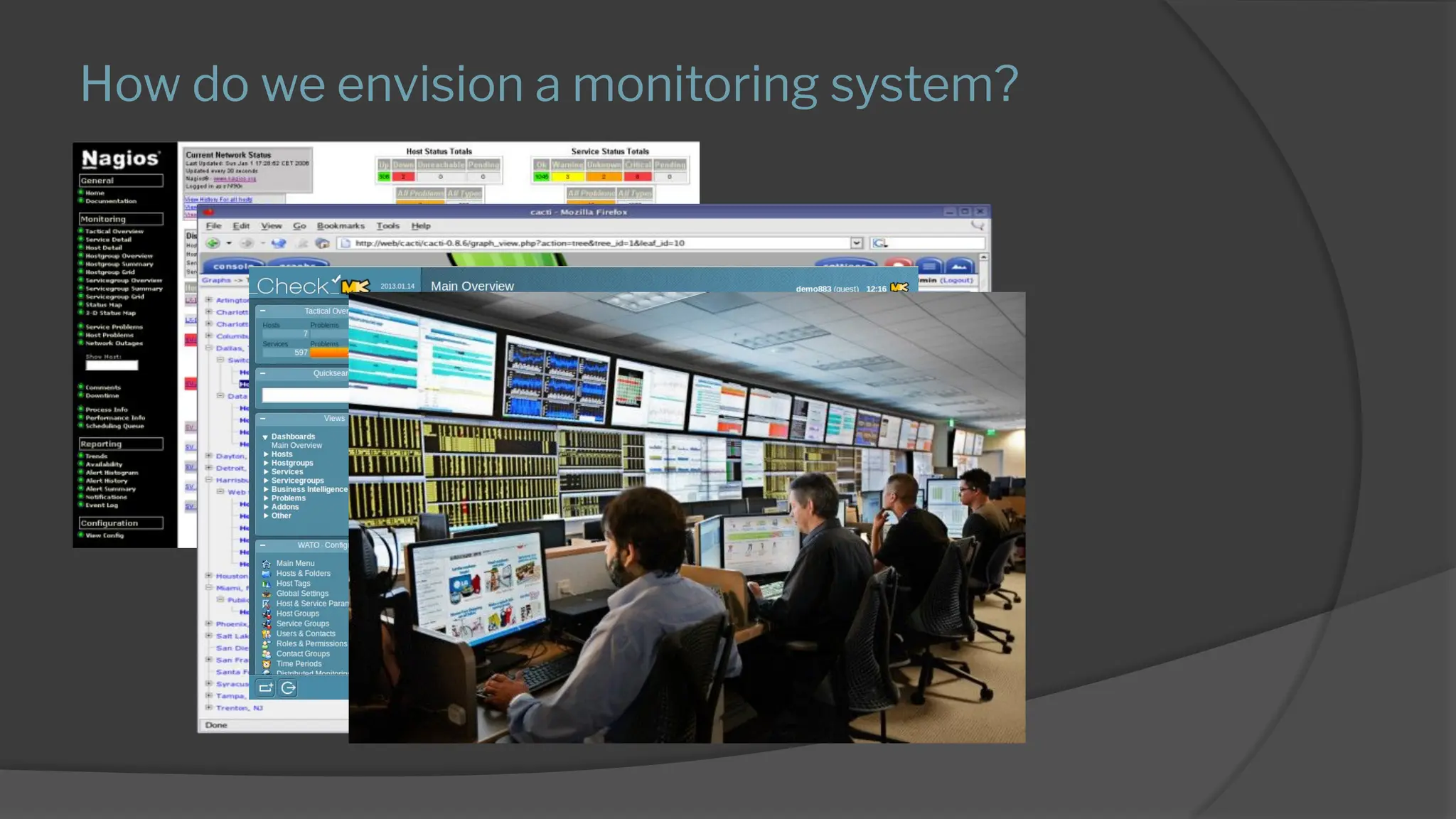
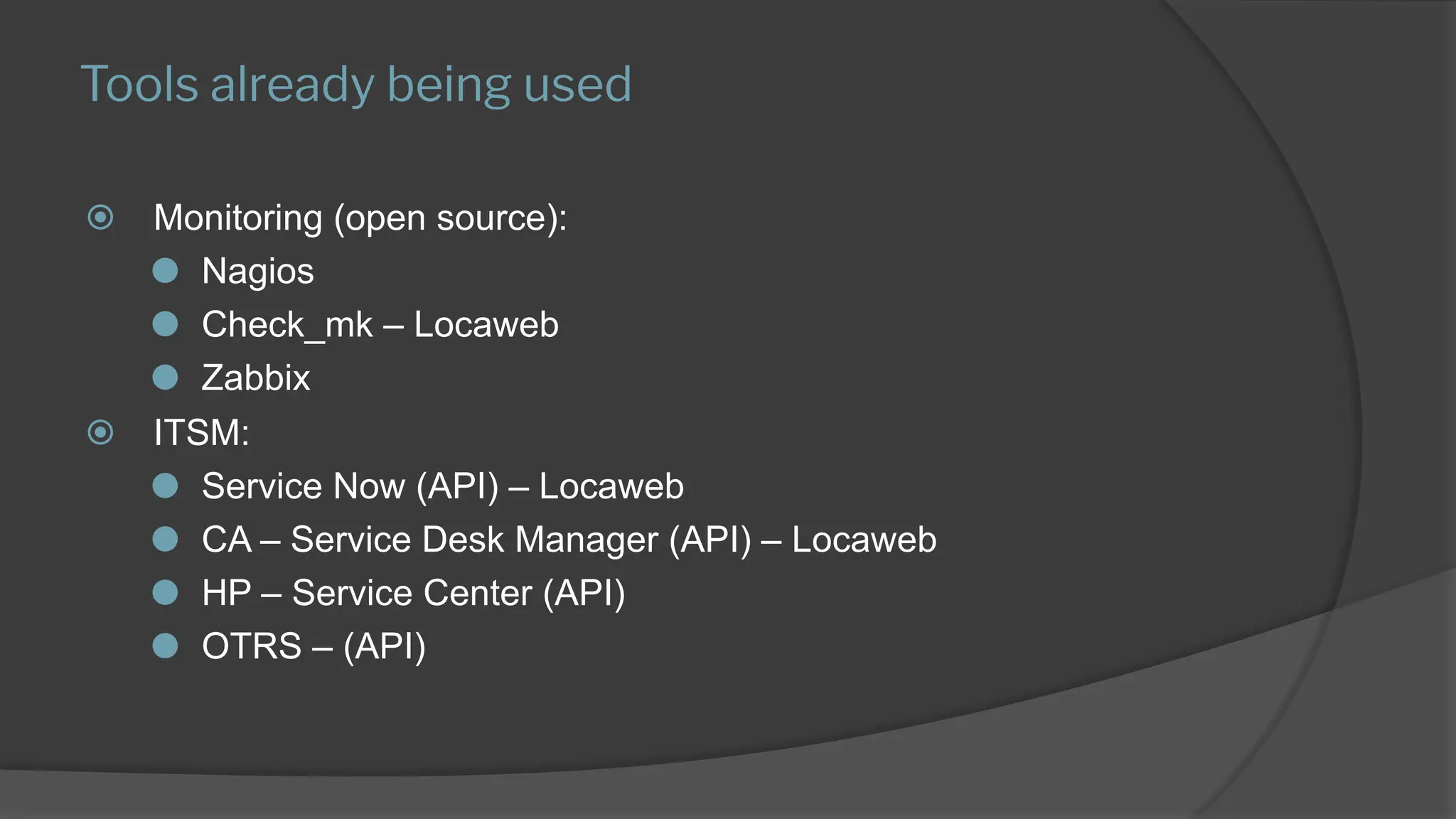
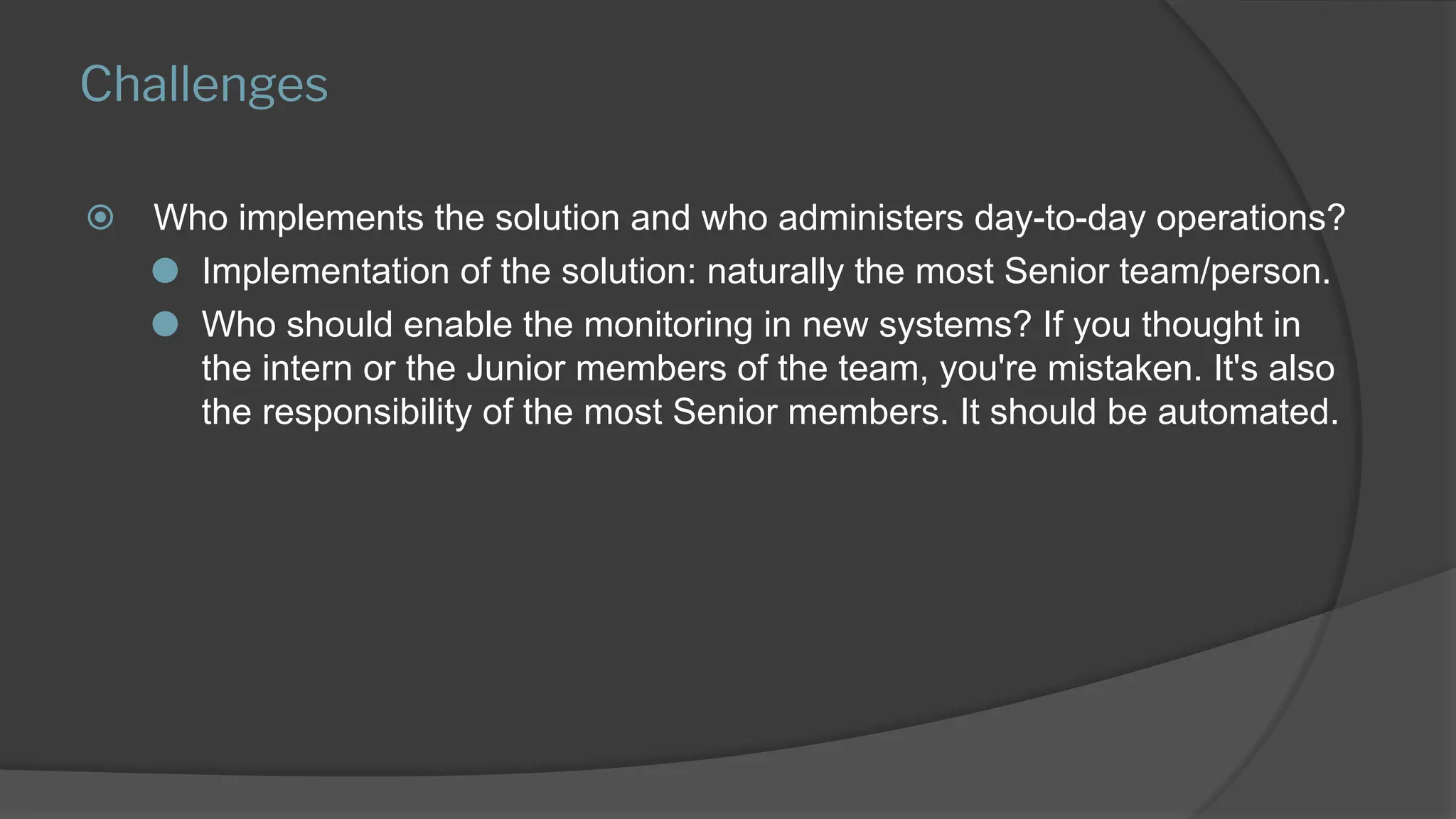
The presentation discusses the implementation of a comprehensive monitoring system that emphasizes best practices and process over tools, highlighting the importance of understanding resources, skills, and gradual implementation. It covers various aspects of monitoring, including what to track, configuration automation, and the benefits of ITIL and ITSM tools for automatic incident creation. Key challenges include managing false positives, ensuring effective processes, and the need for experienced team members to drive implementation and automation.