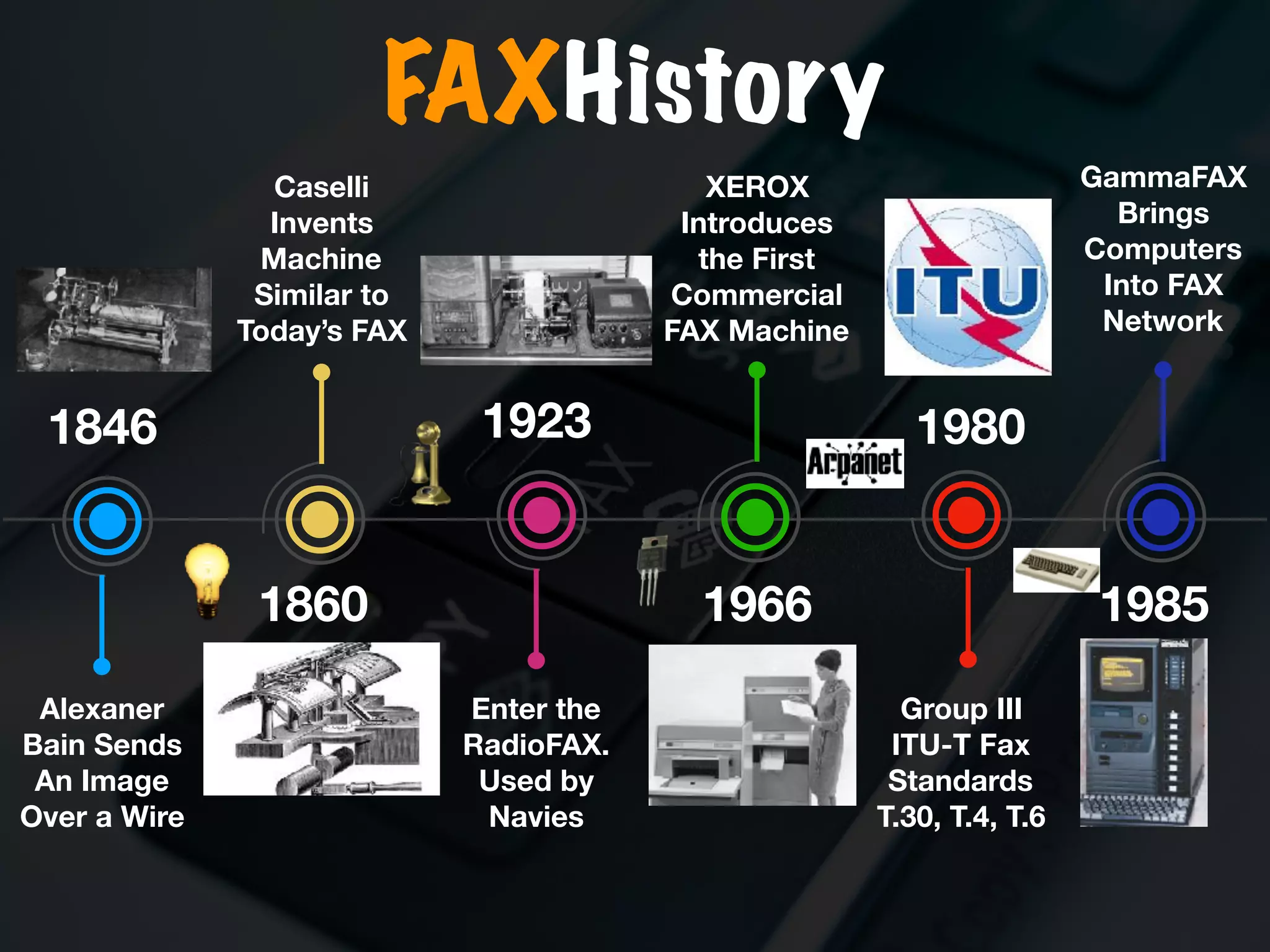
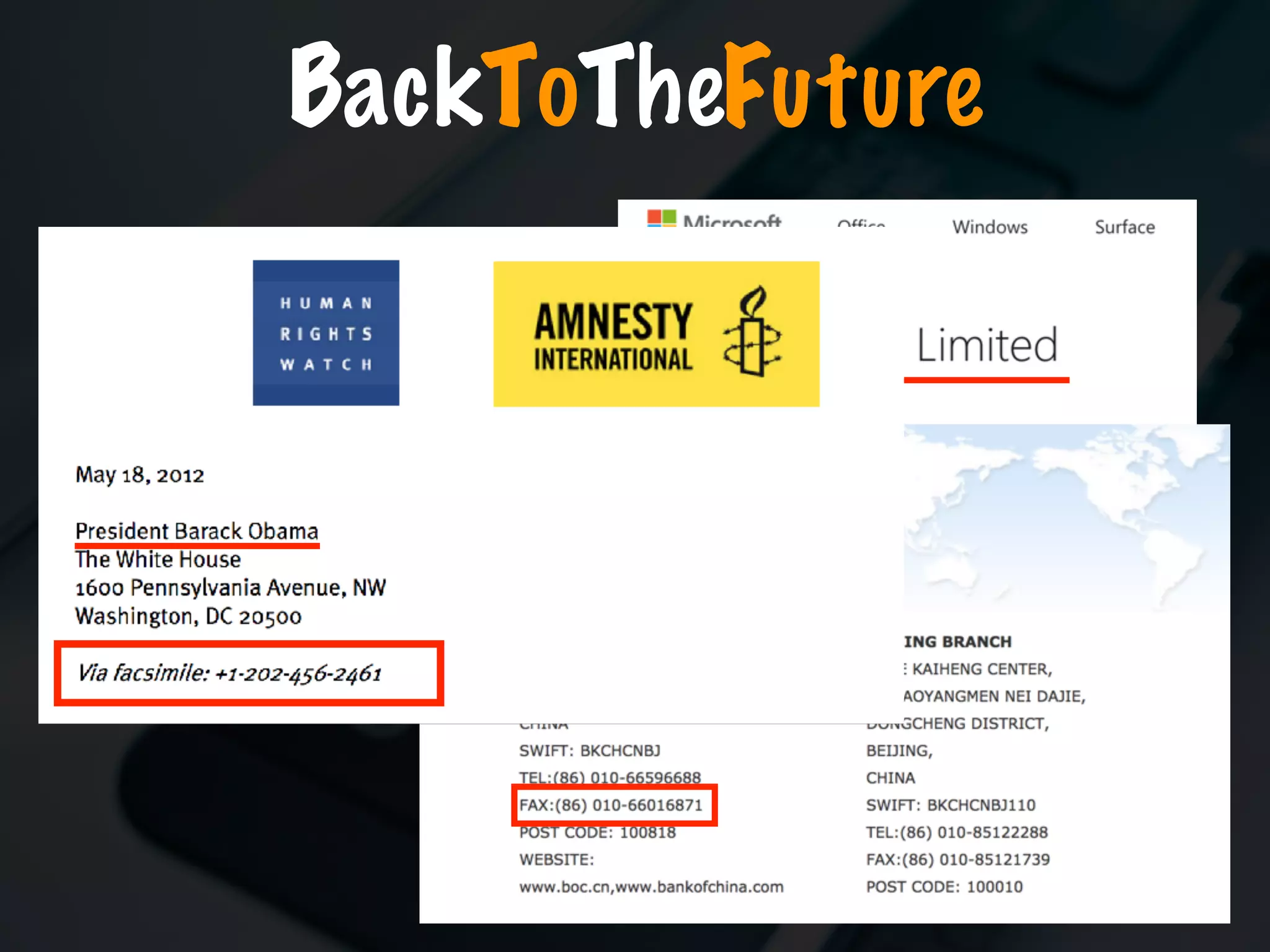
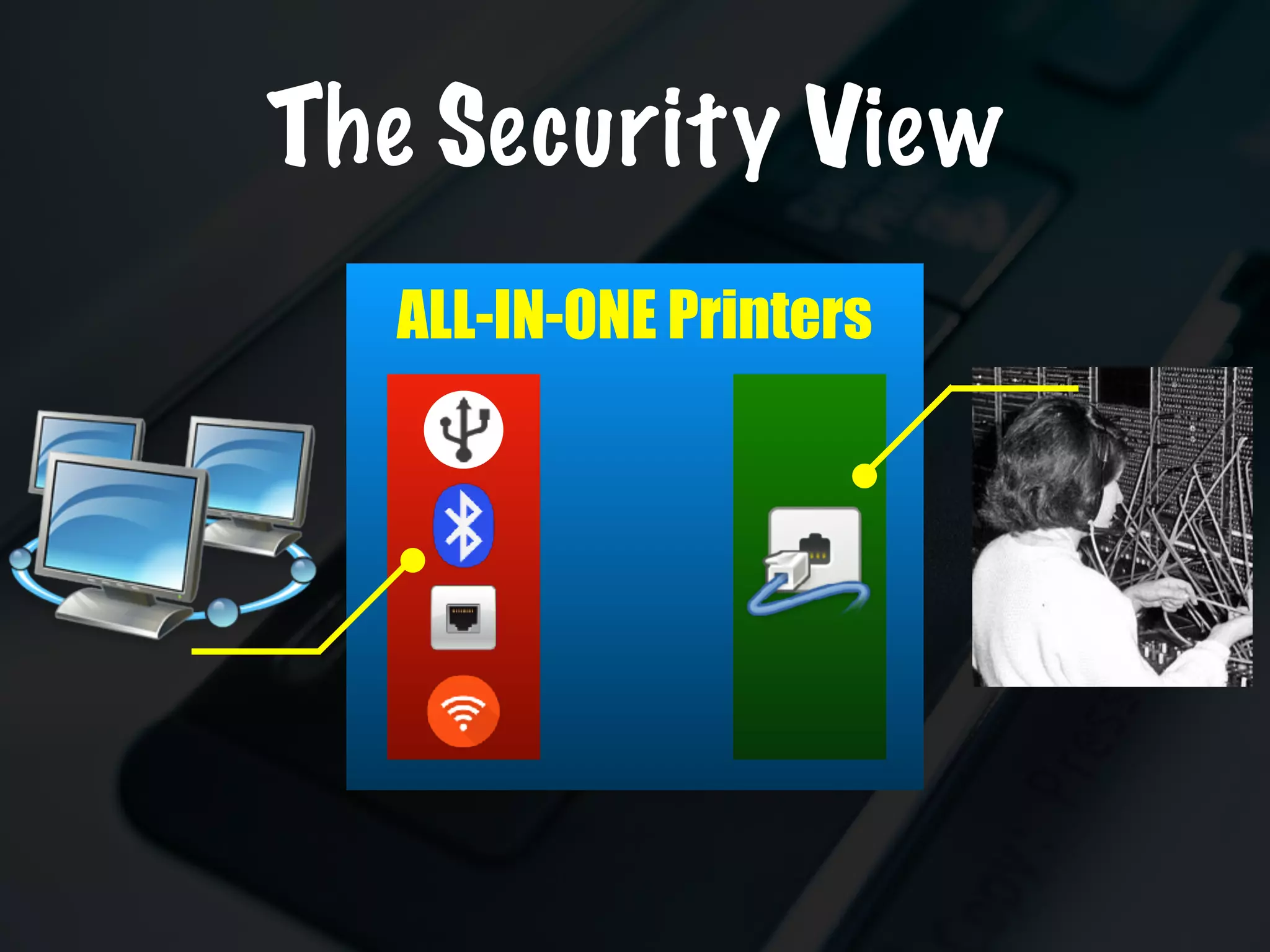
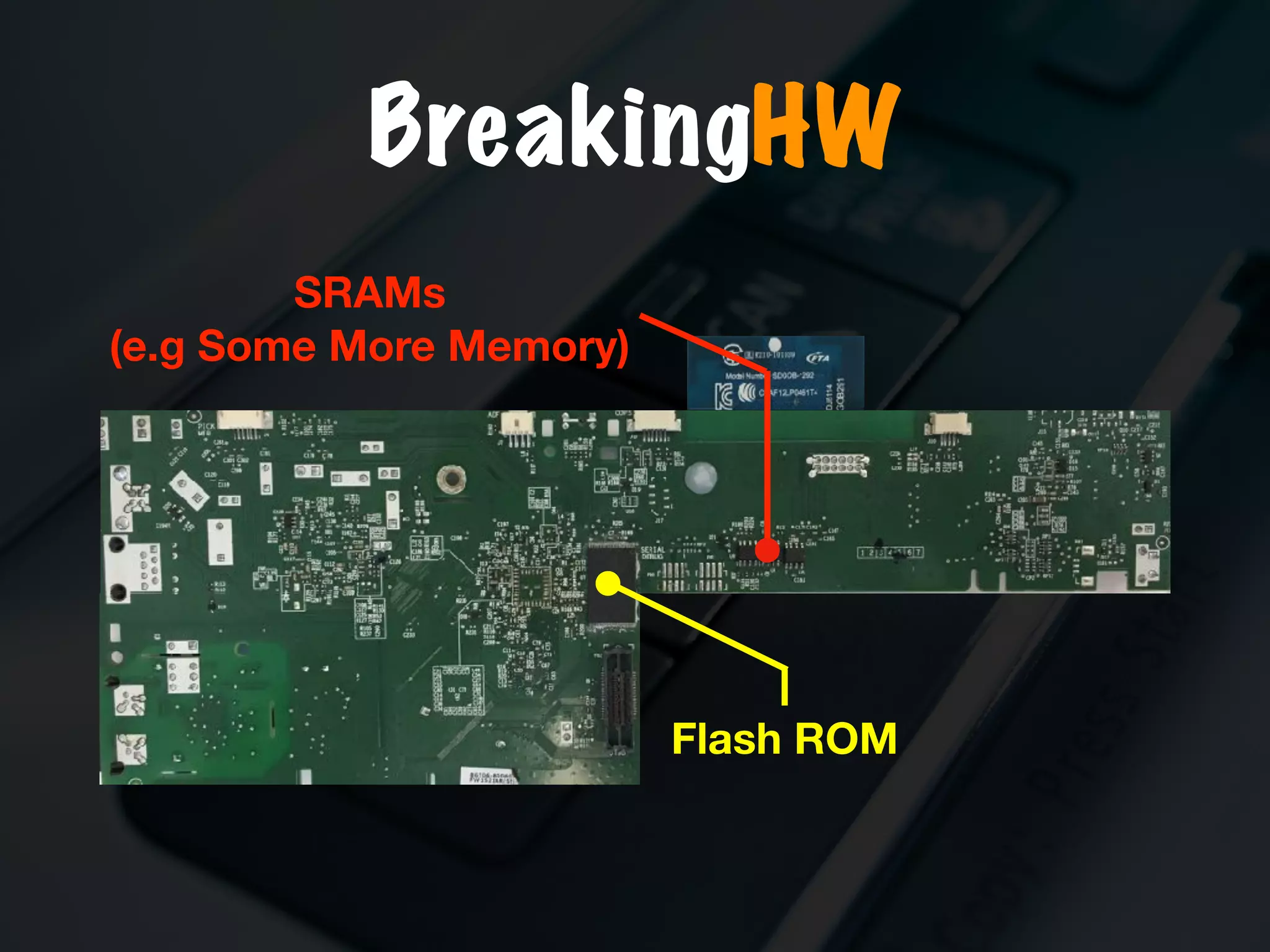
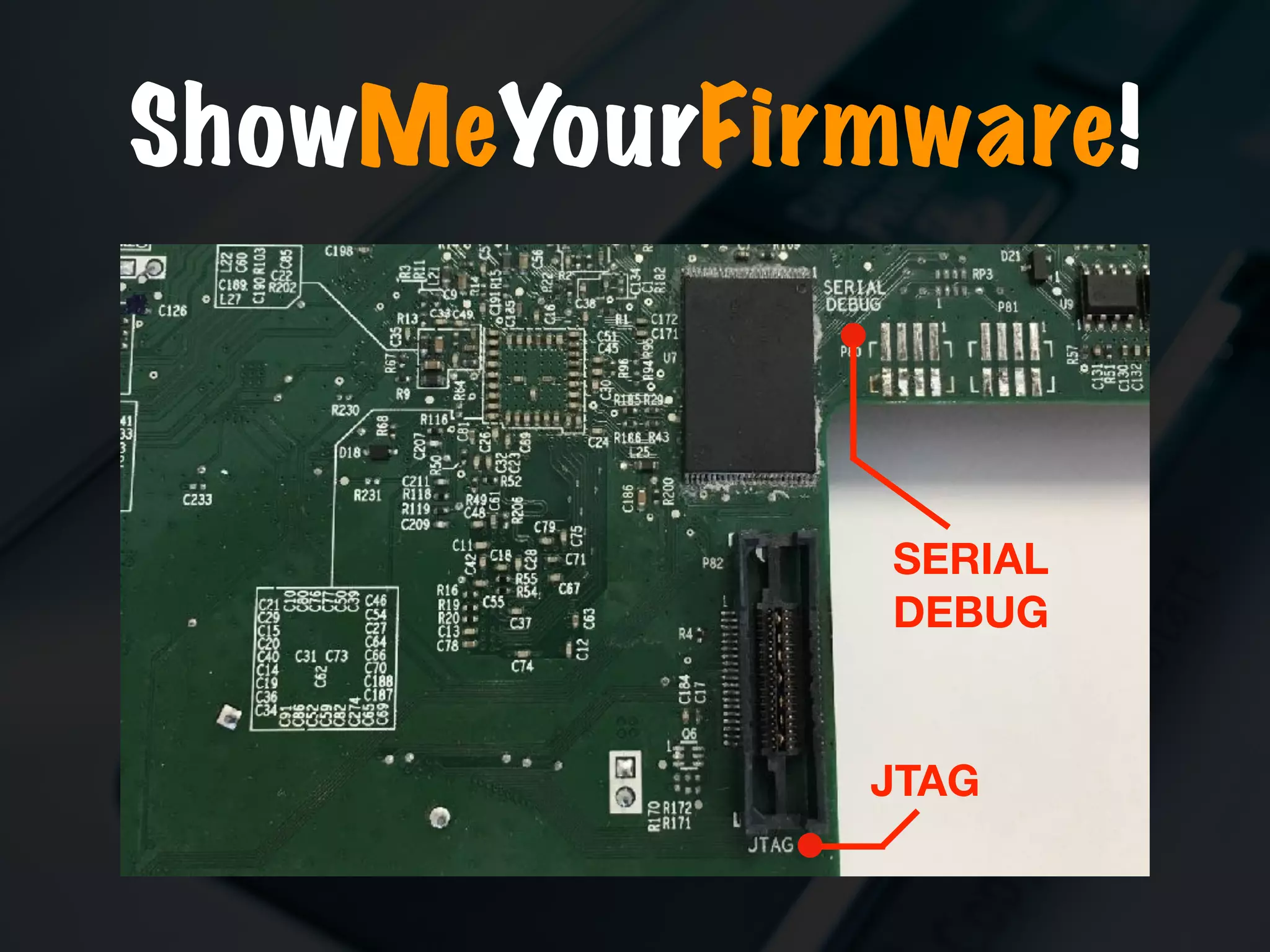
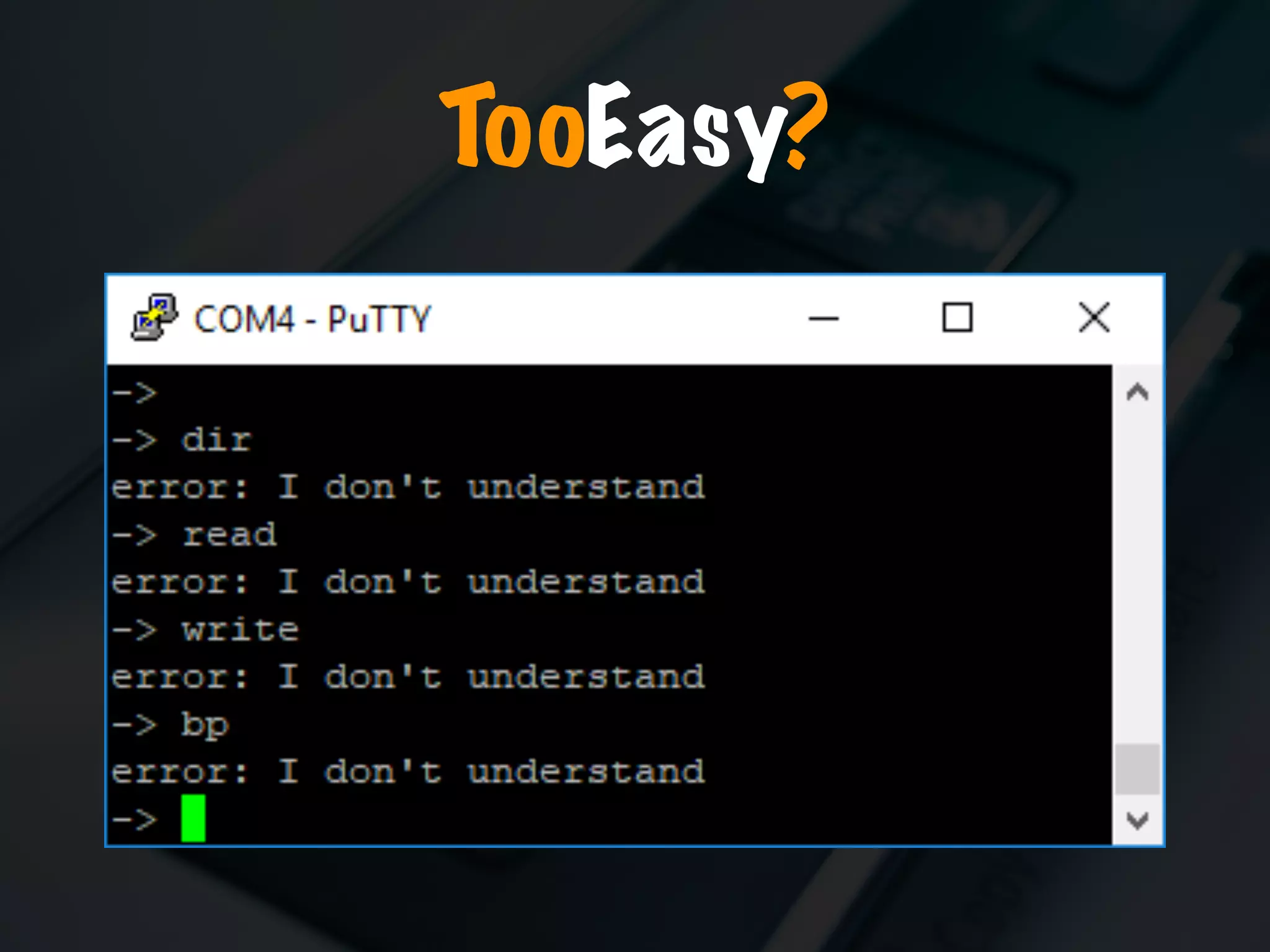
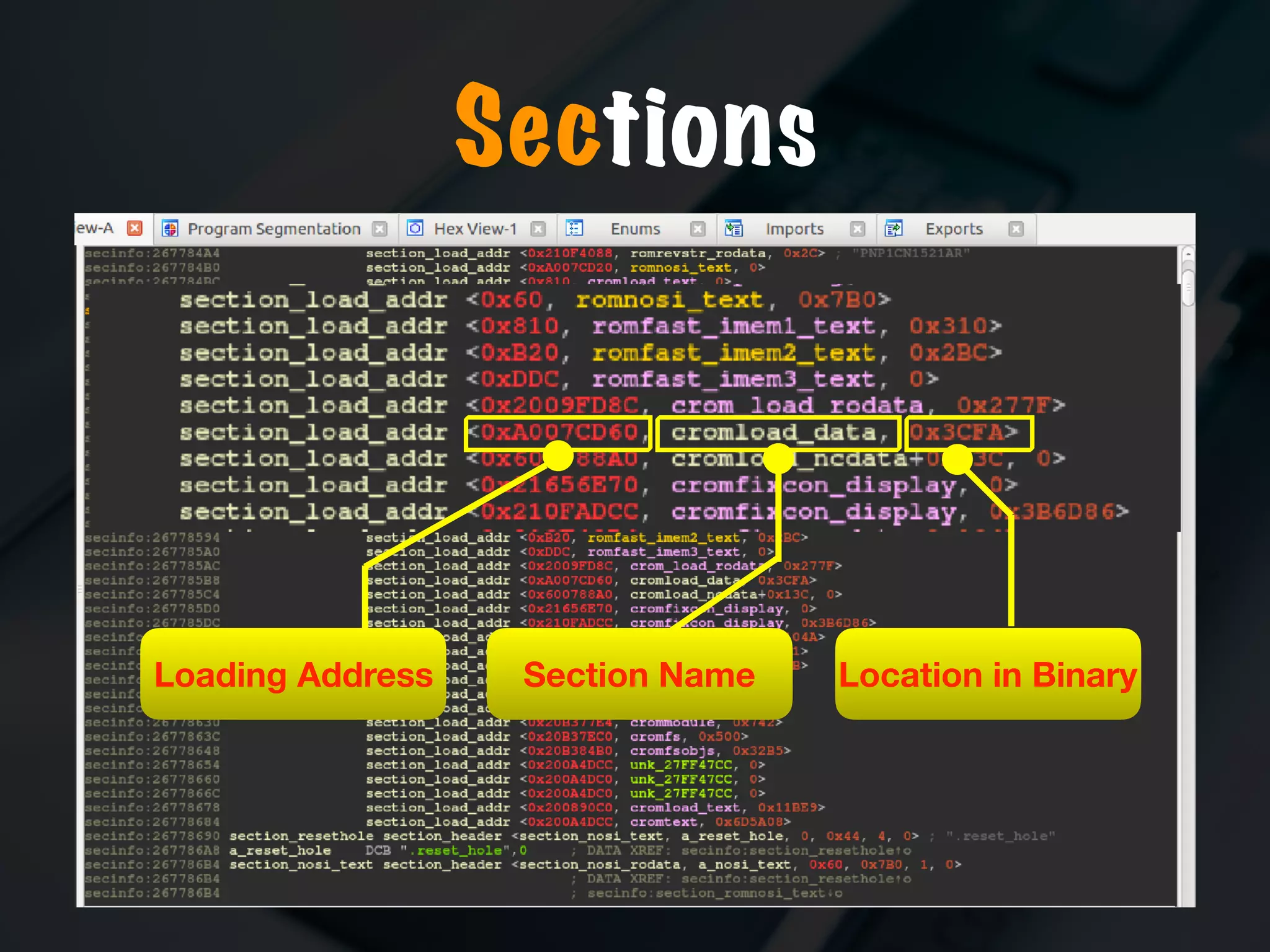
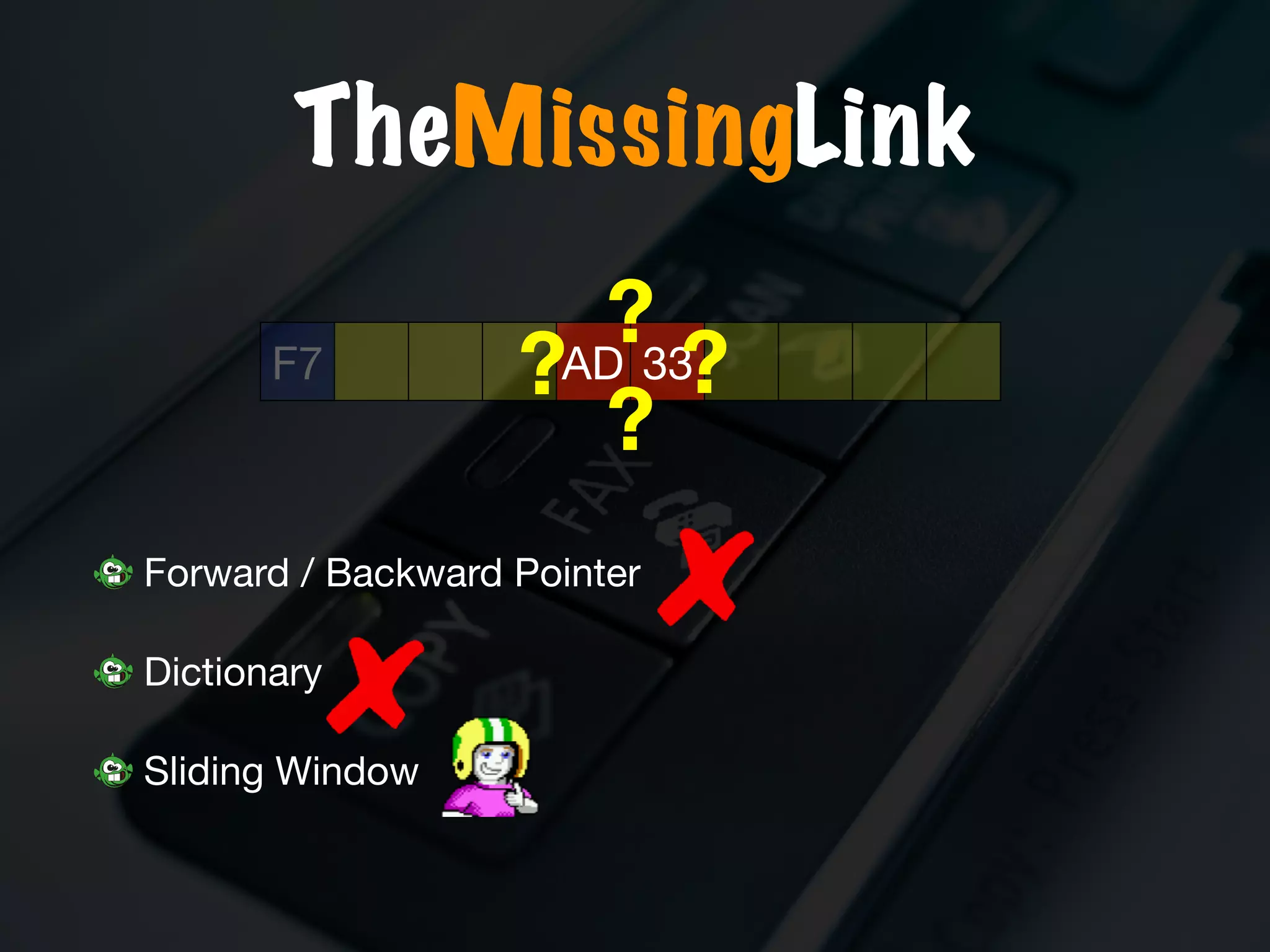
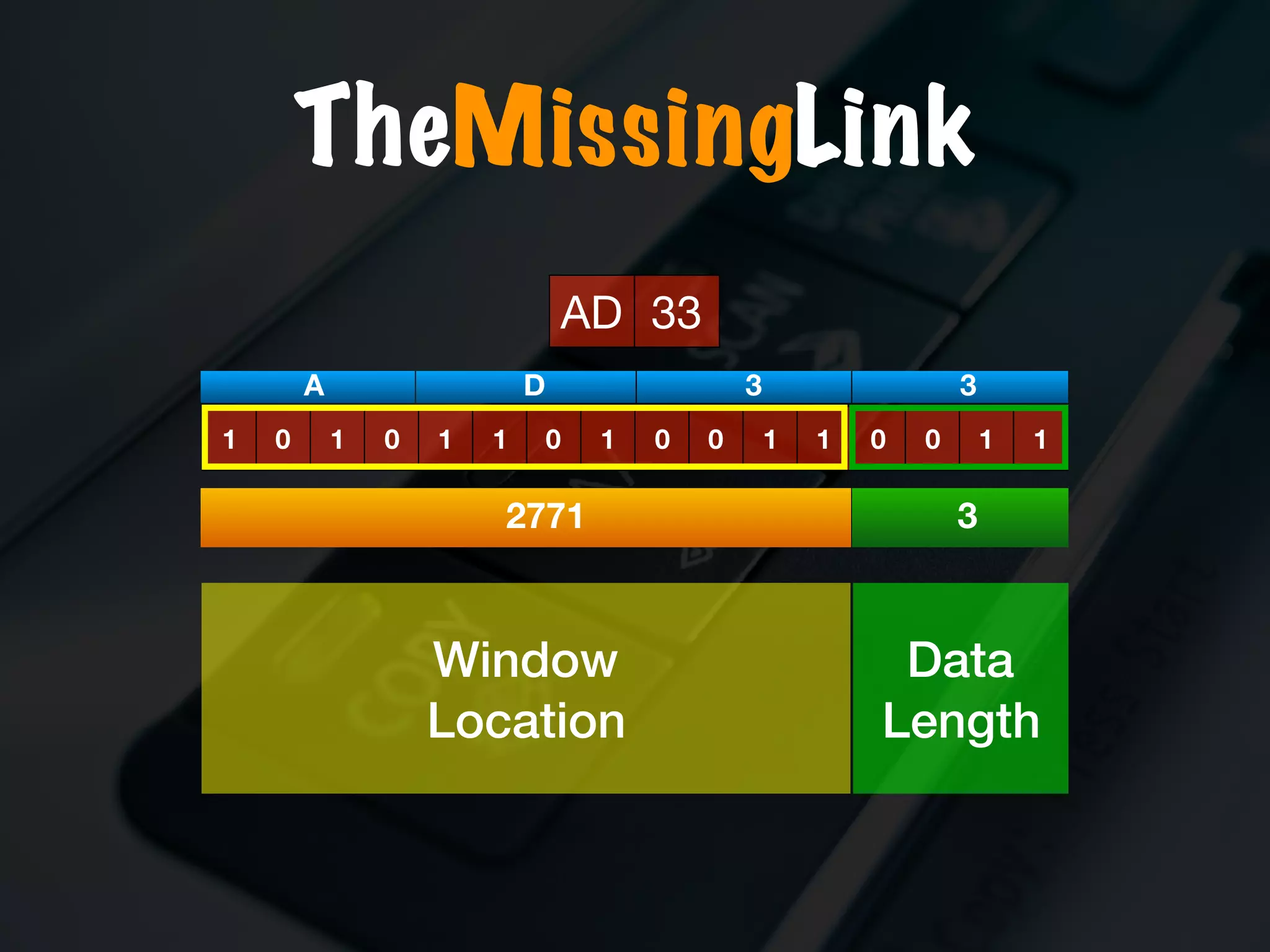
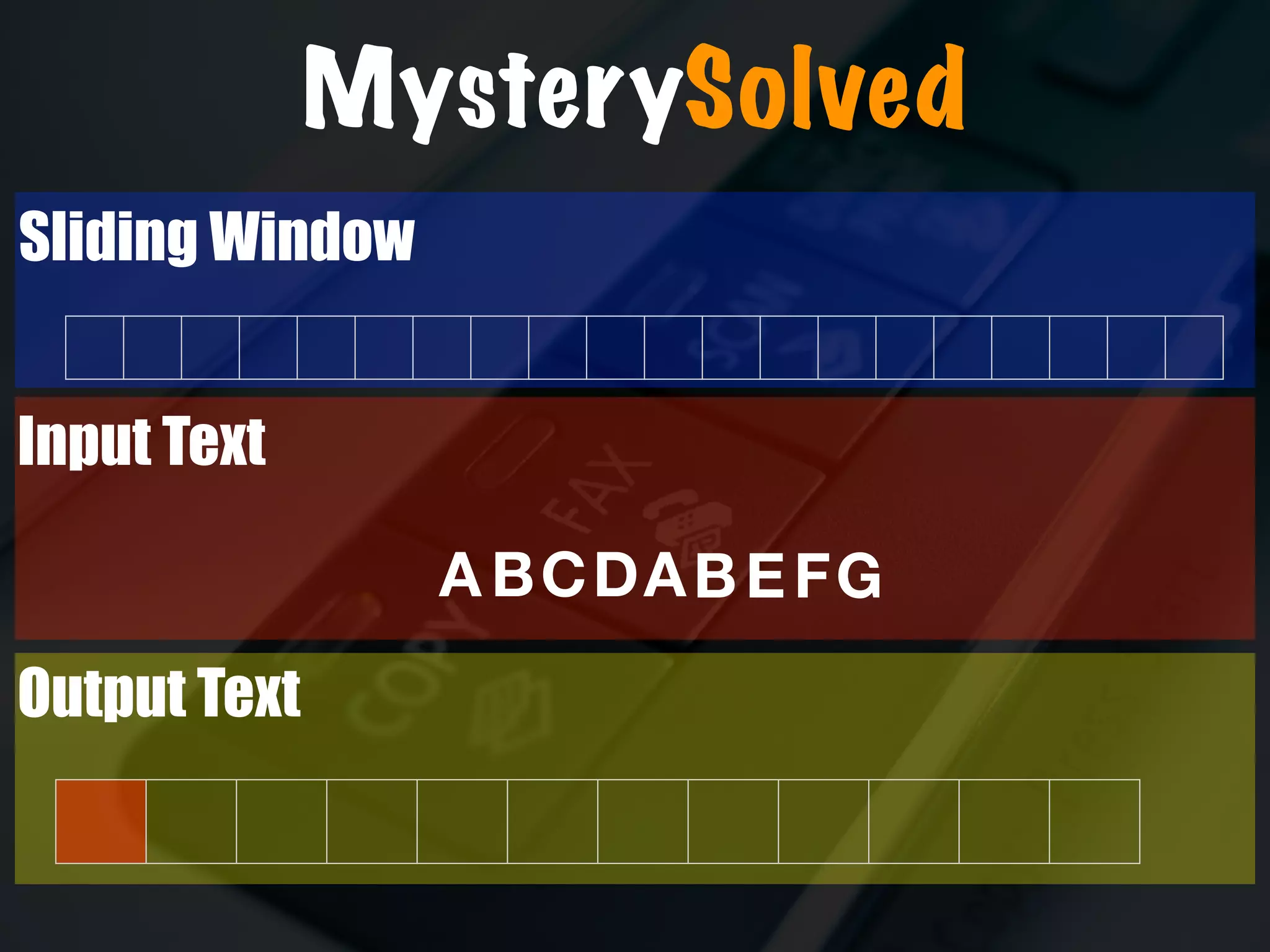
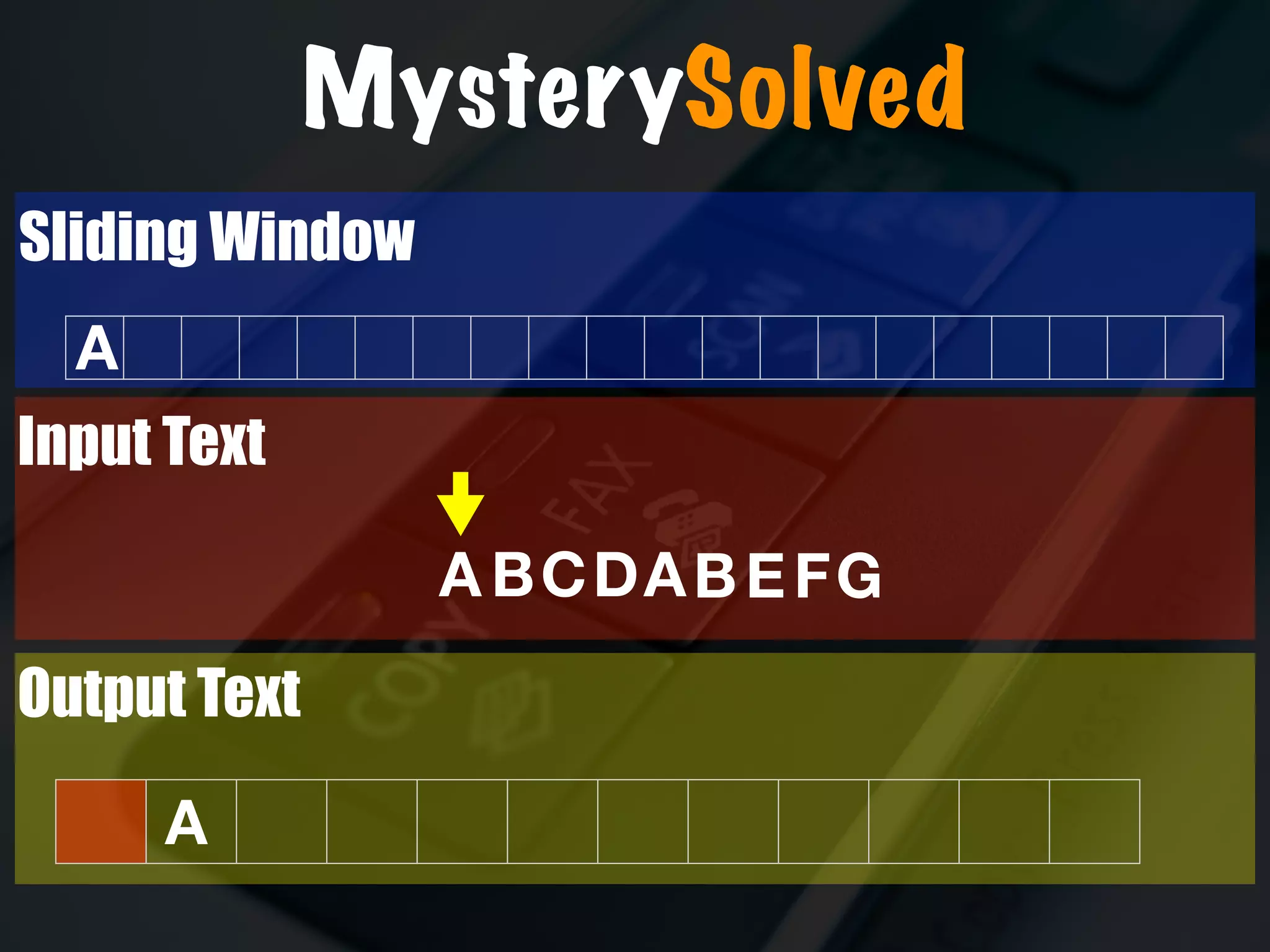
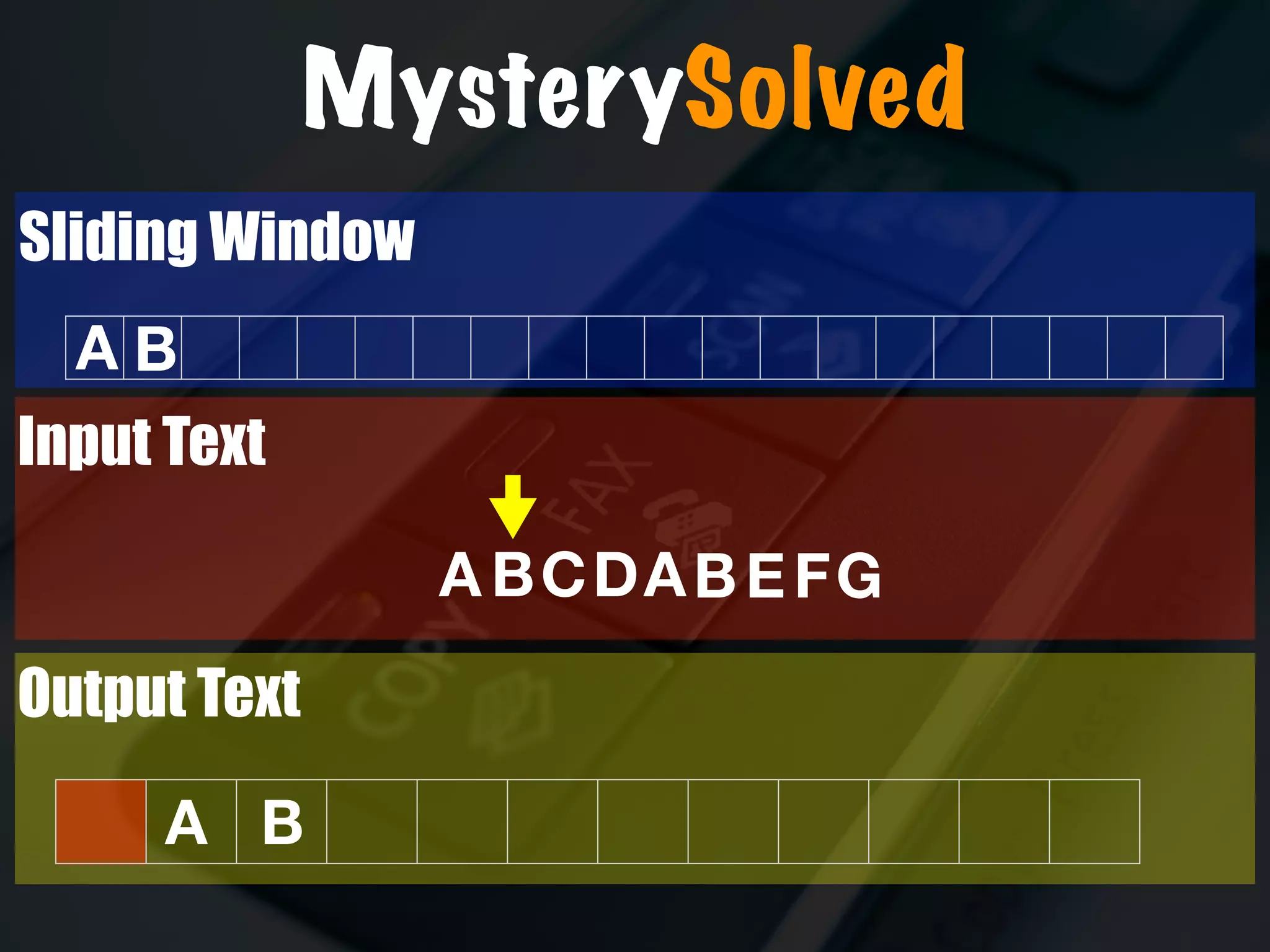
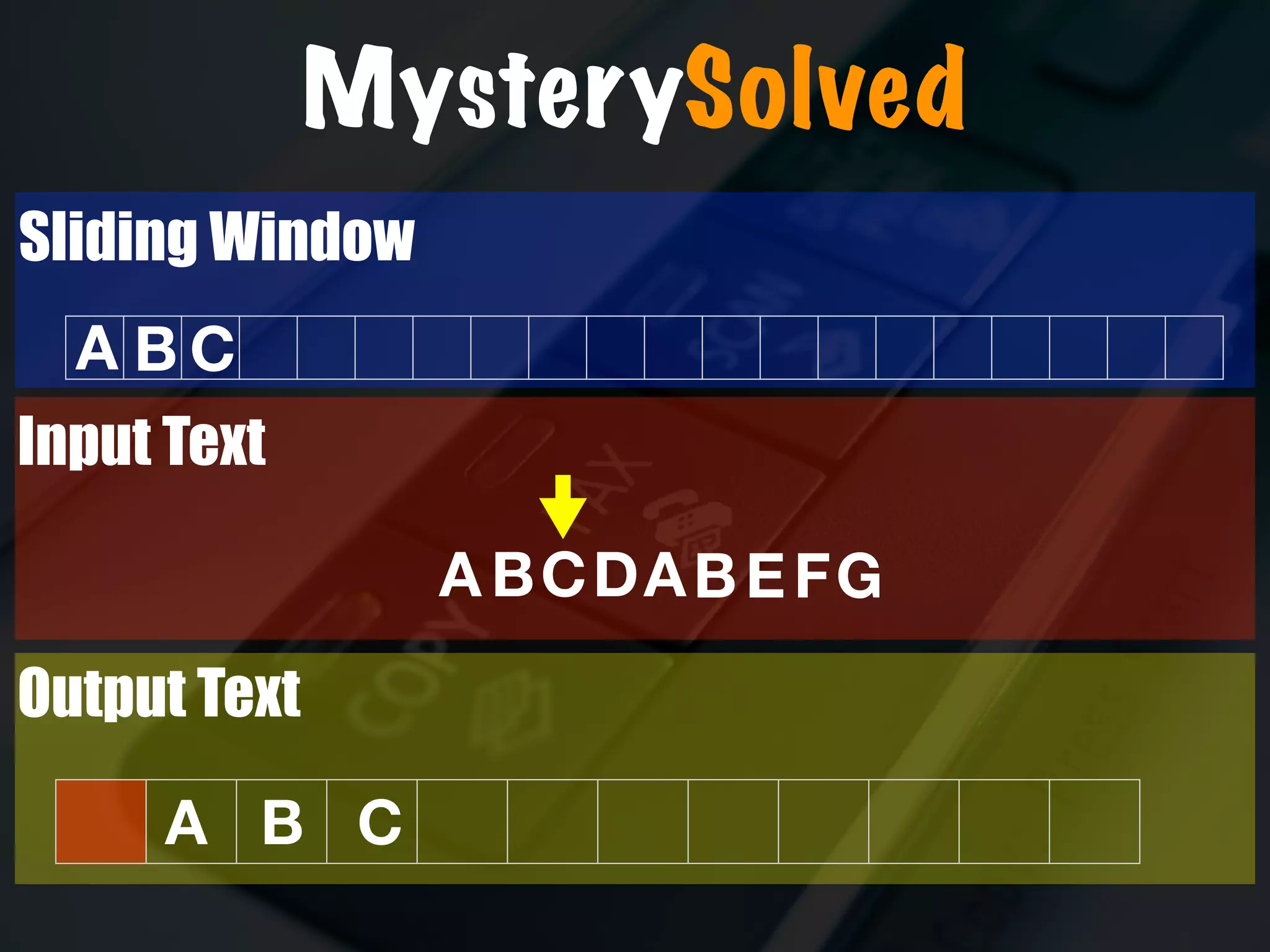
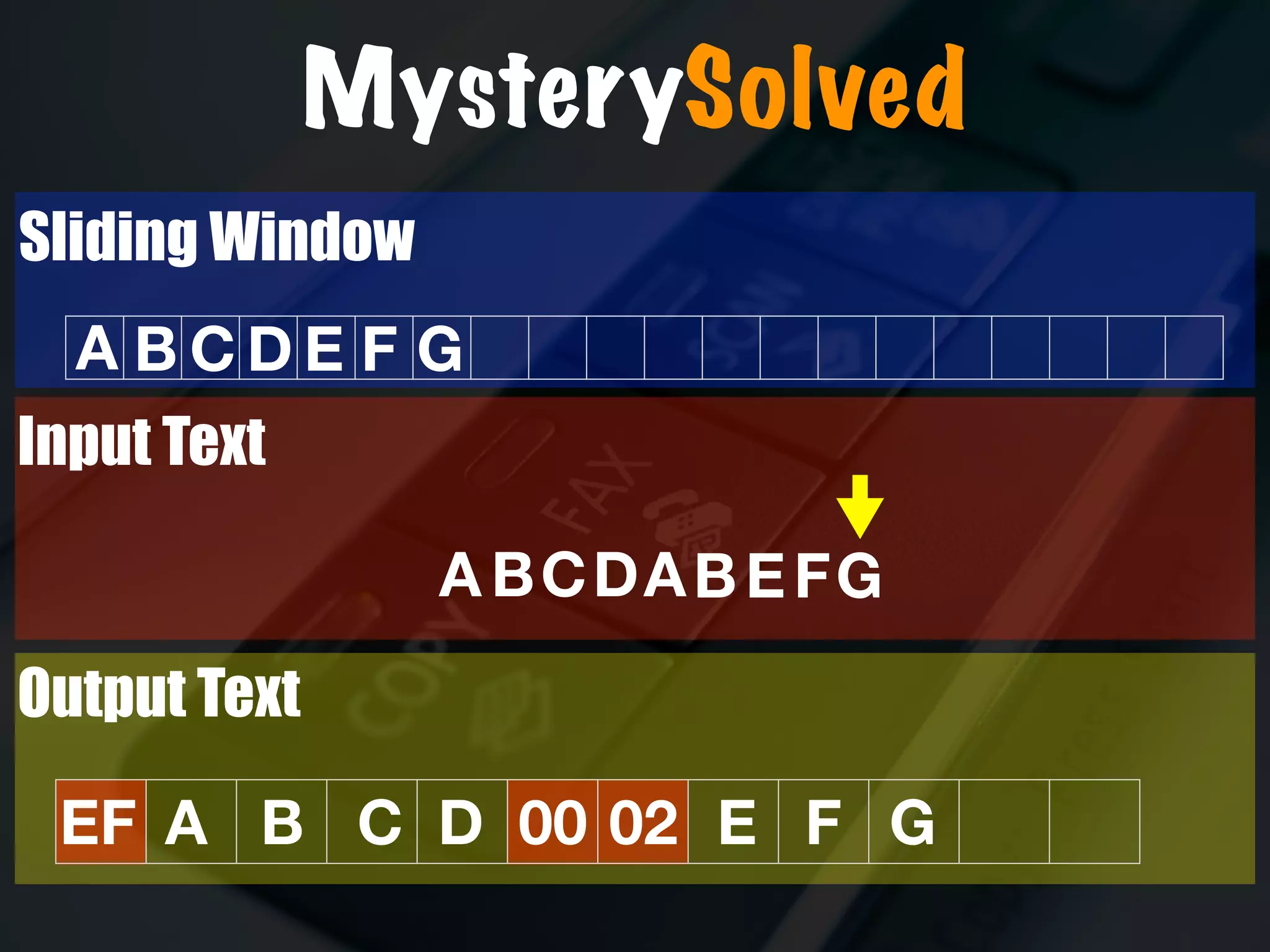
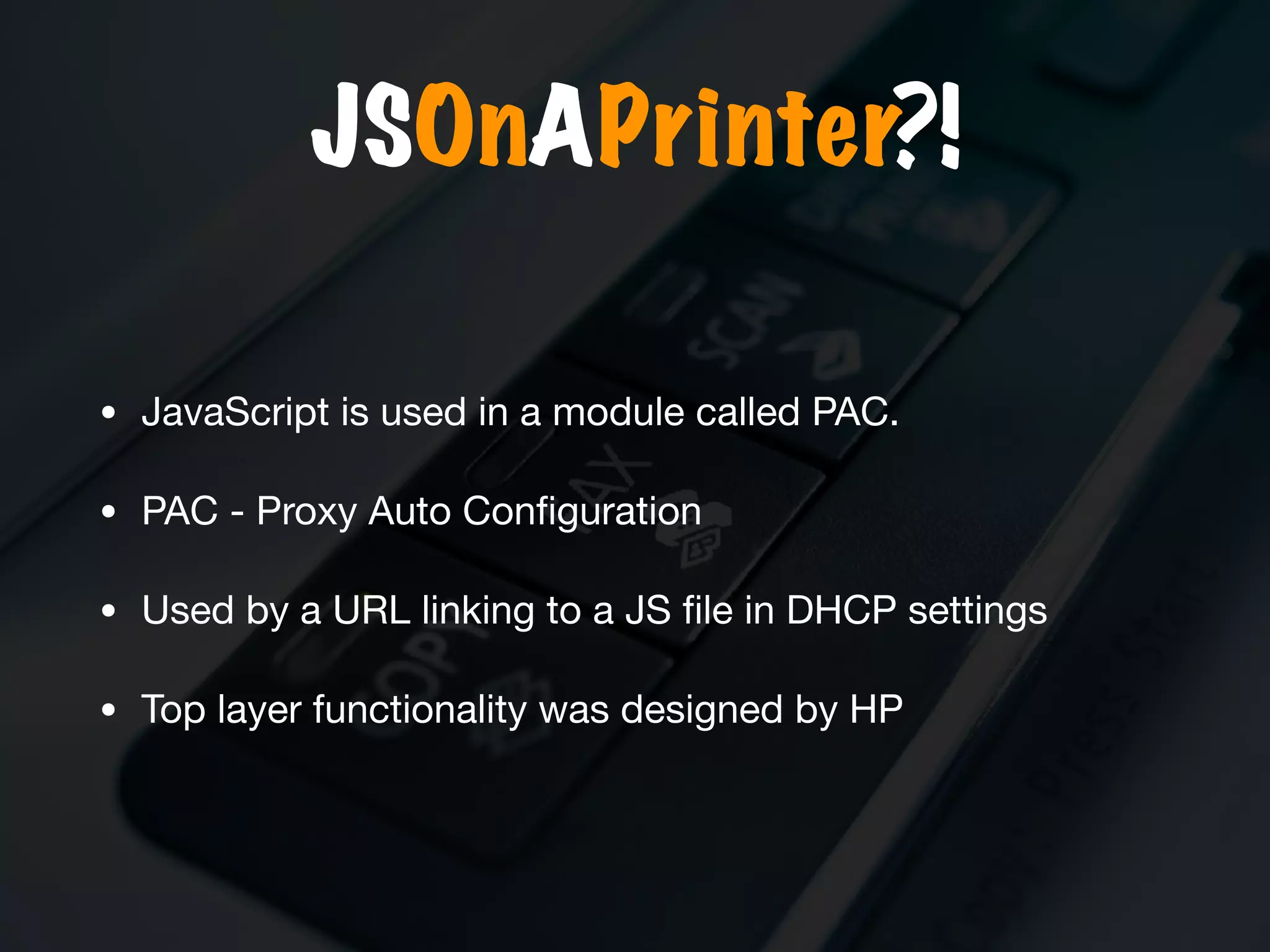
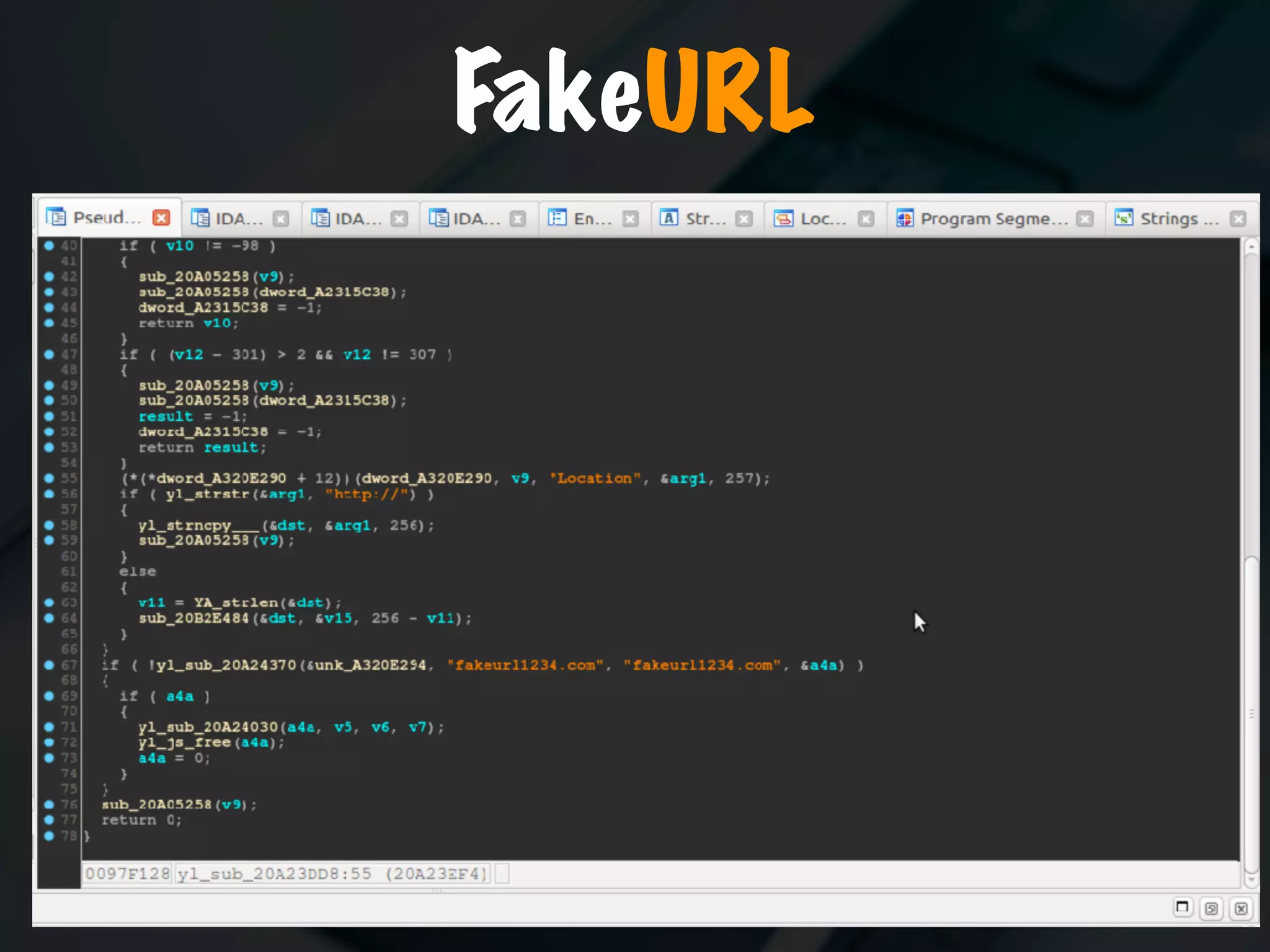
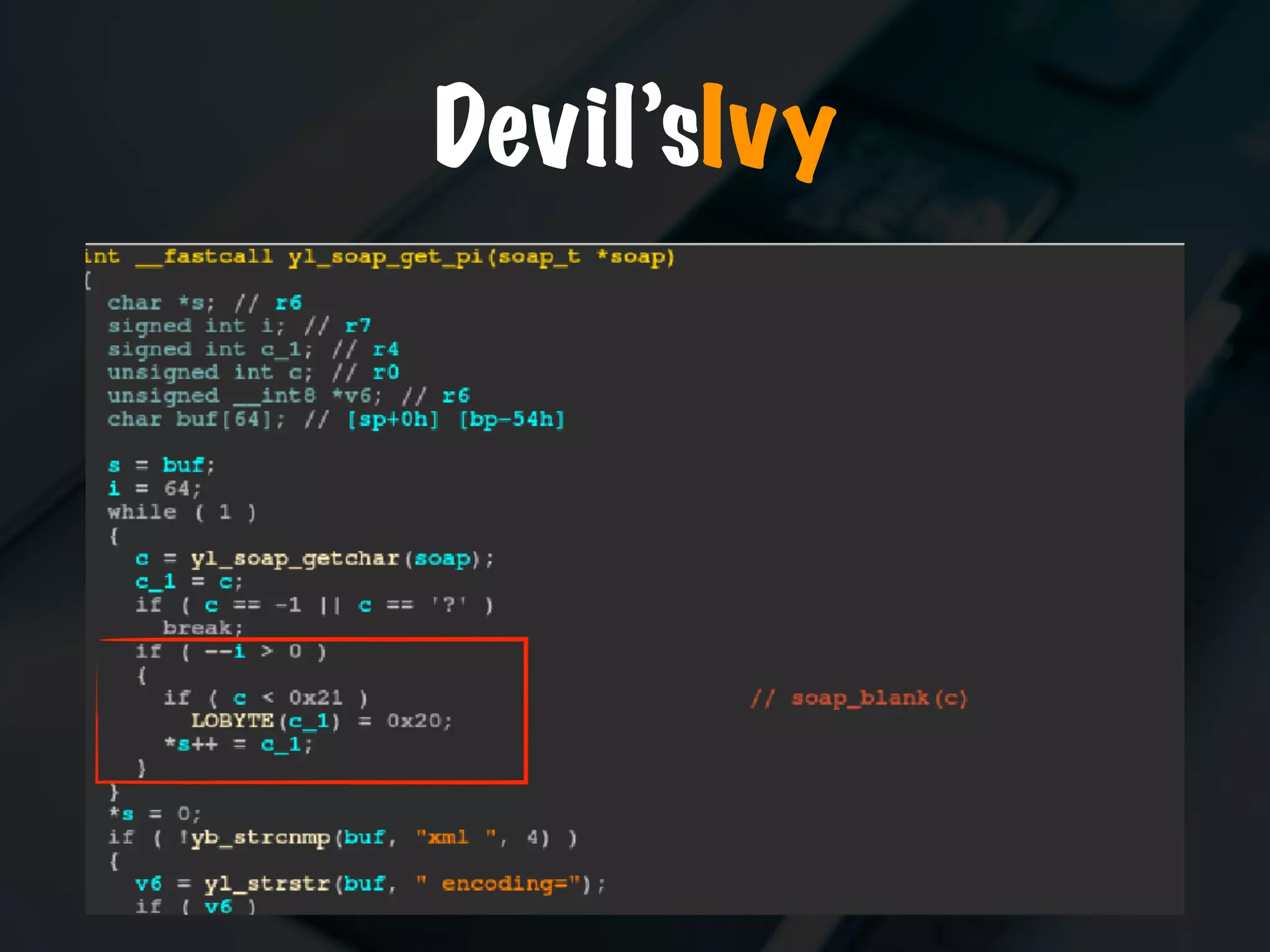
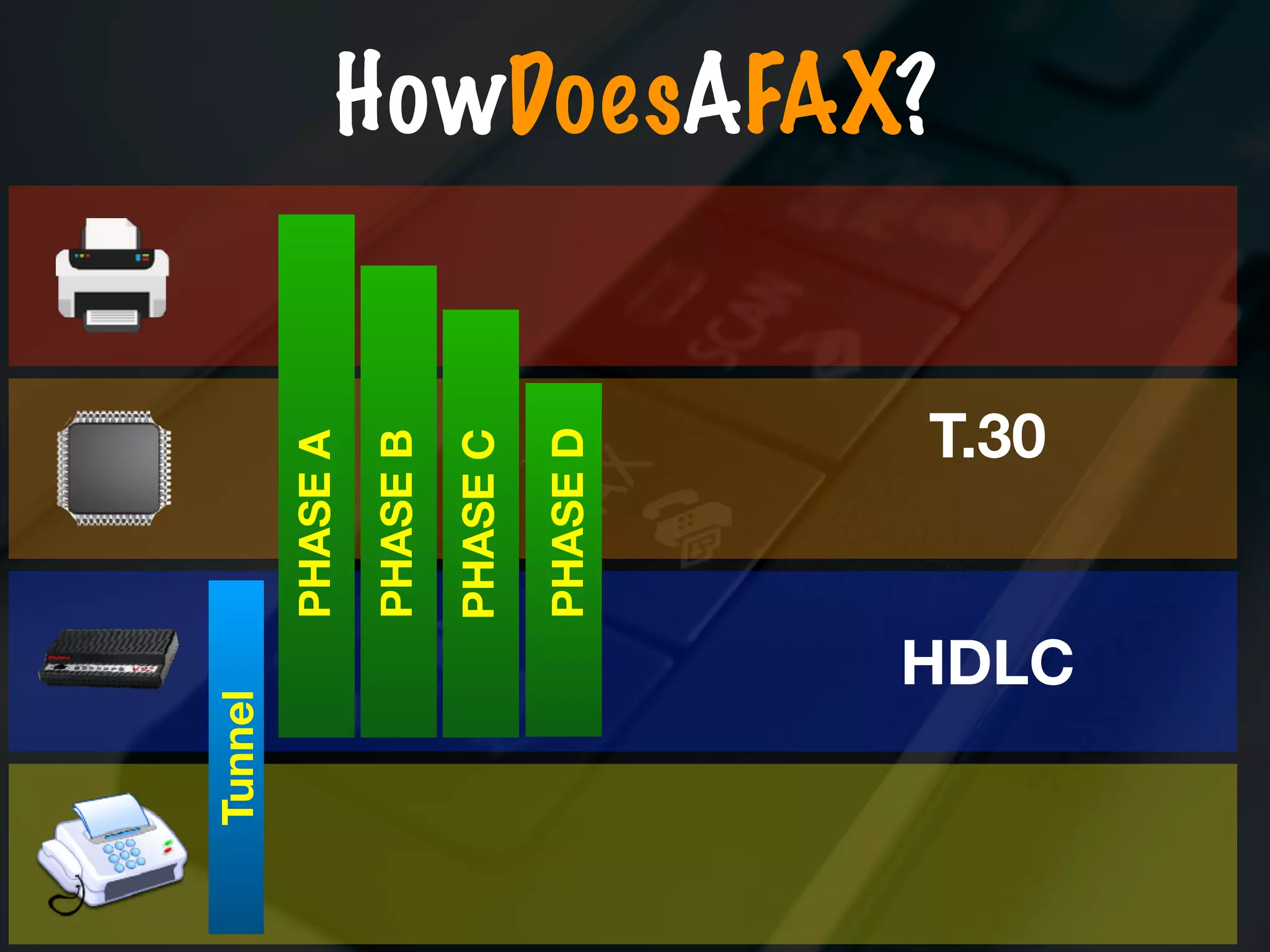
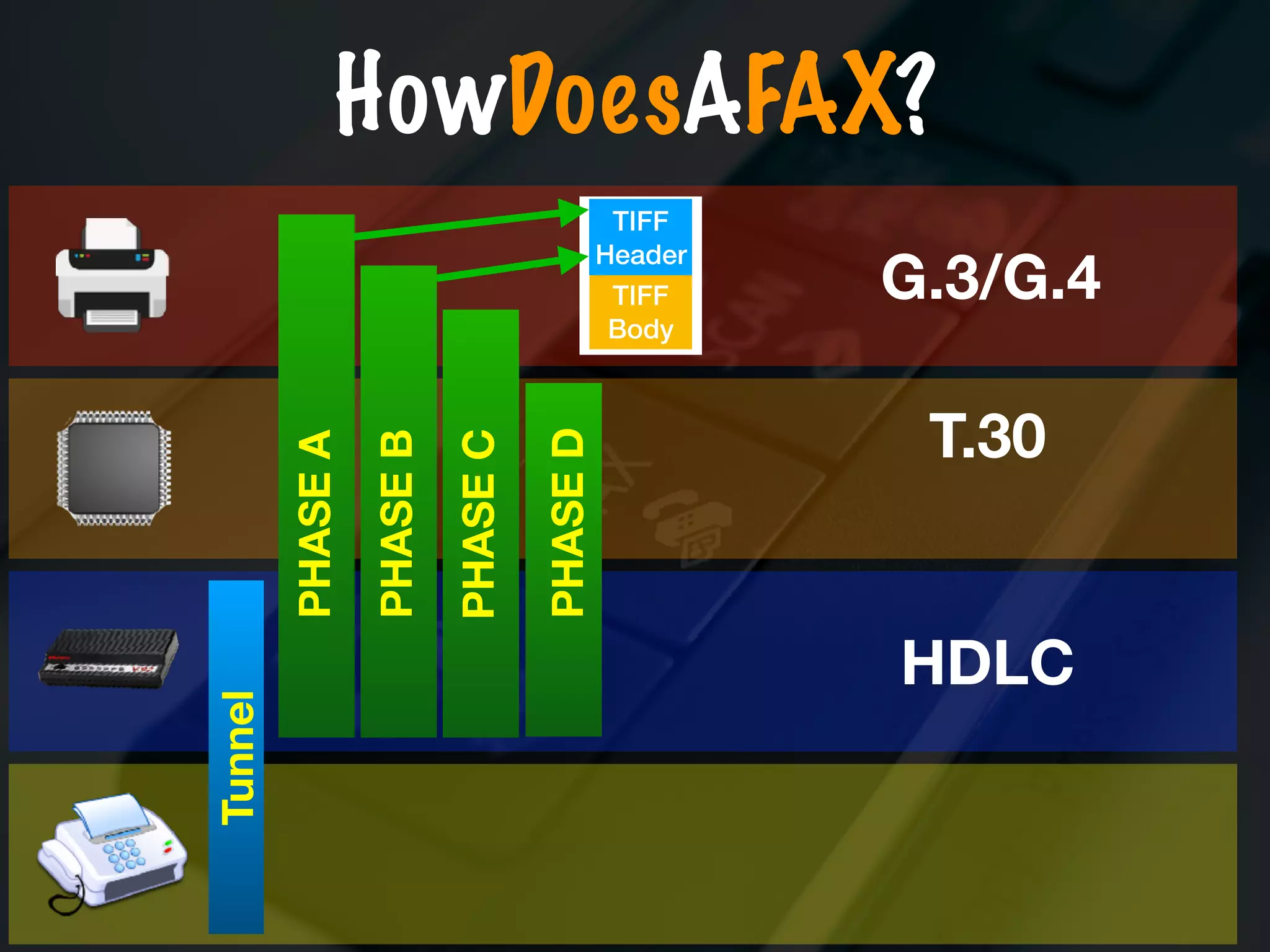
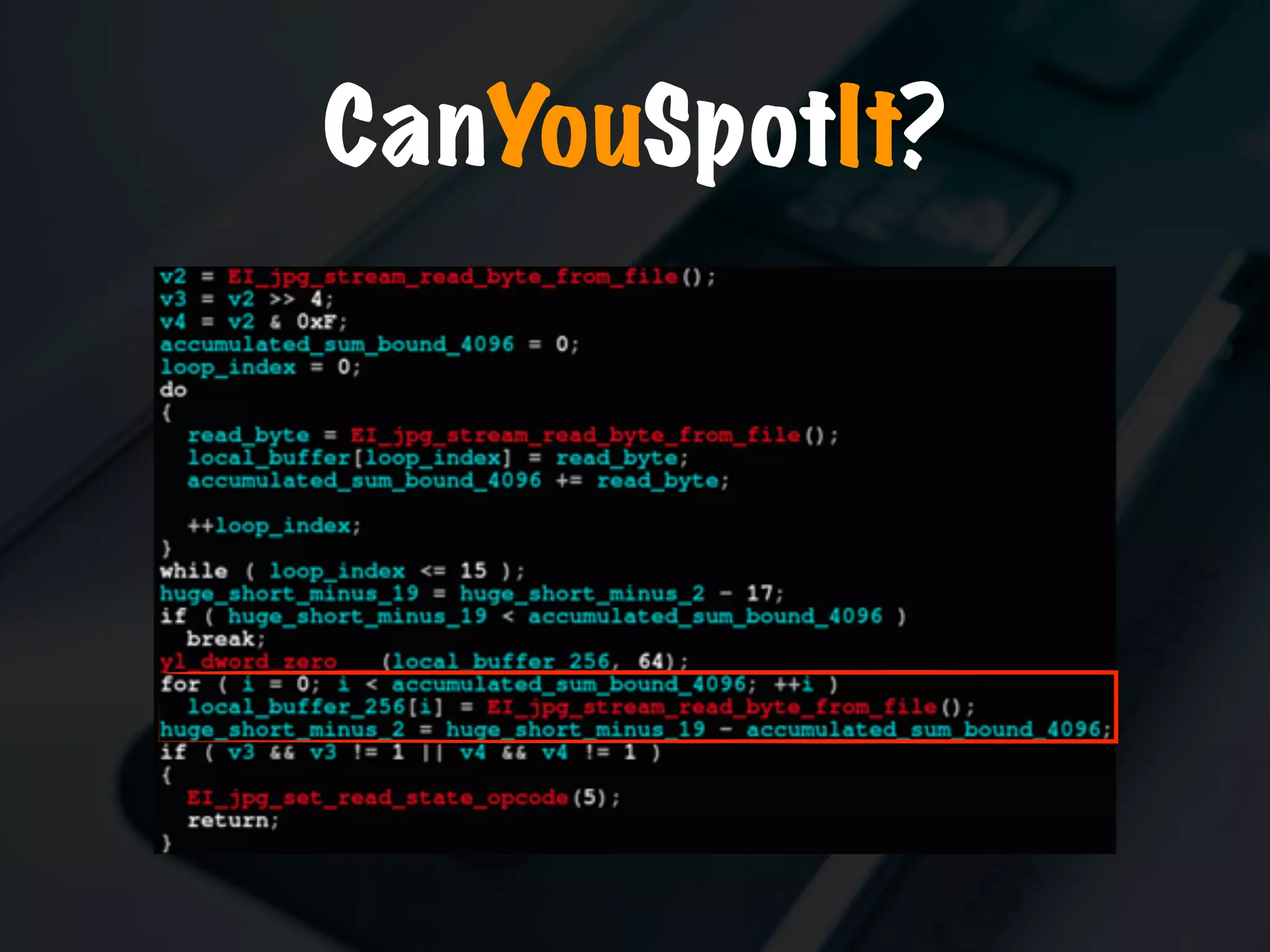
The document discusses the evolution and security vulnerabilities of fax technology, particularly emphasizing modern all-in-one printers that incorporate fax functionalities. It outlines various attacks, exploits, and debugging challenges related to these devices, highlighting a recent exploit named 'devil’s ivy' which affects certain printer models. The document concludes with recommendations for securing fax systems and contexts where they should still be avoided.