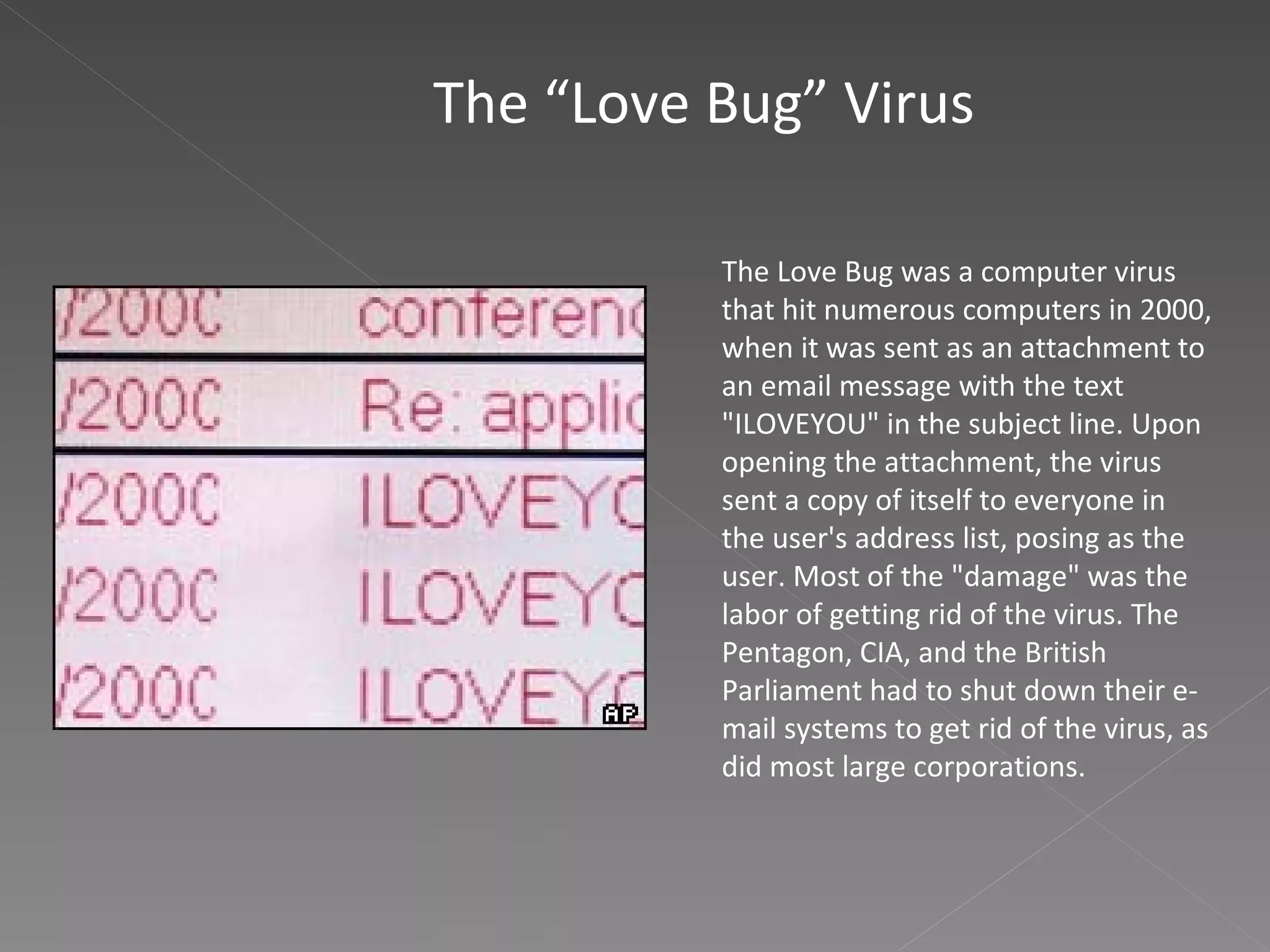
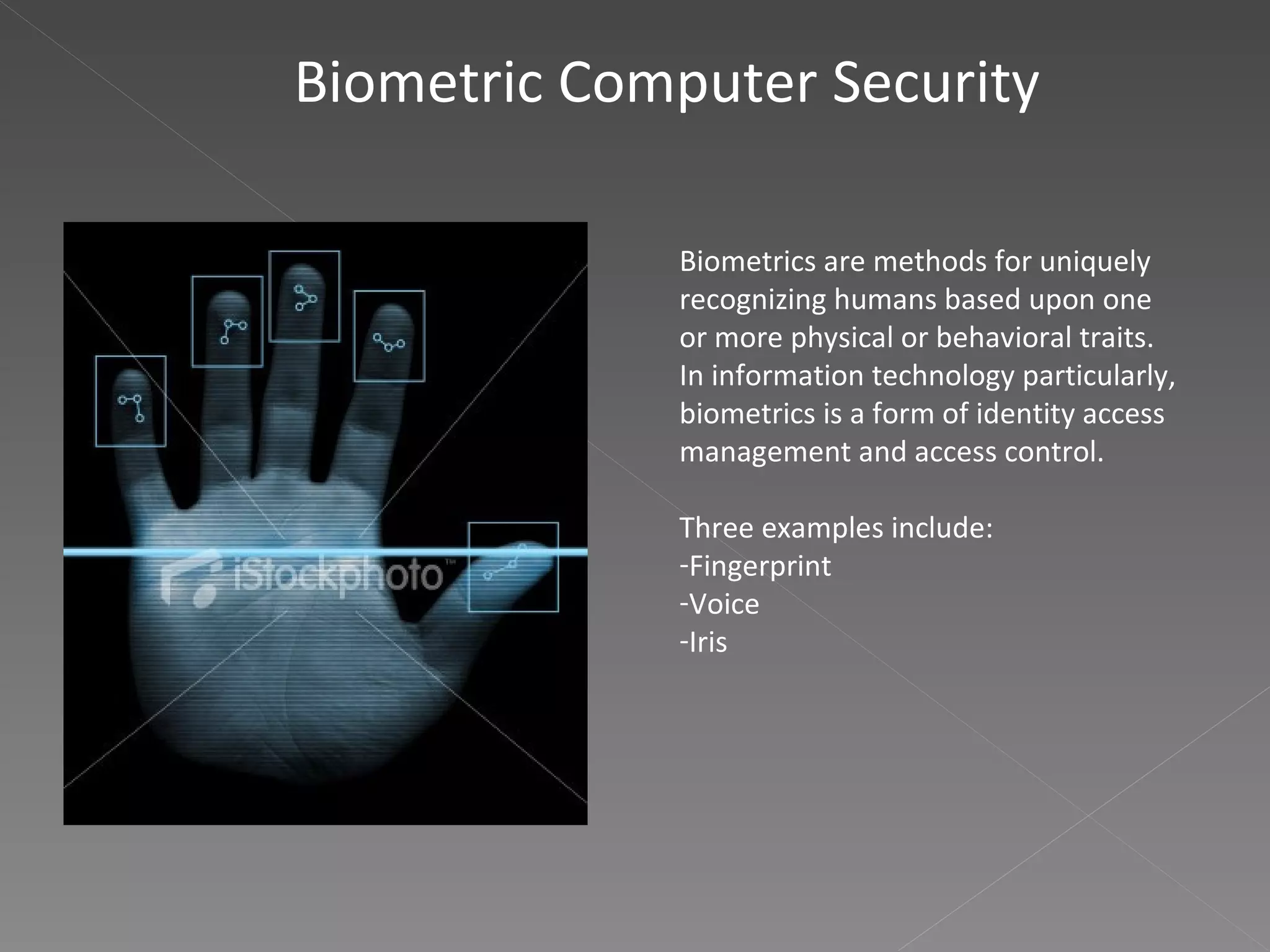
The document discusses several topics related to computer security including the Code Red computer worm from 2001, the Love Bug virus from 2000, biometric computer security using fingerprints, voice and iris recognition, phishing schemes such as the 2006 MySpace worm, advantages and disadvantages of biometric security, antivirus software, and types of information that should be encrypted like credit card numbers, passwords, personal details and medical records.