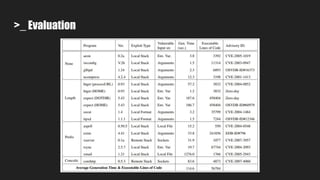
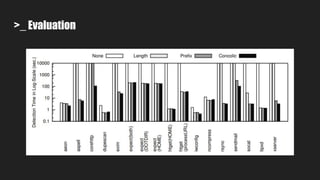
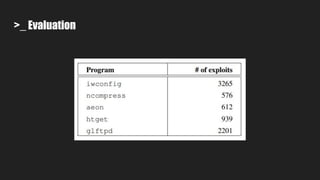
Automatic Exploit Generation (AEG) aims to automatically find vulnerabilities and generate exploits by analyzing source code through a series of steps:
1. It pre-processes source code to generate intermediate representations for binary and source code analysis.
2. It performs source code analysis to determine the maximum size of symbolic data.
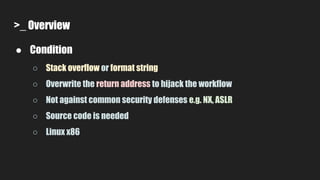
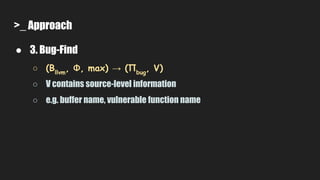
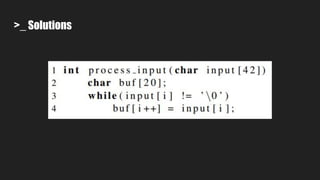
3. It uses symbolic execution guided by an "unsafe path predicate" to find bugs in the source code and collect related information.
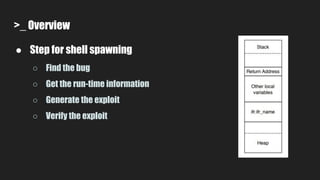
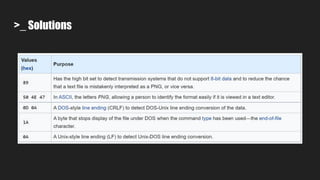
4. It performs dynamic binary analysis to gather runtime information needed for exploit generation.
5. It generates an "exploit predicate" using the collected information to hijack program control flow and execute shellcode.
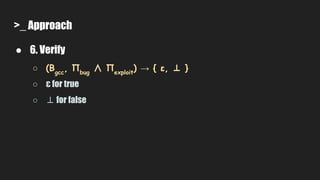
6. It verifies whether the generated




![>_ Introduction
● Challenges
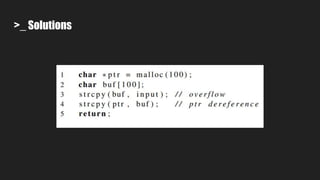
○ Source code analysis alone is inadequate
■ char src[12], dst[10]; strncpy(dst, src, sizeof(src))
○ Infinite number of possible paths
■ Which paths should we check first?](https://image.slidesharecdn.com/aegautomaticexploitgeneration-221012091843-ccc5df02/85/AEG_-Automatic-Exploit-Generation-5-320.jpg)