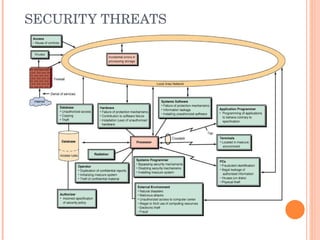
The document discusses the vulnerabilities of information systems and highlights major defense methods against cyber threats, including examples of significant cyber crimes and their impacts. It outlines the risks to organizational information resources, including human errors, environmental hazards, and intentional threats. Additionally, it emphasizes the importance of security audits and various defense strategies to mitigate these risks.