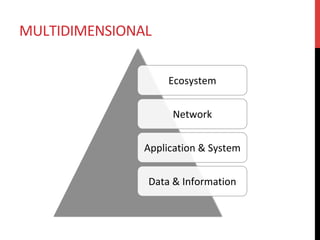
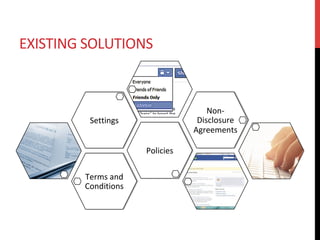
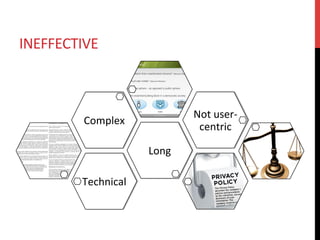
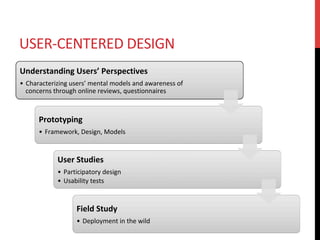
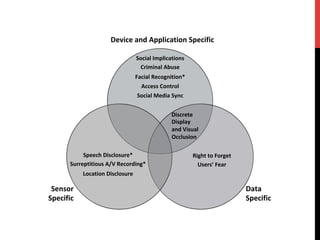
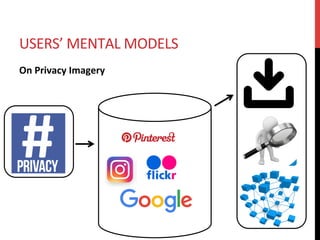
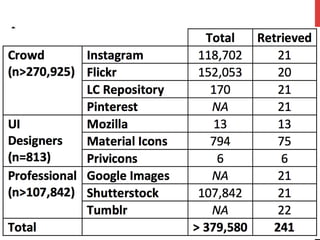
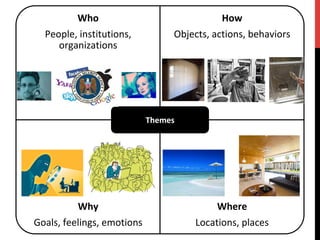
The document discusses privacy issues related to emerging technologies like wearables and smart home devices. It begins with an outline of topics to be covered, including contextualizing privacy, theoretical definitions versus real-world practices, privacy studies on online reviews, and open questions. The rest of the document delves into these topics, finding that privacy is a multidimensional concept that varies by context and individual. User studies of online reviews reveal different perspectives on privacy concerns for technologies. Imagery analysis identifies common metaphors and mental models around privacy concepts. Open questions remain around simplifying privacy and developing effective user-centric solutions.







![1. ONLINE REVIEWS
• Wearables and Smart Home Devices
• Major Findings
• ‘I have never thought about it…’
• Oblivious users
• ‘Pick your poison’
• Deliberate choices
• ‘I am [my data is] not important’
• Unconcerned users](https://image.slidesharecdn.com/usp-190314204721/85/Usable-Privacy-16-320.jpg)


![WEARABLES
Fear of Surveillance
• ‘[wearable devices are] the NSA's new best friend’
Fear of Sousveillence
• ‘There's also another challenge that affects not only
those who wear Glass, but everyone else around privacy’](https://image.slidesharecdn.com/usp-190314204721/85/Usable-Privacy-19-320.jpg)











![REFERENCES
• CHHETRI, C.; MOTTI, V. G. (2019). Eliciting Privacy Concerns for Smart Home
Devices from a User Centered Perspective. In Proceedings of the iConference
2019. Lecture Notes in Computer Science. Springer-Verlag.
• LOWENS, B.; MOTTI, V. G.; CAINE, K. (2017) Wearable Privacy: Skeletons in The
Data Closet. In Proceedings of the IEEE International Conference on Healthcare
Informatics. DOI 10.1109/ICHI.2017.29 [PDF] [Slides]
• MOTTI, V. G. & CAINE, K. E. (2016). Towards a Visual Vocabulary for Privacy
Concepts. In Proceedings of the Human Factors and Ergonomics Society 2016
Annual Meeting. Washington DC, USA: Human Factors and Ergonomics Society.
September 2016
• MOTTI, V. G.; CAINE, K. E. (2015). Users' Privacy Concerns About Wearables:
Impact of Form Factor, Sensors and Type of Data Collected. In Proceedings of
the Financial Cryptography and Data Security (1st Workshop on Wearable
Security and Privacy). Lecture Notes in Computer Science. Springer-Verlag
Berlin Heidelberg, Vol 8976, pp. 1-14. DOI=10.1007/978-3-662-48051-9_16](https://image.slidesharecdn.com/usp-190314204721/85/Usable-Privacy-39-320.jpg)
