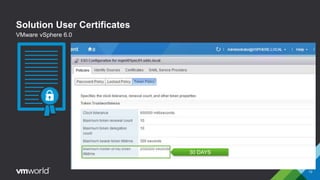
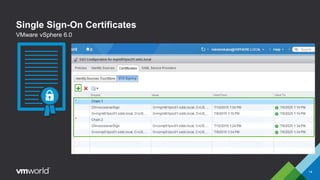
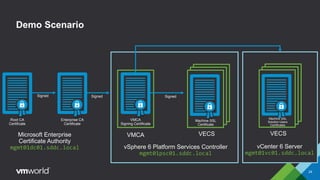
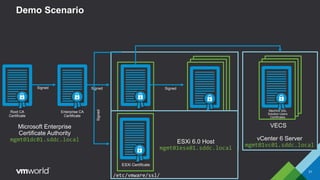
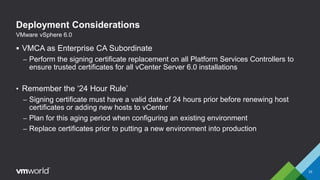
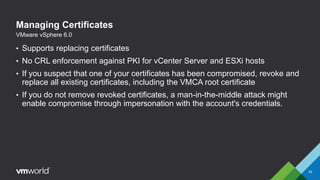
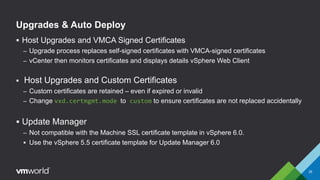
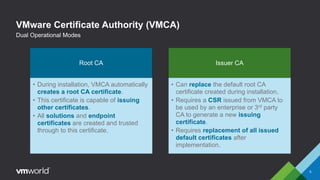
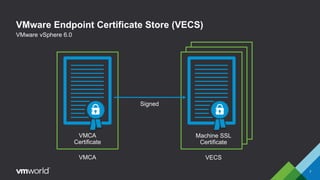
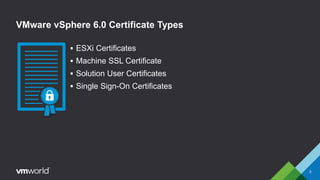
VMware vSphere 6.0 introduces new capabilities for managing certificates throughout the virtual infrastructure lifecycle. It includes the VMware Certificate Authority (VMCA) and VMware Endpoint Certificate Store (VECS) to provision and manage certificates for ESXi hosts, vCenter Server services, and other VMware components. Administrators can choose to use VMCA as the root CA, as an enterprise CA subordinate to an external root, or bring their own custom CA certificates. The presentation demonstrates how to replace the VMCA signing certificate with an enterprise CA-issued certificate as well as how to renew ESXi host certificates after the change.




![ESXi Certificates
10
VMware vSphere 6.0
Example:
function refreshcerts {
process {
$hostid = Get-VMHost $vmhost | Get-View
$hostParam = New-Object VMware.Vim.ManagedObjectReference[] (1)
$hostParam[0] = New-Object VMware.Vim.ManagedObjectReference
$hostParam[0].value = $hostid.moref.value
$hostParam[0].type = 'HostSystem'
$_this = Get-View -Id 'CertificateManager-certificateManager'
$_this.CertMgrRefreshCertificates_Task($hostParam)
}
}](https://image.slidesharecdn.com/inf4529eckerlejohnsonformatted4-160707230304/85/VMworld-2015-VMware-vSphere-Certificate-Management-for-Mere-Mortals-10-320.jpg)