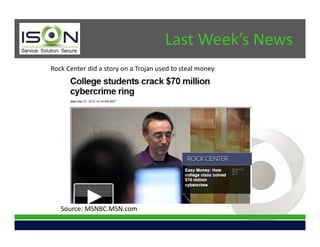
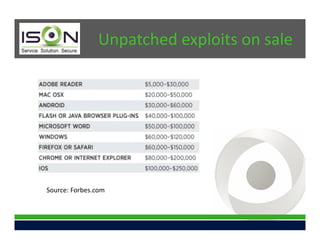
This document summarizes a presentation on effective cybersecurity. It discusses continuing trends in threats like control system attacks and money-stealing Trojans being reported on news programs. Identity information and exploits are being sold online. New threats include internal attacks, social media risks for small businesses, and new spam vectors posing as legitimate companies. The presentation addresses defensive techniques like penetration testing, security awareness training, and compliance practices. It introduces ISON as a managed IT services firm focused on small and medium businesses, providing security solutions to help organizations address these challenges.