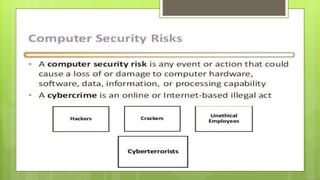
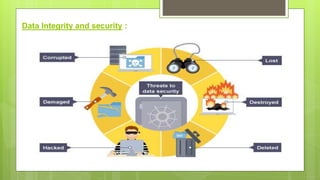
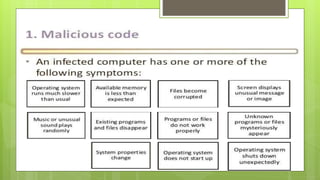
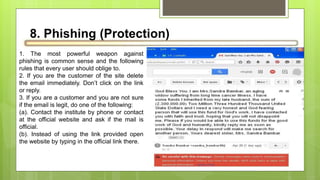
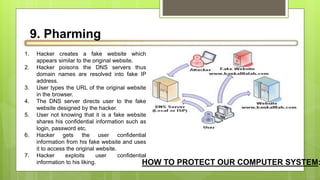
This document discusses various internet security risks such as malware, viruses, spyware, hacking, phishing, and pharming. It provides details on each risk, including how they work and potential security issues. Methods to minimize risks are discussed for most threats. For example, for viruses it notes they can be spread through email attachments and the importance of deleting suspicious emails. For phishing, it recommends verifying any unusual emails by contacting organizations directly rather than clicking links. Common sense and caution are emphasized as important protections against many internet security threats.