This document contains a lecture on working with arrays, scripts, and SSH/SCP in UNIX systems. It discusses special variables used in scripts, how to define and manipulate arrays, examples of useful scripts for renaming files, backing up data, and extracting video files from DVDs, and how to use SSH to securely connect to remote systems and SCP to securely transfer files between systems. It also covers generating and using public/private key pairs for passwordless SSH login.



![/bin/sh arrays
area[11]=23
area[13]=37
area[51]=UFOs
echo ${area[11]}
4](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-4-320.jpg)
![Array operations (exercise)
area[5]=`expr ${area[11]} + ${area[13]}`
area[6]=`expr ${area[11]} + ${area[51]}`
Where is the mistake?
5](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-5-320.jpg)
![Other methods
area2=( zero one two three four)
echo ${area2[0]}
area3=([17]=seventeen[24]=twenty four)
array1=( `cat "$filename" | tr 'n' ' '`)
read -a colors
base64_charset=( {A..Z} {a..z} {0..9} + / = )
6](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-6-320.jpg)
![No type
string=abcABC123ABCabc
echo ${string[@]} # abcABC123ABCabc
echo ${string[*]} # abcABC123ABCabc
echo ${string[0]} # abcABC123ABCabc
echo ${string[1]} #
echo ${#string[@]} # 1
7](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-7-320.jpg)
![Remember and use
array= ( zero one two three four five)
# Elementai: 0 1 2 3 4 5
echo ${array[0]} # zero
echo ${array:0} # zero
echo ${array:1} # ero
echo ${#array[0]} # 5
echo ${#array}
echo ${#array[1]} # 6
echo ${#array[*]} # 6
echo ${#array[@]} # 6
8](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-8-320.jpg)
![Operations with string
arrayZ=( one two three four five five )
echo ${arrayZ[@]:0} # one two three four five five
echo ${arrayZ[@]:1} # two three four five five
echo ${arrayZ[@]:1:2} # two three
echo ${arrayZ[@]#f*r} # one two three five five
echo ${arrayZ[@]##t*e} # one two four five five
echo ${arrayZ[@]%h*e} # one two t four five five
echo ${arrayZ[@]%%t*e} # one two four five five
9](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-9-320.jpg)
![Element replacement
echo ${arrayZ[@]%%t*e} # one two four five five
echo ${arrayZ[@]//iv/YY} # one two three four fYYe fYYe
echo ${arrayZ[@]//fi/} # one two three four ve ve
echo ${arrayZ[@]/#fi/XY} # one two three four XYve Xyve
echo ${arrayZ[@]/%ve/ZZ} # one two three four fiZZ fiZZ
echo ${arrayZ[@]/%o/XX} # one twXX three four five five
10](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-10-320.jpg)

![singleton
#!/bin/bash
echo "argument: $1"
RESULT=`/bin/ps xauwww | /bin/grep -v "$0" | /bin/grep "^$USER.*$1$"`
if [ -z "$RESULT" ] ; then
LC_MESSAGES=en_US $*
else
echo "Sorry, already running as:"
echo " $RESULT”
echo "singleton reports that $1 is already started”
fi
#end
12](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-12-320.jpg)
![mysqltcpdump
# tcpdump -i eth0 -s 0 -l -w - dst port 3306 | strings | perl -e '
while(<>) { chomp; next if /^[^ ]+[ ]*$/;
if(/^(SELECT|UPDATE|DELETE|INSERT|SET|COMMIT|ROLLBACK|
CREATE|DROP|ALTER)/i) {
if (defined $q) { print "$qn"; }
$q=$_;
} else {
$_ =~ s/^[ t]+//; $q.=" $_";
}
}'
13](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-13-320.jpg)
![#!/usr/bin/perl -w # camel code
use strict;
$_='ev
al("seek040D
ATA,0, 0;");foreach(1..3)
{<DATA>;}my @camel1hump;my$camel;
my$Camel ;while( <DATA>){$_=sprintf("%-6
9s",$_);my@dromedary 1=split(//);if(defined($
_=<DATA>)){@camel1hum p=split(//);}while(@dromeda
ry1){my$camel1hump=0 ;my$CAMEL=3;if(defined($_=shif
t(@dromedary1 ))&&/S/){$camel1hump+=1<<$CAMEL;}
$CAMEL--;if(d efined($_=shift(@dromedary1))&&/S/){
$camel1hump+=1 <<$CAMEL;}$CAMEL--;if(defined($_=shift(
@camel1hump))&&/S/){$camel1hump+=1<<$CAMEL;}$CAMEL--;if(
defined($_=shift(@camel1hump))&&/S/){$camel1hump+=1<<$CAME
L;;}$camel.=(split(//,"040..m`{/J047134}L^7FX"))[$camel1h
ump];}$camel.="n";}@camel1hump=split(/n/,$camel);foreach(@
camel1hump){chomp;$Camel=$_;y/LJF7173175`047/061062063
064065066067070/;y/12345678/JL7F175173047`/;$_=reverse;
print"$_040$Cameln";}foreach(@camel1hump){chomp;$Camel=$_;y
/LJF7173175`047/12345678/;y/12345678/JL7F1751730 47`/;
$_=reverse;print"040$_$Cameln";}';;s/s*//g;;eval; eval
("seek040DATA,0,0;");undef$/;$_=<DATA>;s/s*//g;( );;s
;^.*_;;;map{eval"print"$_"";}/.{4}/g; __DATA__ 124
1 501450401651631450401571 460401 410
40143141 1551451 540401 51155 141
1471450 40151156 040141 16316 3
157143 15114116 41511 57156
040167 1511641 50040 1201
45162 15404015 1163 04014
10401 641621 41144 145
15514 1162 15304 0157
146 04011 7047 1221
4515 11541 54171 040
046 01210116 316
315 714315 114
116 4145163 054
040 11115614 3056
040 12516314514 4040
1671 511641 500 40160
145162 155151
163163 1511
57156056
(unused…)
14](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-14-320.jpg)
![movies
#!/bin/bash
# Made by ioccatflashdancedotcx
# Version 1.6,
if [ -n "$(ls 2>/dev/null *001|grep *001)" ]; then
rar x *01.rar
if [ -n "$(ls 2>/dev/null *bin)" ]; then
for i in *bin ; do vcdxrip -p --bin-file="$i" ; done
mv *mpg cd.mpg; rm *cue *bin *.xml _cdi_cdi_* _extra_svcdinfo.txt &>/dev/null
fi
fi
if [ -n "$(ls 2>/dev/null *01.rar|grep *01.rar)" ]; then
rar x *01.rar
if [ -n "$(ls 2>/dev/null *bin)" ]; then
for i in *bin ; do vcdxrip -p --bin-file="$i" ; done
mv *mpg cd.mpg; rm *cue *bin *.xml _cdi_cdi_* _extra_svcdinfo.txt &>/dev/null
fi
fi
if [ -n "$(ls 2>/dev/null *.rar|grep *.rar)" ]; then
rar x *rar
if [ -n "$(ls 2>/dev/null *bin)" ]; then
for i in *bin ; do vcdxrip -p --bin-file="$i" ; done
mv *mpg cd.mpg; rm *cue *bin *.xml _cdi_cdi_* _extra_svcdinfo.txt &>/dev/null
fi
fi
15](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-15-320.jpg)

![if cd ${cddir} &>/dev/null; then
if [ -n "$(ls 2>/dev/null *001|grep *001)" ]; then
rar x *001
if [ -n "$(ls 2>/dev/null *bin)" ]; then
for i in *bin ; do vcdxrip -p --bin-file="$i" ; done
if [ -n "$(ls 2>/dev/null avseq02.mpg)" ]; then
rm avseq01.mpg
fi
mv *mpg ../${cddir}.mpg
rm *cue *bin *.xml _cdi_cdi_* _extra_svcdinfo.txt &>/dev/null
cd ..
for i in ${cddir}.mpg ; do mv -- $i `echo $i|tr A-Z a-z` ; done
elif [ -n "$(ls 2>/dev/null *mpg)" ]; then
mv *mpg ../${cddir}.mpg
cd ..
for i in ${cddir}.mpg ; do mv -- $i `echo $i|tr A-Z a-z` ; done
elif [ -n "$(ls 2>/dev/null *avi)" ]; then
mv *avi ../${cddir}.avi
cd ..
for i in ${cddir}.avi ; do mv -- $i `echo $i|tr A-Z a-z` ; done
fi
else…
17](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-17-320.jpg)
![movies… (enough already?)else
if [ -n "$(ls 2>/dev/null *01.rar|grep *01.rar)" ]; then
rar x *01.rar
if [ -n "$(ls 2>/dev/null *bin)" ]; then
for i in *bin ; do vcdxrip -p --bin-file="$i" ; done
if [ -n "$(ls 2>/dev/null avseq02.mpg)" ]; then
rm avseq01.mpg
fi
mv *mpg ../${cddir}.mpg
rm *cue *bin *.xml _cdi_cdi_* _extra_svcdinfo.txt &>/dev/null
cd ..
for i in ${cddir}.mpg ; do mv -- $i `echo $i|tr A-Z a-z` ; done
elif [ -n "$(ls 2>/dev/null *mpg)" ]; then
mv *mpg ../${cddir}.mpg
cd ..
for i in ${cddir}.mpg ; do mv -- $i `echo $i|tr A-Z a-z` ; done
elif [ -n "$(ls 2>/dev/null *avi)" ]; then
mv *avi ../${cddir}.avi
cd ..
for i in ${cddir}.avi ; do mv -- $i `echo $i|tr A-Z a-z` ; done
fi
else
if [ -n "$(ls 2>/dev/null *.rar|grep *.rar)" ]; then
rar x *rar
if [ -n "$(ls 2>/dev/null *bin)" ]; then
for i in *bin ; do vcdxrip -p --bin-file="$i" ; done
if [ -n "$(ls 2>/dev/null avseq02.mpg)" ]; then
rm avseq01.mpg
fi
mv *mpg ../${cddir}.mpg
rm *cue *bin *.xml _cdi_cdi_* _extra_svcdinfo.txt &>/dev/null
cd ..
for i in ${cddir}.mpg ; do mv -- $i `echo $i|tr A-Z a-z` ; done
elif [ -n "$(ls 2>/dev/null *mpg)" ]; then
mv *mpg ../${cddir}.mpg
cd ..
for i in ${cddir}.mpg ; do mv -- $i `echo $i|tr A-Z a-z` ; done
elif [ -n "$(ls 2>/dev/null *avi)" ]; then
mv *avi ../${cddir}.avi
cd ..
for i in ${cddir}.avi ; do mv -- $i `echo $i|tr A-Z a-z` ; done
fi
fi
fi
fi
fi
done
18](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-18-320.jpg)


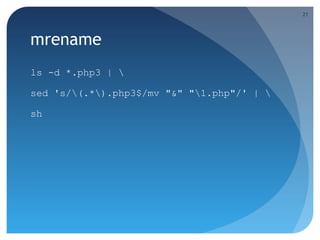



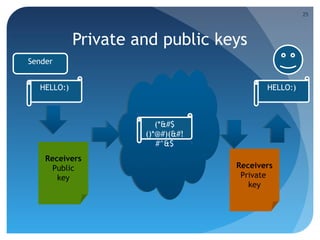



![Port forwarding
ssh –R [bind_address:]port:host:hostport
ssh -L [bind_address:]port:host:hostport
30](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-30-320.jpg)
![Security
anti-sec:~/pwn/xpl# ./0pen0wn -h xx.yy.143.133 -p 22
[+] 0wn0wn – anti-sec group
[+] Target: xx.yy.143.133
[+] SSH Port: 22
[~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~>]
sh-3.2# export HISTFILE=/dev/null
sh-3.2# id
uid=0(root) gid=0(root)
groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
sh-3.2# uname -a
Linux xx.yy.net 2.6.24.5-grsec-hostnoc-4.0.0-x86_64-libata
#1 SMP Mon Aug 25 15:56:12 EDT 2012 x86_64 x86_64 x86_64
GNU/Linux
31](https://image.slidesharecdn.com/unix5en-150705181101-lva1-app6892/85/Unix-5-en-31-320.jpg)
