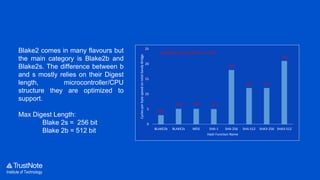
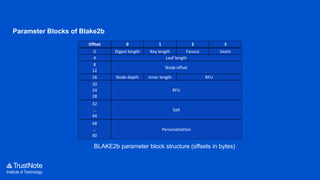
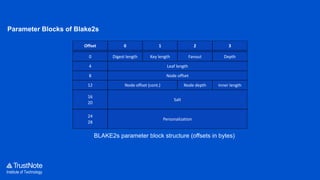
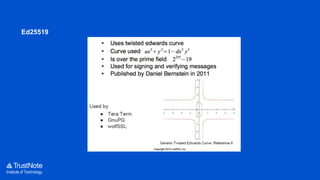
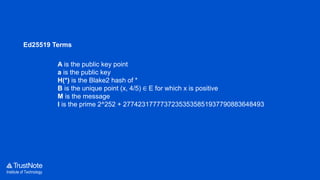
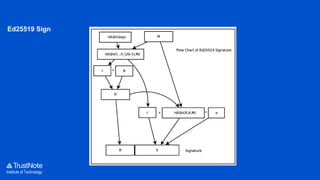
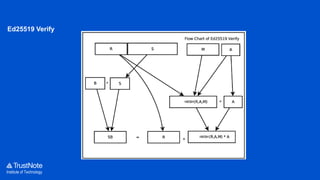
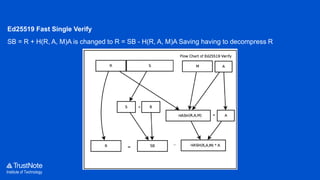
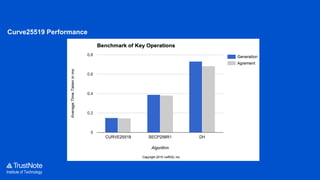
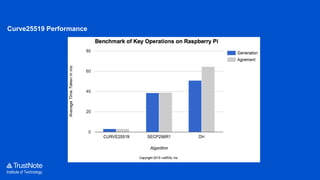
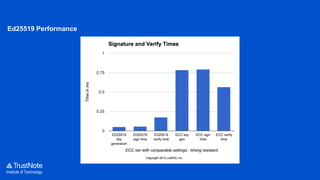
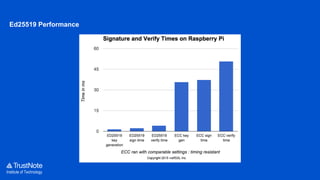
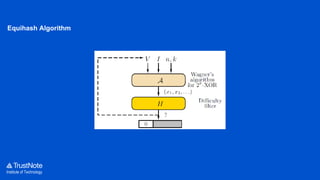
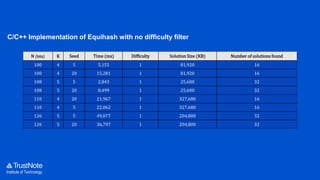
The document provides an overview of the cryptographic algorithms used by Trustnote, highlighting the use of Blake2 as the hash function for its high hash rate and reliability, and Ed25519 as the signature algorithm due to its fast performance and high security. It details the structure and parameters of Blake2b and Blake2s, as well as the signing and verification steps for the Ed25519 algorithm. Additionally, it mentions Equihash for its ASIC resistance and fairness, providing performance metrics for various implementations.