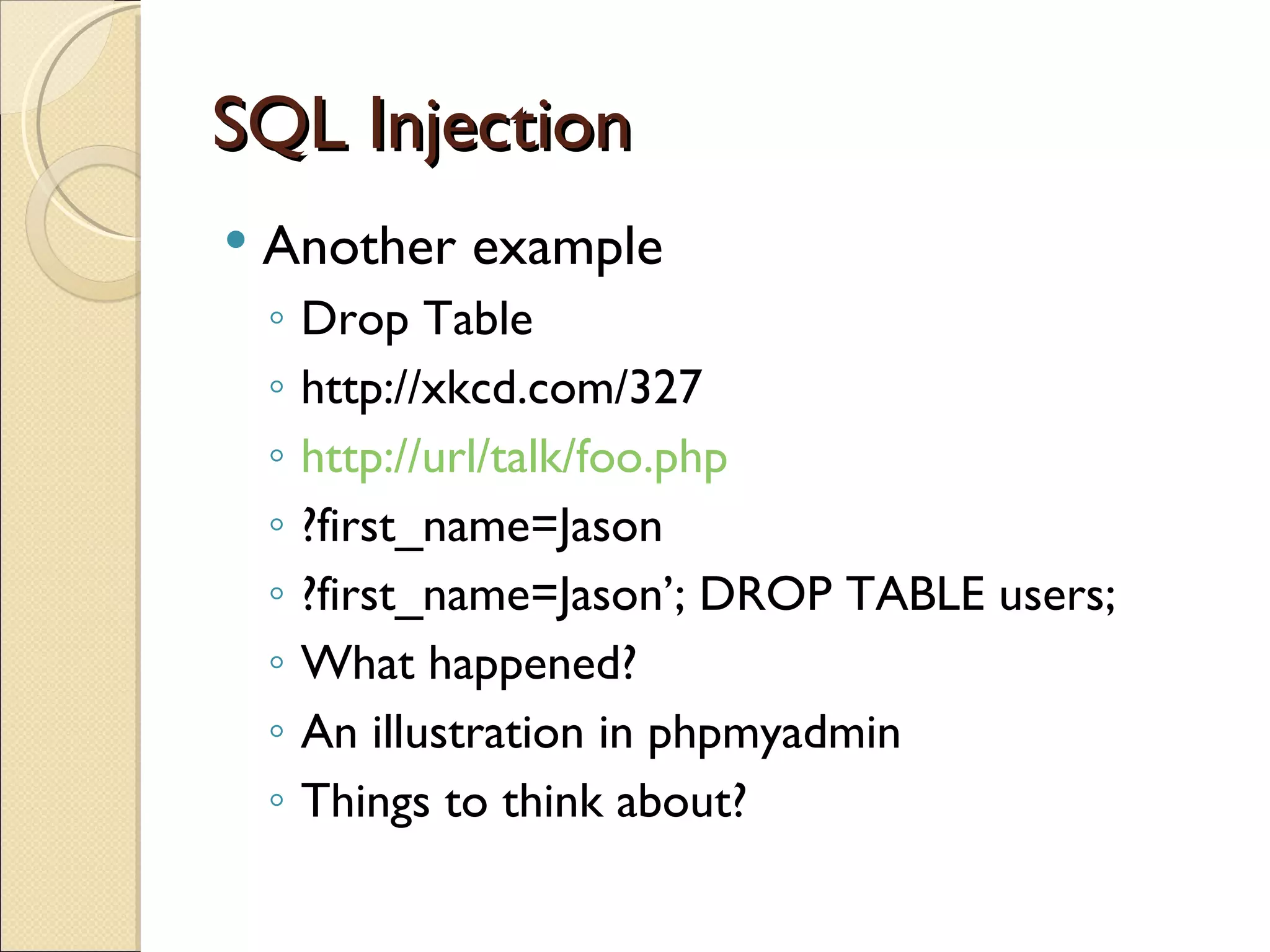
The document discusses various security concerns for web applications including SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It provides examples of each vulnerability and emphasizes the importance of filtering input, escaping output, and reducing database user privileges to help prevent security issues.