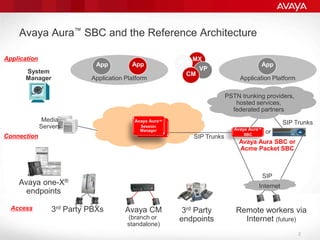
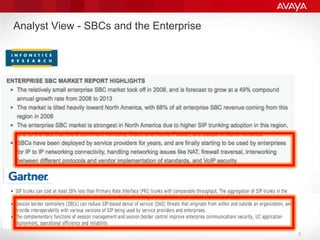
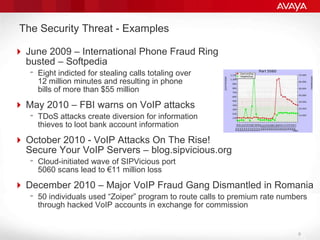
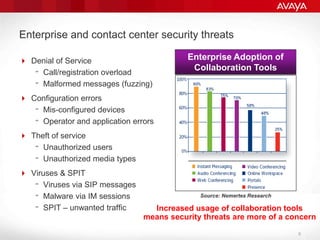
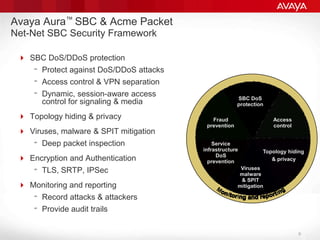
The document explains the necessity of session border controllers (SBCs) in enterprise communication systems to enhance flexibility, improve security, and enable support for specific customer call flows. It highlights the differences between service provider networks and enterprise needs, emphasizes the security threats faced in VoIP communications, and outlines how SBCs can mitigate these risks through features like call monitoring and encryption. Additionally, it discusses the implications of using SBCs for integration with SIP trunk providers and ensuring compliance with security standards.