This document summarizes several vulnerabilities that affected Ruby on Rails applications in early 2013. It describes 4 SQL injection vulnerabilities in January, an unsafe query generation issue in January, and an XML deserialization of YAML vulnerability in January that could allow remote code execution. It warns that YAML can be deserialized to objects and discusses eval usage. It provides recommendations to stay up-to-date on Rails security updates, sign up for security mailing lists, use strong parameters, and sanitize inputs to applications.




























![Post.find_by_id(params[:id])
I Can Haz Inject SQL?
Jan 2
CVE-2012-5664
SQL Injection Vulnerability](https://image.slidesharecdn.com/slides-130207110801-phpapp01/85/YAML-is-the-new-Eval-30-320.jpg)
![HashWithIndifferentAccess
Post.find_by_id(params[:id])
I Can Haz Inject SQL?
Jan 2
CVE-2012-5664
SQL Injection Vulnerability](https://image.slidesharecdn.com/slides-130207110801-phpapp01/85/YAML-is-the-new-Eval-31-320.jpg)


![CookieStore
session[:token] = {:select => “foo; DROP TABLE… ; --”}
Jan 2
CVE-2012-5664
SQL Injection Vulnerability](https://image.slidesharecdn.com/slides-130207110801-phpapp01/85/YAML-is-the-new-Eval-34-320.jpg)


![Foo.find_by_bar( [ nil ] )
JSON or XML payload
Result
Jan 8
CVE-2013-0155
Unsafe Query Generation](https://image.slidesharecdn.com/slides-130207110801-phpapp01/85/YAML-is-the-new-Eval-37-320.jpg)



![!ruby/hash
Calls #[]=
Jan 14
CVE-2013-0156
XML will deserialize YAML](https://image.slidesharecdn.com/slides-130207110801-phpapp01/85/YAML-is-the-new-Eval-42-320.jpg)

![ActionController::Routing::
RouteSet::NamedRouteCollection
def add(name, route)
define_named_route_methods(name, route)
end
alias []= add
def define_url_helper(route, name, kind, options)
@module.module_eval <<-END
def #{name}_#{kind}(*args)
Jan 14
options = hash_for_#{name}_#{kind}(args.extract_options!)
CVE-2013-0156
XML will deserialize YAML](https://image.slidesharecdn.com/slides-130207110801-phpapp01/85/YAML-is-the-new-Eval-44-320.jpg)












![attr_accessible
even better : strong_parameters
params.require(:person).permit(:name, :age)
params.permit(:name, { :emails => [ ] }](https://image.slidesharecdn.com/slides-130207110801-phpapp01/85/YAML-is-the-new-Eval-59-320.jpg)
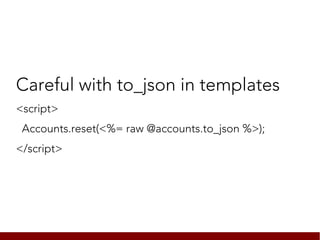
![Careful with to_json in templates
<script>
Accounts.reset([{name: "</script><script>alert('xss')</script>", ...}]);
</script>](https://image.slidesharecdn.com/slides-130207110801-phpapp01/85/YAML-is-the-new-Eval-61-320.jpg)