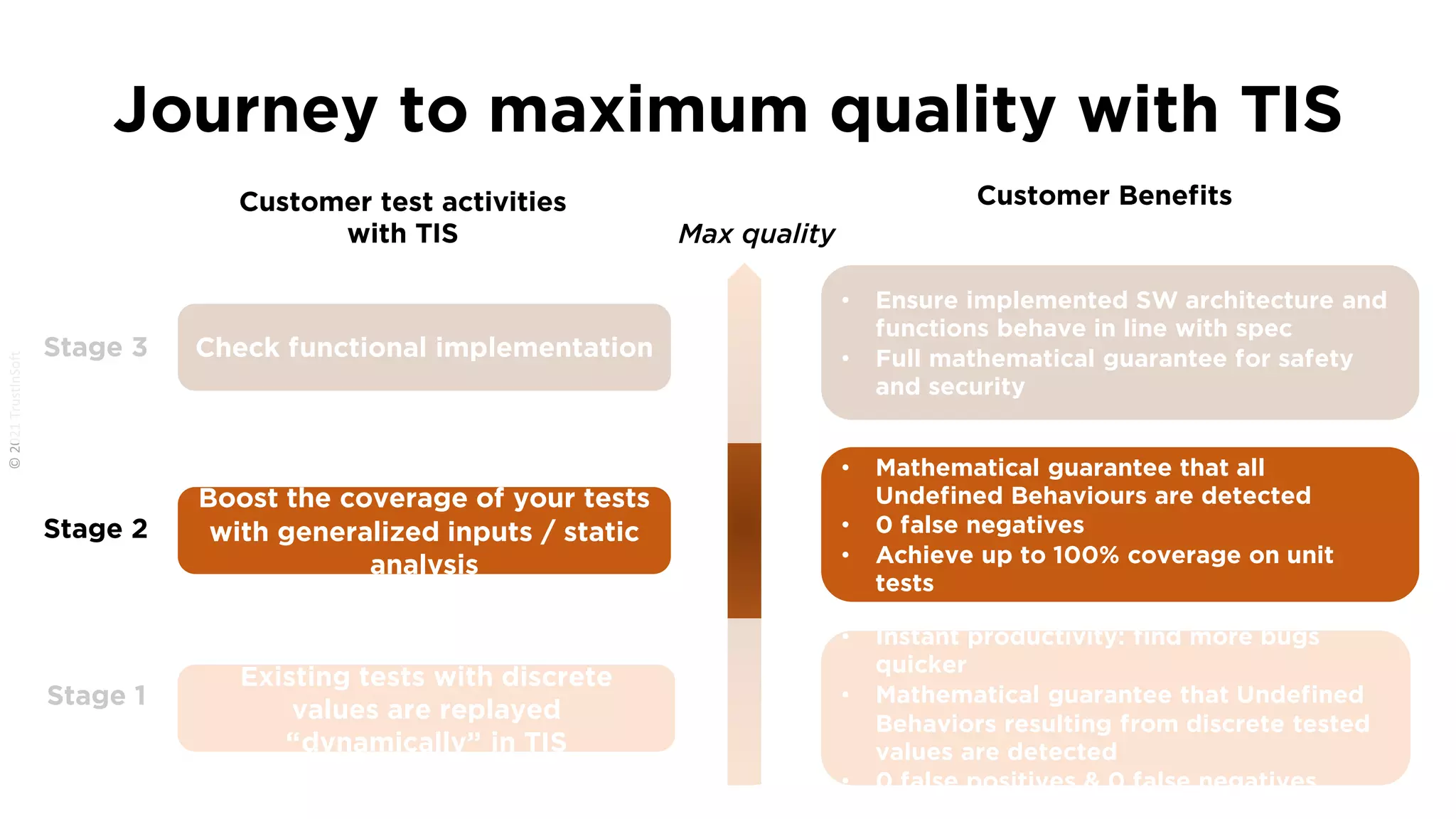
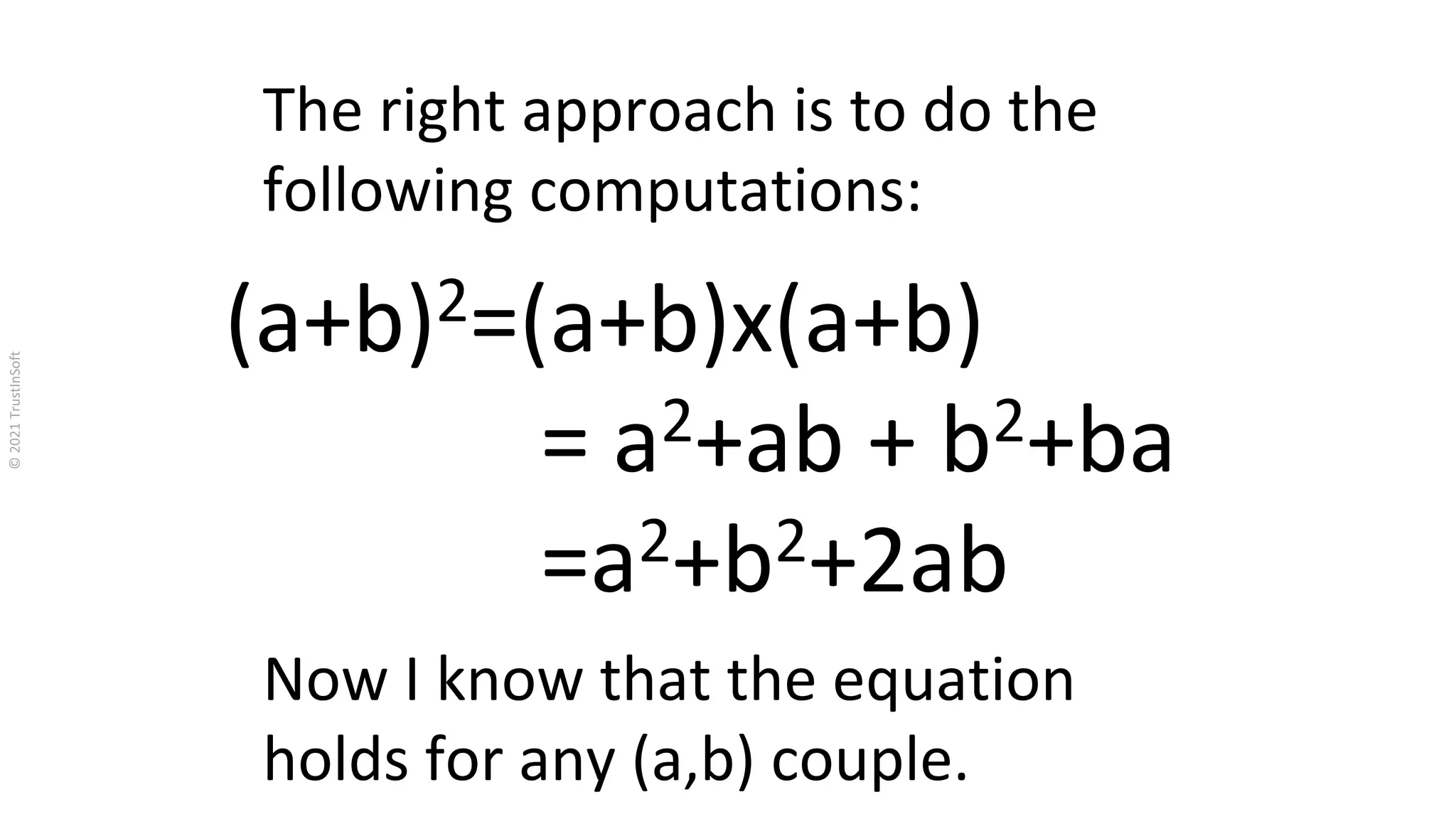
The document discusses the importance of functional safety and cybersecurity in the automotive industry, highlighting standards such as ISO 26262 and ISO 21434, which govern the development of electronic systems in vehicles. It addresses challenges like software requirement specifications, freedom from interference, and verification methods for software design to ensure safety and reliability. The document emphasizes the need for thorough training and rigorous assessment processes to achieve 0-bug software and comply with regulatory standards.















![Compute 2^4 in a virtual machine
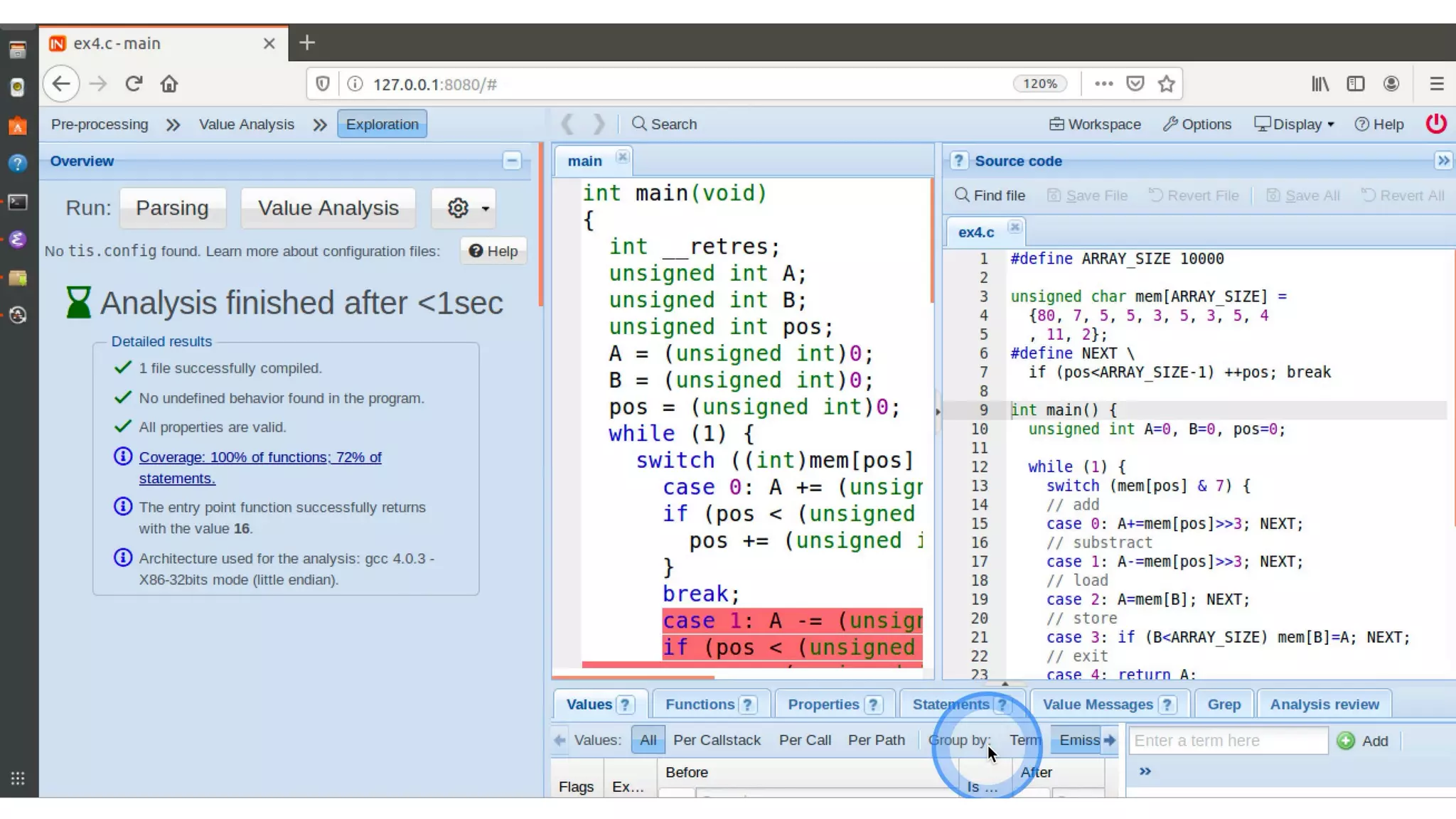
#define ARRAY_SIZE 10000
unsigned char mem[ARRAY_SIZE] =
{80, 7, 5, 5, 3, 5, 3, 5, 4 , 11, 2};
#define NEXT
if (pos<ARRAY_SIZE-1) ++pos; break
int main() {
unsigned int A=0, B=0, pos=0;
while (1) {
switch (mem[pos] & 7) {
// add
case 0: A+=mem[pos]>>3; NEXT;
// substract
case 1: A-=mem[pos]>>3; NEXT;
// load
case 2: A=mem[B]; NEXT;
// store
case 3: if (B<ARRAY_SIZE) mem[B]=A; NEXT;
// exit
case 4: return A;
// load and add
case 5: if (B<ARRAY_SIZE) A=A+mem[B]; NEXT;
// goto A
case 6: if (A<ARRAY_SIZE) pos=A; break;
// swap A and B
case 7: {int tmp=B; B=A; A=tmp;} NEXT;
}}}](https://image.slidesharecdn.com/slides-210406121315/75/Towards-0-bug-software-in-the-automotive-industry-48-2048.jpg)

![Compute 2^4 in a virtual machine
#define ARRAY_SIZE 10000
unsigned char mem[ARRAY_SIZE] =
{80, 7, 5, 5, 3, 5, 3, 5, 4 , 11, 2};
#define NEXT
if (pos<ARRAY_SIZE-1) ++pos; break
int main() {
unsigned int A=0, B=0, pos=0;
while (1) {
switch (mem[pos] & 7) {
// add
case 0: A+=mem[pos]>>3; NEXT;
// substract
case 1: A-=mem[pos]>>3; NEXT;
// load
case 2: A=mem[B]; NEXT;
// store
case 3: if (B<ARRAY_SIZE) mem[B]=A; NEXT;
// exit
case 4: return A;
// load and add
case 5: if (B<ARRAY_SIZE) A=A+mem[B]; NEXT;
// goto A
case 6: if (A<ARRAY_SIZE) pos=A; break;
// swap A and B
case 7: {int tmp=B; B=A; A=tmp;} NEXT;
}}}](https://image.slidesharecdn.com/slides-210406121315/75/Towards-0-bug-software-in-the-automotive-industry-50-2048.jpg)

![solution
#include <tis_builtin.h>
#define ARRAY_SIZE 10000
unsigned char mem[ARRAY_SIZE] =
{80, 7, 5, 5, 3, 5, 3, 5, 4 , 11, 2};
#define NEXT
if (pos<ARRAY_SIZE-1) ++pos; break
int main() {
unsigned int A=0, B=0, pos=0;
tis_make_unkown(mem, ARRAY_SIZE);
while (1) {
switch (mem[pos] & 7) {
// add
case 0: A+=mem[pos]>>3; NEXT;
// substract
case 1: A-=mem[pos]>>3; NEXT;
// load
case 2: A=mem[B]; NEXT;
// store
case 3: if (B<ARRAY_SIZE) mem[B]=A; NEXT;
// exit
case 4: return A;
// load and add
case 5: if (B<ARRAY_SIZE) A=A+mem[B]; NEXT;
// goto A
case 6: if (A<ARRAY_SIZE) pos=A; break;
// swap A and B
case 7: {int tmp=B; B=A; A=tmp;} NEXT;
}}}](https://image.slidesharecdn.com/slides-210406121315/75/Towards-0-bug-software-in-the-automotive-industry-54-2048.jpg)
![solution
#include <tis_builtin.h>
#define ARRAY_SIZE 10000
unsigned char mem[ARRAY_SIZE] =
{80, 7, 5, 5, 3, 5, 3, 5, 4 , 11, 2};
#define NEXT
if (pos<ARRAY_SIZE-1) ++pos; break
int main() {
unsigned int A=0, B=0, pos=0;
tis_make_unkown(mem, ARRAY_SIZE);
while (1) {
switch (mem[pos] & 7) {
// add
case 0: A+=mem[pos]>>3; NEXT;
// substract
case 1: A-=mem[pos]>>3; NEXT;
// load
case 2: if (B<ARRAY_SIZE) A=mem[B]; NEXT;
// store
case 3: if (B<ARRAY_SIZE) mem[B]=A; NEXT;
// exit
case 4: return A;
// load and add
case 5: if (B<ARRAY_SIZE) A=A+mem[B]; NEXT;
// goto A
case 6: if (A<ARRAY_SIZE) pos=A; break;
// swap A and B
case 7: {int tmp=B; B=A; A=tmp;} NEXT;
}}}](https://image.slidesharecdn.com/slides-210406121315/75/Towards-0-bug-software-in-the-automotive-industry-55-2048.jpg)


![/*@requires n>=0 &&
valid(t+(0 .. n−1));
assigns nothing;
ensures result!=0 <==>
(forall integer j ;0<=j<n ==> t[j]==0) ;
*/
int check_all_zeros (int t[],int n){
int k;
/*@ loop invariant 0<=k<=n;
loop invariant (forall integer j ; 0<=j<k ==> t[j]==0);
loop assigns k ;
loop variant n−k ; */
for(k=0; k<n; k++)
if(t[k]!=0)
return 0;
return 1;
}
Checking values
in an array
9 red lines
6 black lines
From https://nikolai-kosmatov.eu/publications/talk_2015_11_24_SASEFOR_slides.pdf, thanks Nikolaï!](https://image.slidesharecdn.com/slides-210406121315/75/Towards-0-bug-software-in-the-automotive-industry-61-2048.jpg)