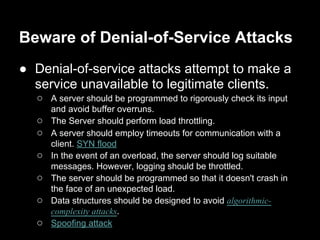
This document discusses guidelines for securely writing privileged programs. It recommends operating with least privilege by dropping privileges when they are not needed and reacquiring them only as required. It also recommends confining the process using capabilities or chroot jails, being careful of signals and race conditions, avoiding buffer overflows, and checking return values of system calls. The overall aim is to minimize the chances of a privileged program being subverted and to minimize potential damage if subversion occurs.




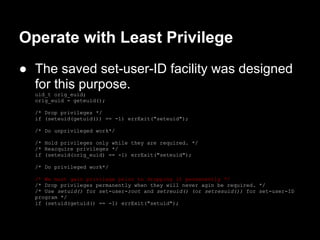
![Operate with Least Privilege (cont.)
● [Tsafrir et al., 2008] recommends that
applications should use system specific
nonstandard system calls for changing
process credentials.
● Not only check that a credential-changing
system call has succeeded, but also to verify
that the change occurred as expected.
● We should drop/raise the privileged effective
user ID last/first when dropping/raising
privileged IDs.](https://image.slidesharecdn.com/tlpi-chapter38writingsecureprivilegedprograms-130613194511-phpapp02/85/Tlpi-chapter-38-writing-secure-privileged-programs-6-320.jpg)