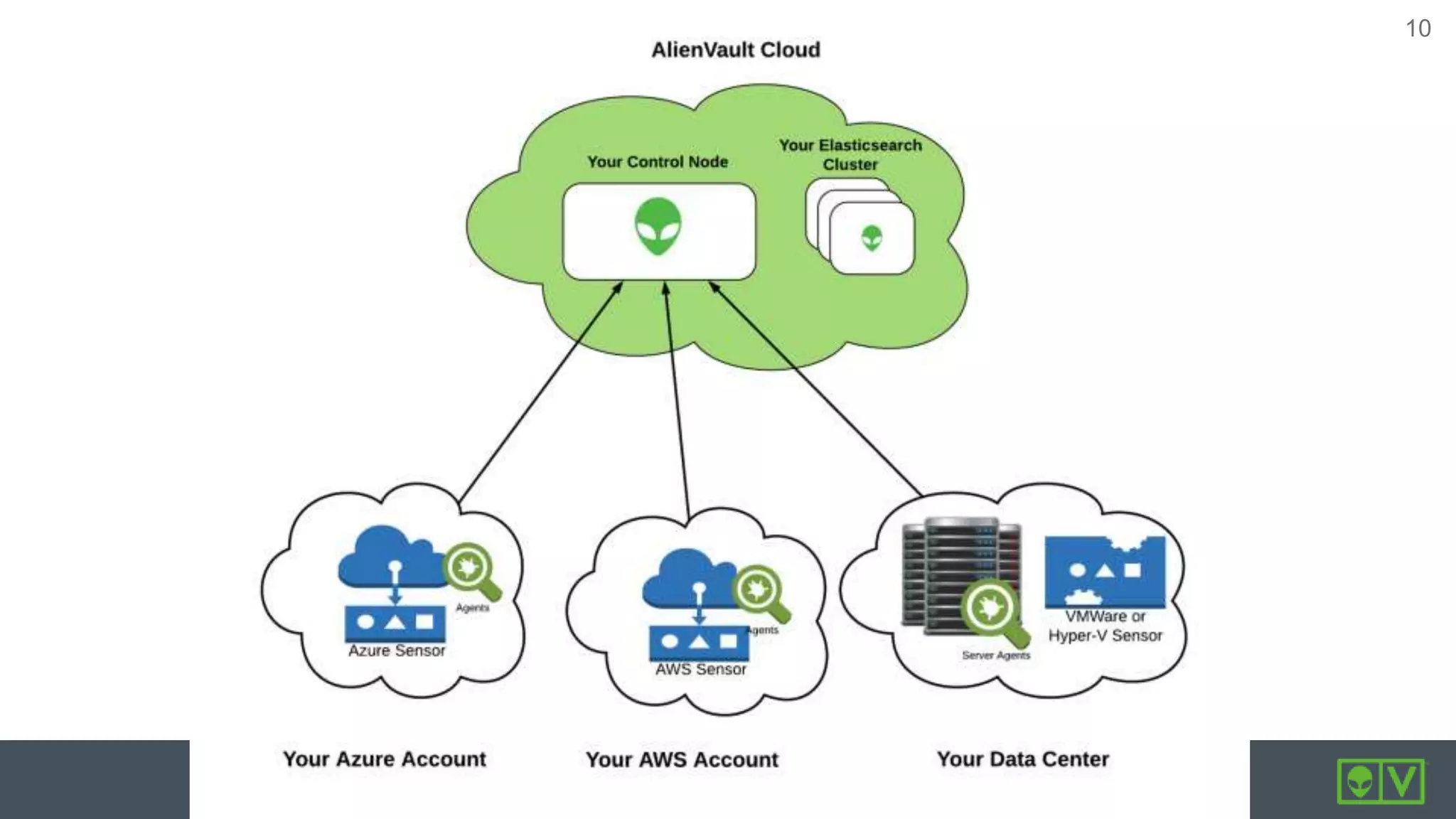
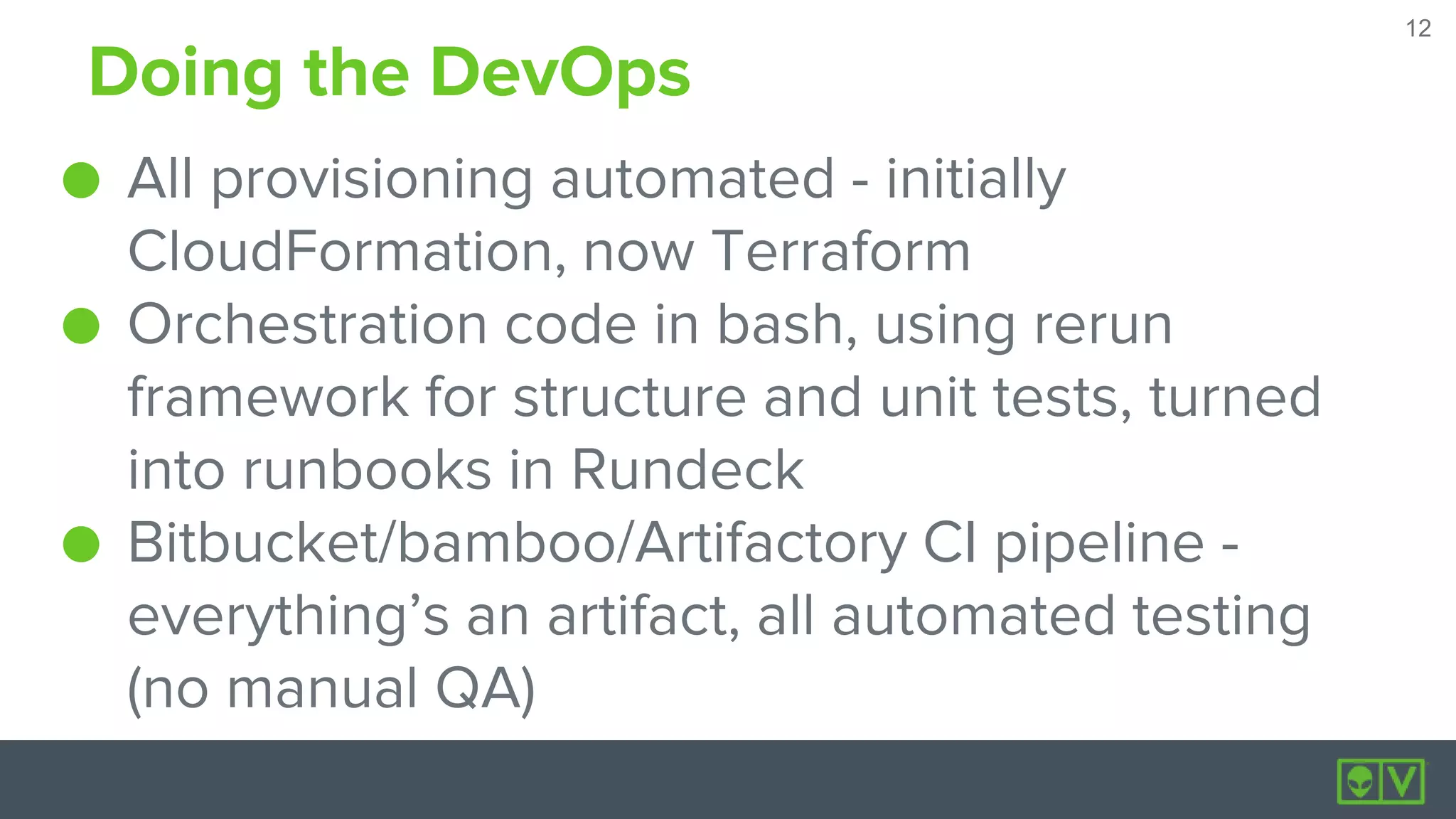
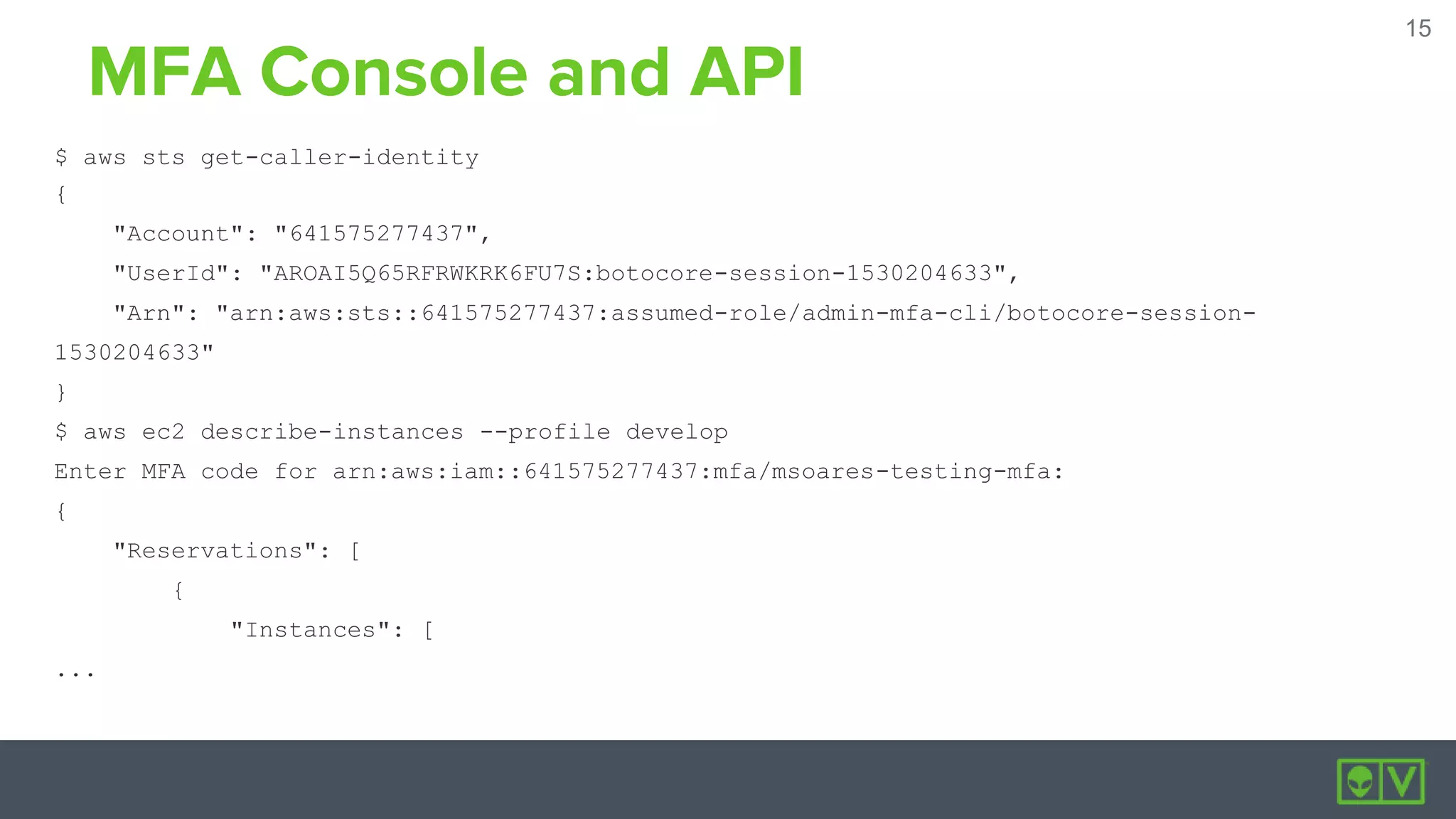
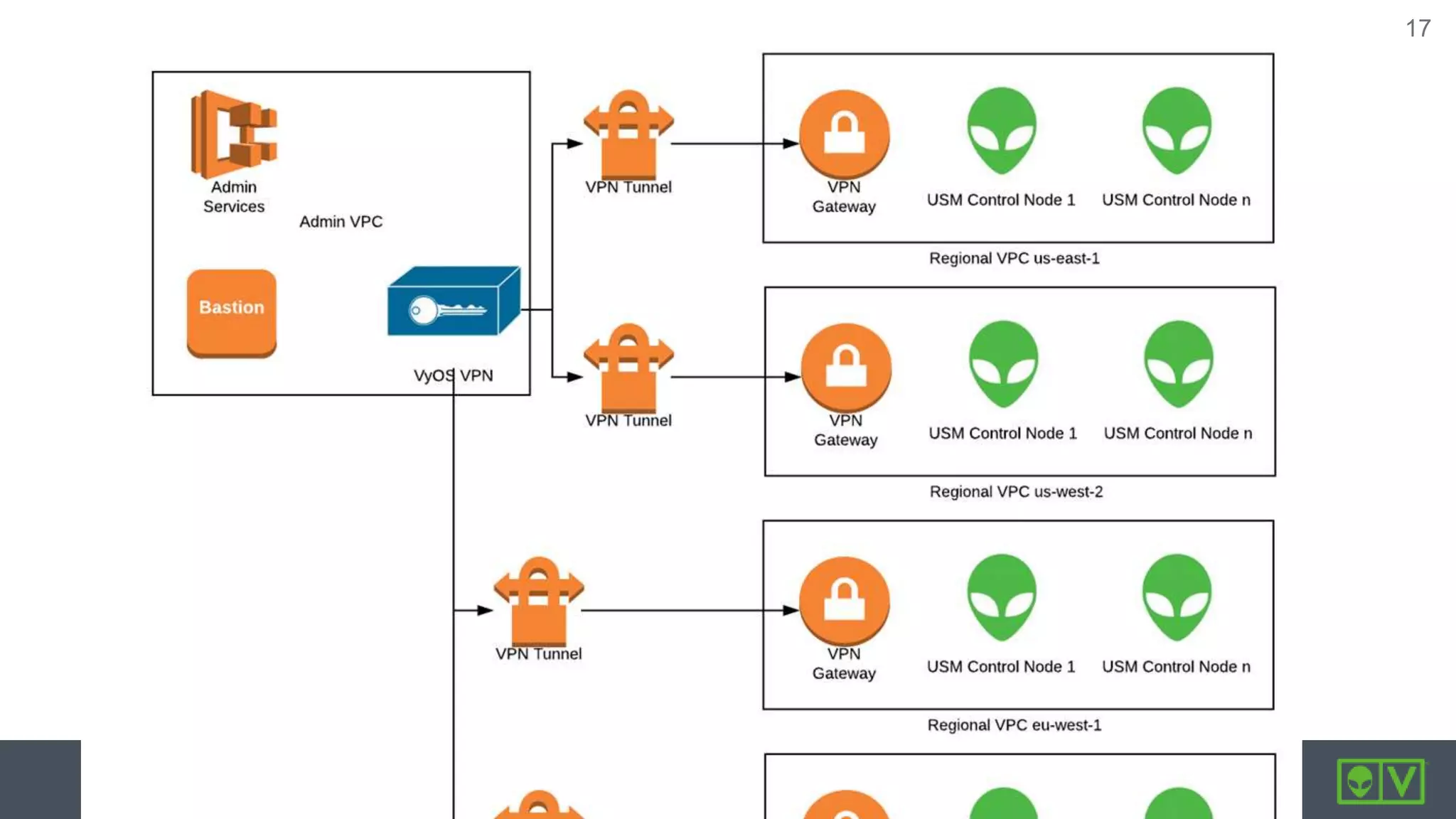
AlienVault launched USM Anywhere, a security information and event management (SIEM) software-as-a-service, in just six months by building it entirely on Amazon Web Services (AWS). The new SaaS used services across AWS including EC2, S3, Lambda, RDS, and more. While most of the components ran in AWS, some sensors integrated with Azure, VMware, and other platforms. The product was developed using DevOps practices like infrastructure as code with Terraform, configuration management with Puppet, continuous integration with Bitbucket and Bamboo, and orchestration with Rundeck. Security measures included multi-factor authentication, separate VPCs and security groups, encryption of data at