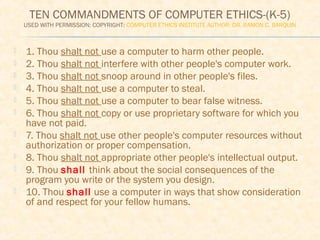
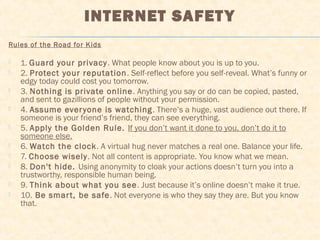
This document discusses digital footprints and online ethics. It begins by explaining that students should understand how to safely and responsibly use the internet to create a positive digital footprint. It then provides two codes of ethics for computer and internet use - the Ten Commandments of Computer Ethics and the High School/University Code of Ethics. Both codes outline responsible behaviors around topics like privacy, property, honesty and respect. The document concludes by asking students to consider what kind of digital footprint they are creating and stresses the importance of only posting online what they would be proud of in the future.