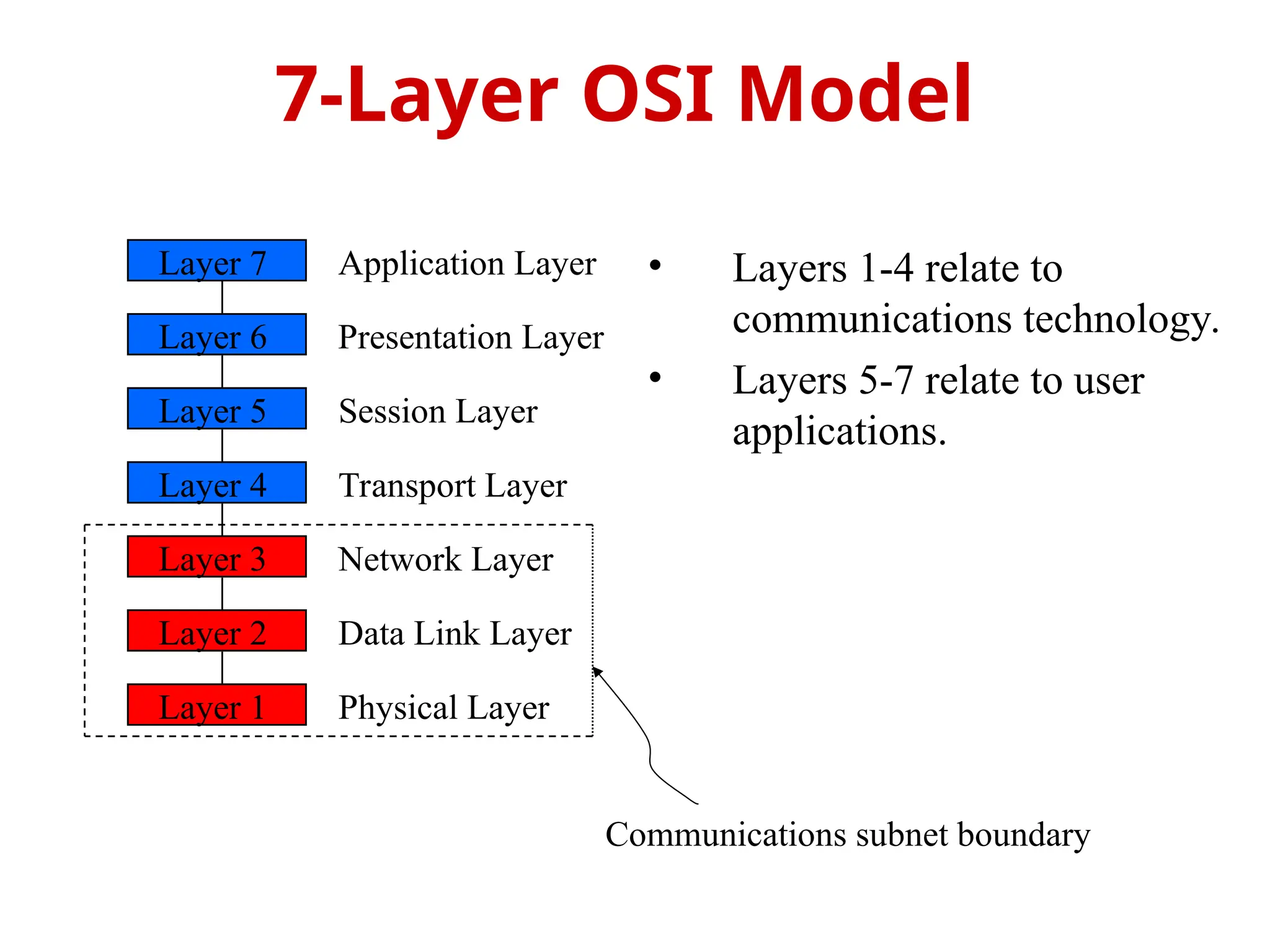
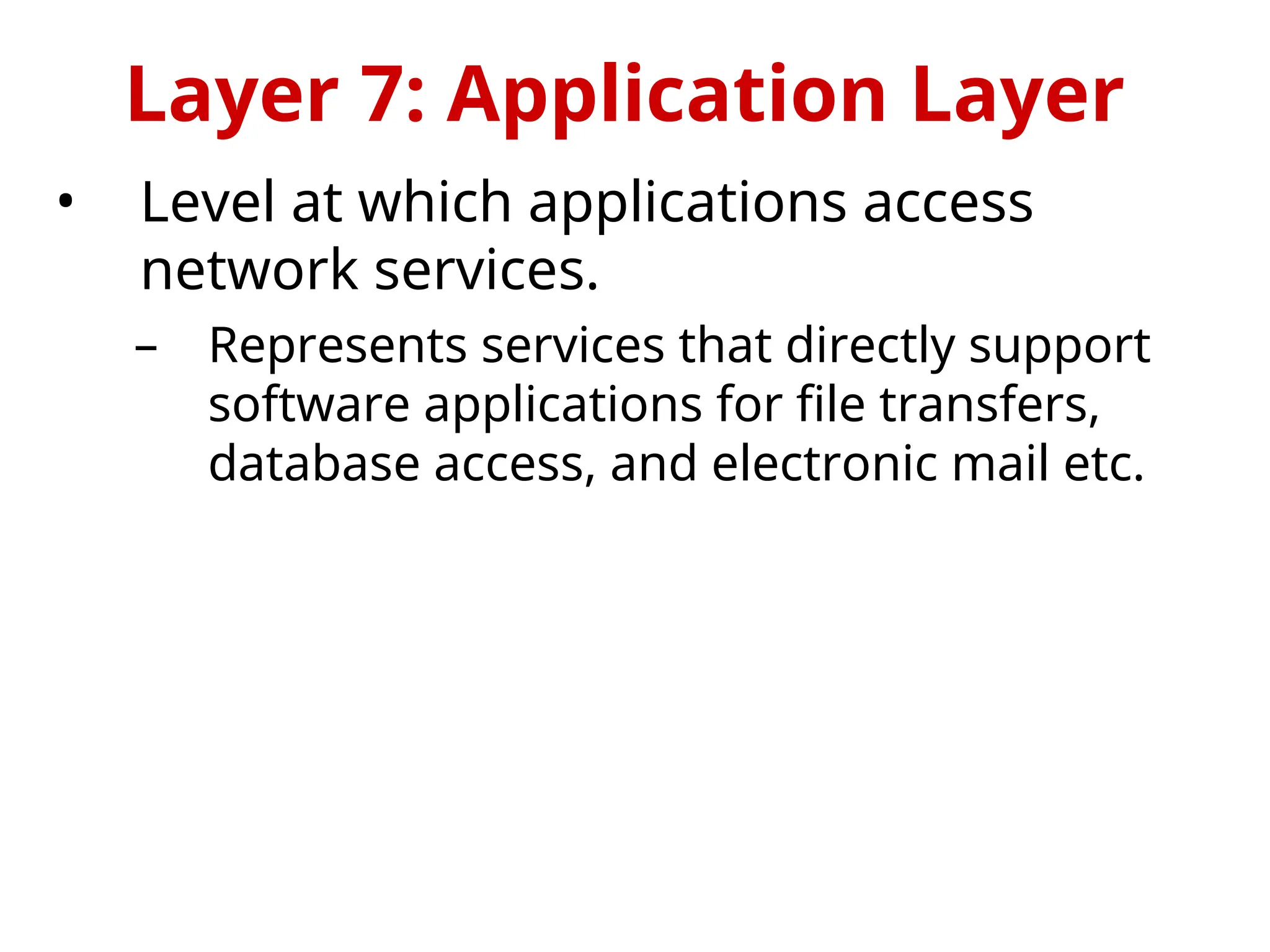
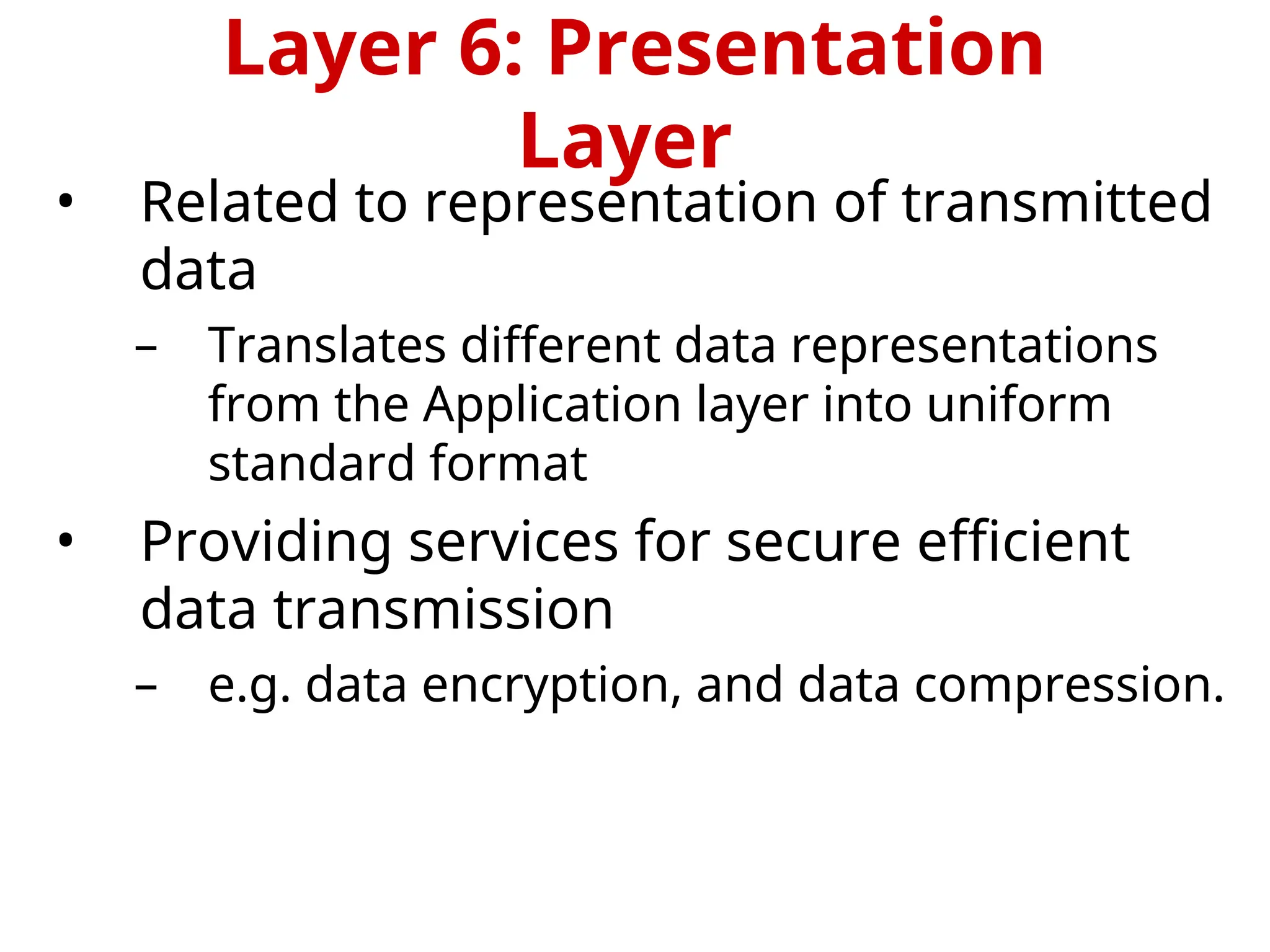
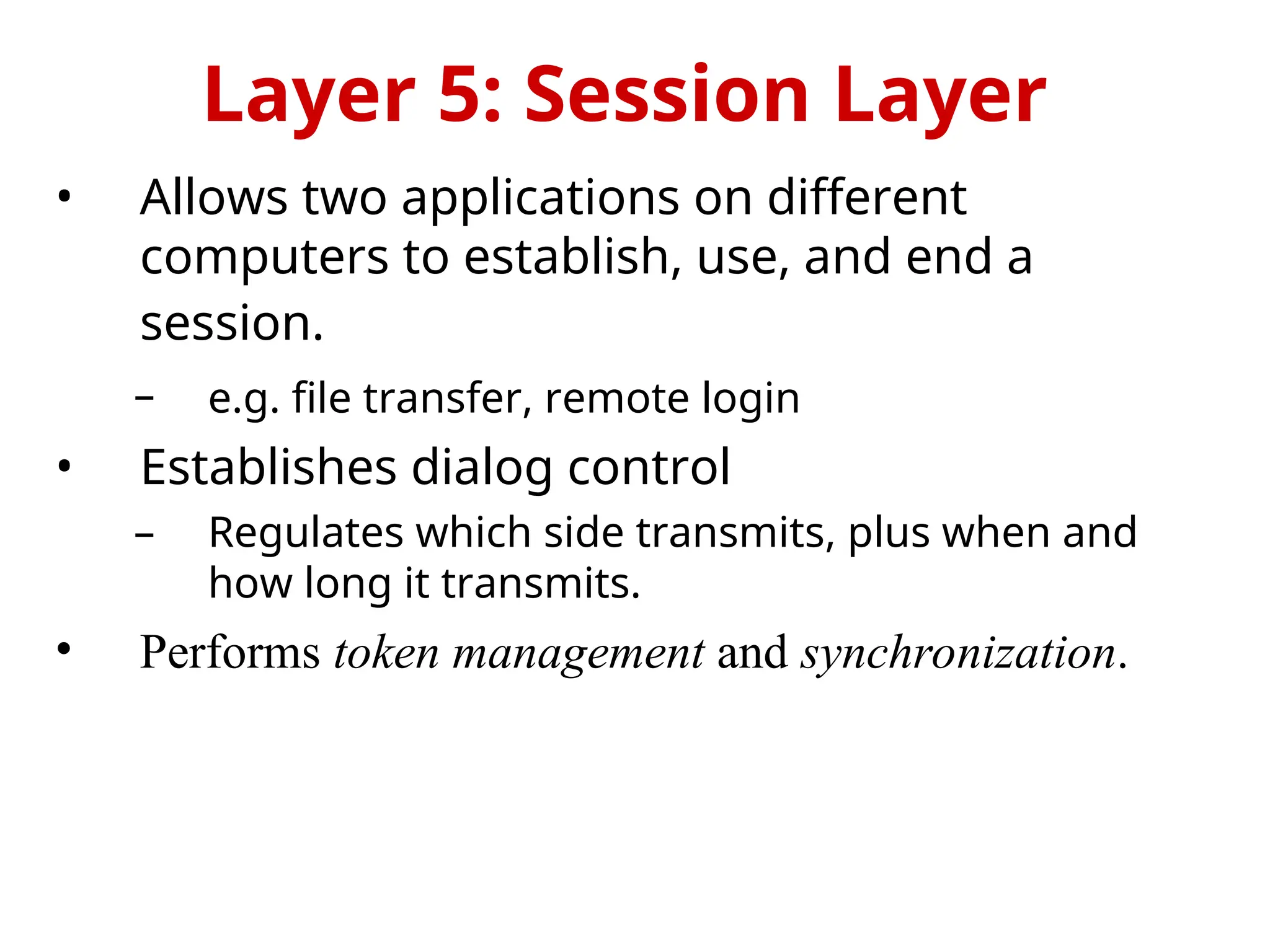
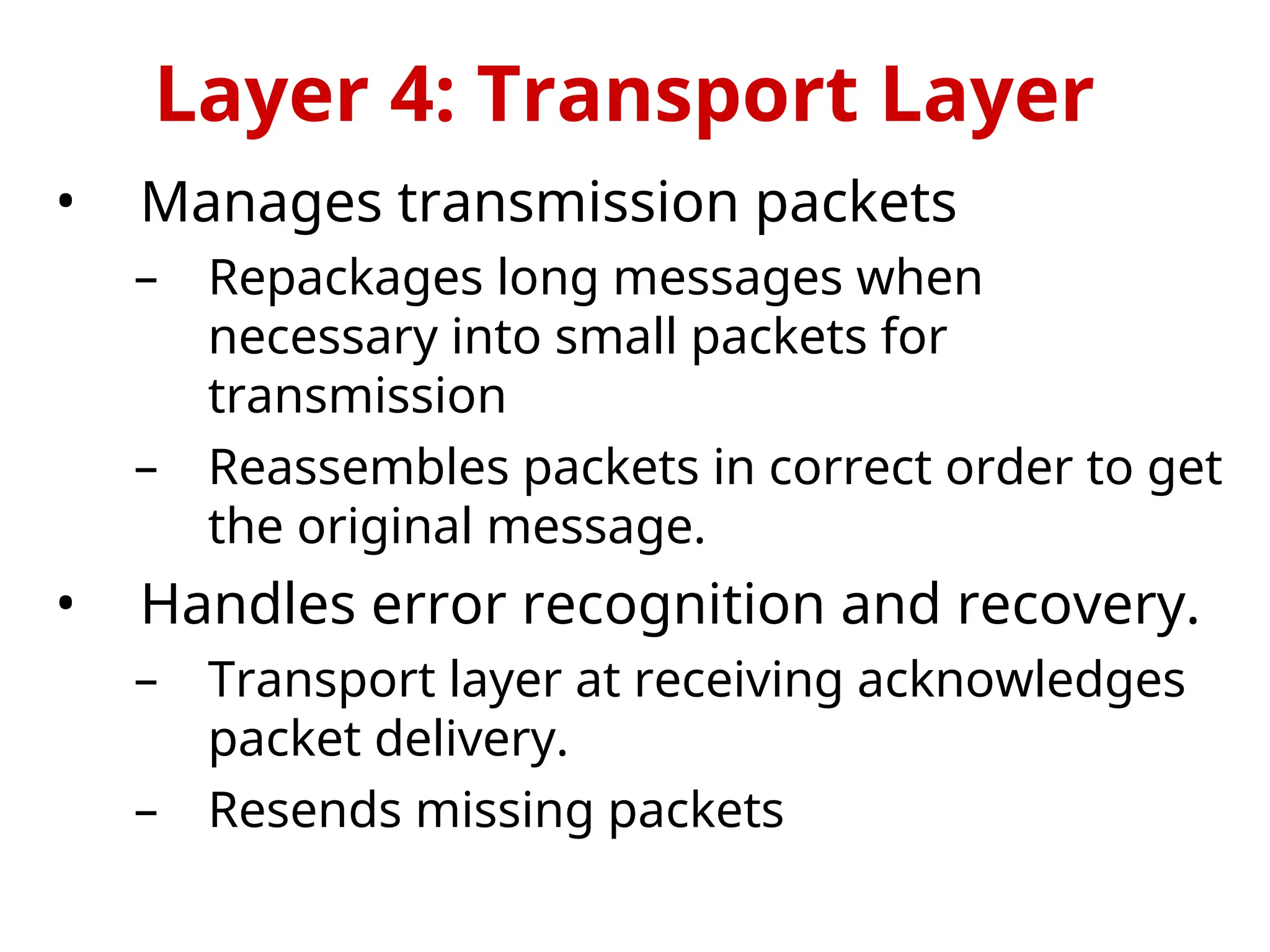
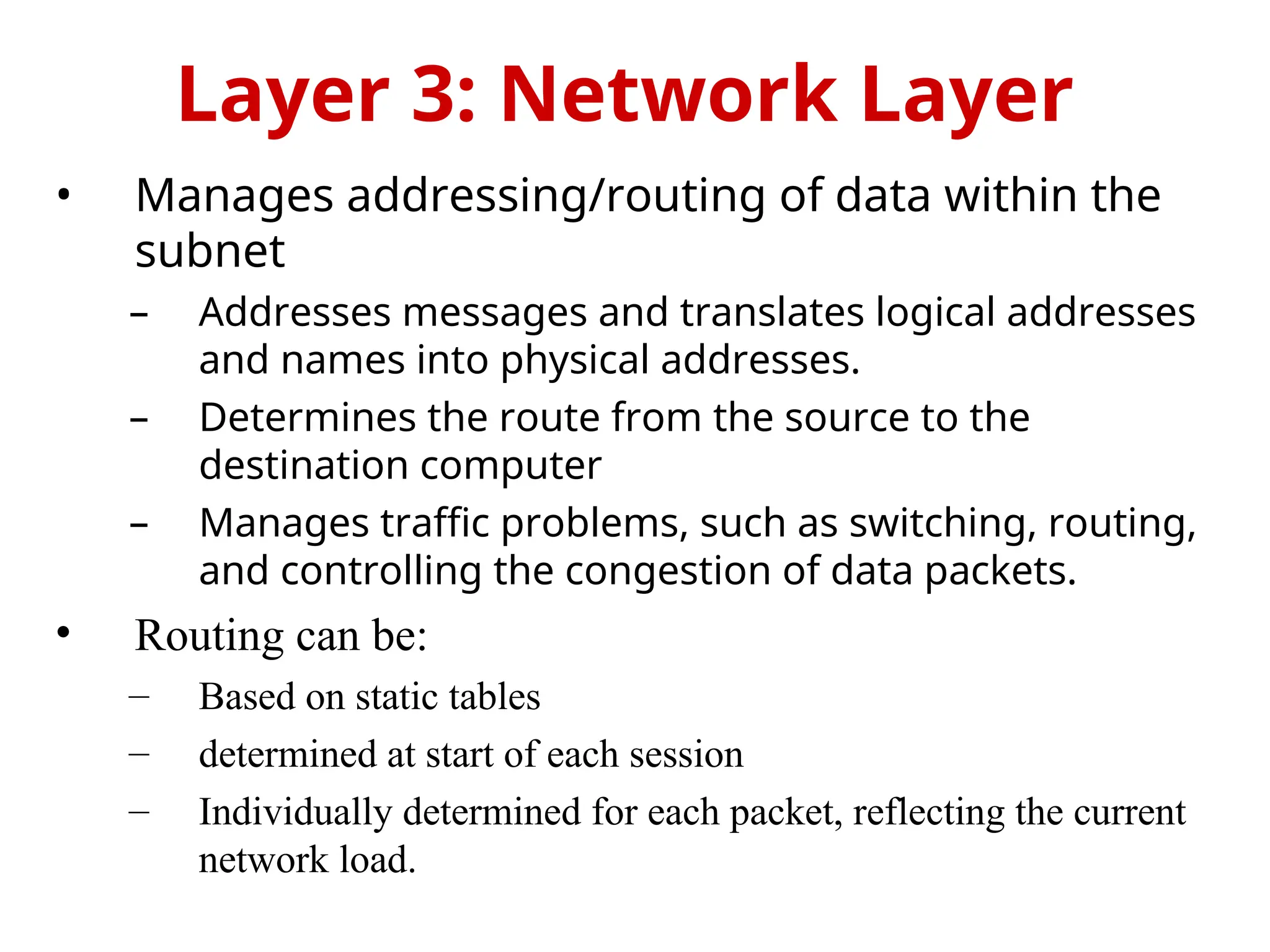
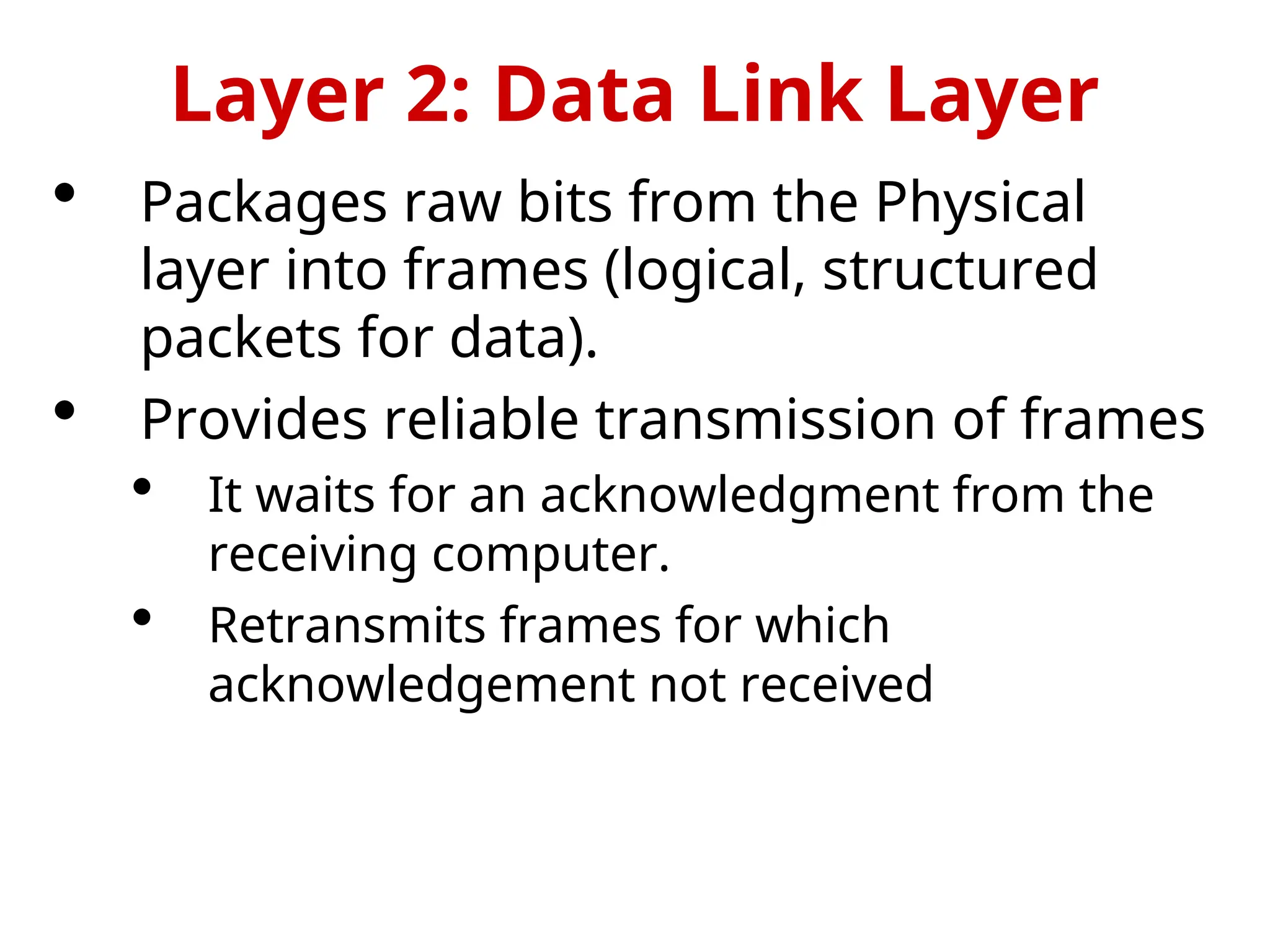
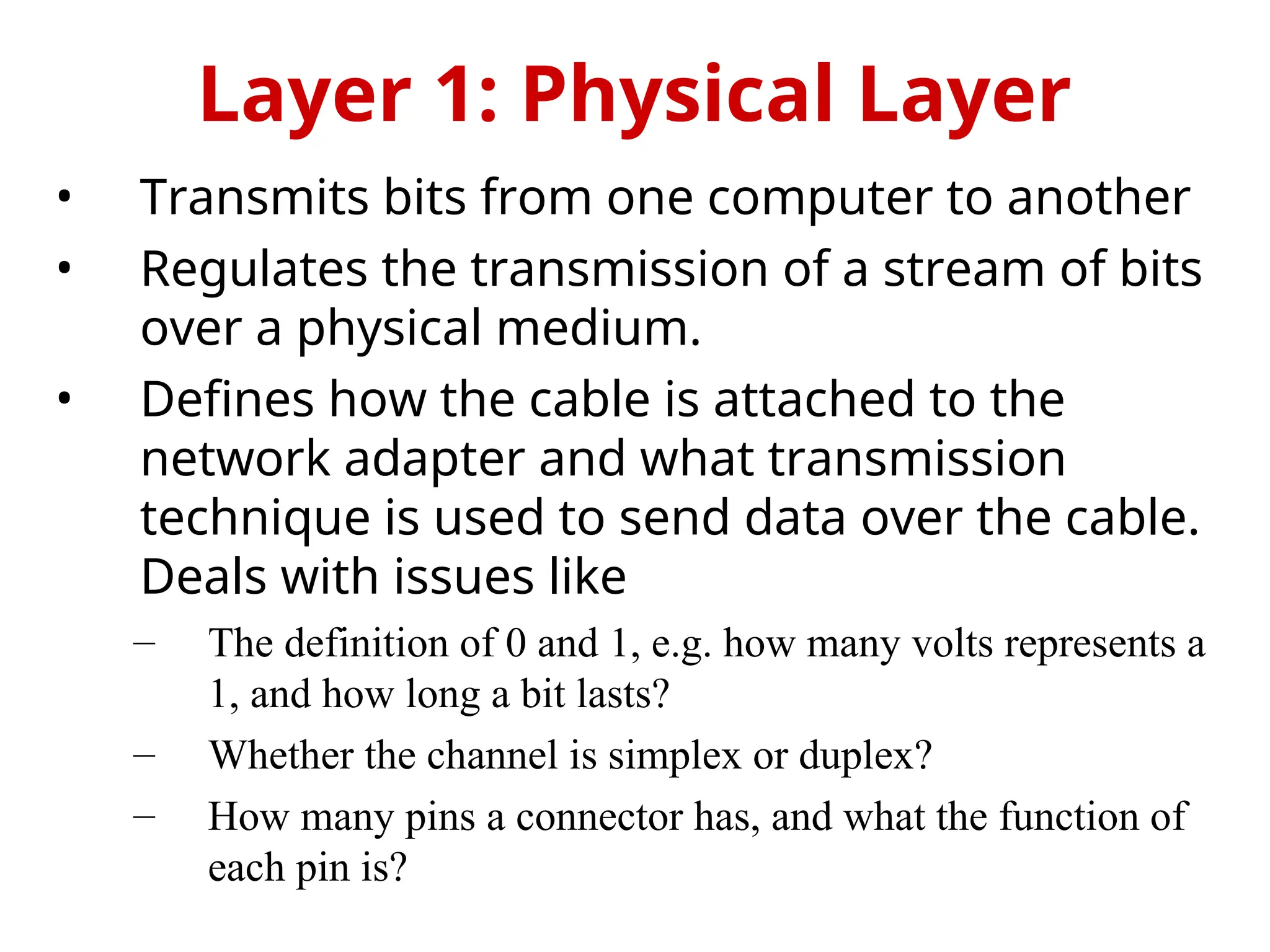
The OSI Reference Model is an internationally standardized network architecture consisting of seven layers. Layers 1-4 focus on communications technology while layers 5-7 are related to user applications, managing everything from data transmission and error recovery to session management and data representation. Each layer plays a specific role in ensuring efficient and reliable communication across different systems.