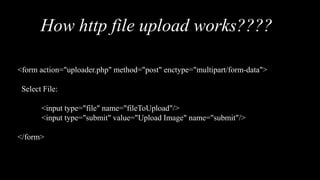
The document discusses the insecure file upload vulnerability, detailing how it works and providing an example of an HTTP file upload form. It includes references for further reading on exploiting file upload vulnerabilities and showcases the author's background as a pentester and security enthusiast. The document also features links to the author's social media profiles.