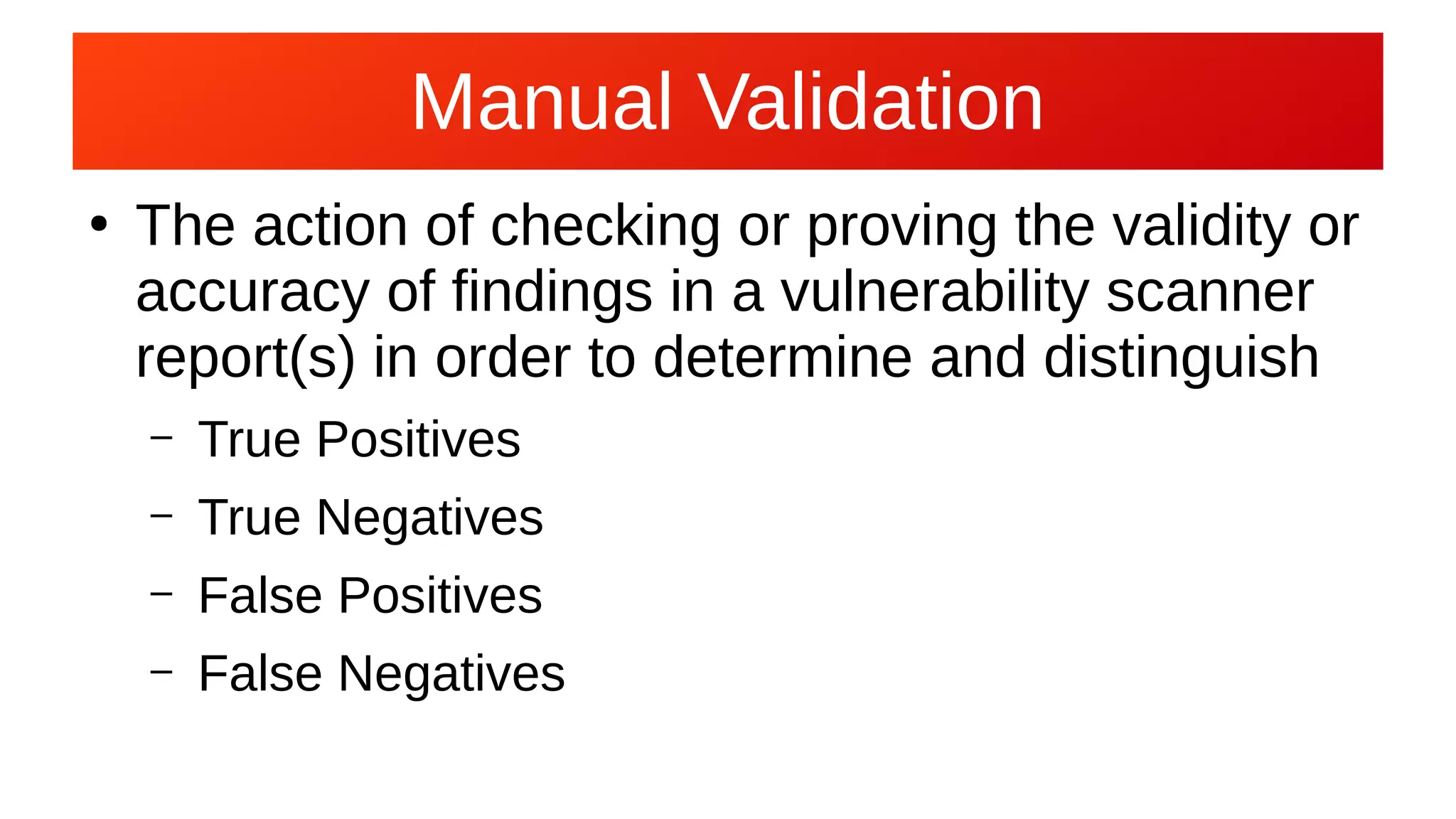
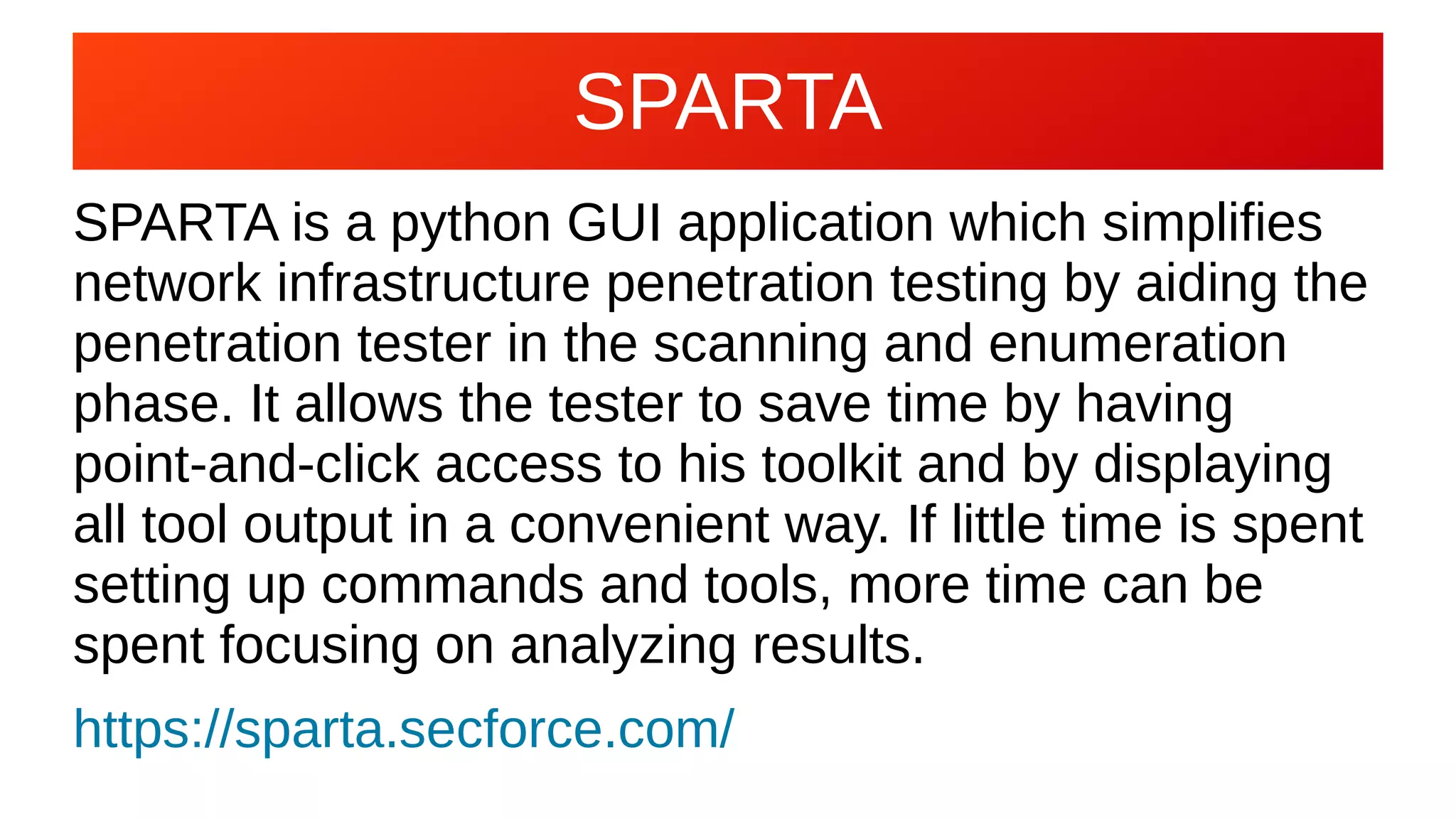
The document discusses the importance of vulnerability management and assessment in computer security, highlighting tools like OWASP ZAP and Metasploit for identifying and exploiting vulnerabilities. It emphasizes the necessity for manual validation of vulnerability scanner reports and encourages security professionals to proactively scan for sensitive data exposure and weak credentials. Additionally, it warns that threat actors are likely exploiting these vulnerabilities, urging organizations to address these issues before they are discovered by malicious entities.