Embed presentation
Download to read offline
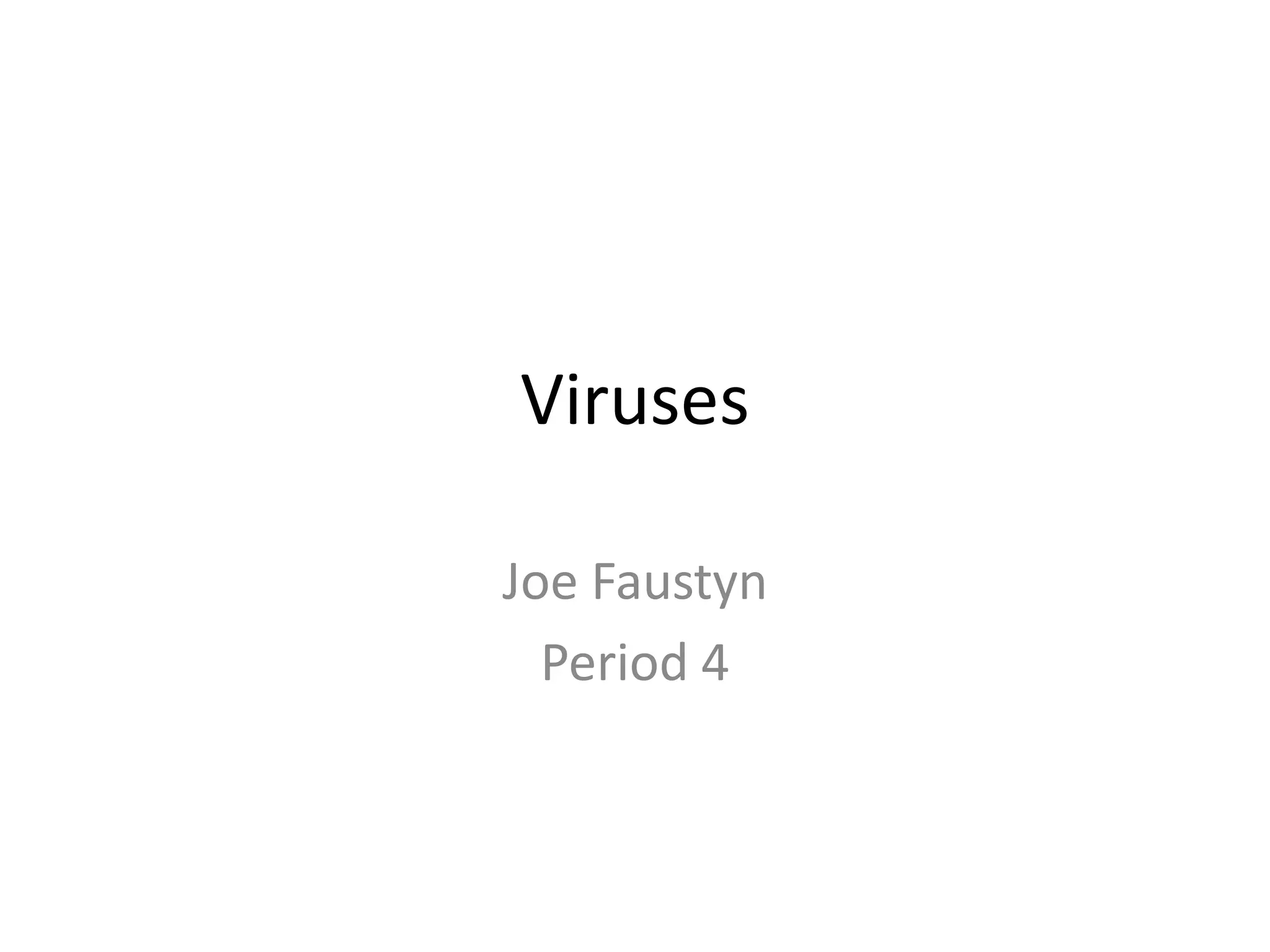
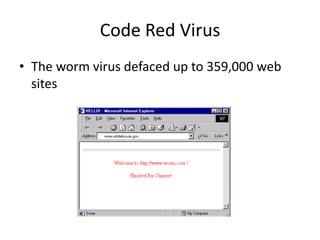


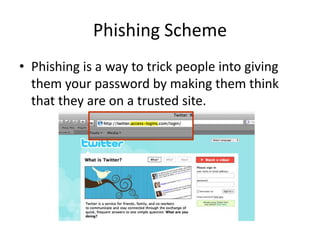



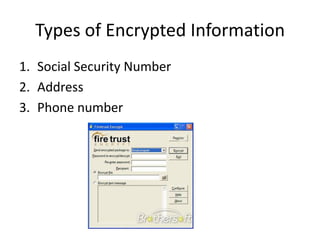
The document discusses different types of viruses like the Code Red virus and Love Bug virus. It also discusses biometric computer security using fingerprints or eye scans instead of passwords. Phishing schemes are described as ways to trick users into giving away passwords. Biometric security allows only authorized users access and is impossible to forge but may be picky or deny access if a fingerprint is cut. Anti-virus software fights viruses by identifying and destroying them in emails and websites. Encrypted personal information can include social security numbers, addresses, and phone numbers.








