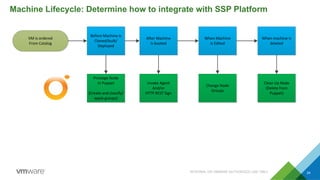
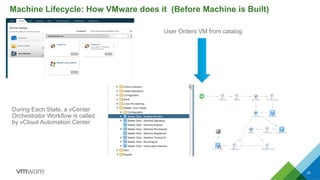
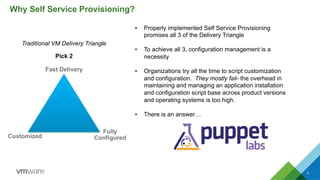
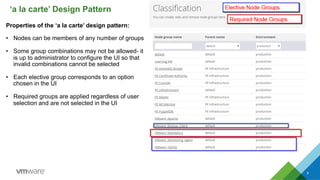
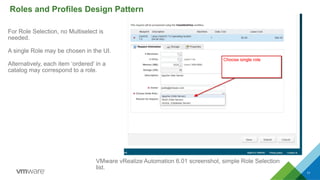
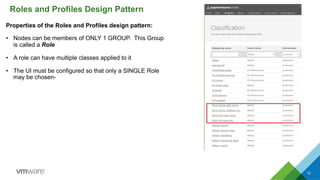
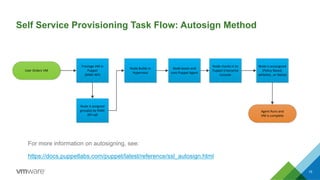
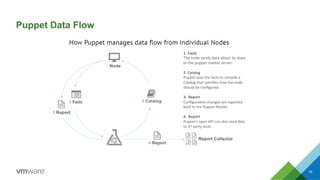
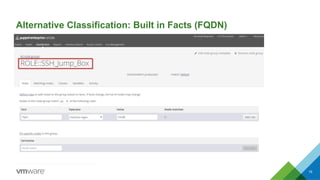
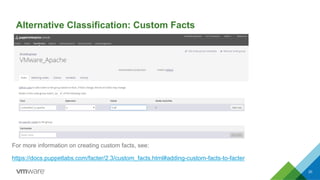
This document discusses integrating Puppet configuration management with self-service provisioning systems. It describes two common design patterns for applying Puppet configurations - the "a la carte" pattern where users select from multiple configuration options, and the "roles and profiles" pattern where users select a single predefined role. The document also outlines different approaches to classifying nodes in Puppet and integrating the Puppet master with provisioning platforms like VMware vRealize Automation. It provides examples of using the Puppet RAKE API to pre-stage nodes and assign configuration groups.










![21
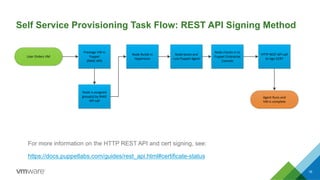
Sample RAKE API Commands (Prestage ‘a la carte’)
For more information on RAKE API, see the following:
https://docs.puppetlabs.com/pe/latest/console_rake_api.html
Automation engine will SSH into Puppet Enterprise Console and Create Node / Assign
Group membership is a single command
$
sudo
/opt/puppet/bin/rake
-‐f
/opt/puppet/share/puppet-‐dashboard/Rakefile
RAILS_ENV=production
node:add[my_vm_01,(VMware_Mandatory,VMware_Monitoring_Agent,
VMware_Apache)]](https://image.slidesharecdn.com/usingpuppetwithselfserviceprovisioning-150113171358-conversion-gate02/85/Using-Puppet-with-Self-Service-Provisioning-21-320.jpg)
![22
Sample RAKE API Commands (Prestage ‘Roles and Profiles’)
For more information on RAKE API, see the following:
https://docs.puppetlabs.com/pe/latest/console_rake_api.html
Automation engine will SSH into Puppet Enterprise Console and Create Node / Assign
Group membership is a single command
$
sudo
/opt/puppet/bin/rake
-‐f
/opt/puppet/share/puppet-‐dashboard/Rakefile
RAILS_ENV=production
node:add[my_vm_01,(ROLE::Apache_Web_Server)]](https://image.slidesharecdn.com/usingpuppetwithselfserviceprovisioning-150113171358-conversion-gate02/85/Using-Puppet-with-Self-Service-Provisioning-22-320.jpg)