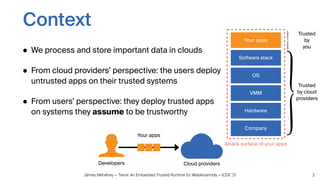
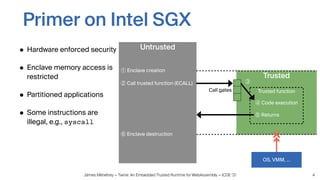
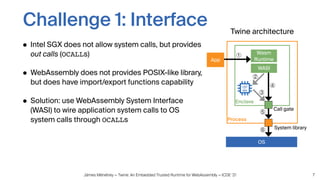
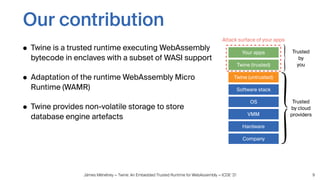
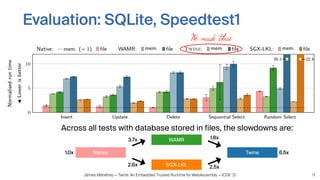
Twine is a trusted runtime that allows WebAssembly applications to execute securely within Intel SGX enclaves on untrusted cloud infrastructure. It addresses challenges of interfacing WebAssembly with hardware security modules and optimizing performance. Evaluations show Twine can execute SQLite compiled to WebAssembly within SGX enclaves with overhead of only 2.5-6.5x compared to native execution. Twine shields user applications while allowing them to be deployed across programming languages and hardware security environments.




![Jämes Ménétrey — Twine: An Embedded Trusted Runtime for WebAssembly — ICDE ‘21
Evaluation: SQLite, microbenchmark
12
0 50 100 150
0
1
2
EPC full
Database size [MiB]
Time
[s]
J
Lower
is
better
(a) Insertion
0 50 100 150
0
0.5
1
EPC full
Database size [MiB]
(b) Sequential reading
0 50 100 150
0
2
4
6
8
EPC full
Database size [MiB]
(c) Random reading
Native: mem. file SGX-LKL: mem. file WAMR: mem. file Twine: mem. file
• Enclave Page Cache (EPC) is a special memory area to store
the enclaves’ code and data (size of 92 MiB)
• Once full, encrypted memory pages are swapped out into
the unprotected memory, which is a costly operation
We made these](https://image.slidesharecdn.com/twine-presentation-final-230324142111-5d15fcd9/85/Twine-An-Embedded-Trusted-Runtime-for-WebAssembly-Presentation-slides-12-320.jpg)
![Jämes Ménétrey — Twine: An Embedded Trusted Runtime for WebAssembly — ICDE ‘21
Evaluation: SQLite, microbenchmark
13
Insertion Sequential Random
0
0.5
1
Type of query
Normalised
run
time
J
Lower
is
better
Twine: HW SW SGX-LKL: HW SW
2.5x
3.3x 0.9x
Slowdowns
0 50 100 150
0
1
2
EPC full
Database size [MiB]
Time
[s]
J
Lower
is
better
(a) Insertion
0 50 100 150
0
0.5
1
EPC full
Database size [MiB]
(b) Sequential reading
0 50 100 150
0
2
4
6
8
EPC full
Database size [MiB]
(c) Random reading
Native: mem. file SGX-LKL: mem. file WAMR: mem. file Twine: mem. file
We made these](https://image.slidesharecdn.com/twine-presentation-final-230324142111-5d15fcd9/85/Twine-An-Embedded-Trusted-Runtime-for-WebAssembly-Presentation-slides-13-320.jpg)
![Jämes Ménétrey — Twine: An Embedded Trusted Runtime for WebAssembly — ICDE ‘21
Optimisations: Intel Protected File System
• Optimisations:
• Memory clearing operations have been removed
• Memory copy operations have been reduced
• Speedup compared to Intel’s version with SQLite:
• Insertion: 1.5x
• Sequential reading: 2.5x
• Random reading: 4.1x
14
0 5 10 15 20 25 30
IPFS
Optimised
Time [s] (J Lower is better)
SQLite inner work Read: other ops. OCALL memset](https://image.slidesharecdn.com/twine-presentation-final-230324142111-5d15fcd9/85/Twine-An-Embedded-Trusted-Runtime-for-WebAssembly-Presentation-slides-14-320.jpg)
