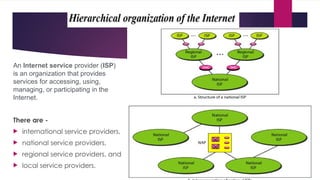
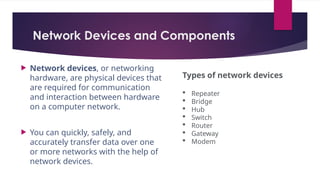
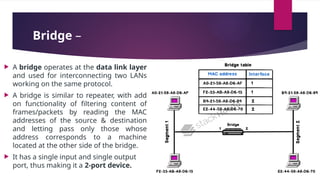
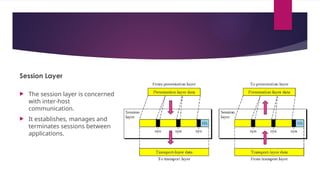
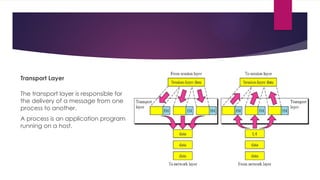
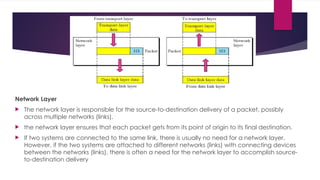
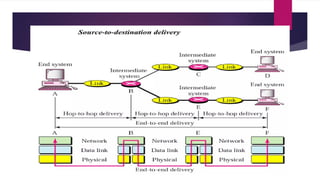
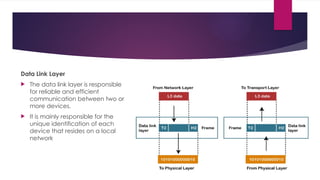
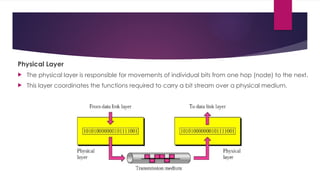
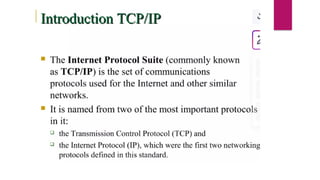
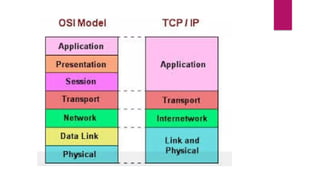
Resource Sharing
High Reliability
Inter-process Communication – if network users located geographically apart
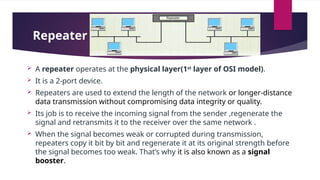
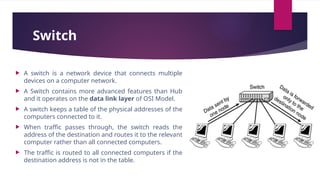
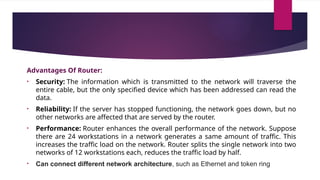
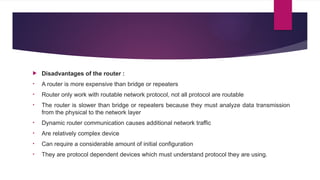
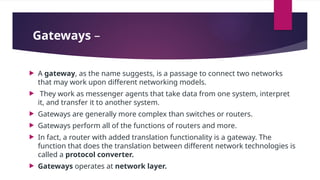
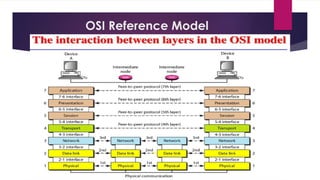
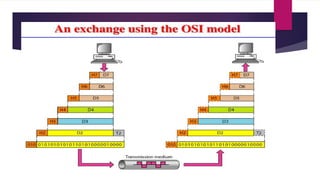
Flexible access – Files can be accessed from any computer in the network.A repeater operates at the physical layer(1st layer of OSI model).
It is a 2-port device.
Repeaters are used to extend the length of the network or longer-distance data transmission without compromising data integrity or quality.
Its job is to receive