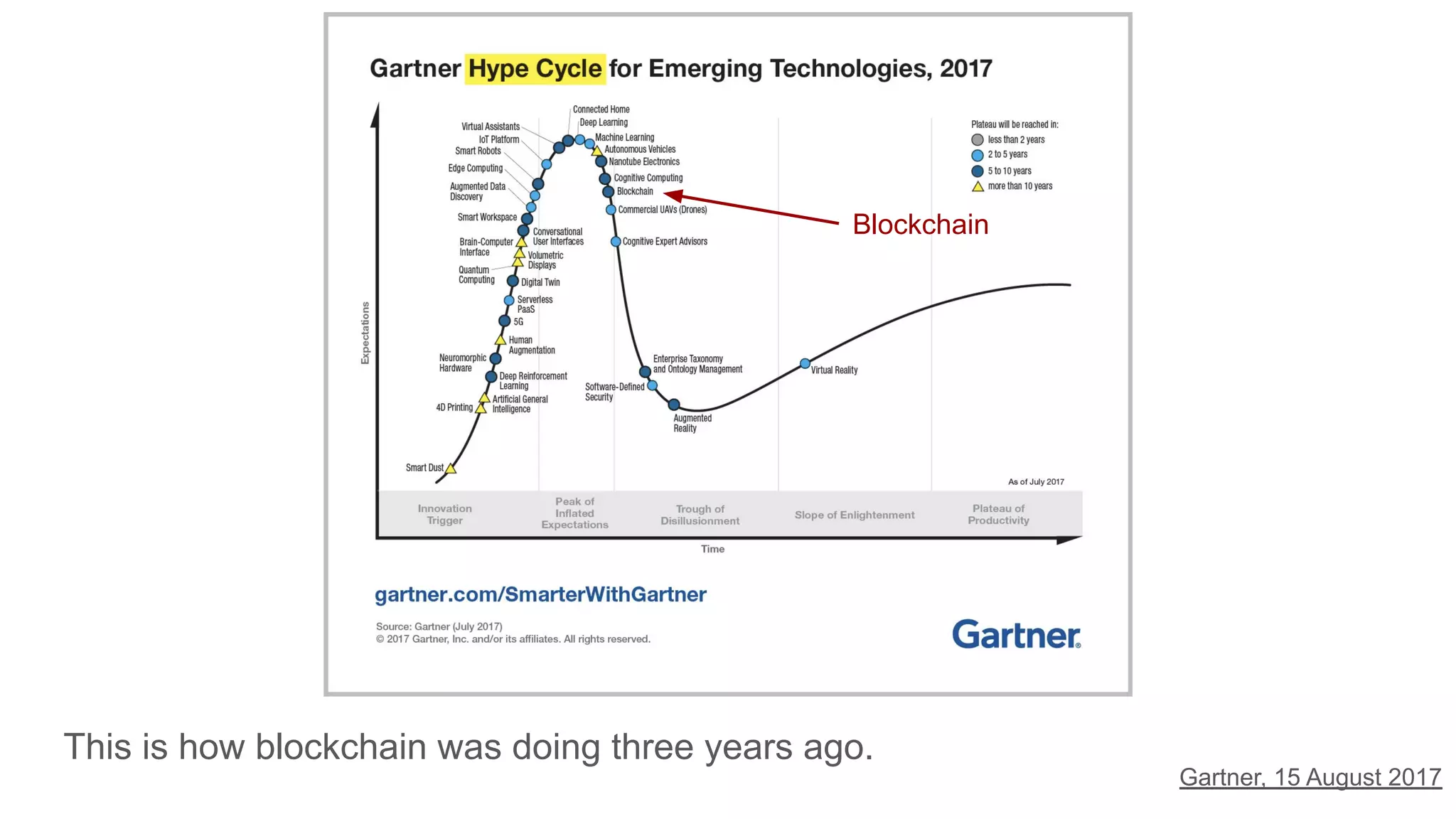
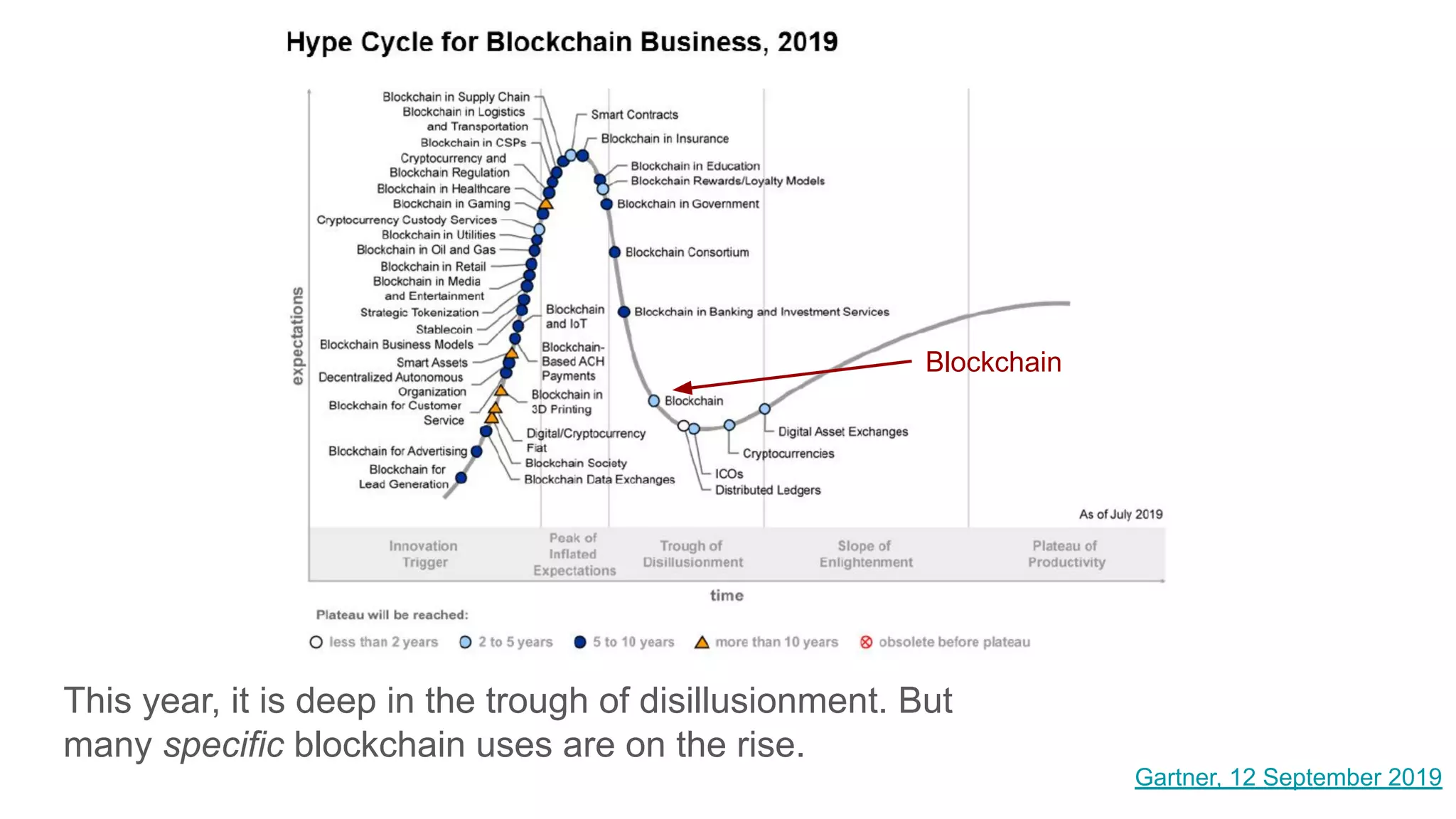
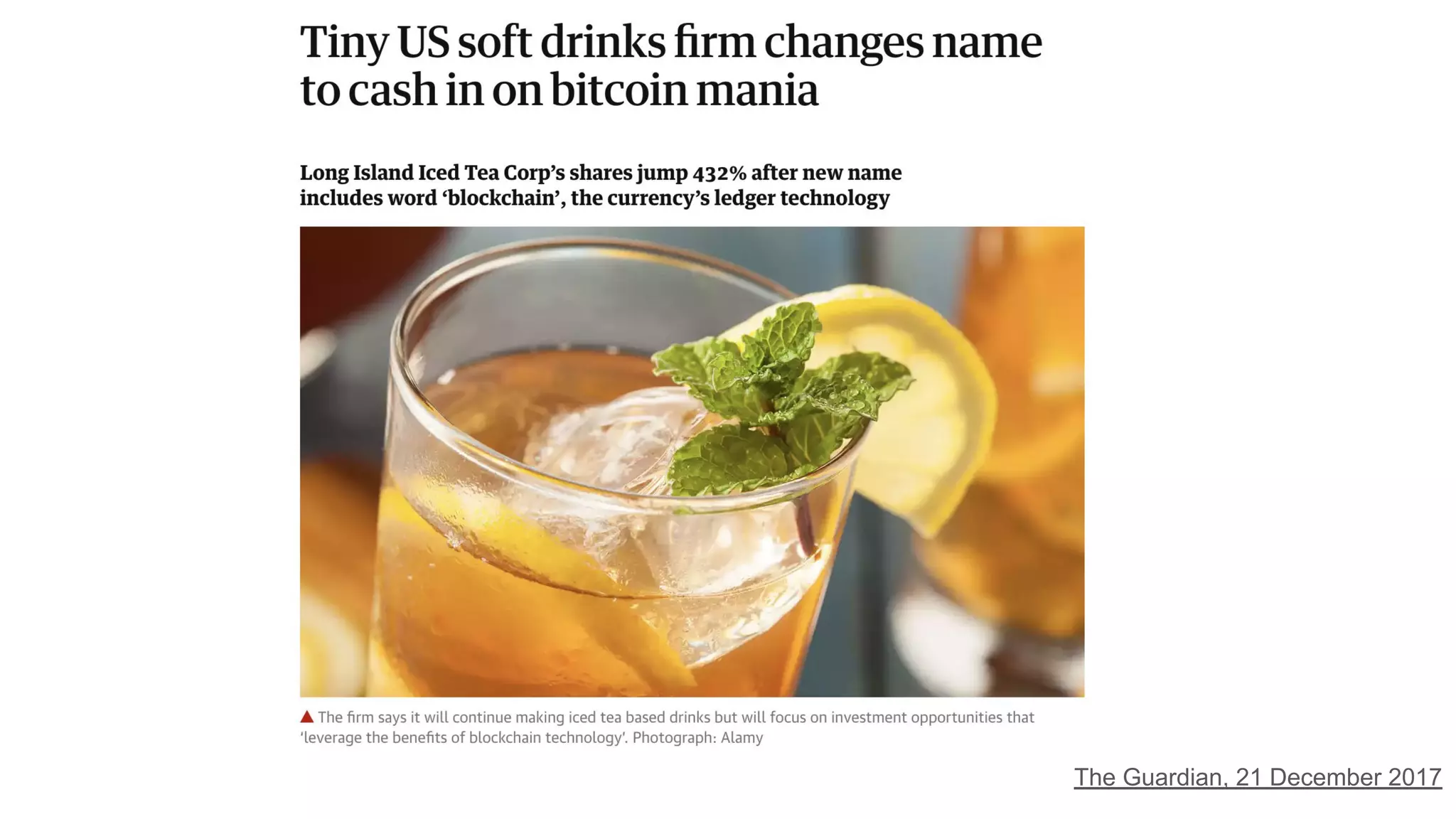
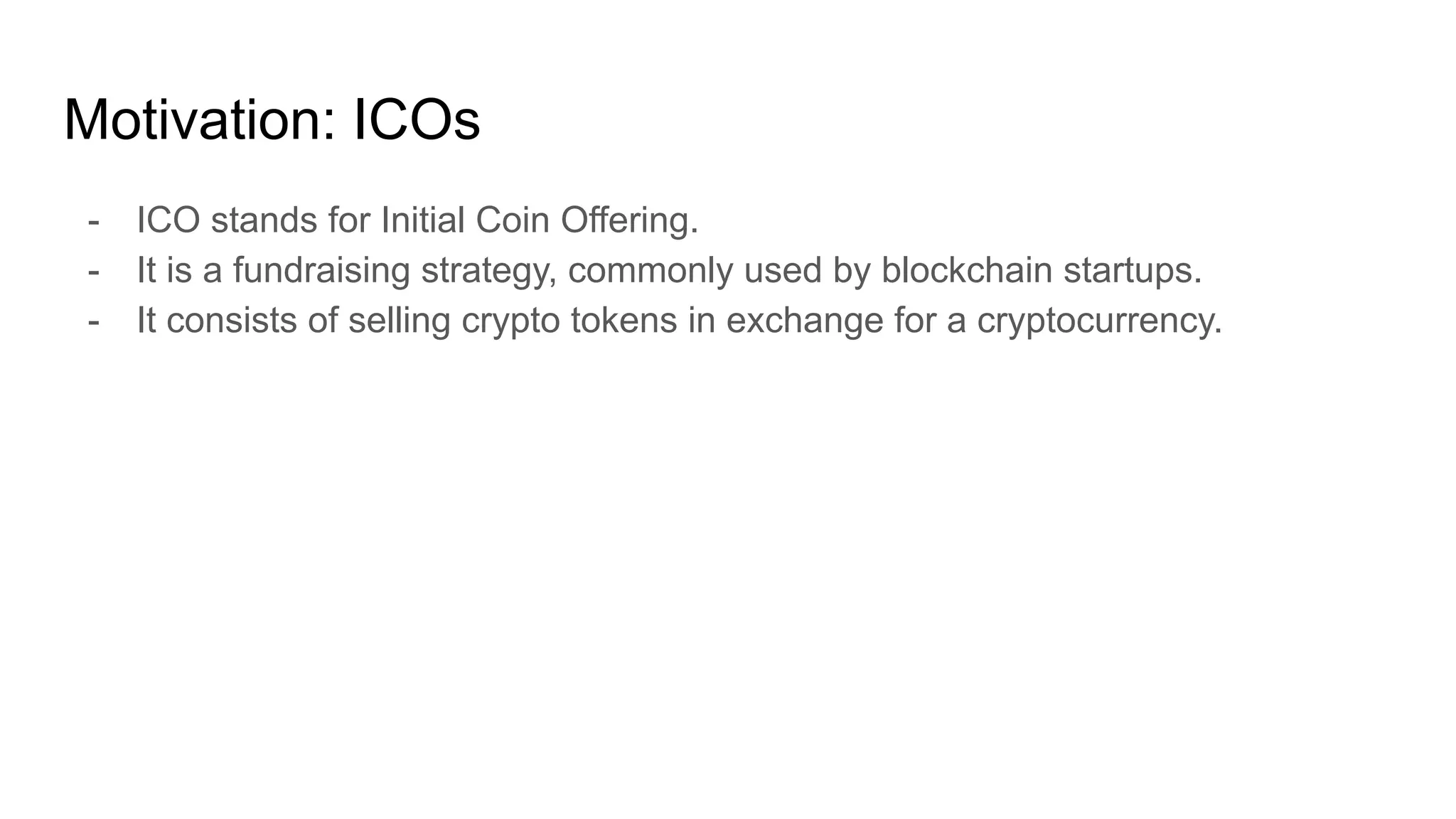
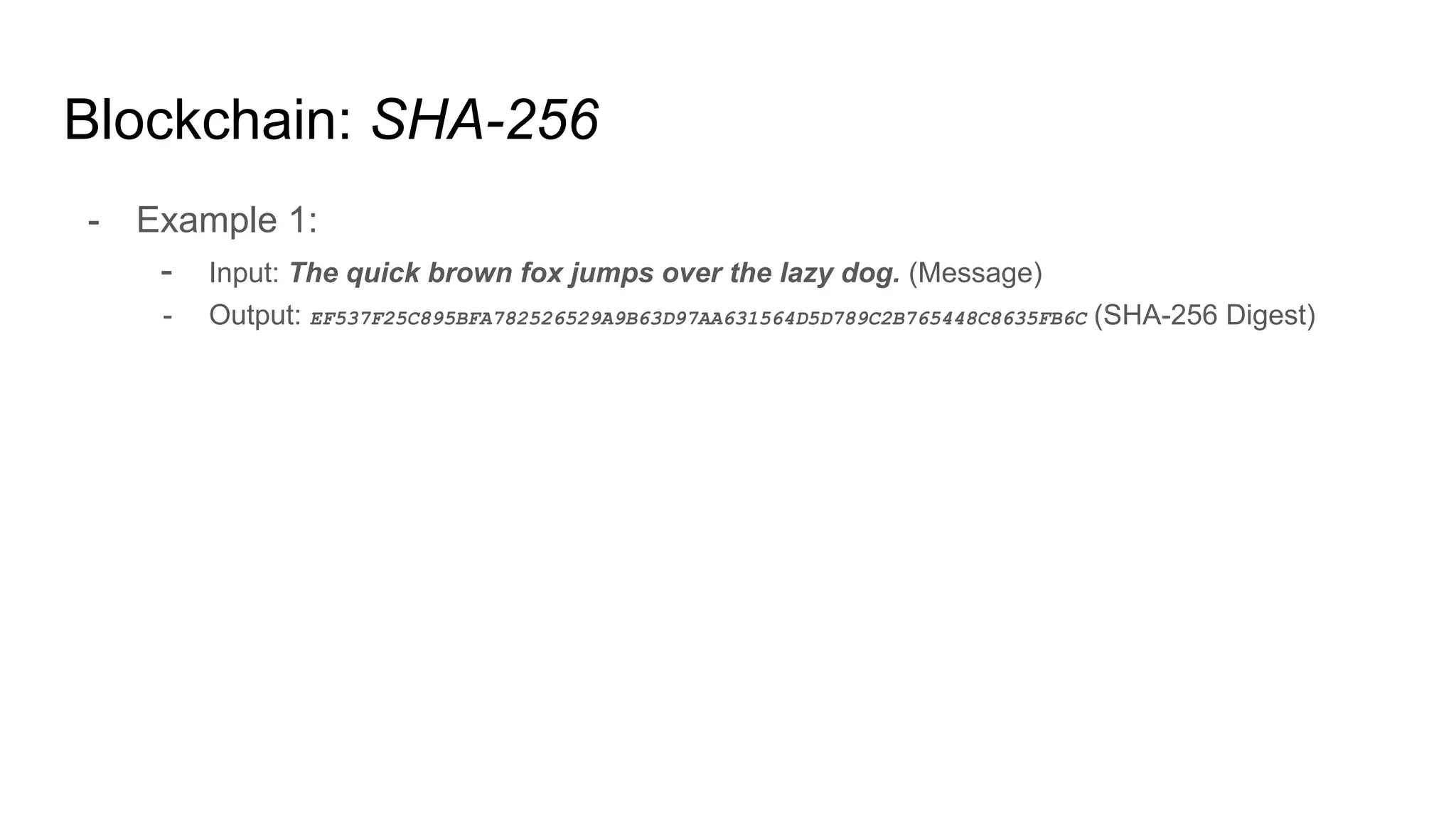
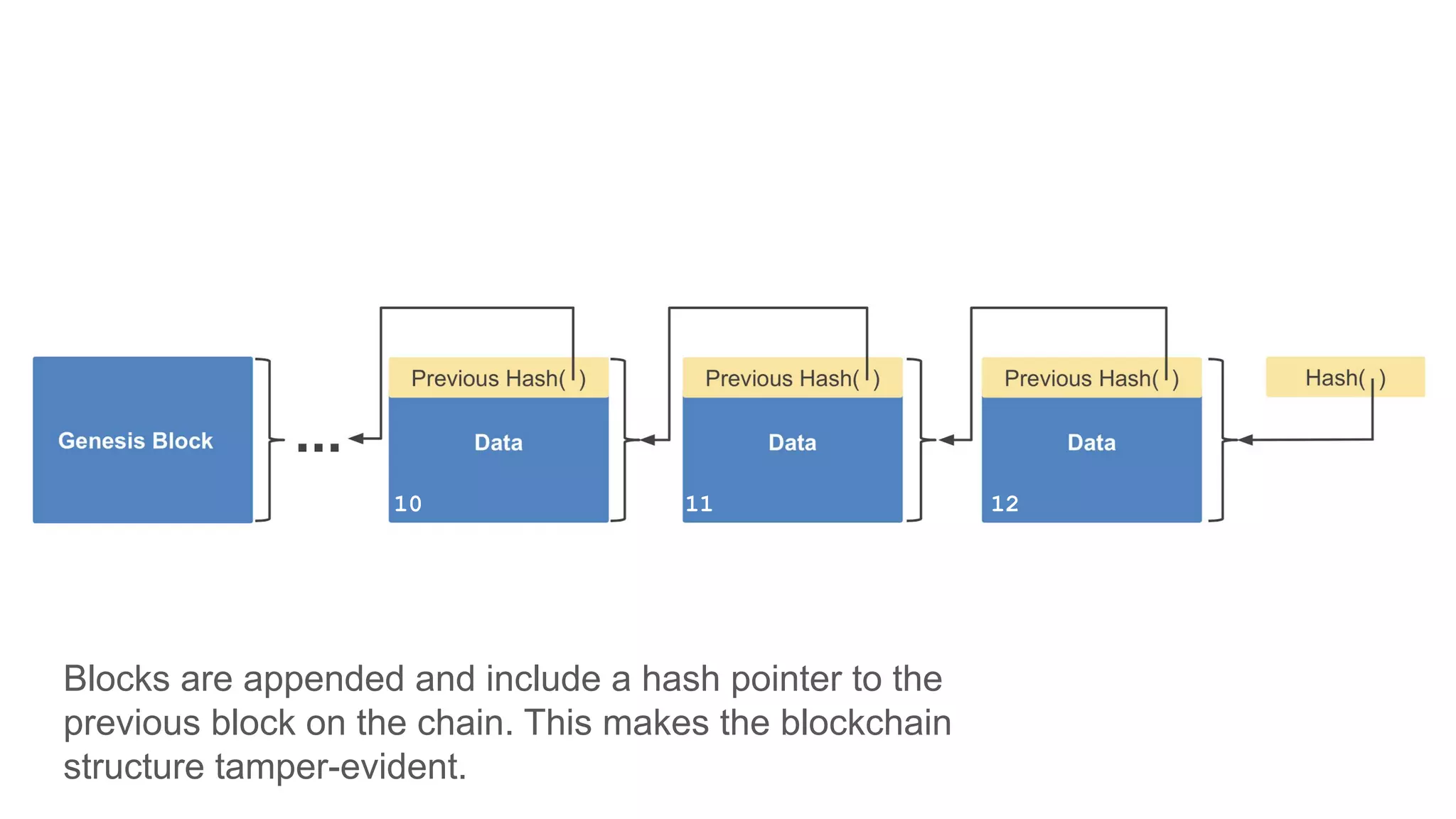
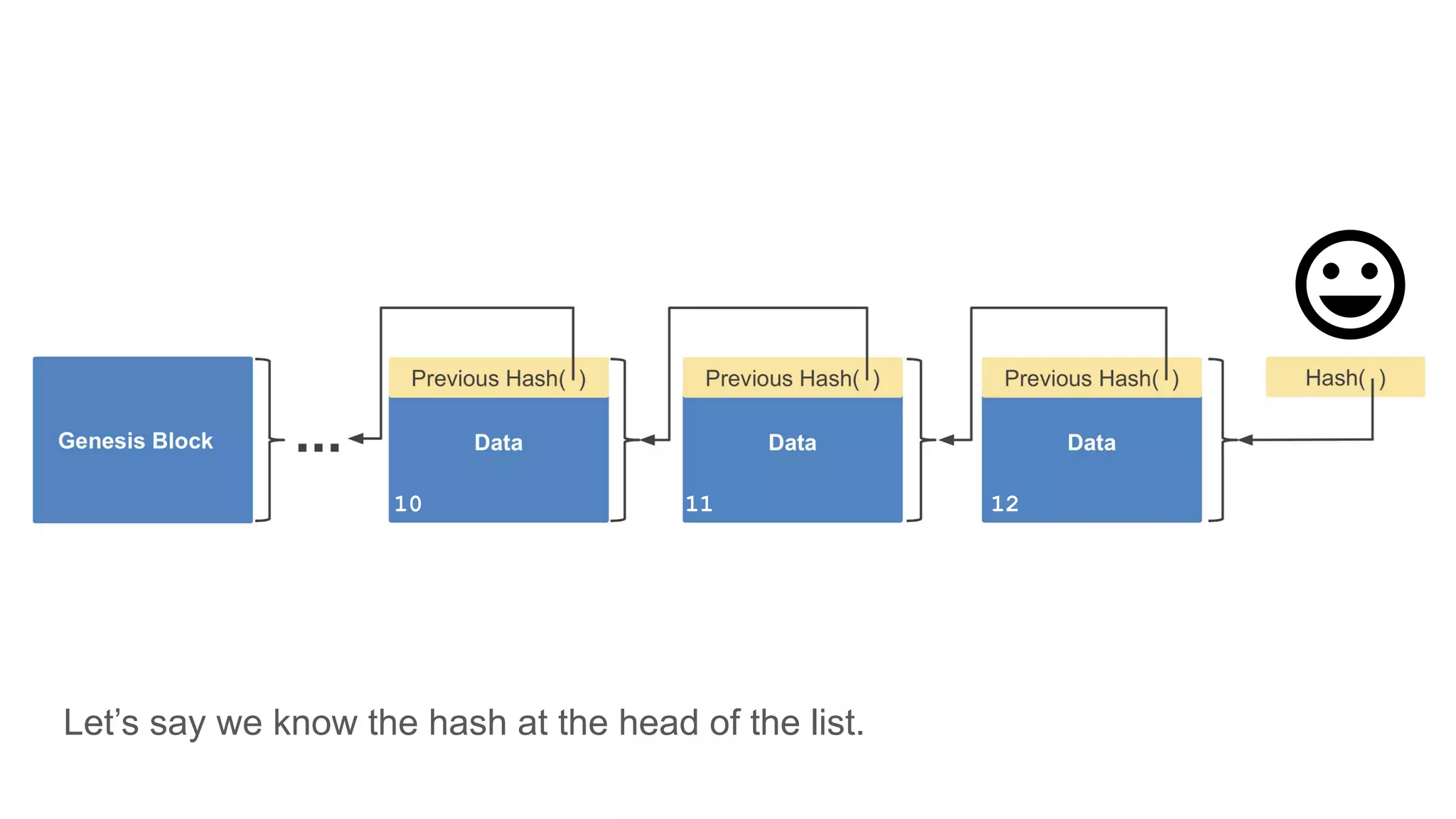
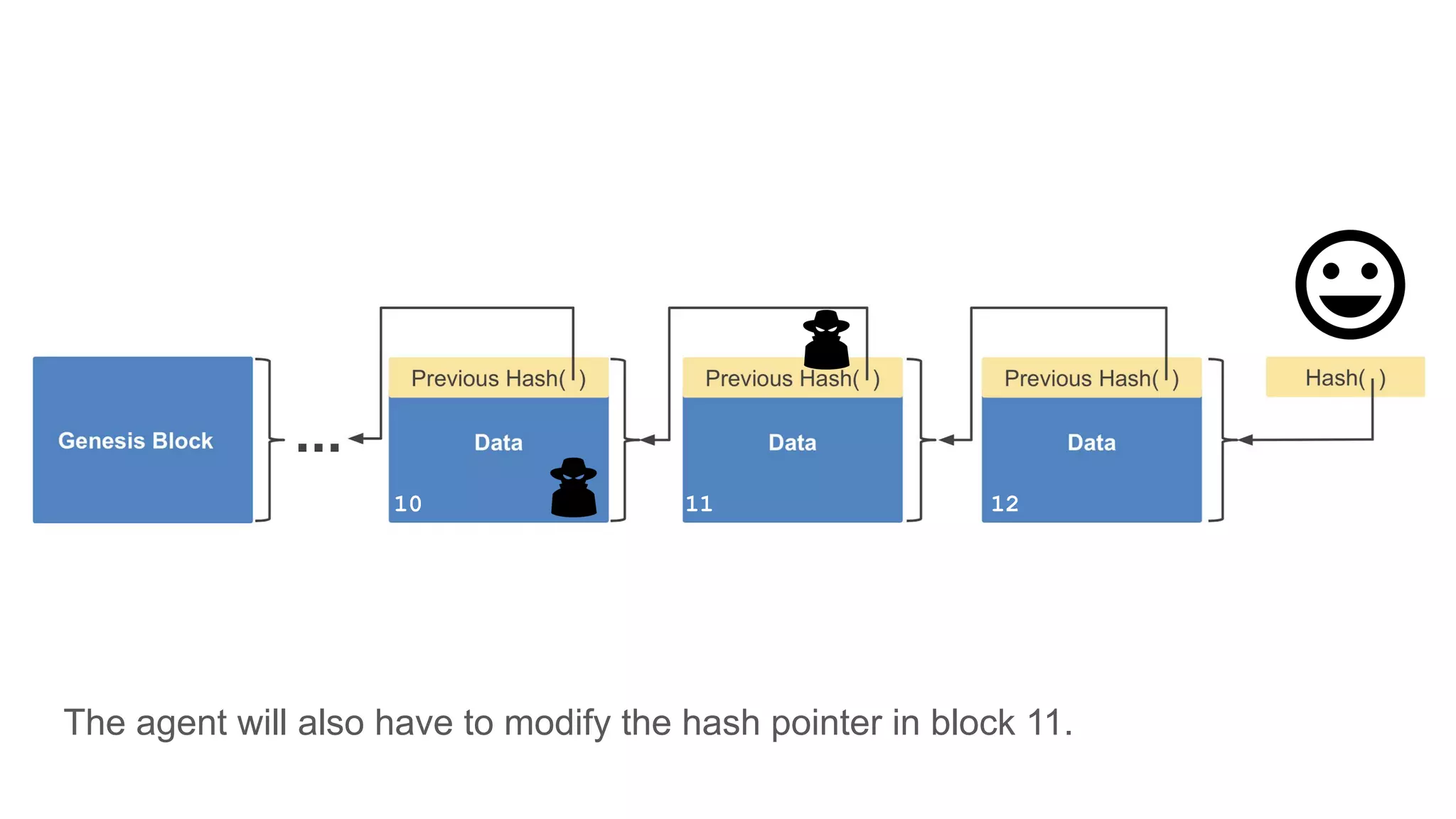
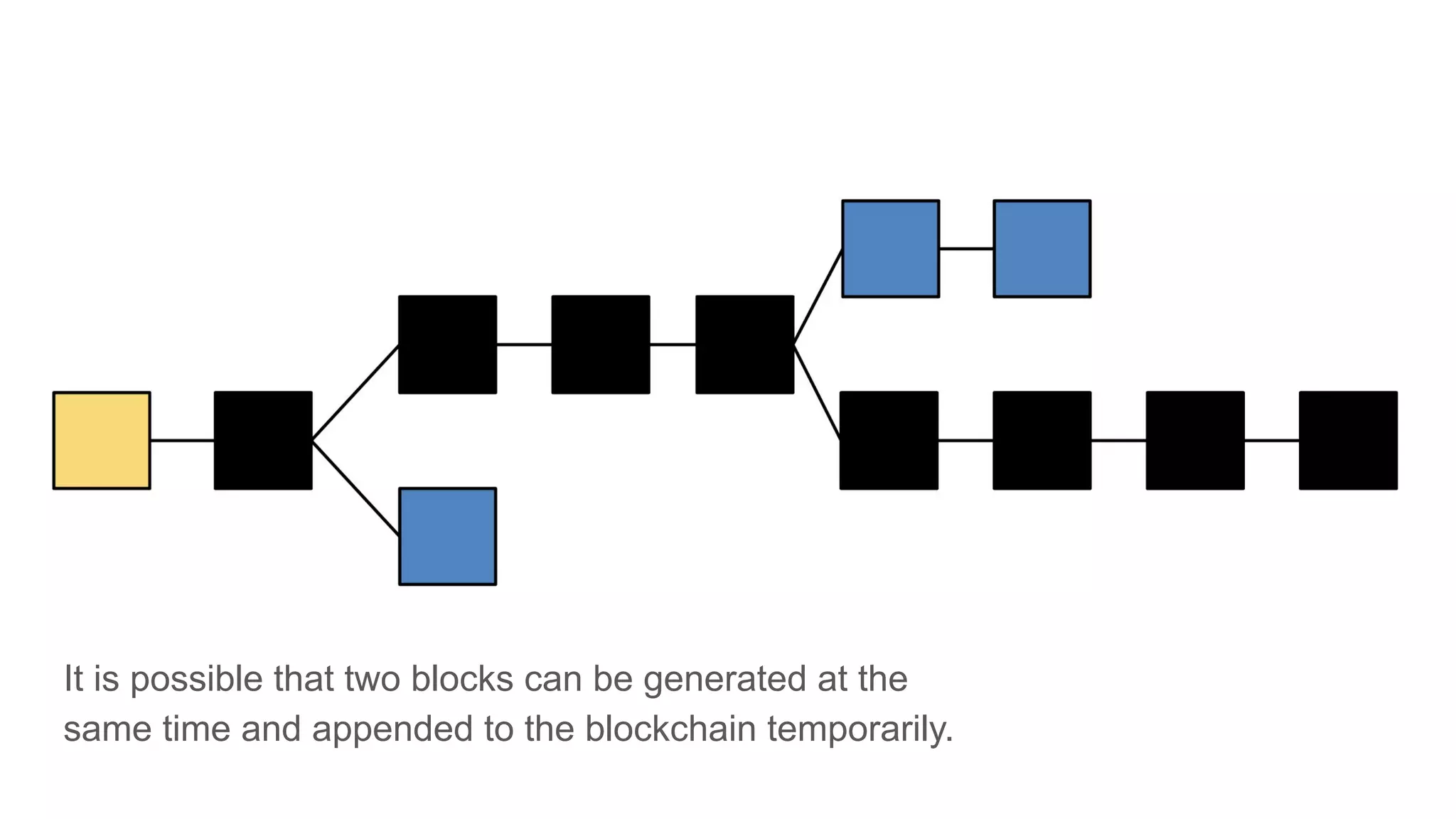
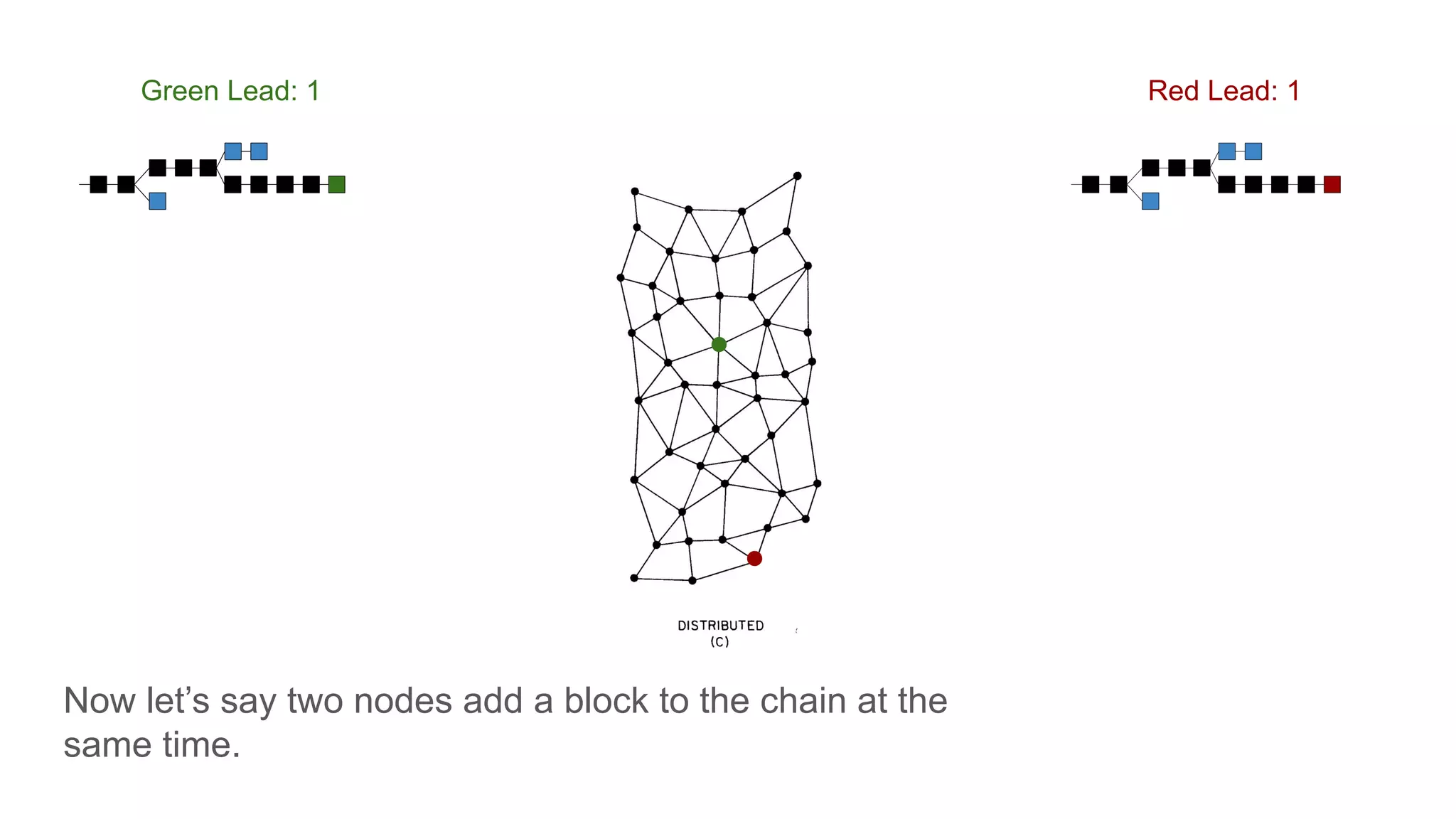
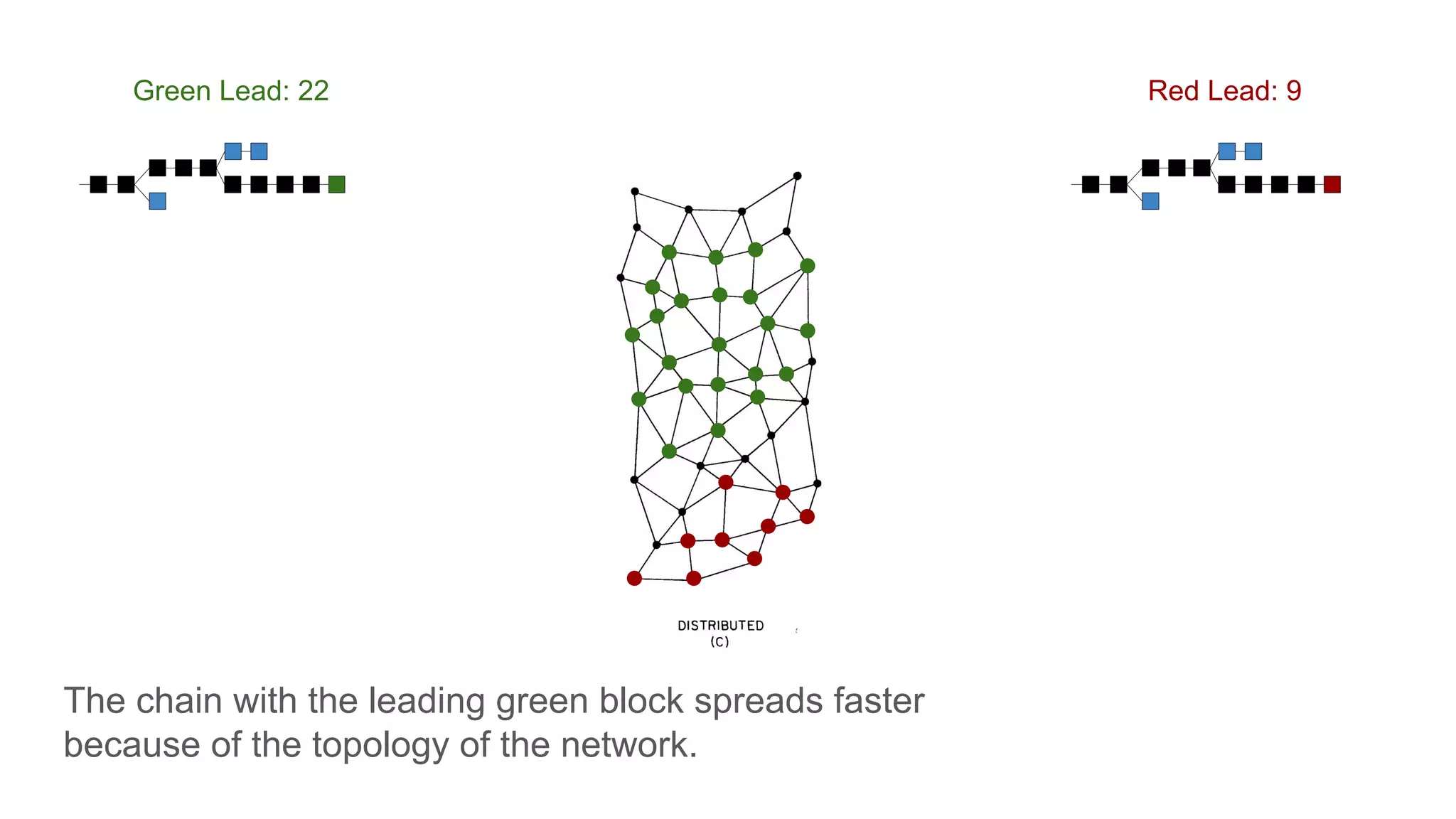
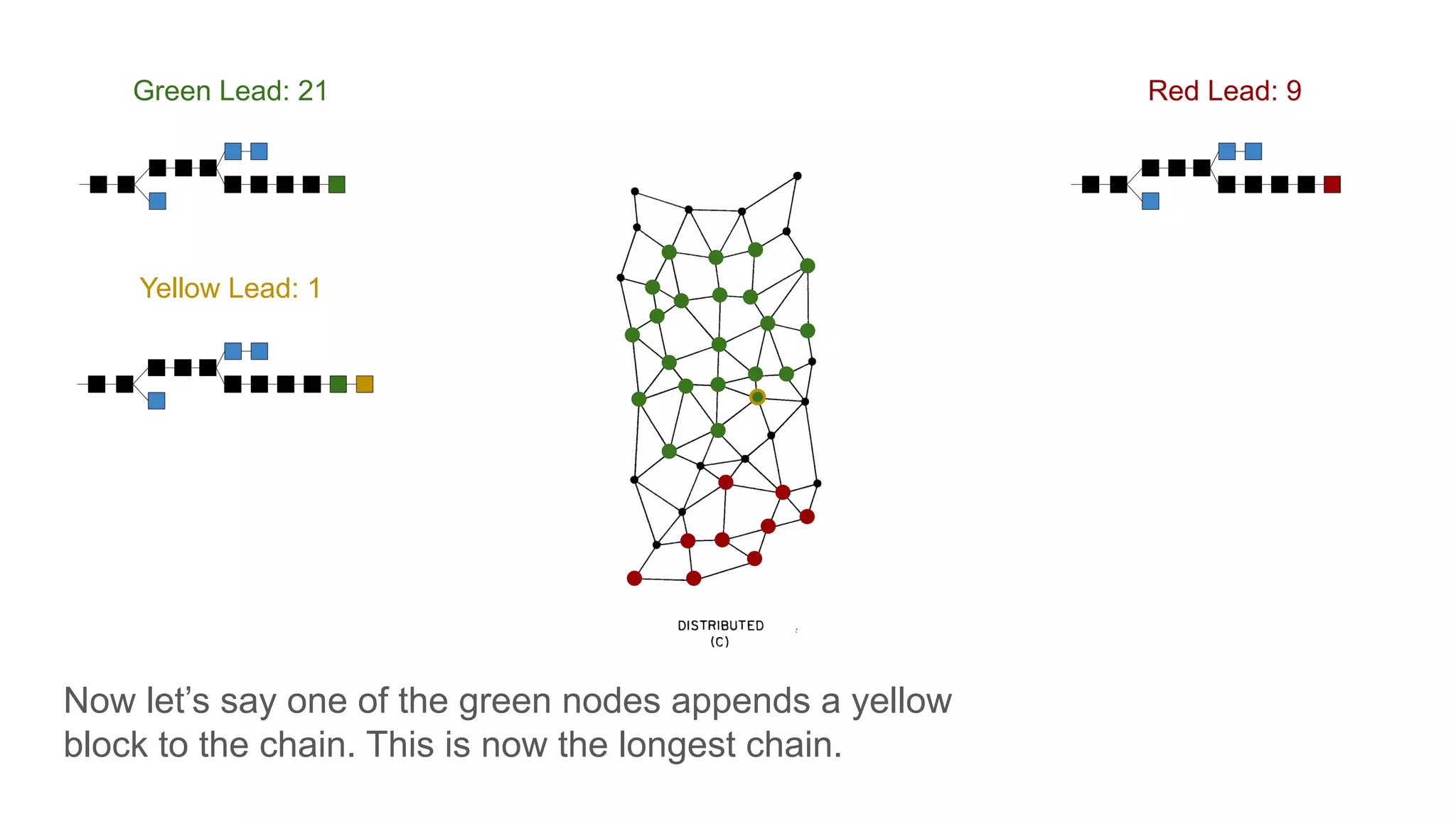
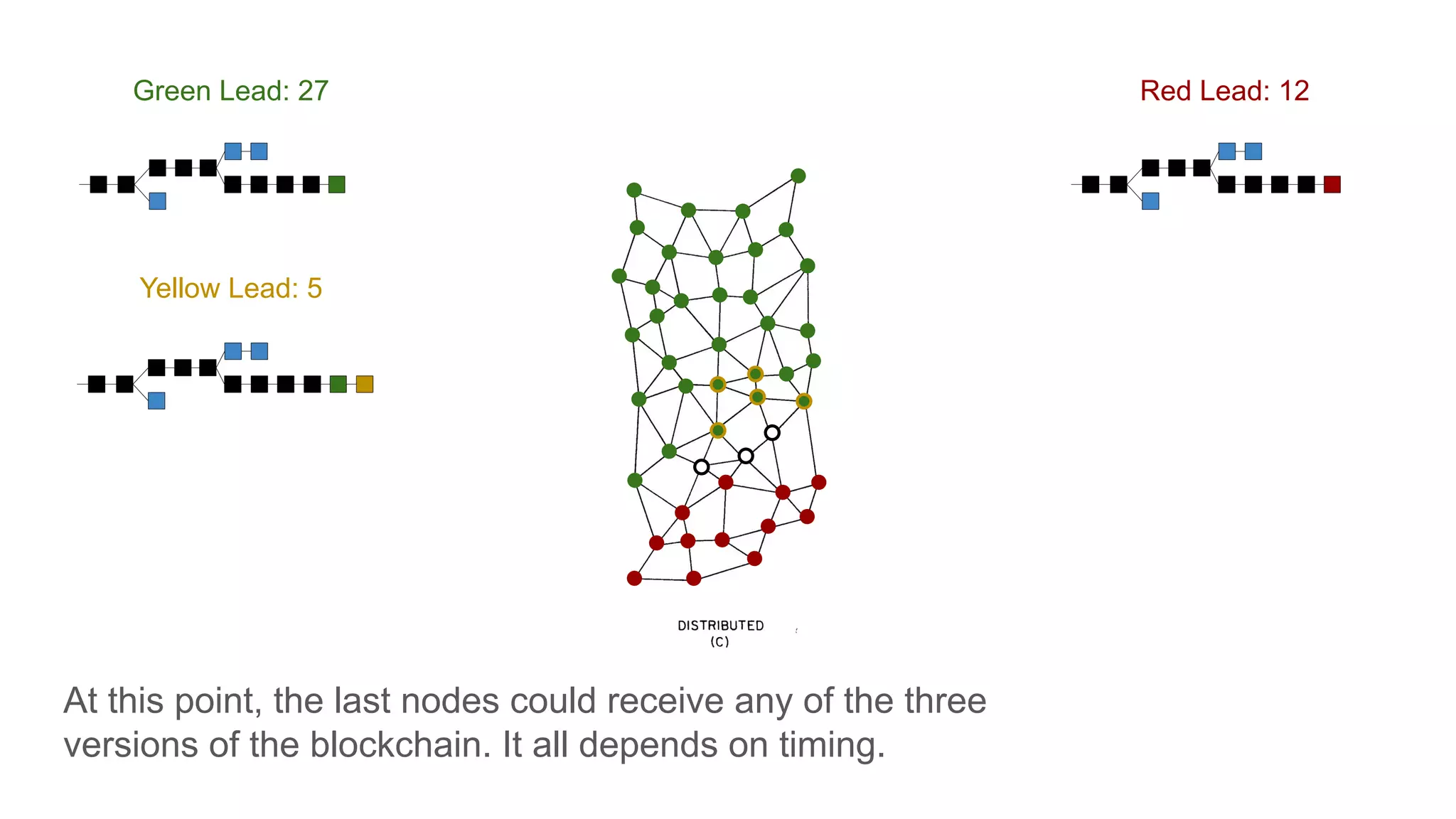
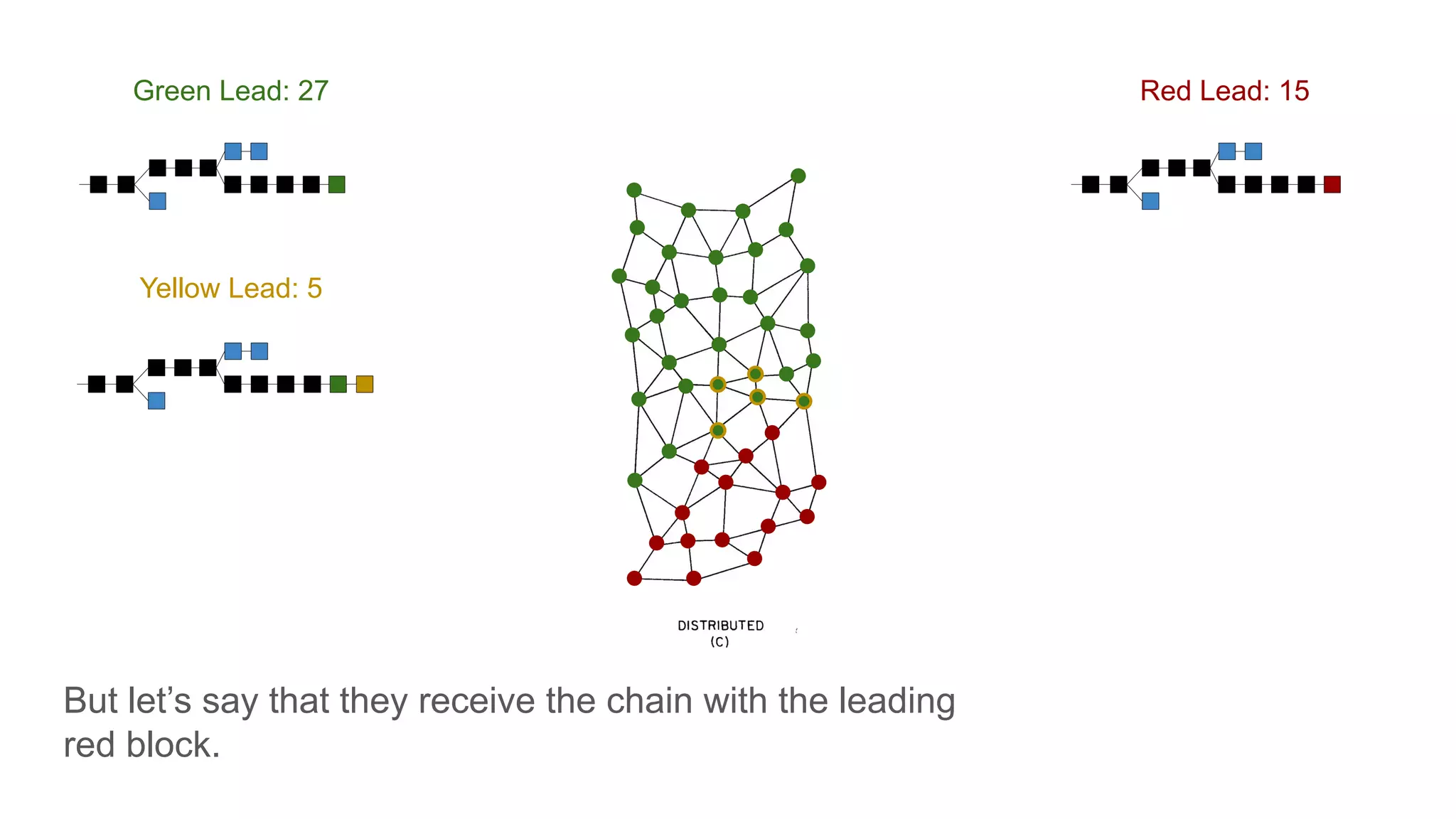
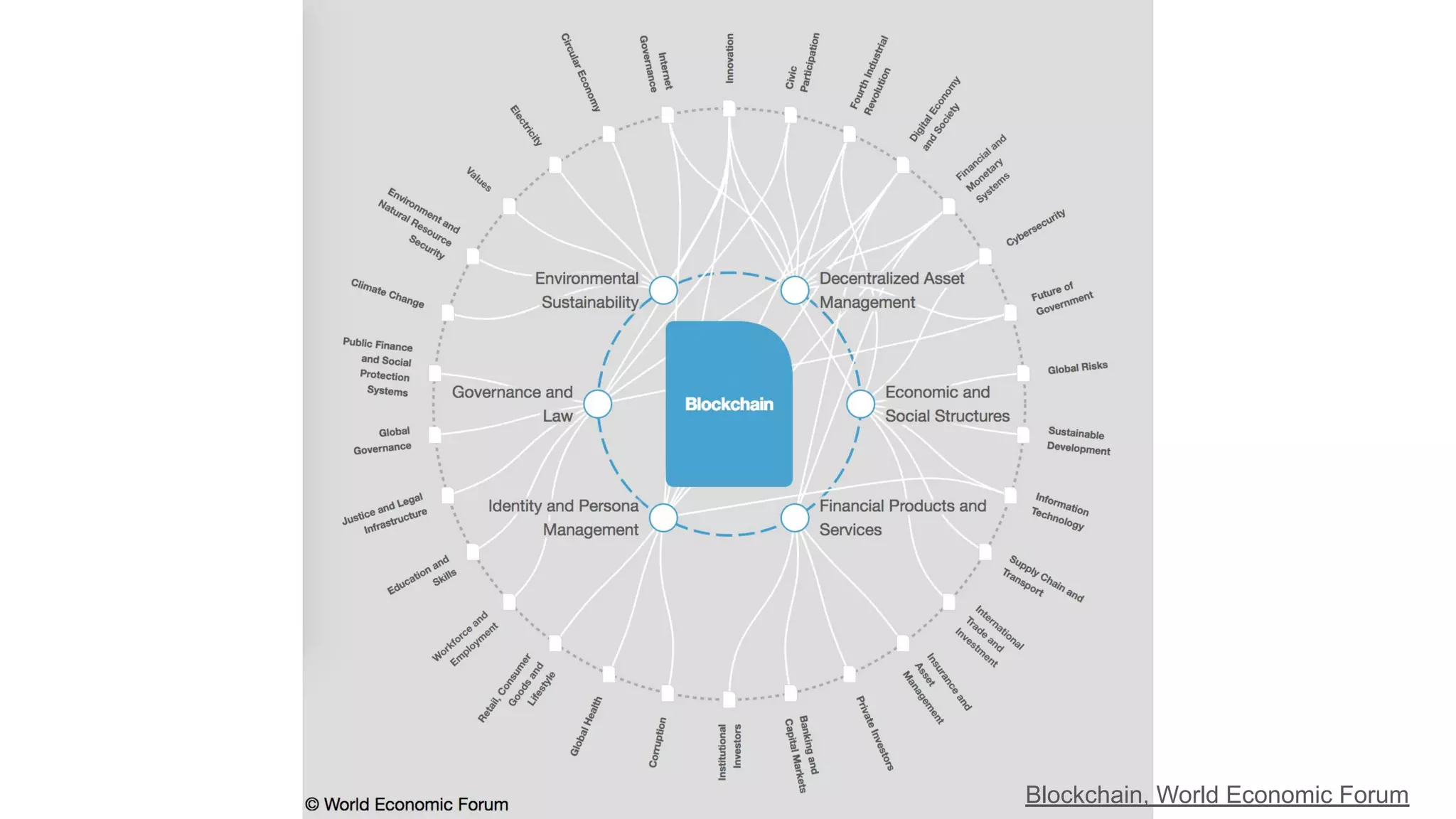
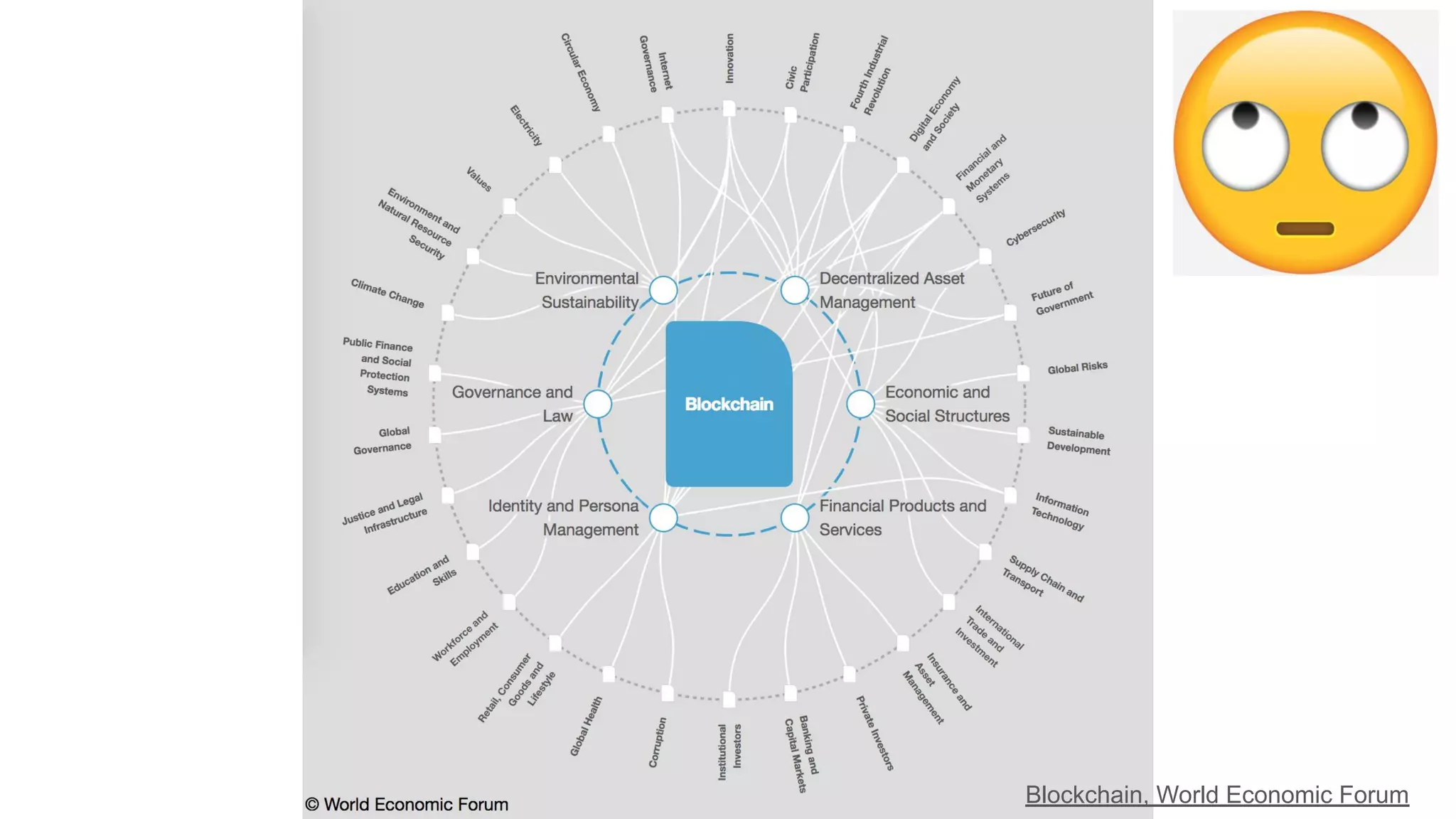
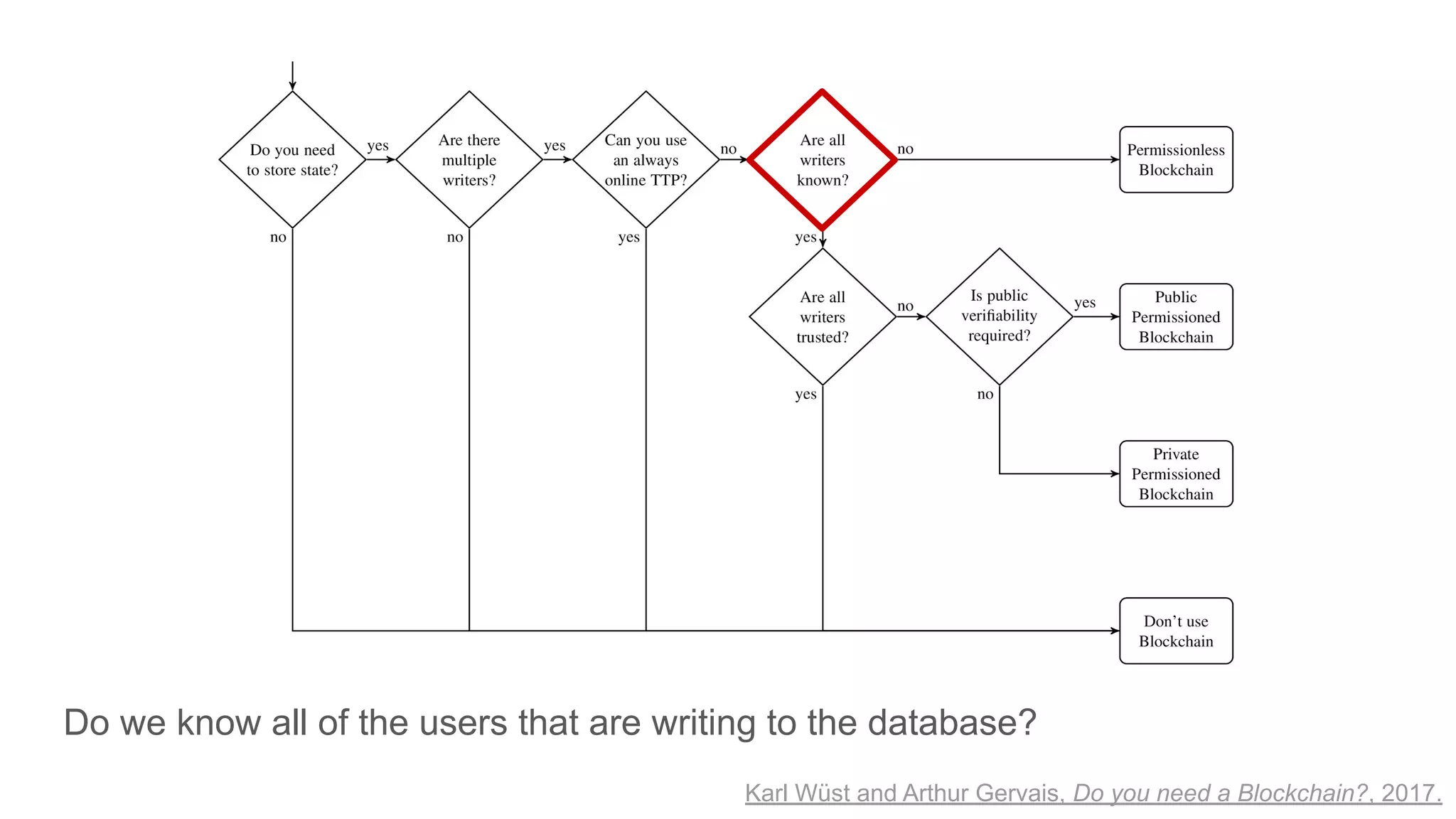
The document explores the concepts of trust, privacy, and blockchain, emphasizing their interconnectedness across various domains such as philosophy, law, and sociology. It provides definitions of trust and privacy, discusses measurement methods for trustworthiness, and models of reputation in digital contexts. Furthermore, it highlights the importance of privacy and trust in personal development and societal interaction, referencing historical perspectives and philosophical viewpoints.












![“Trust is in the end a practical matter. It’s a question of trying
to place it intelligently. [...] With trust, you want to trust things
that are trustworthy and mistrust what’s untrustworthy. And in
both cases the evidence is incomplete and it’s quite difficult.”
Onora O’Neill, Trust, BBC Radio 4 Analysis (2011)](https://image.slidesharecdn.com/trustprivacyandtheblockchain2020-200305142923/75/Trust-Privacy-and-the-Blockchain-15-2048.jpg)
![“Trust is in the end a practical matter. It’s a question of trying
to place it intelligently. [...] With trust, you want to trust things
that are trustworthy and mistrust what’s untrustworthy. And in
both cases the evidence is incomplete and it’s quite difficult.”
Onora O’Neill, Trust, BBC Radio 4 Analysis (2011)](https://image.slidesharecdn.com/trustprivacyandtheblockchain2020-200305142923/75/Trust-Privacy-and-the-Blockchain-16-2048.jpg)







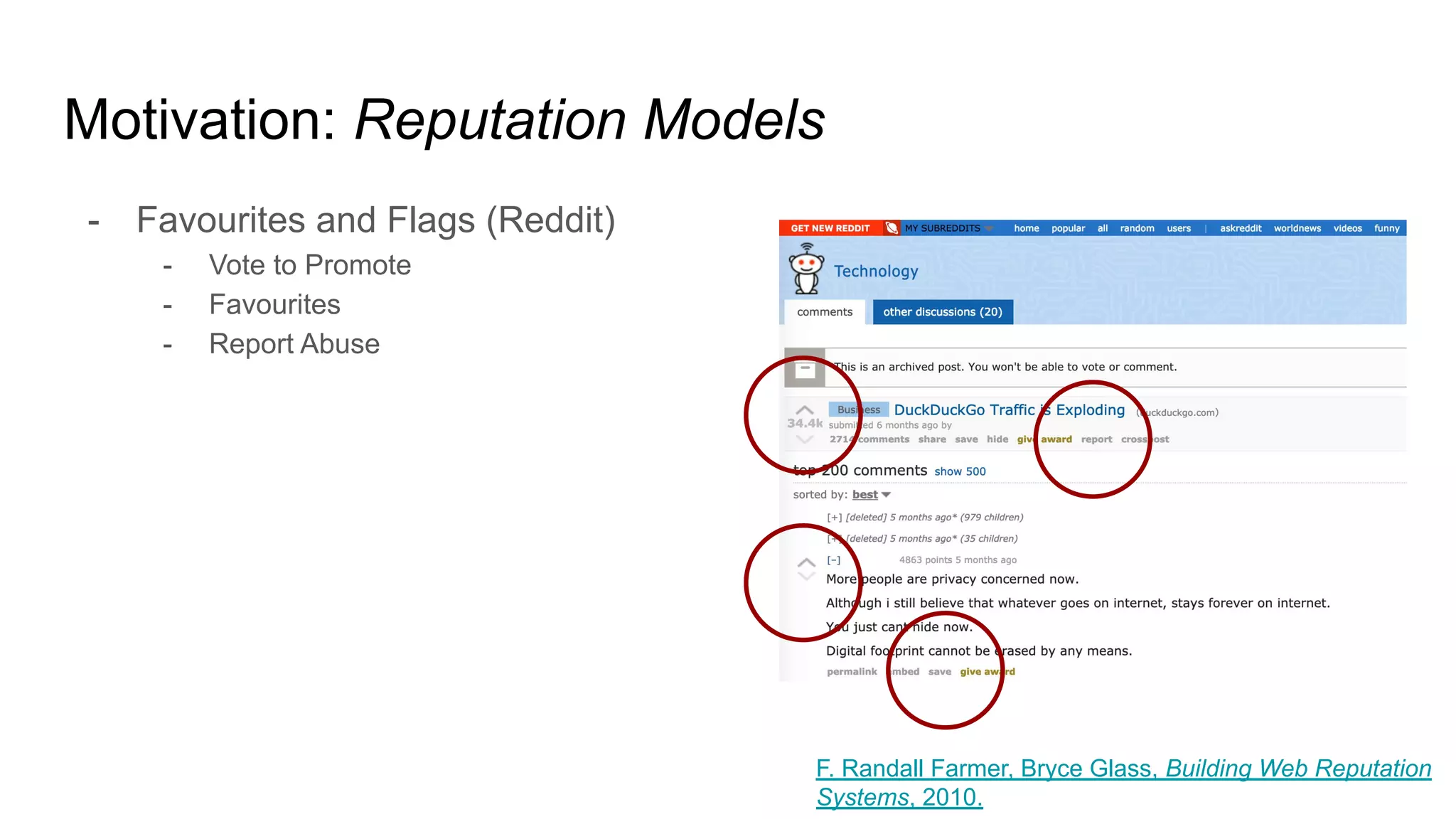
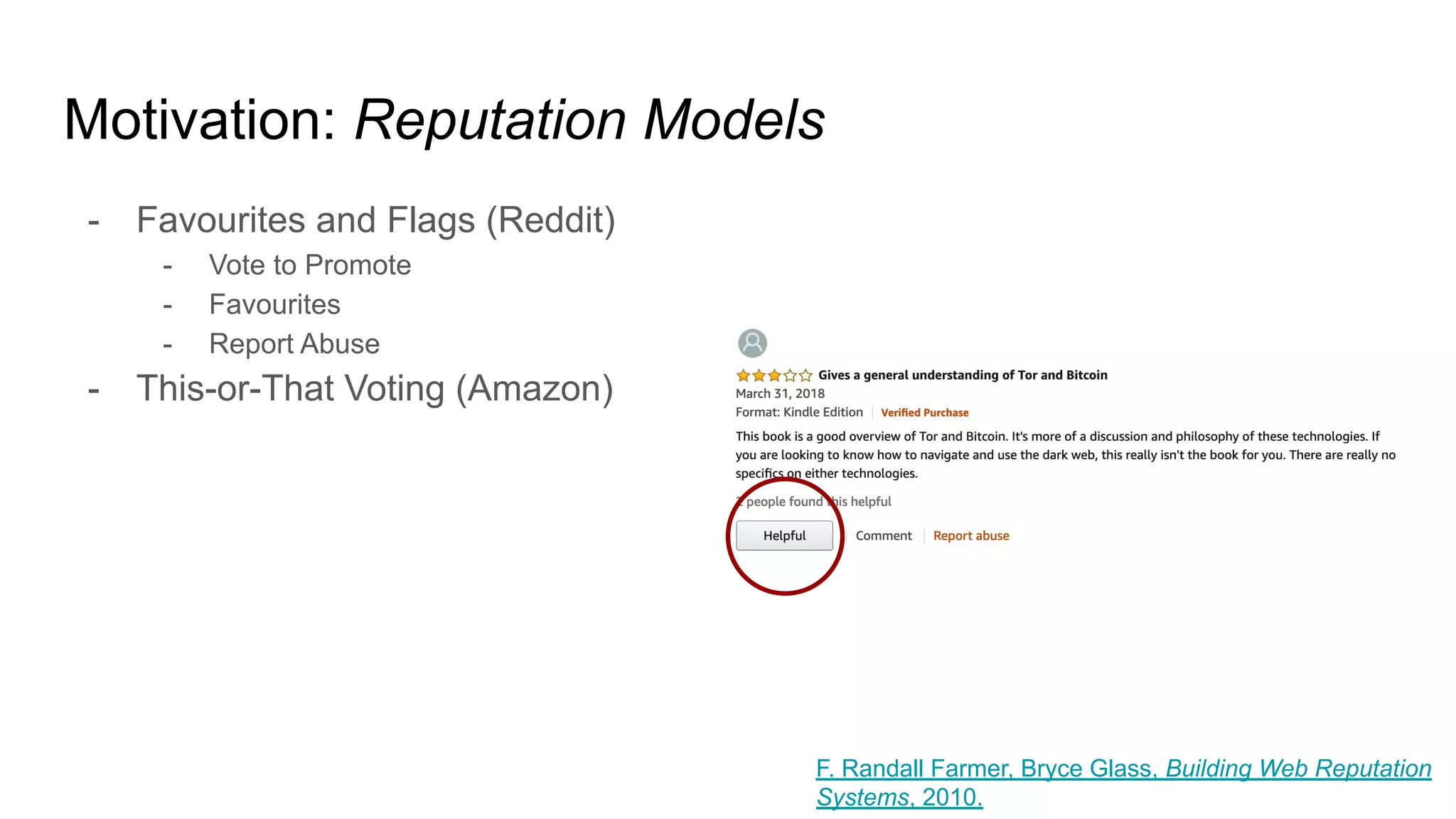
![Motivation: Reputation
- “Reputation is information used to make a value judgment about an object
or a person.”
- Value judgments can be decisive, continuous and expressive.
- E.g. thumbs up, favourite, rating, review, etc.
- The object or person in question is a reputable entity (i.e. can have a reputation).
- The information is a reputation statement.
- E.g. a city is worth visiting, an article is worth reading, a movie is bad.
- Reputation takes place within a context (geography, subject, purpose).
- E.g. local universities, winter tires, abstract art, etc.
- Reputation is often limited in scope, which can or not be surfaced globally.
- E.g. favourite restaurants vs internal employee reviews.
- “[Reputation] brings structure to chaos by allowing us to proxy trust when
making day-to-day decisions.” F. Randall Farmer, Bryce Glass, Building Web Reputation
Systems, 2010.](https://image.slidesharecdn.com/trustprivacyandtheblockchain2020-200305142923/75/Trust-Privacy-and-the-Blockchain-24-2048.jpg)






![Motivation: Why is trust important?
“[Trust] matters because the world is quite uncertain and
getting it right is very useful. It’s very useful if I know whom I
can rely on for which purpose and whom I can’t rely on.”
Onora O’Neill, Trust, BBC Radio 4 Analysis (2011)](https://image.slidesharecdn.com/trustprivacyandtheblockchain2020-200305142923/75/Trust-Privacy-and-the-Blockchain-33-2048.jpg)
![Motivation: Why is trust important?
More lightly speaking... how would your behaviour change
if you were not sure you could trust [ ]?](https://image.slidesharecdn.com/trustprivacyandtheblockchain2020-200305142923/75/Trust-Privacy-and-the-Blockchain-34-2048.jpg)





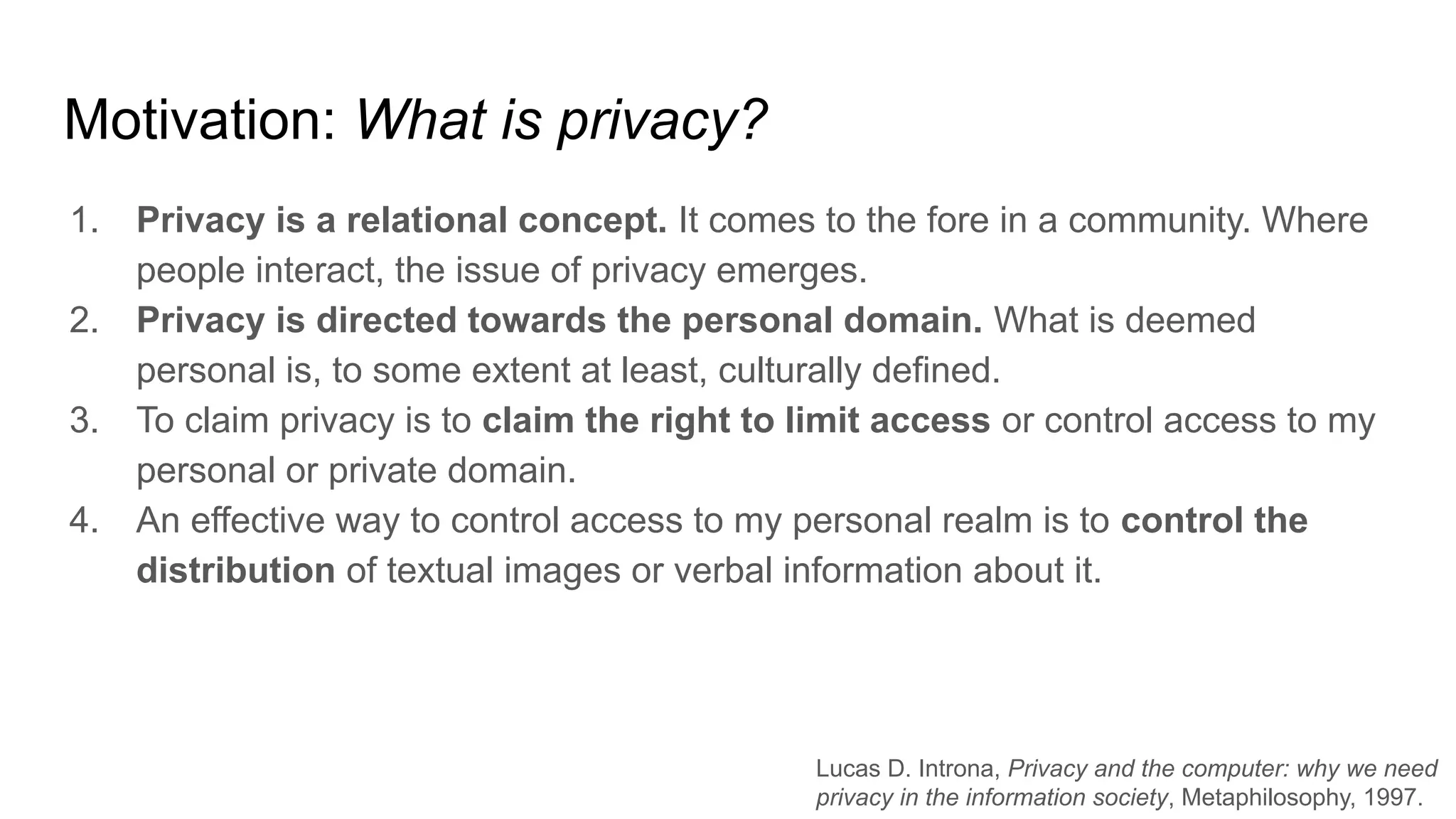









![Motivation: But is privacy really that important?
- In 1975, French philosopher Michel Foucault revisited the panopticon in his
book Discipline and Punish.
- There are panoptic methods operated throughout a disciplinary society (in
schools, factories, hospitals, military regiments, prison), which allows it to
keep its citizens under control and conforming to certain norms.
- Discipline, through these methods, creates “docile bodies”.
- Docile bodies are “something that can be made; out of a formless clay,
an inapt body [from which] the machine required can be constructed.”
- Importance of training.](https://image.slidesharecdn.com/trustprivacyandtheblockchain2020-200305142923/75/Trust-Privacy-and-the-Blockchain-51-2048.jpg)