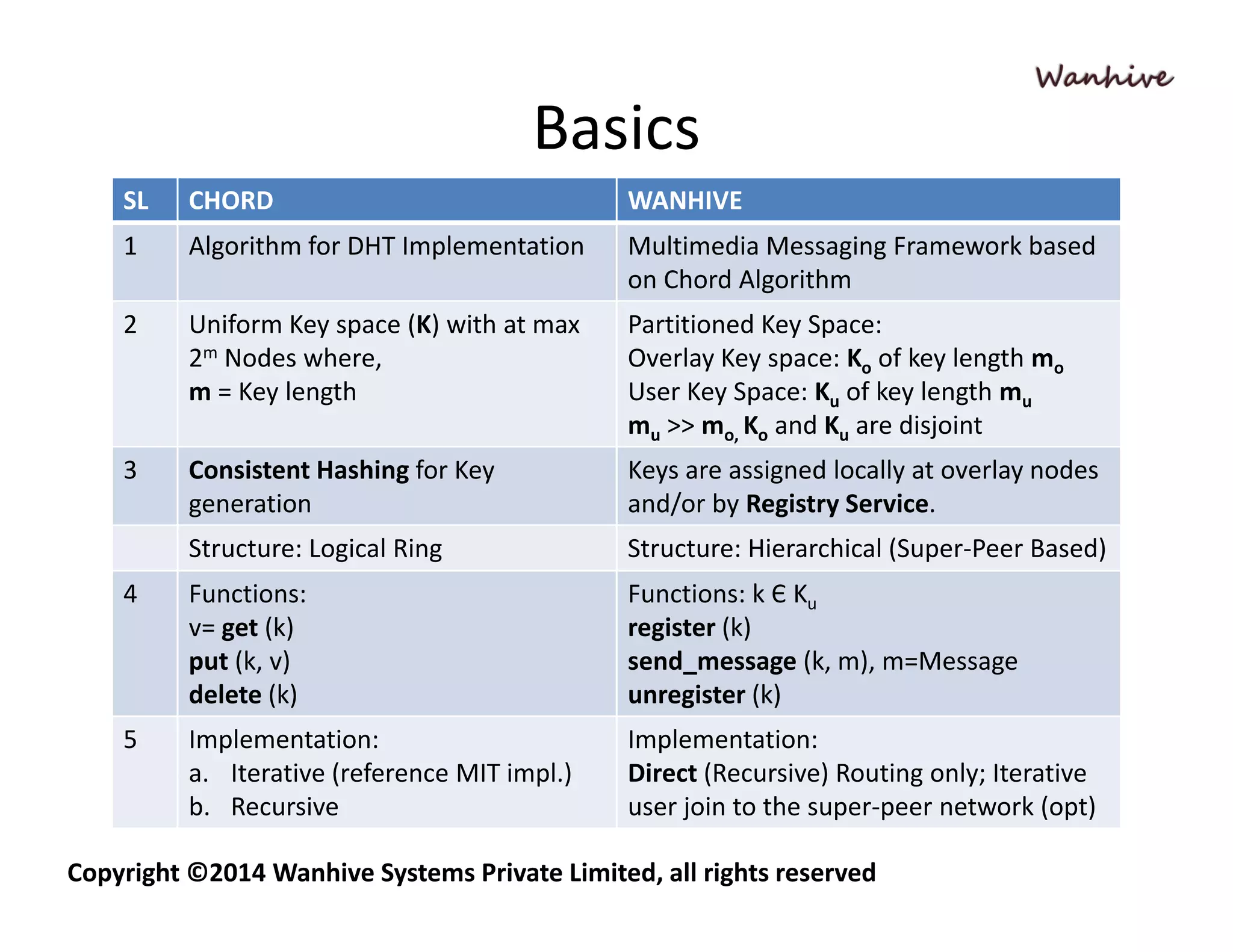
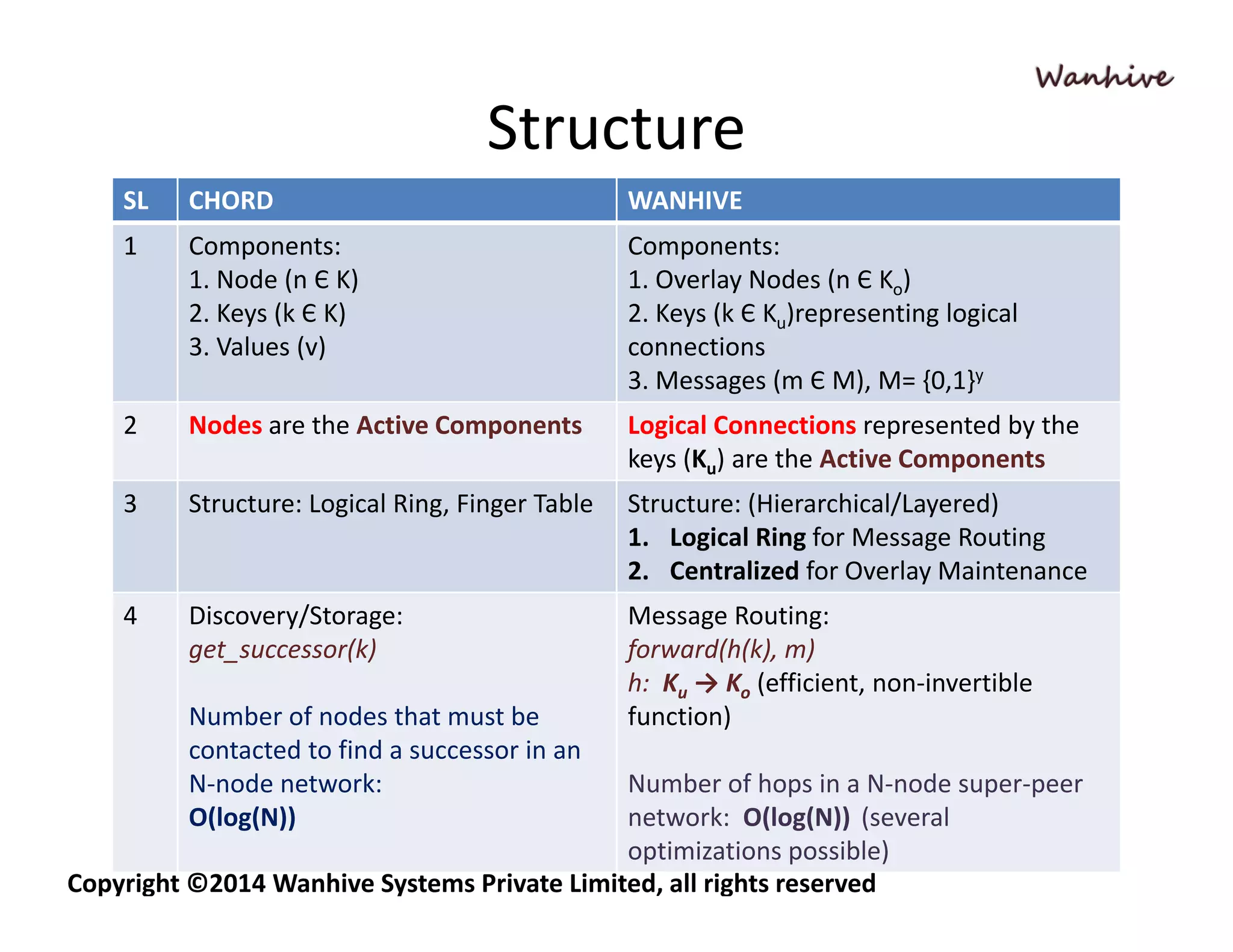
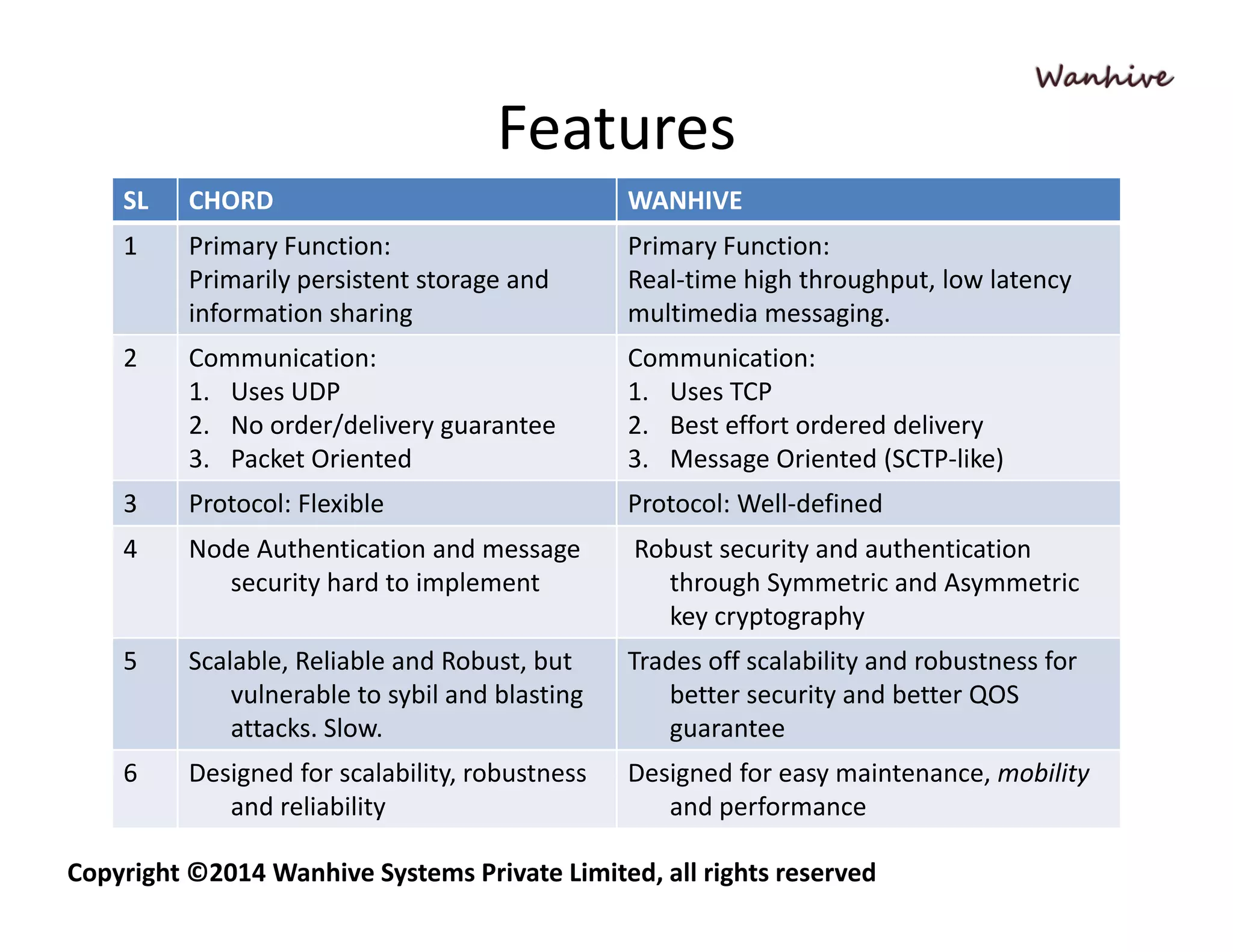
Wanhive vs CHORD is a comparative analysis of two distributed hash table (DHT) implementations - CHORD and Wanhive. CHORD uses a consistent hashing algorithm to map keys to nodes in a distributed logical ring structure for persistent storage and retrieval. Wanhive is a hierarchical, super-peer based architecture designed for real-time multimedia messaging with better security, quality of service guarantees, and ease of maintenance compared to CHORD which is more focused on scalability, robustness, and reliability. The document outlines key differences in the algorithms, structures, features, and research areas of the two DHT approaches.


![That’s it, Thank you
Author: Amit Kumar at Wanhive Systems Private Limited, Patna Bihar (India) 800024. EMAIL:
amit[*AT*]wanhive.com
Copyright ©2014 Wanhive Systems Private Limited, all rights reserved](https://image.slidesharecdn.com/wanhivevschord-140923095634-phpapp02/75/Wanhive-vs-Chord-Distributed-Hash-Table-6-2048.jpg)