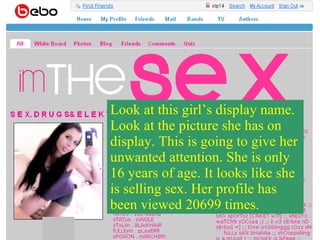
The document discusses various online safety issues for teenagers. It defines cyber crimes like cyber stalking and intimidation. It provides tips for being safe online such as not sharing personal information, avoiding strangers, and telling a trusted adult if feeling uncomfortable. Acronyms used in texting are explained. Overall, the document aims to educate youth on potential online dangers and how to stay safe when using the internet and social media.