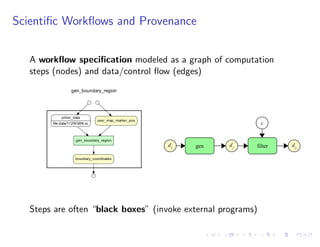
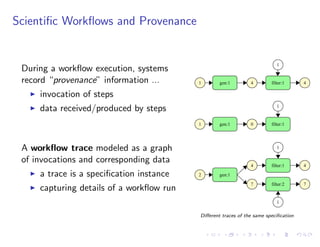
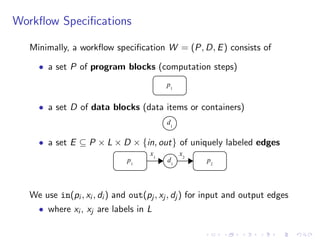
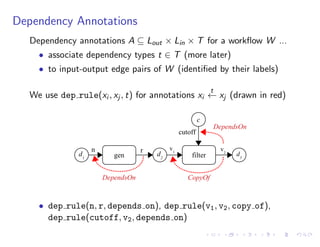
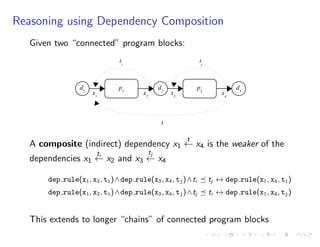
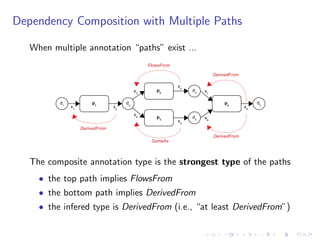
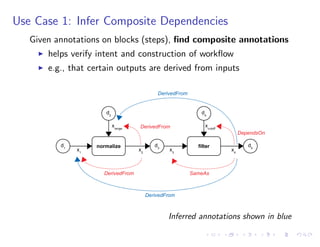
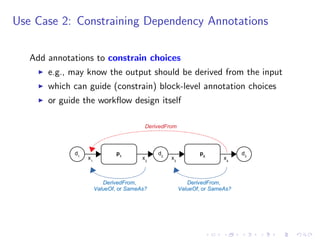
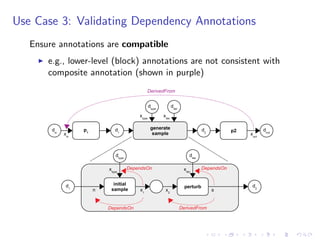
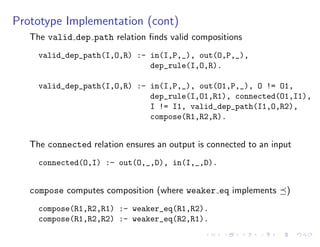
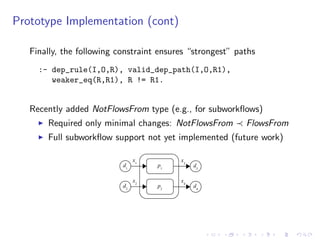
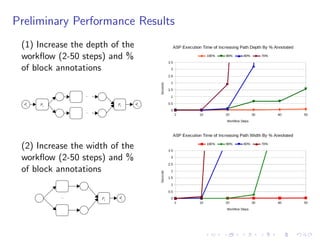
The document discusses a method for validating and inferring schema-level workflow data-dependency annotations to address issues with incorrect and vague inferred dependencies in scientific workflows. It presents an approach allowing workflow authors to specify dependency patterns and types, ensuring annotation correctness while enabling composite annotation inference. The paper outlines the implementation of a prototype using answer-set programming for annotation generation and validation in workflow specifications.