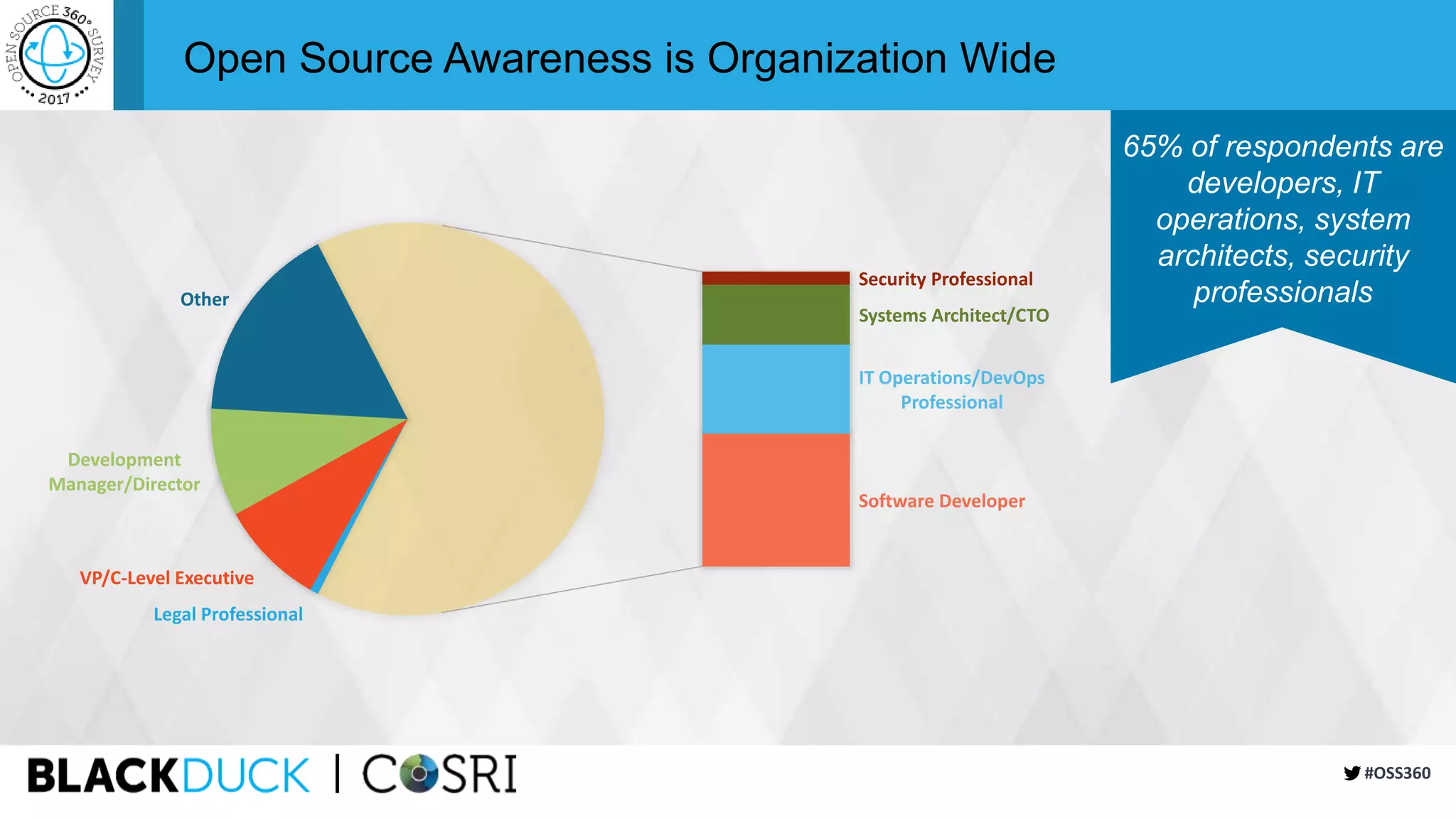
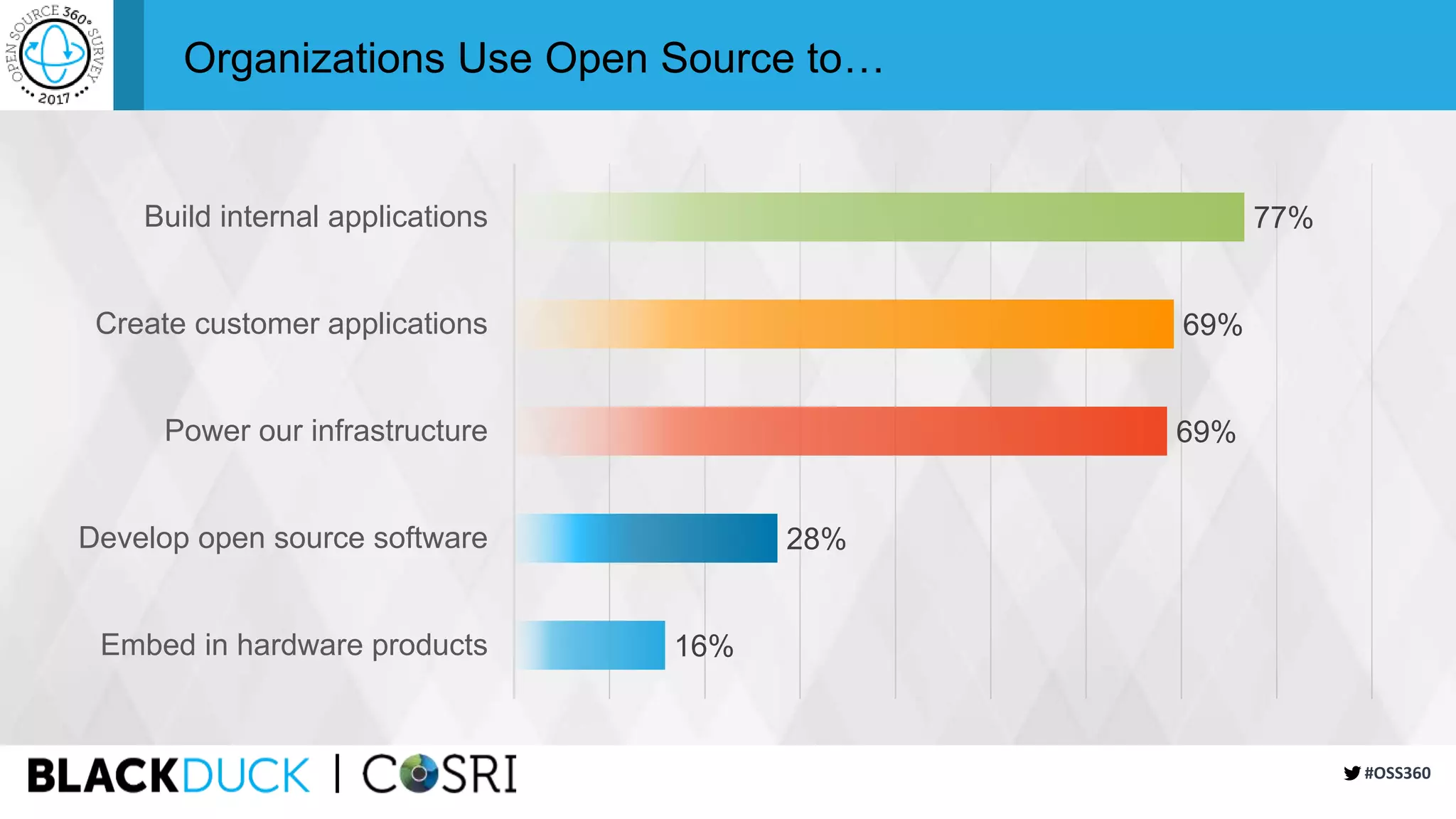
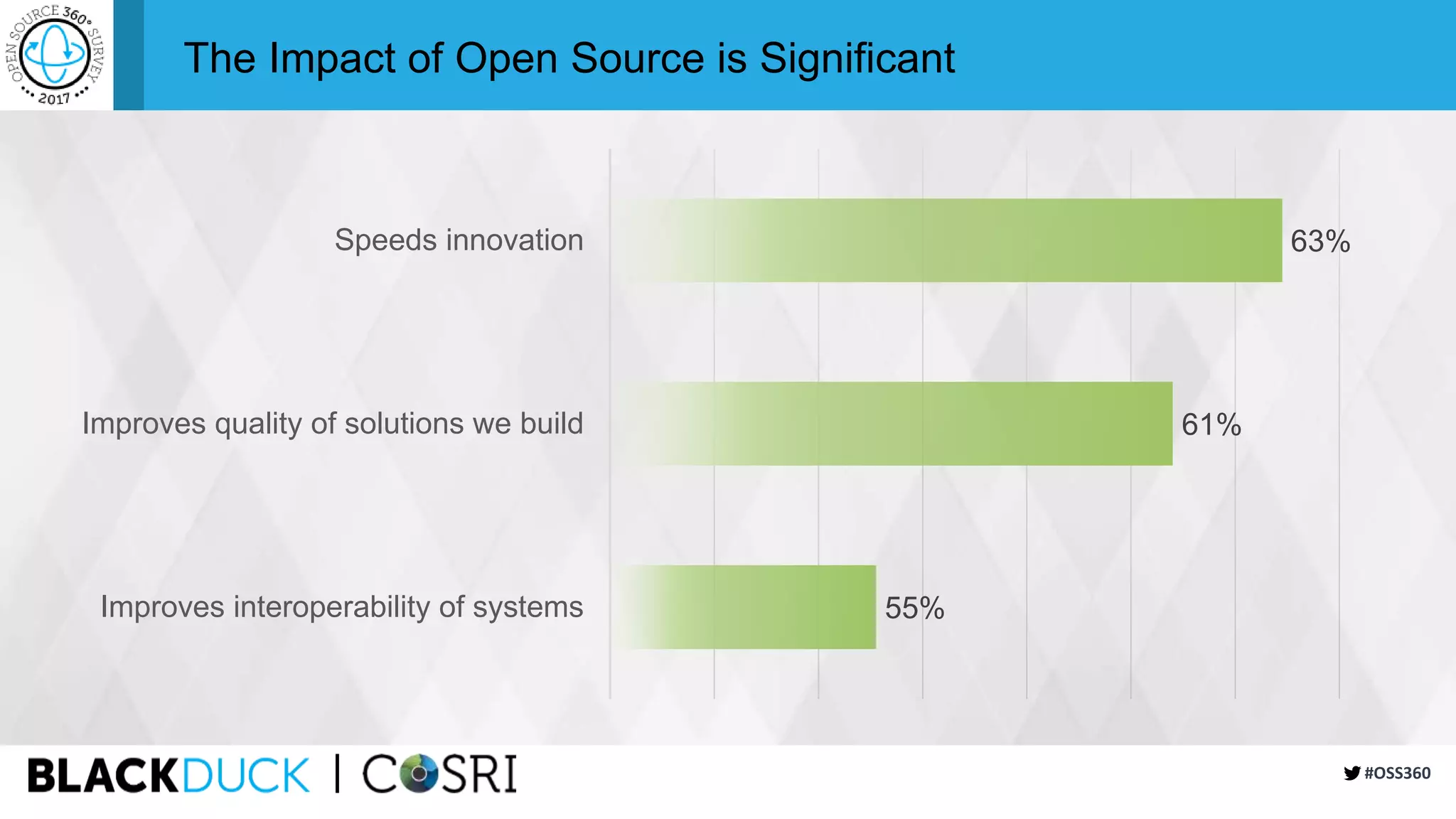
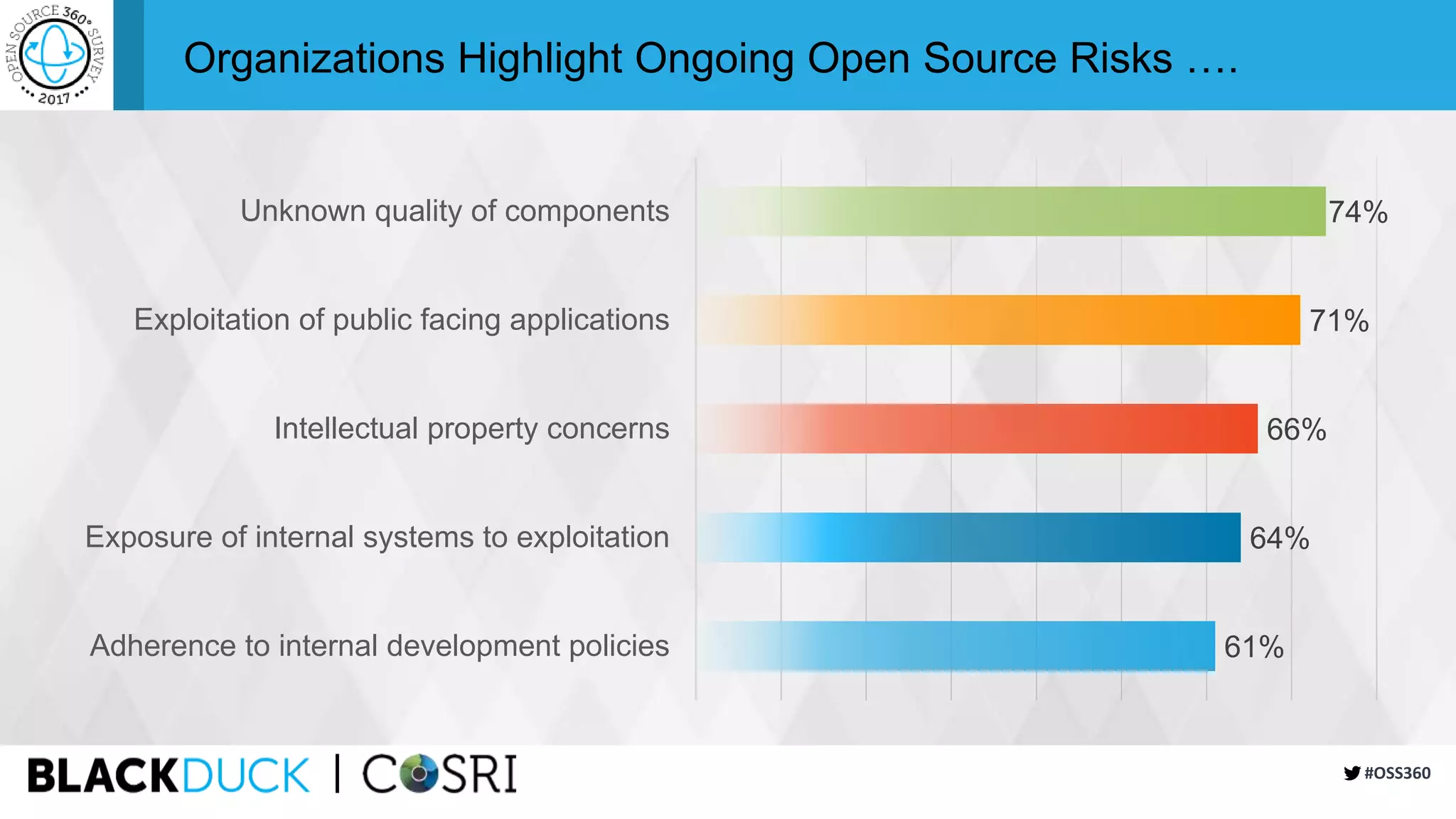
This document summarizes the findings of a survey about open source software usage. It finds that open source usage has increased significantly and is now core to most organizations' IT infrastructure. However, many organizations still do not have formal processes for managing open source use and risks. Common risks include unreviewed code, lack of responsibility for security issues, and incomplete vulnerability tracking. The document recommends that organizations improve open source governance, automate reviews, and participate more actively in open source communities to help address ongoing risks from open source use.