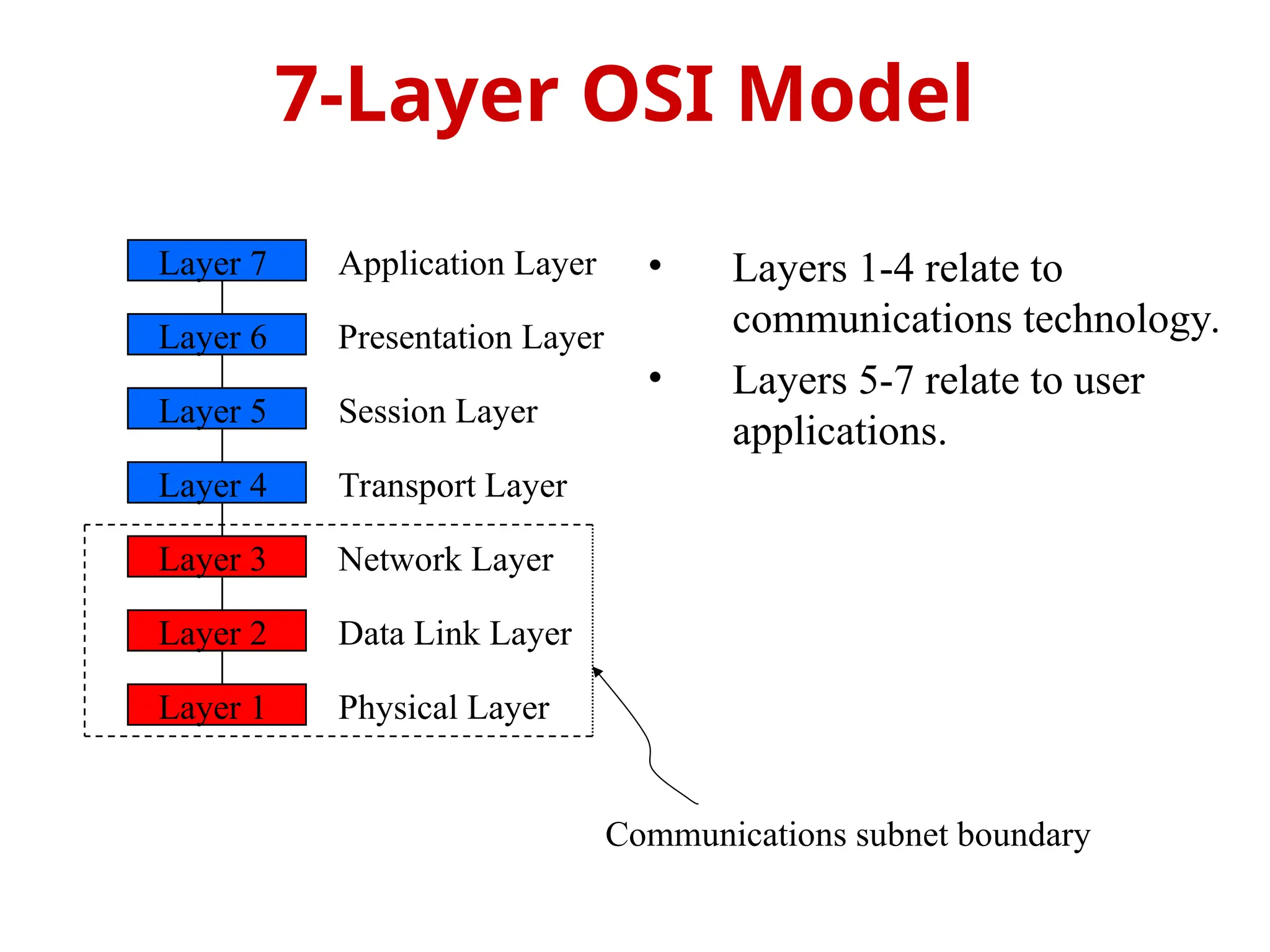
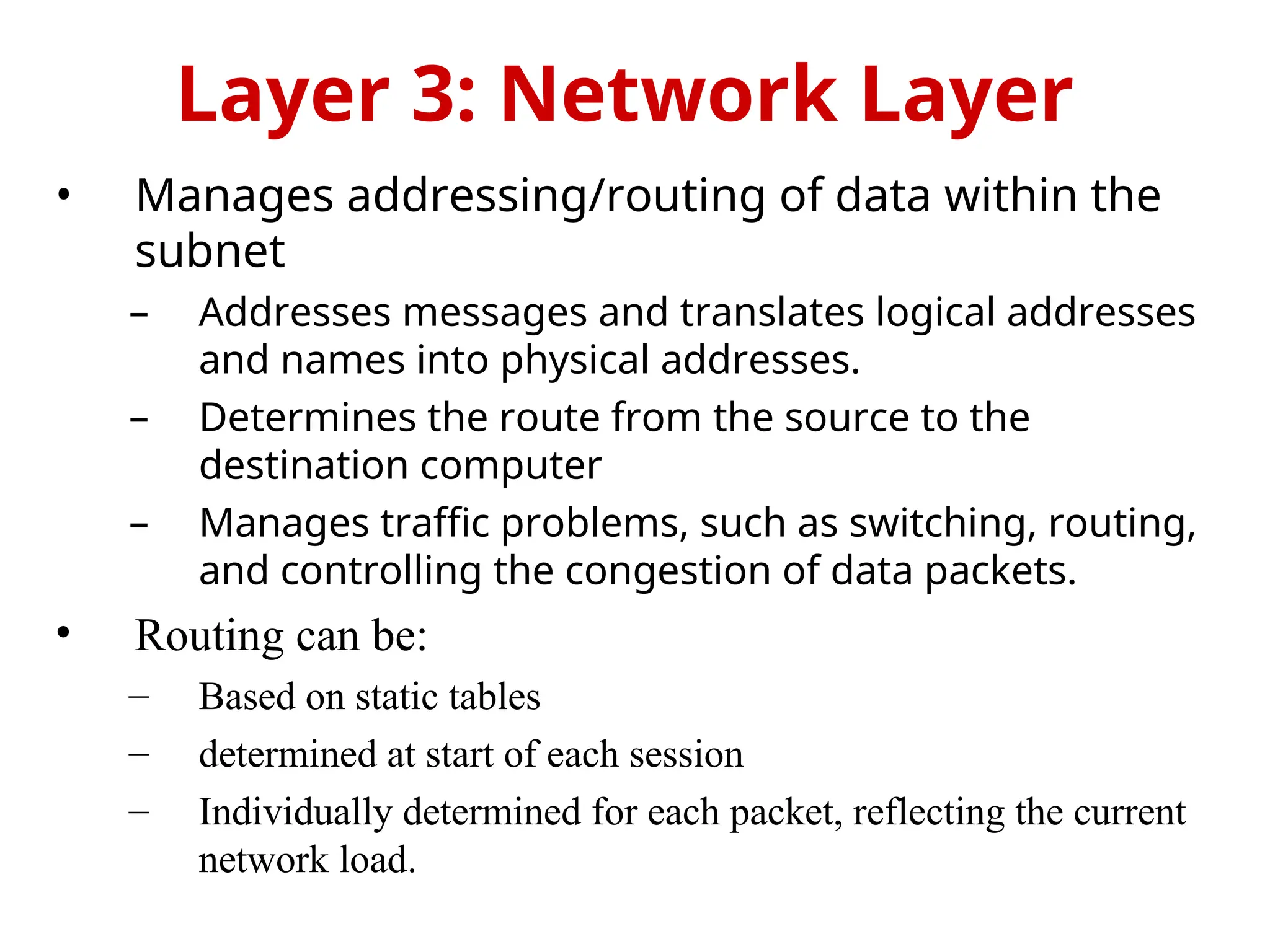
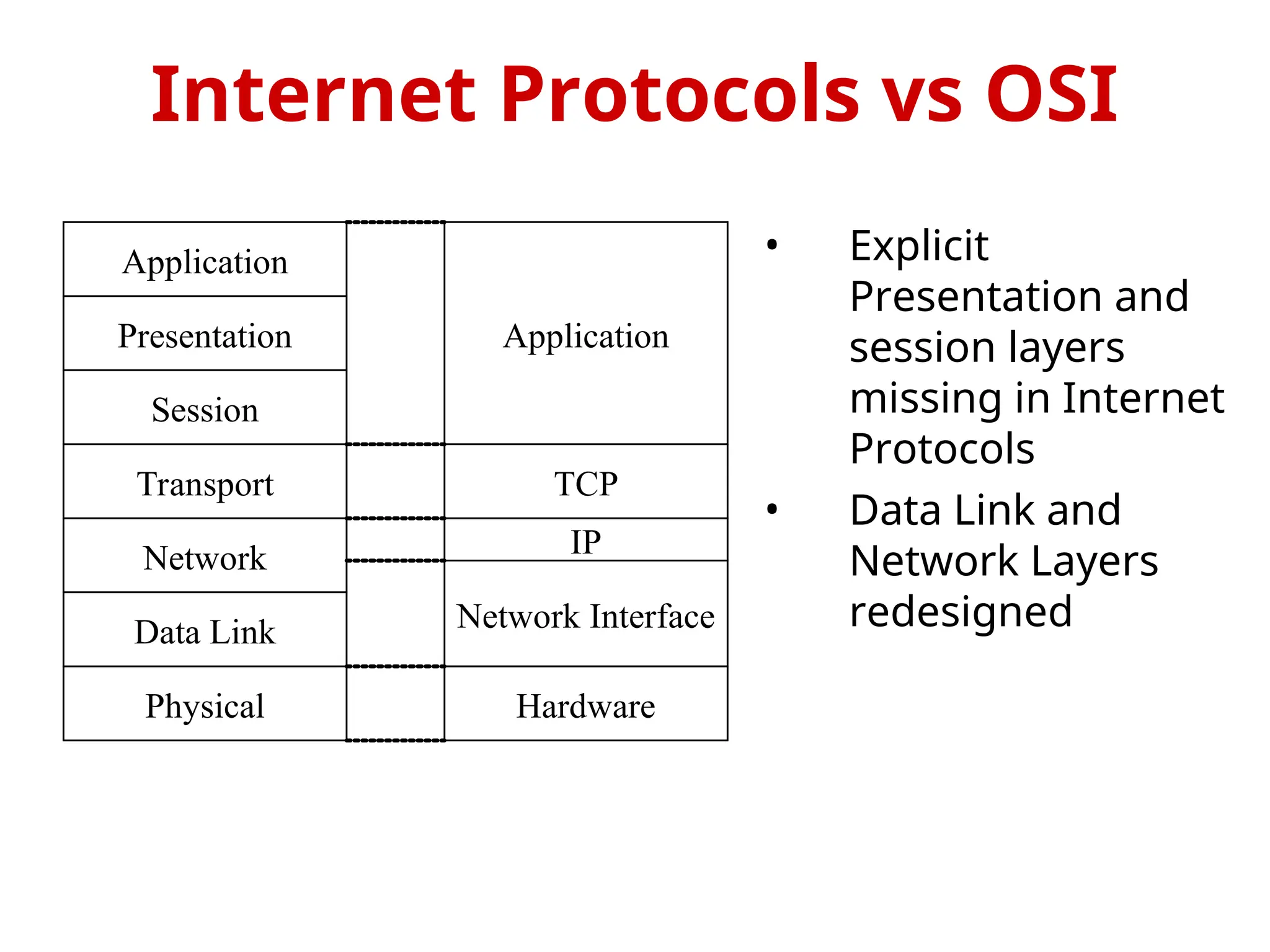
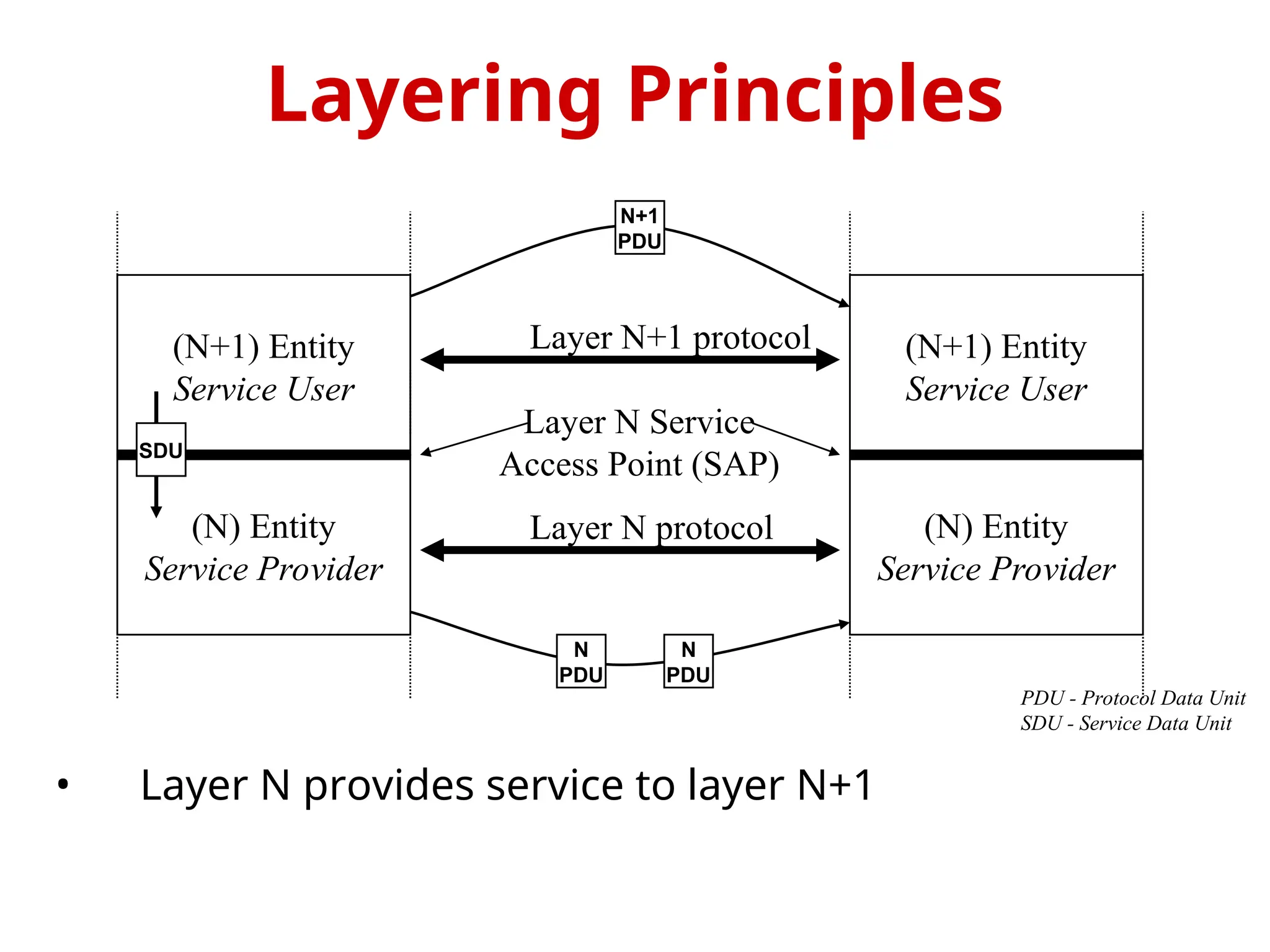
The document provides an overview of the OSI reference model, a standardized 7-layer architecture for network communications, where layers 1-4 focus on communication technology and layers 5-7 on user applications. Each layer has specific functions, such as data transmission, session management, and error handling, with services being provided to the layers above and consumed from the layers below. The OSI model emphasizes the importance of service quality and reliability in data communication, distinguishing between connection-oriented and connectionless services.