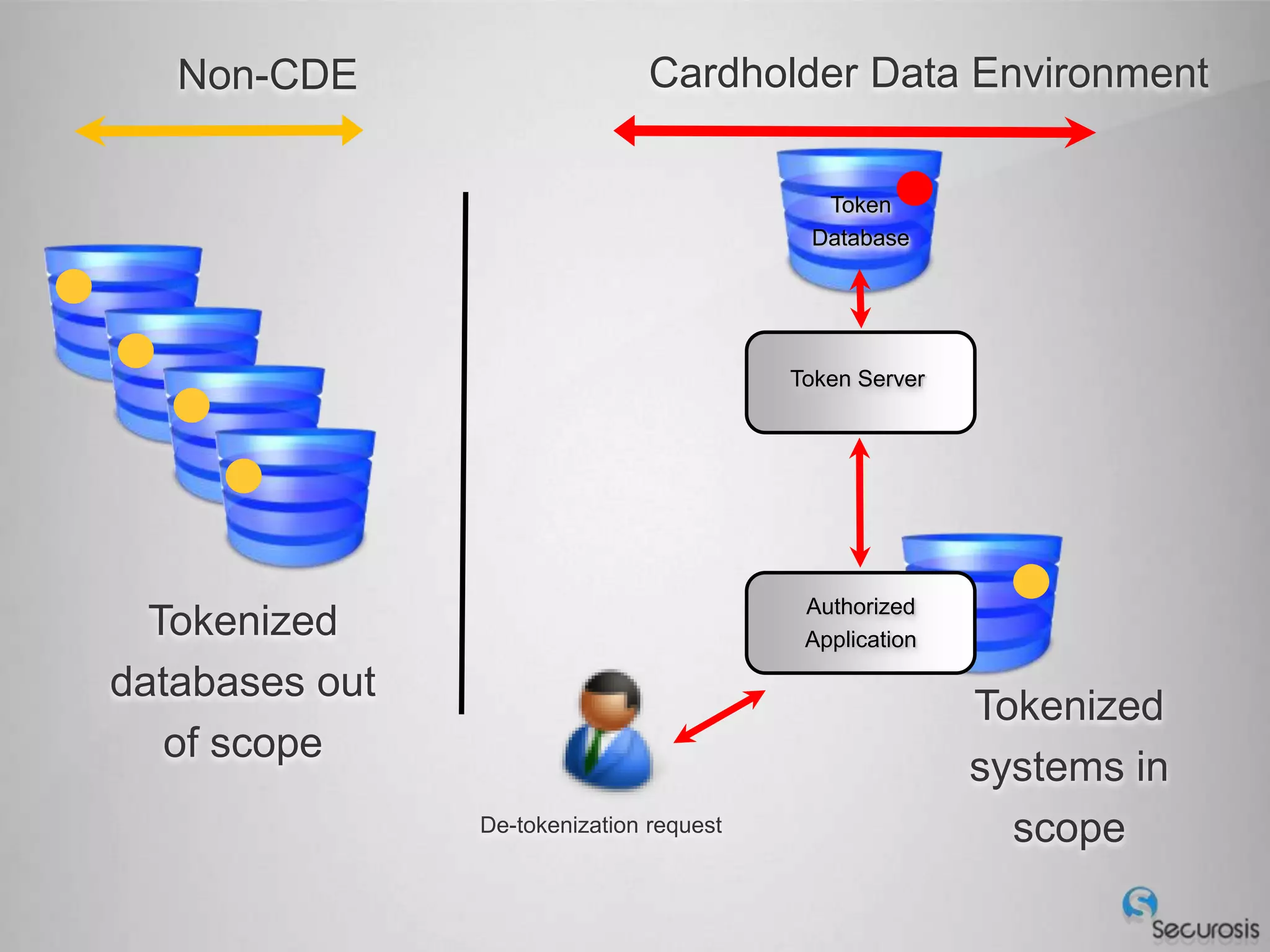
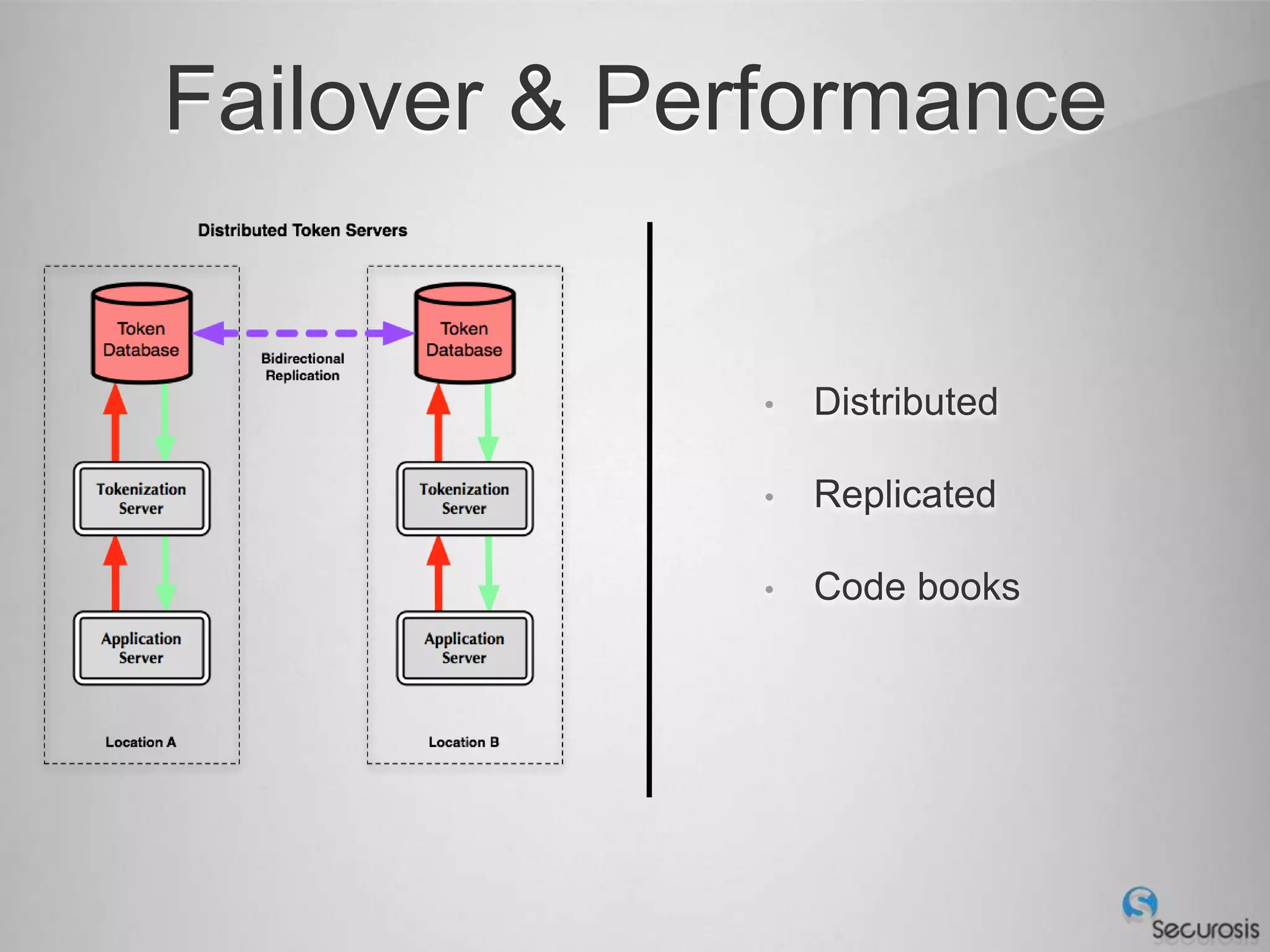
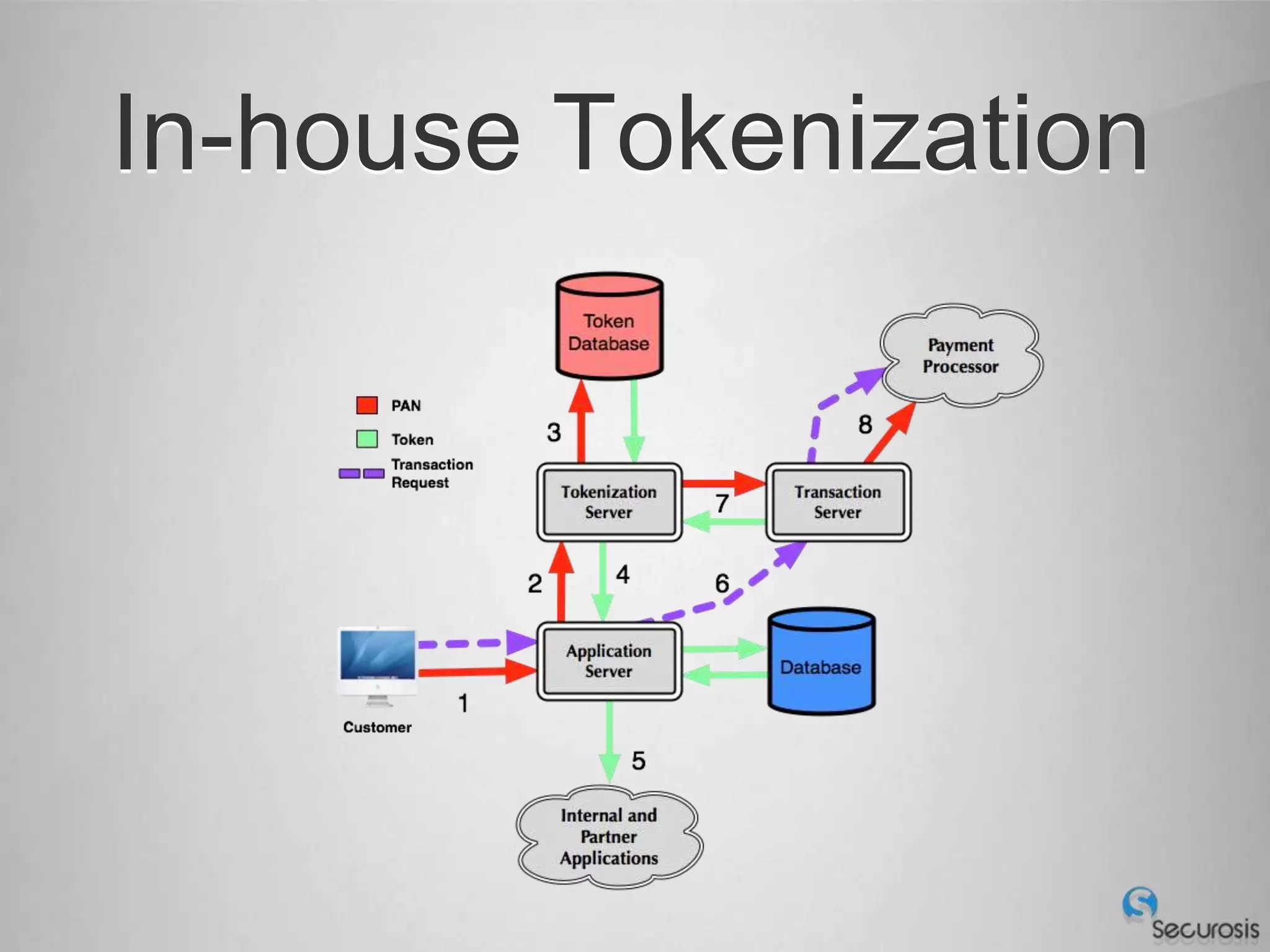
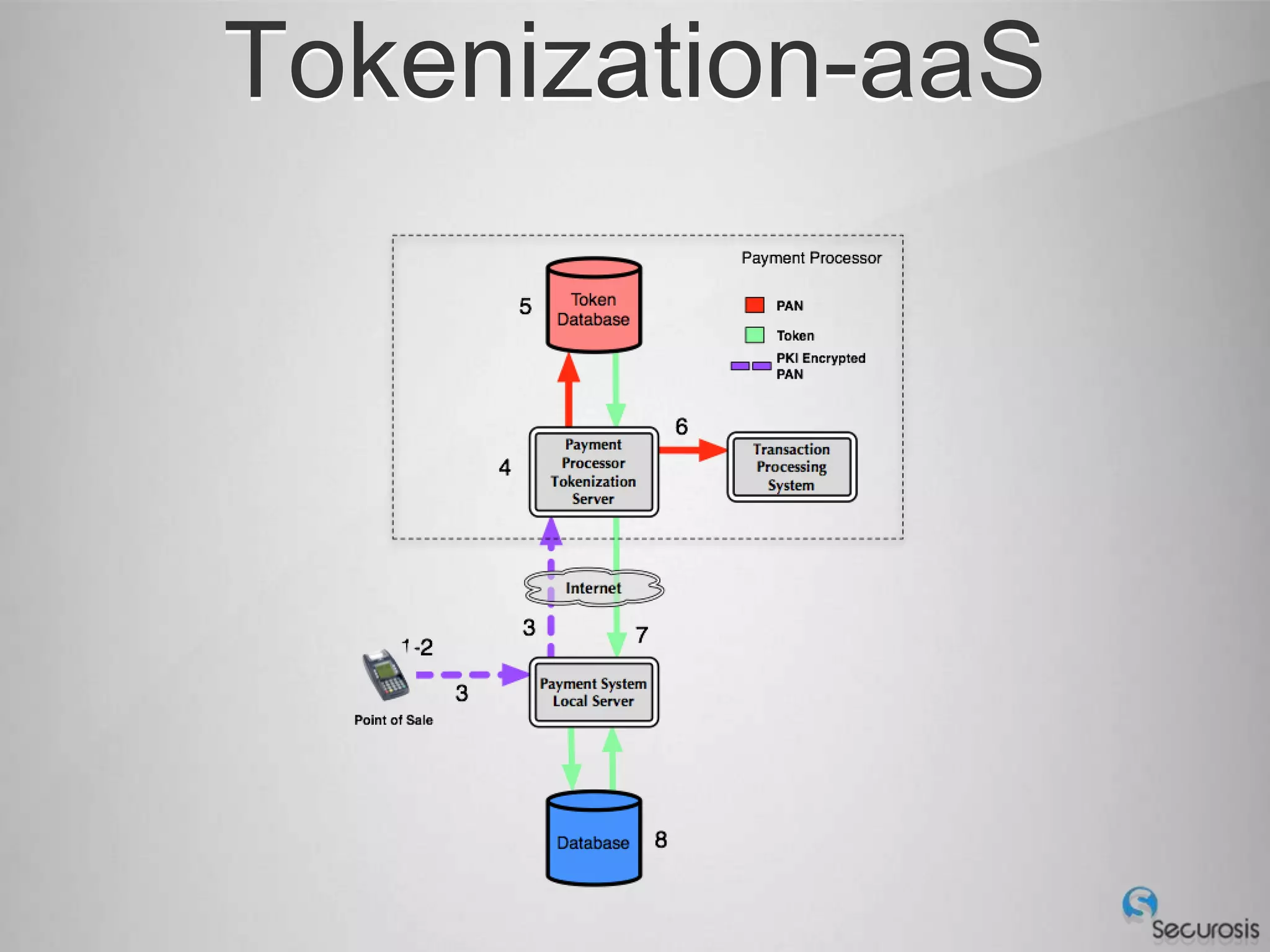
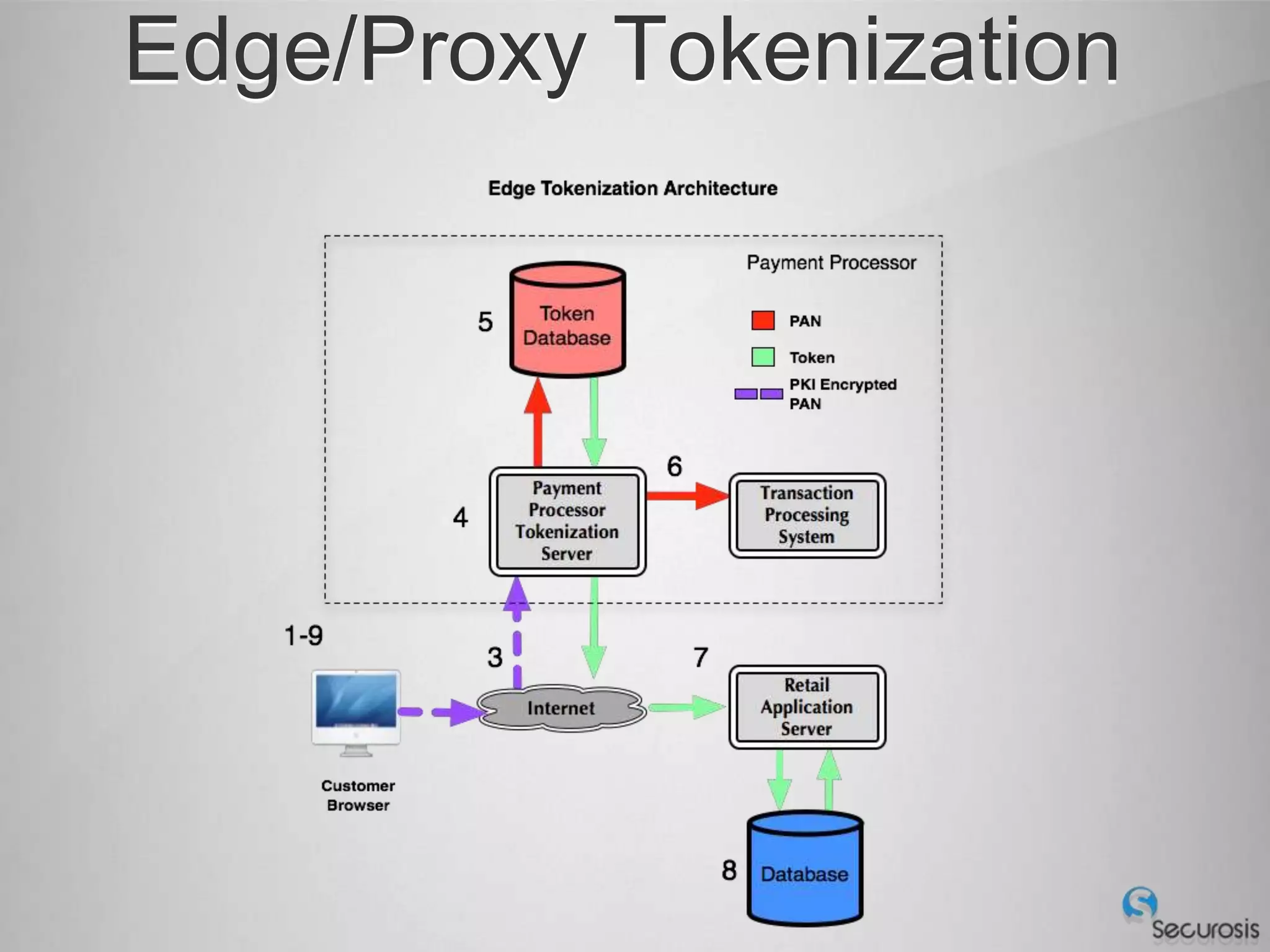
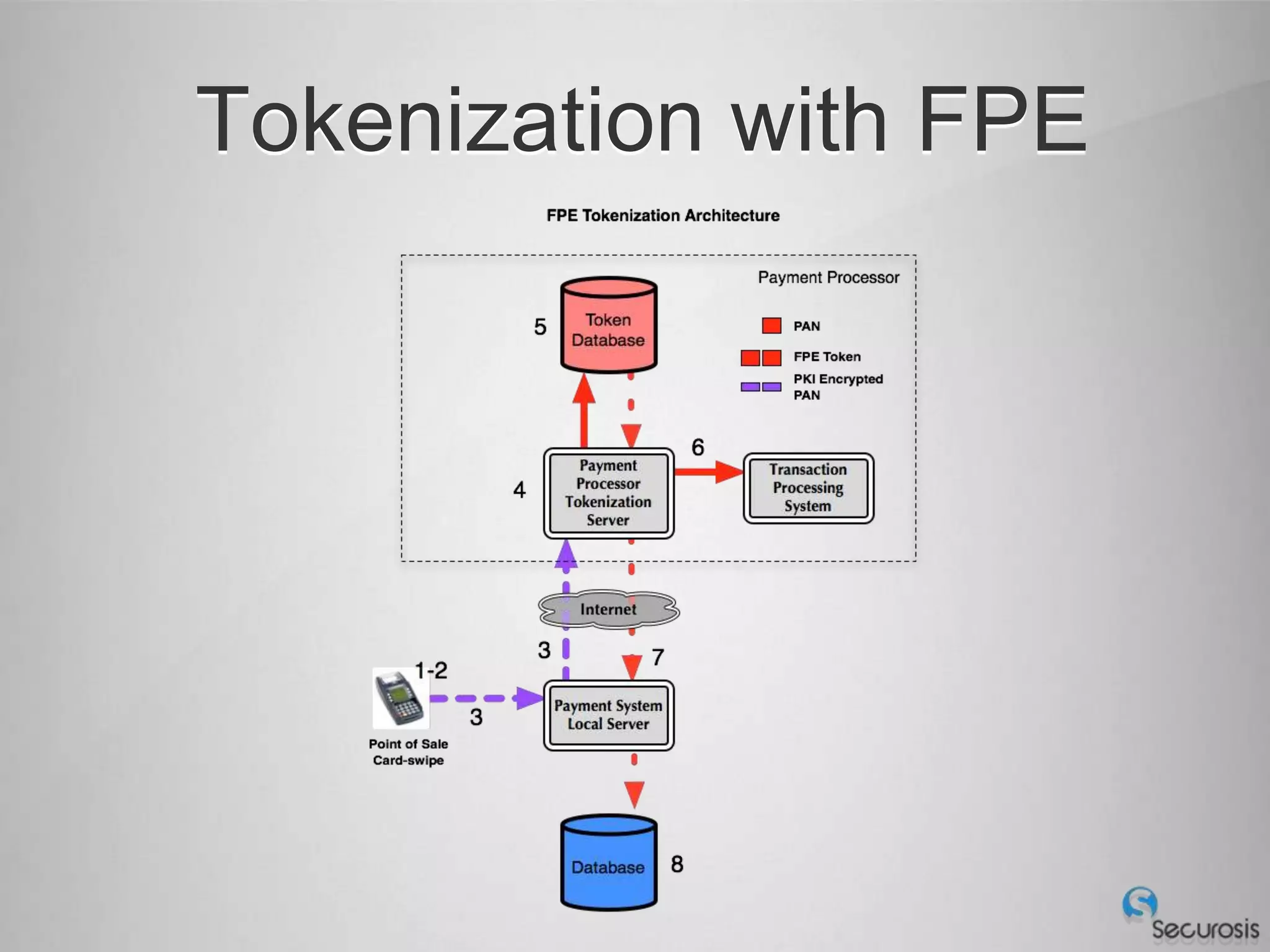
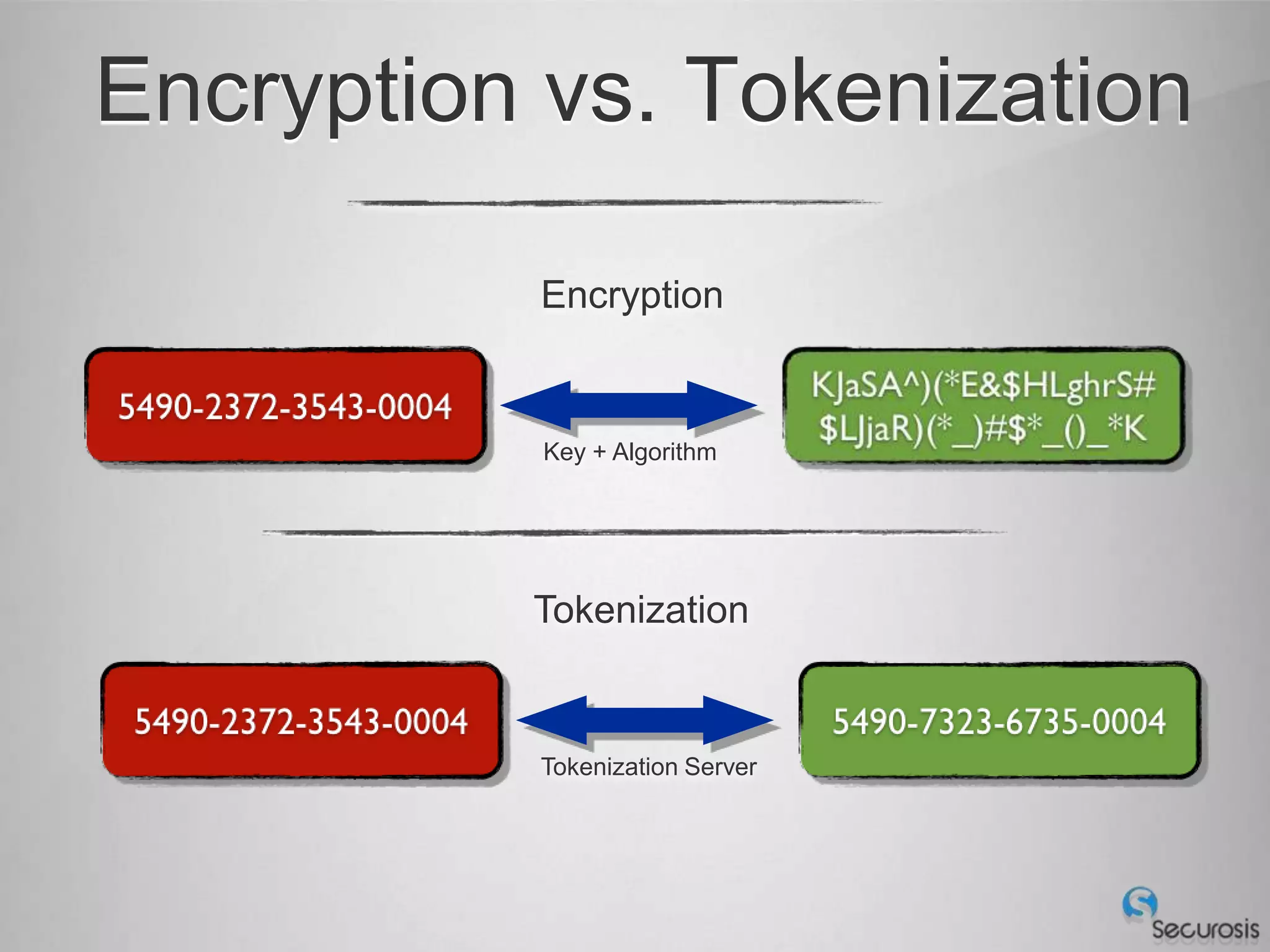
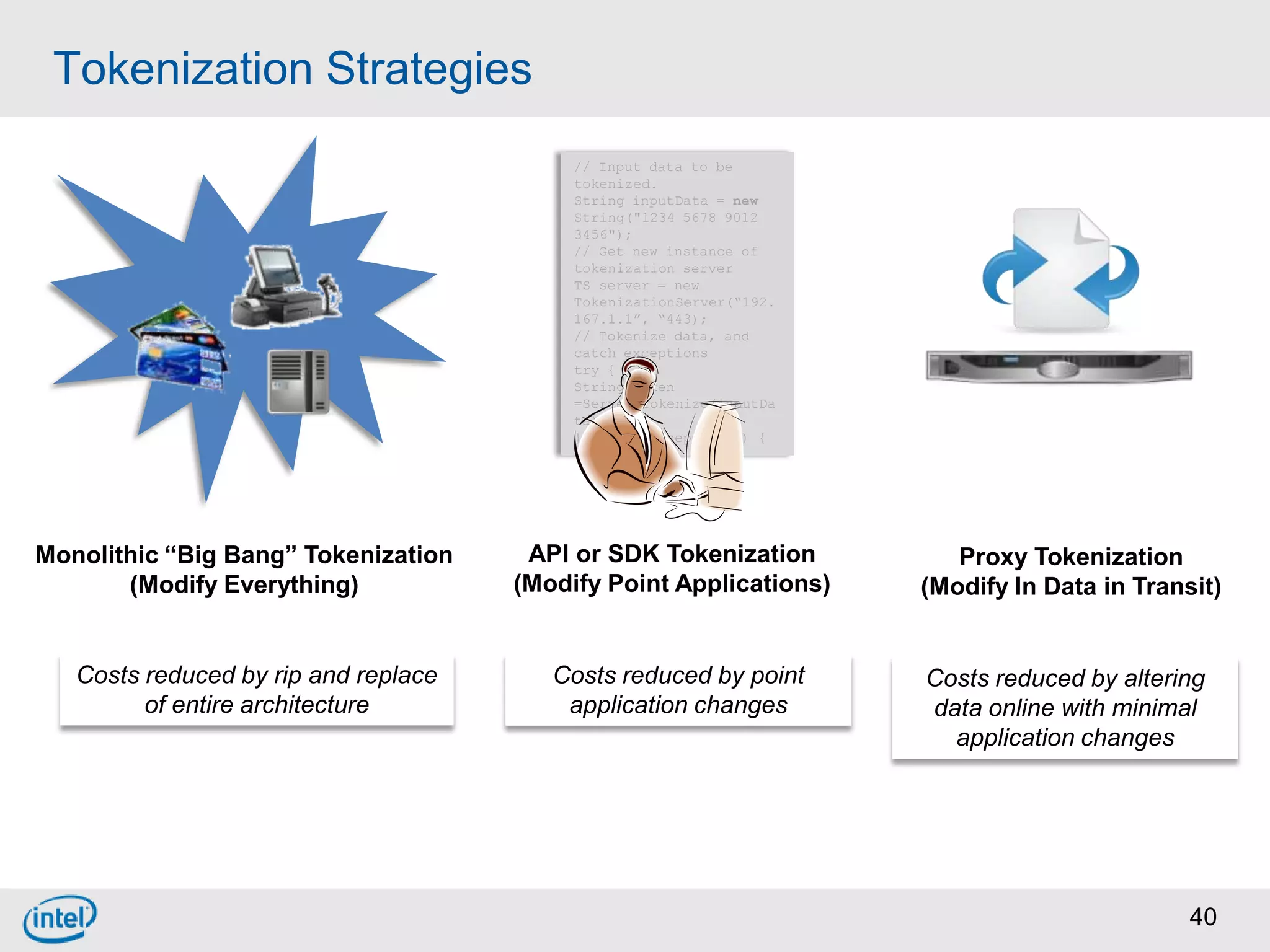
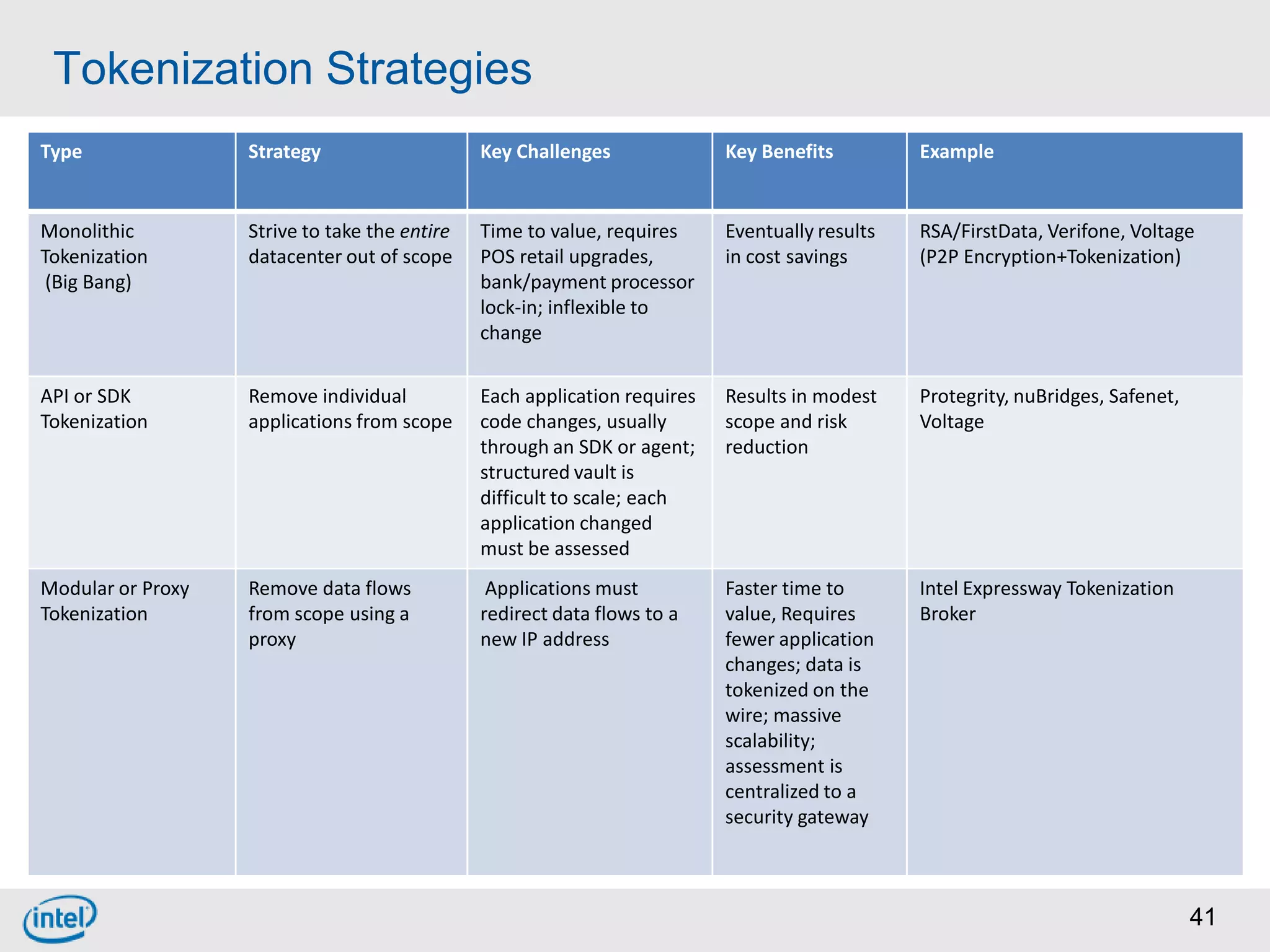
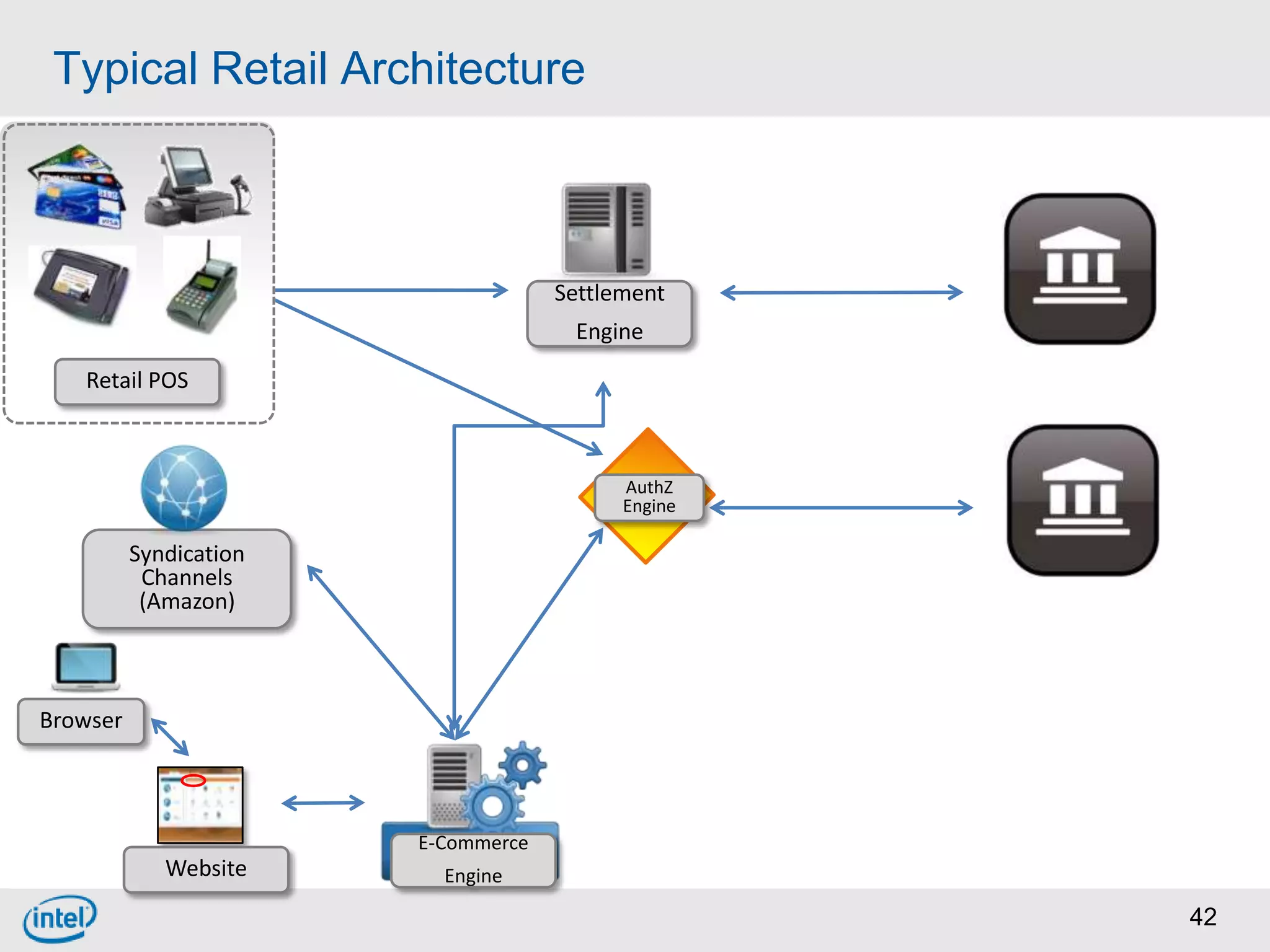
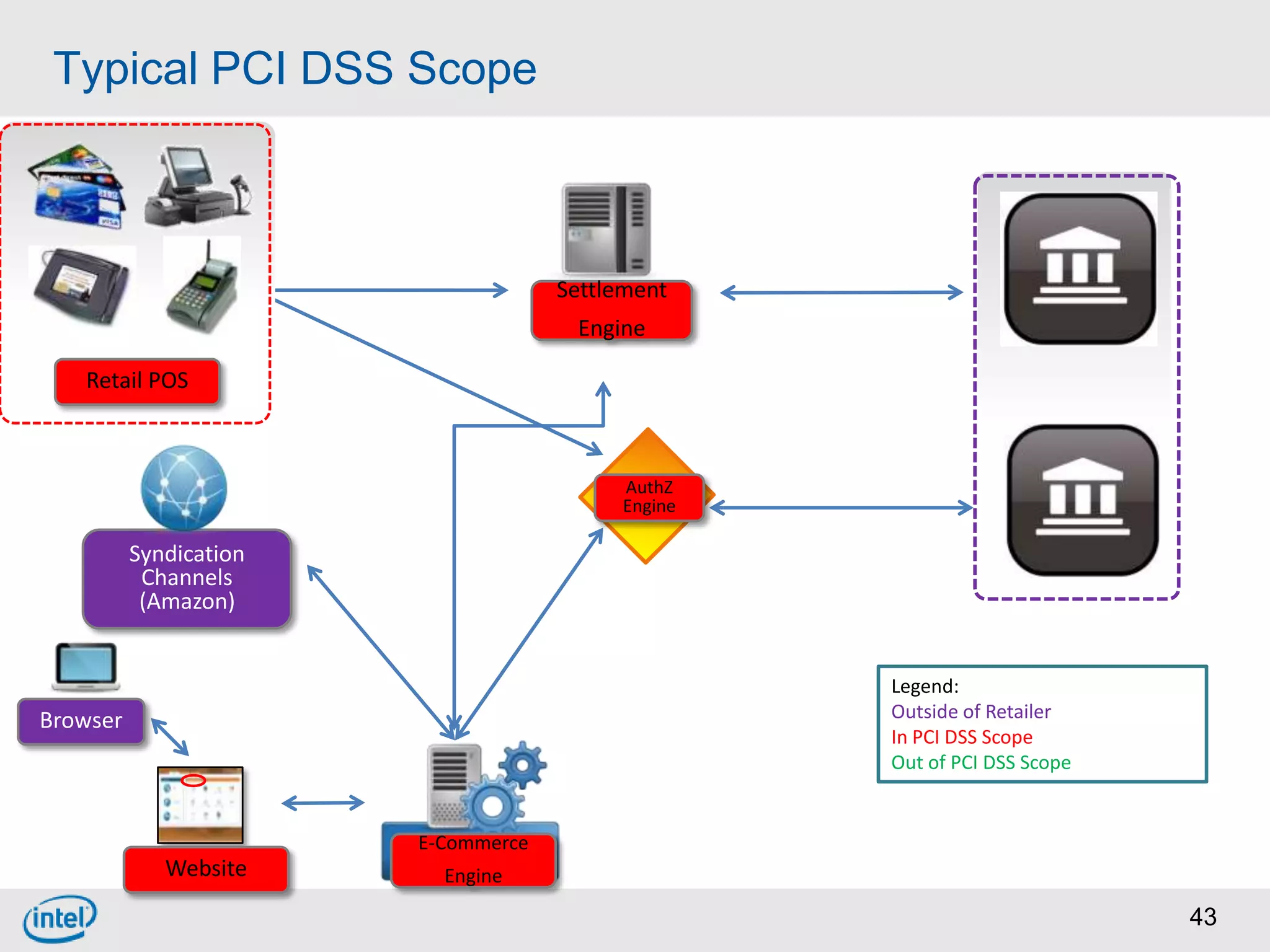
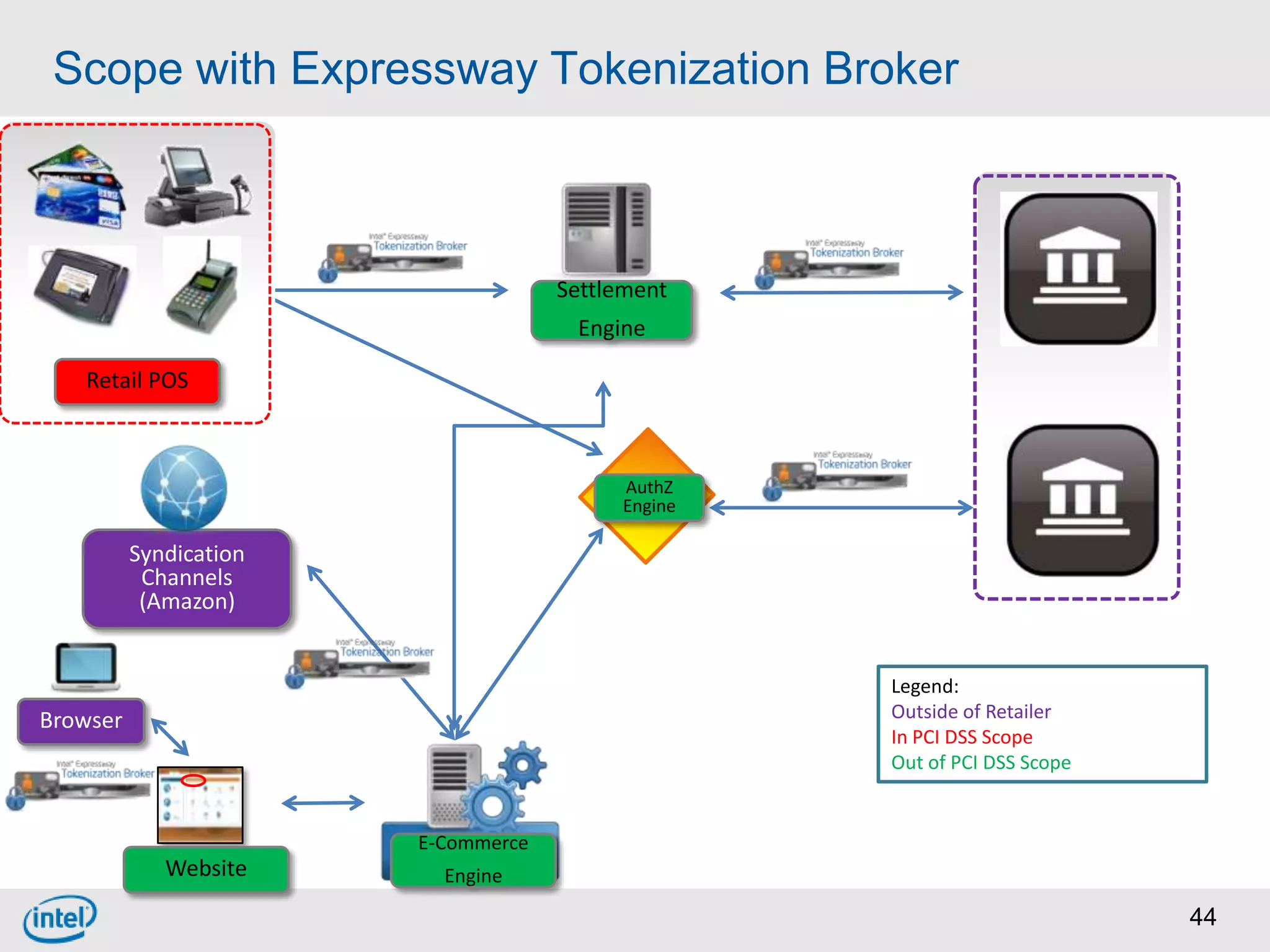
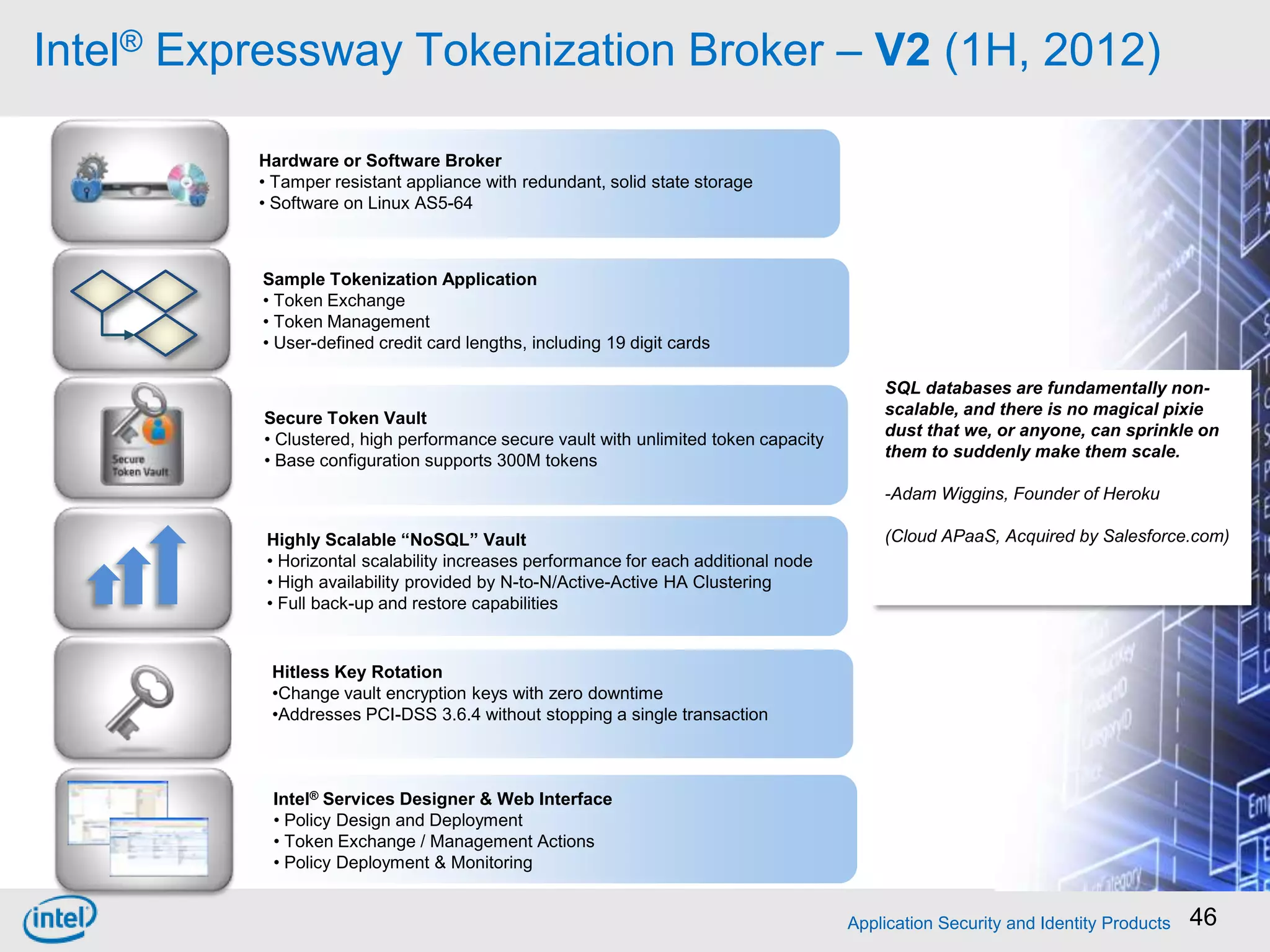
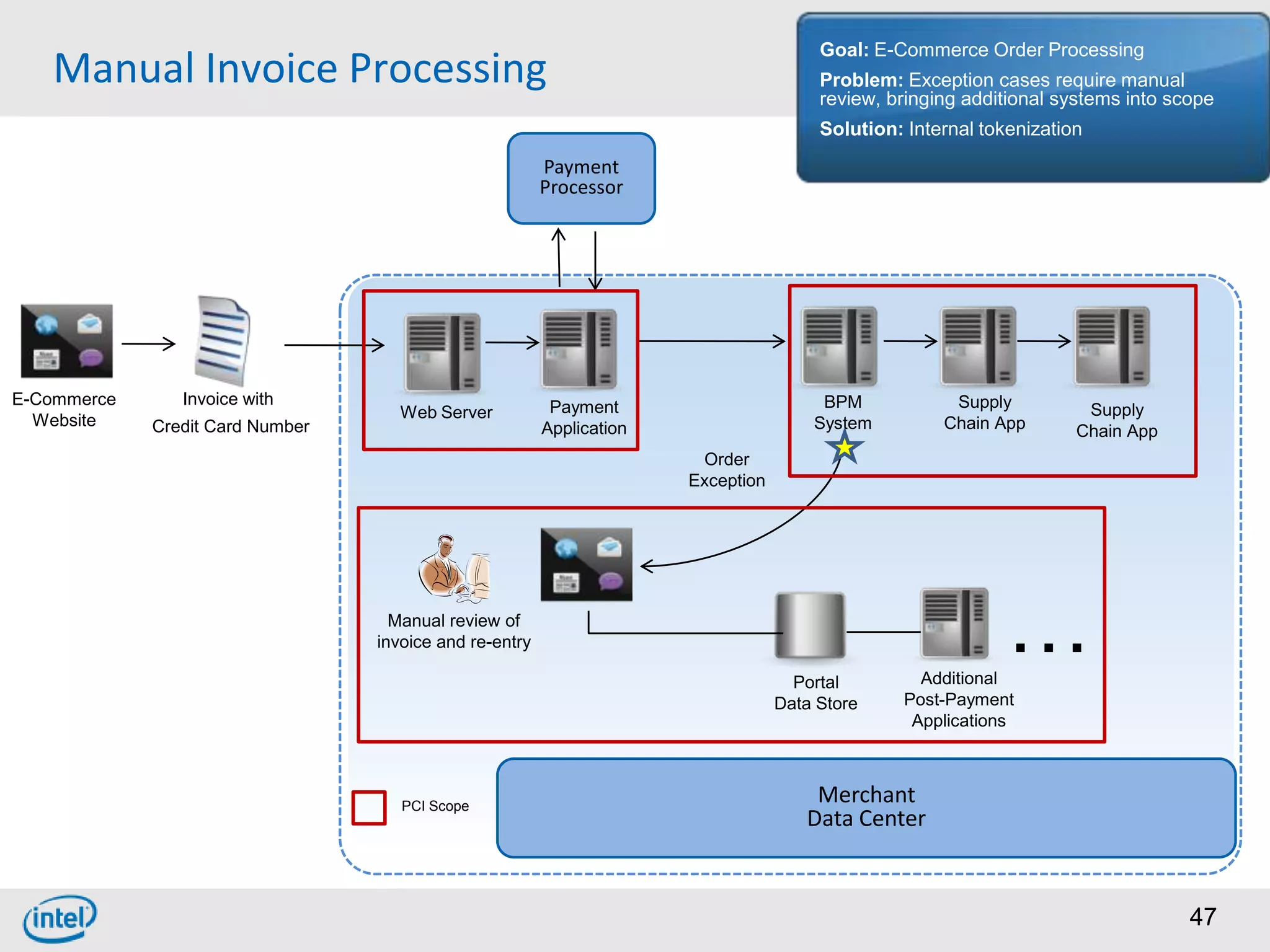
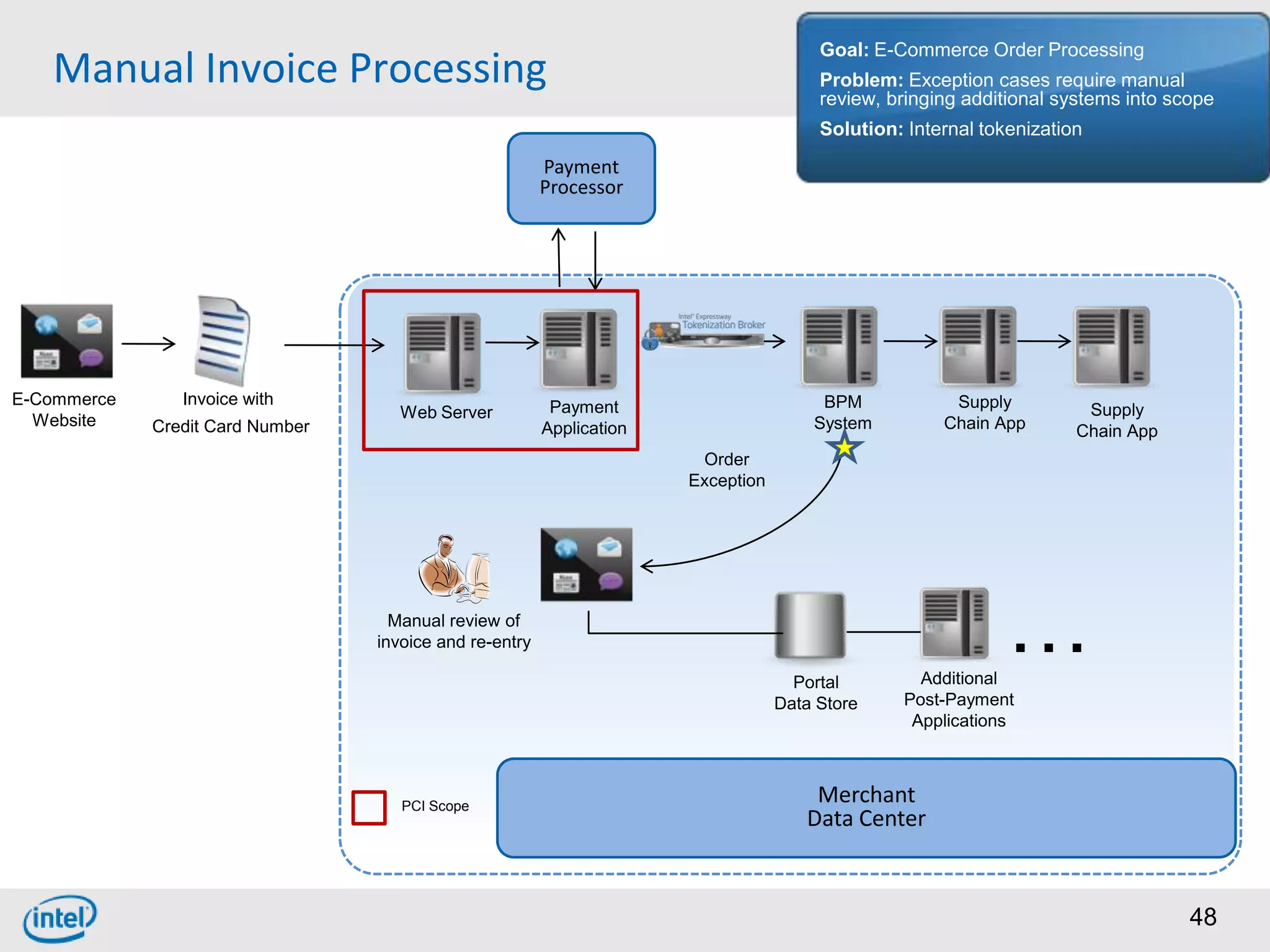
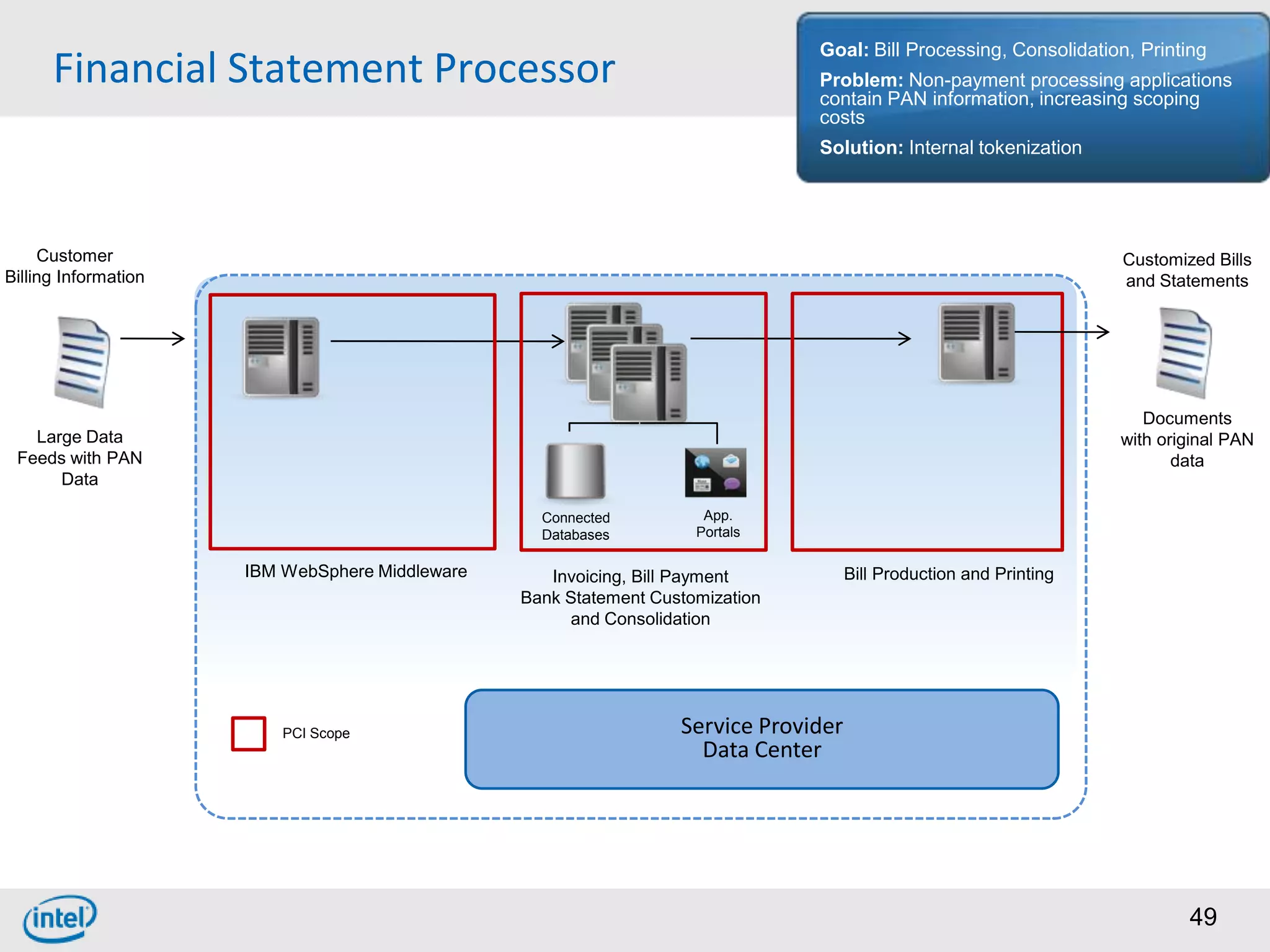
Choosing From 3 Core PCI-DSS Tokenization Models
A. Tokenize 100% of cardholder data by modifying all applications to use tokens instead of real data.
B. Modify some applications to use tokens instead of real data while keeping other applications unchanged.
C. Implement a proxy or gateway that intercepts cardholder data in transit and tokenizes it before sending to applications without modifying the applications.