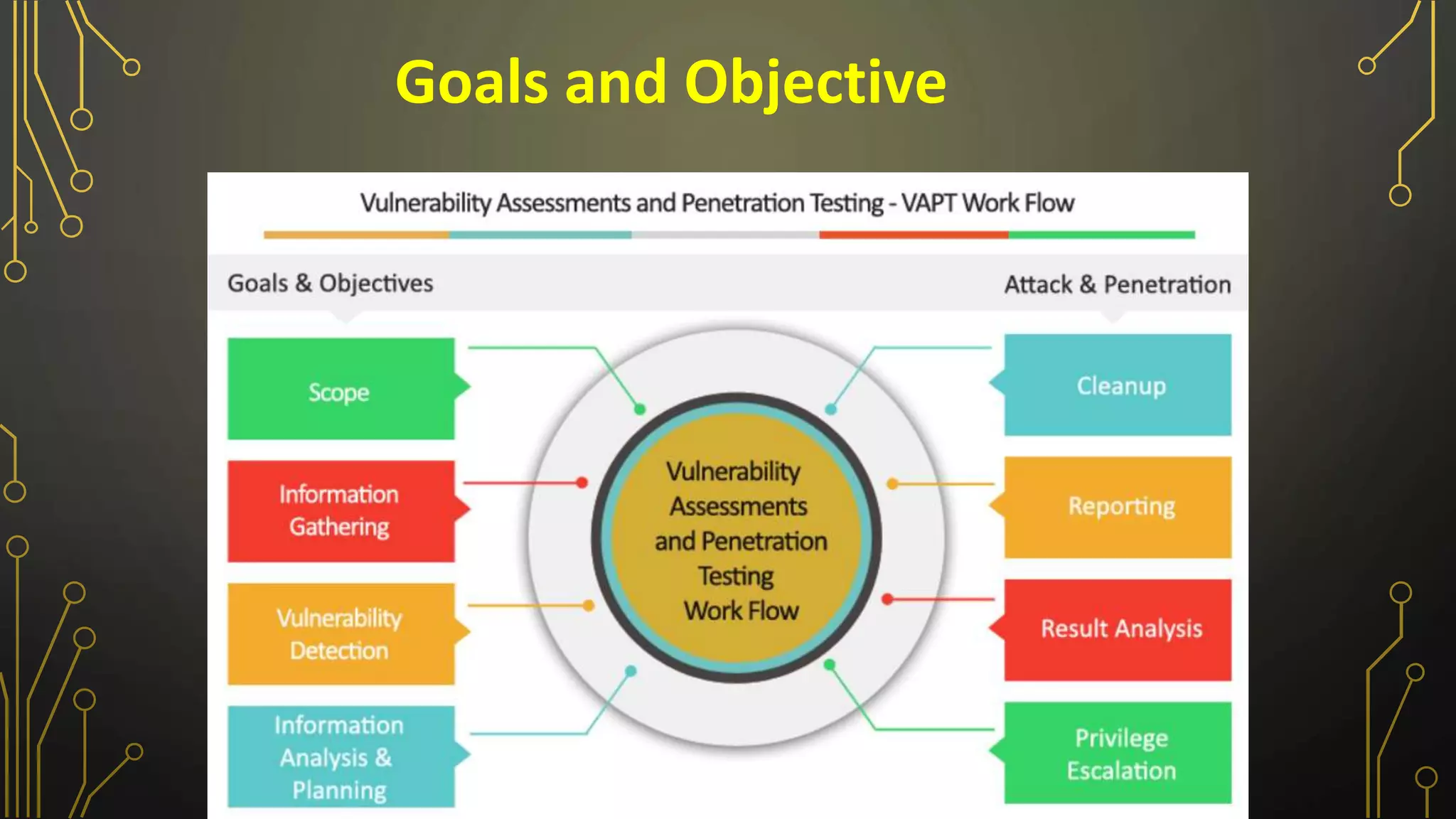
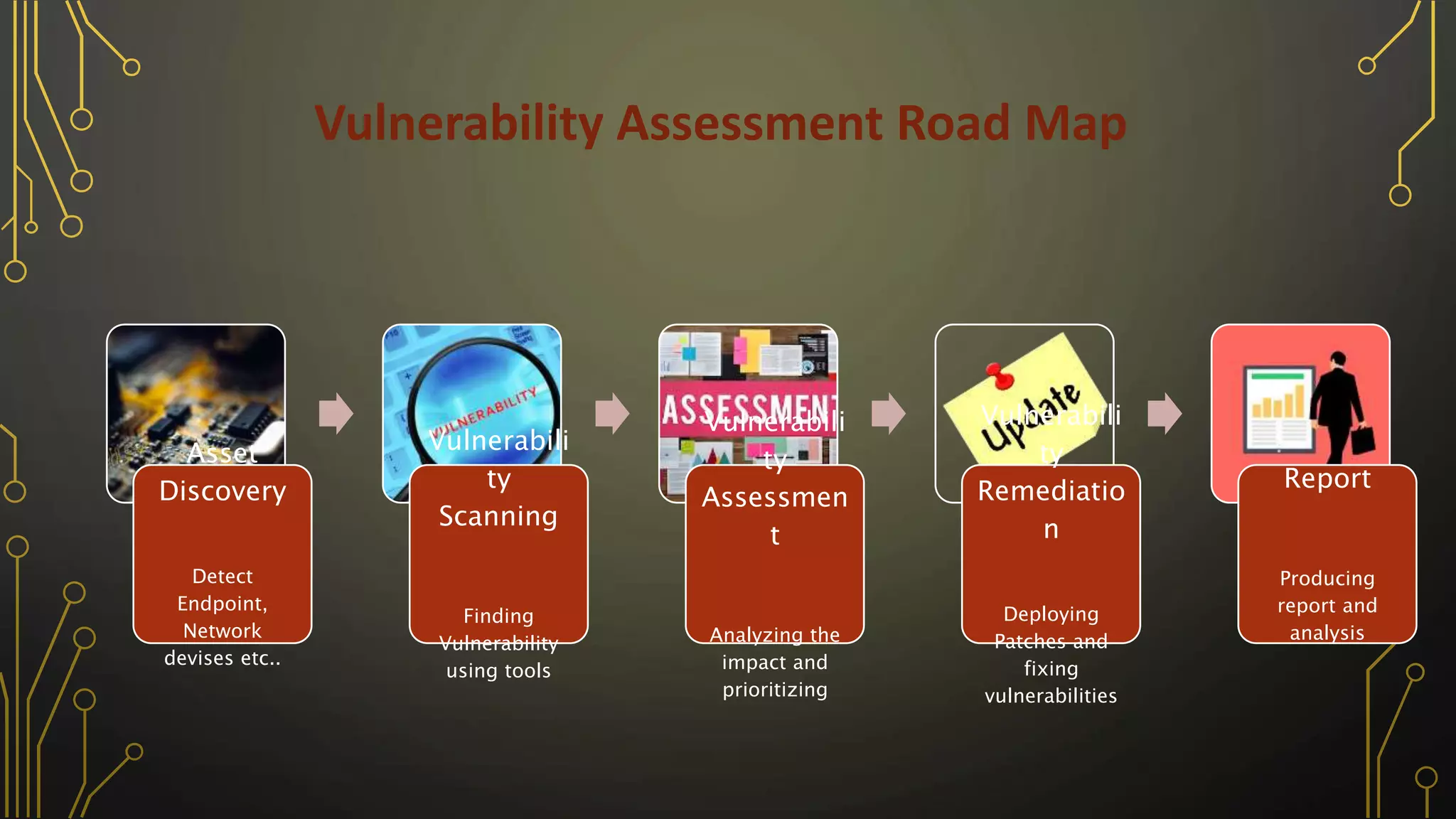
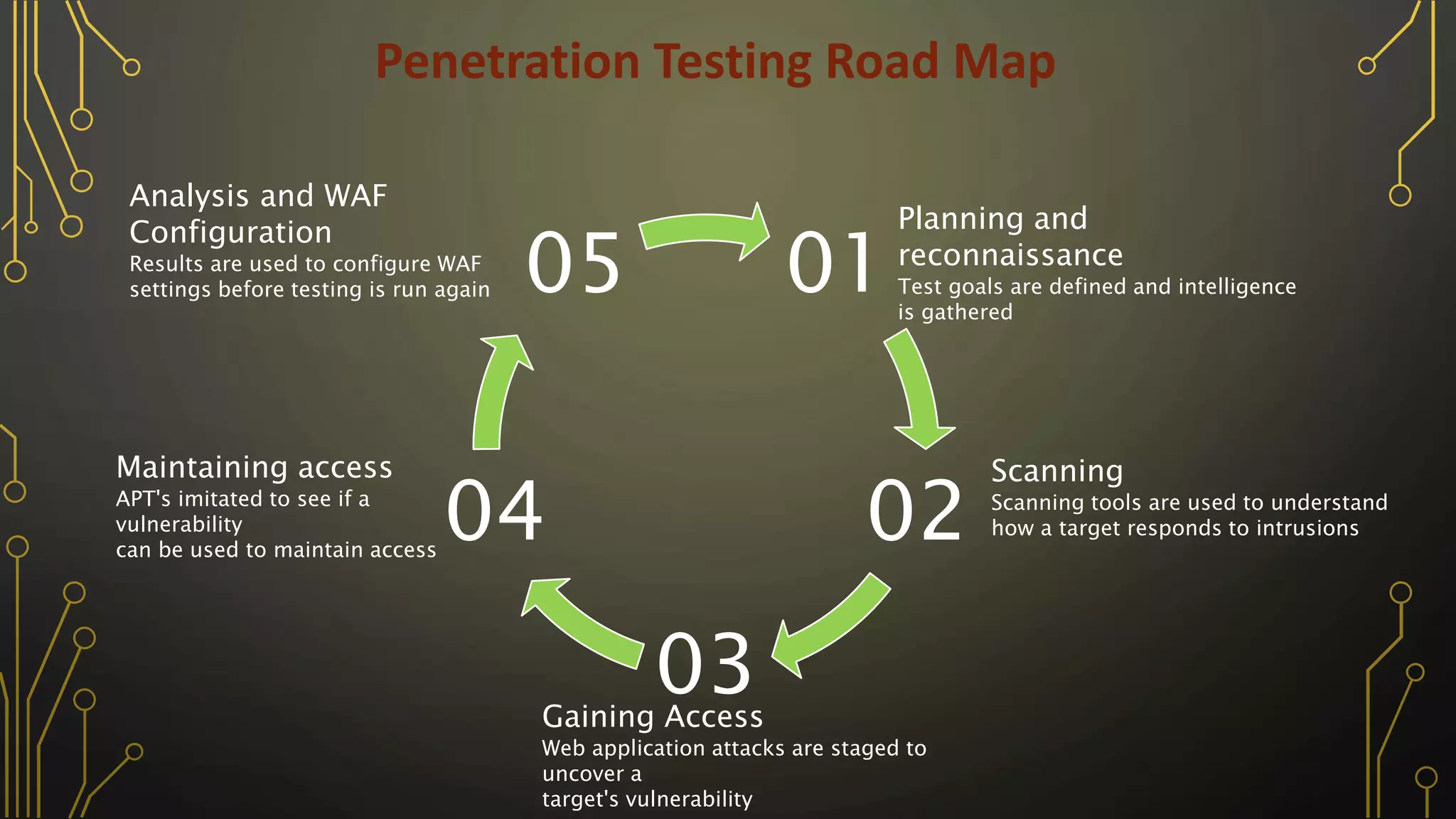
The document outlines various penetration testing techniques and vulnerability assessment methods, including network, web, and physical security testing. It details the steps involved in vulnerability scanning, analyzing impacts, and prioritizing remediation, as well as the importance of reporting findings. Additionally, it discusses different sources of vulnerabilities and methods for exploitation and assessment.