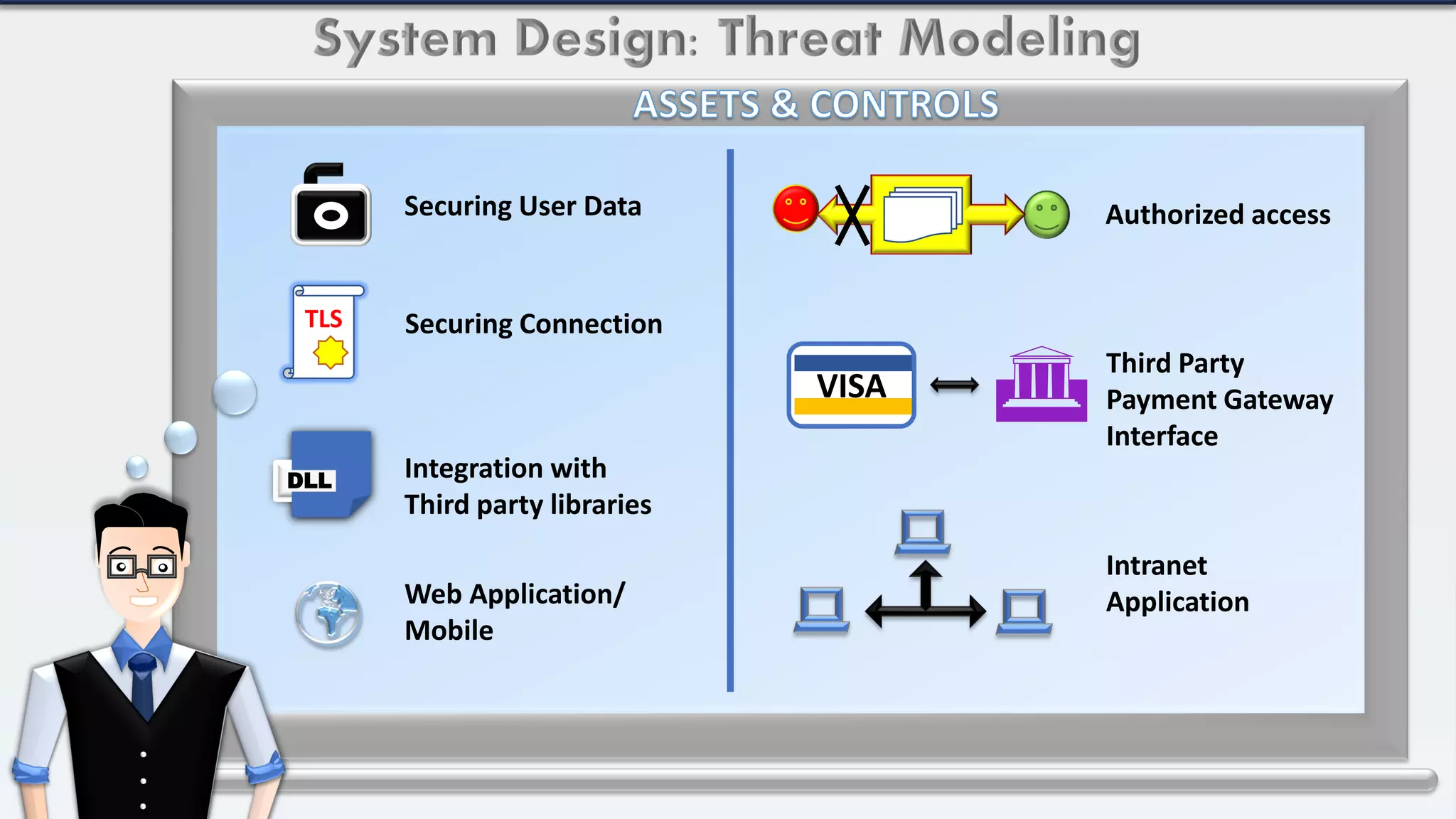
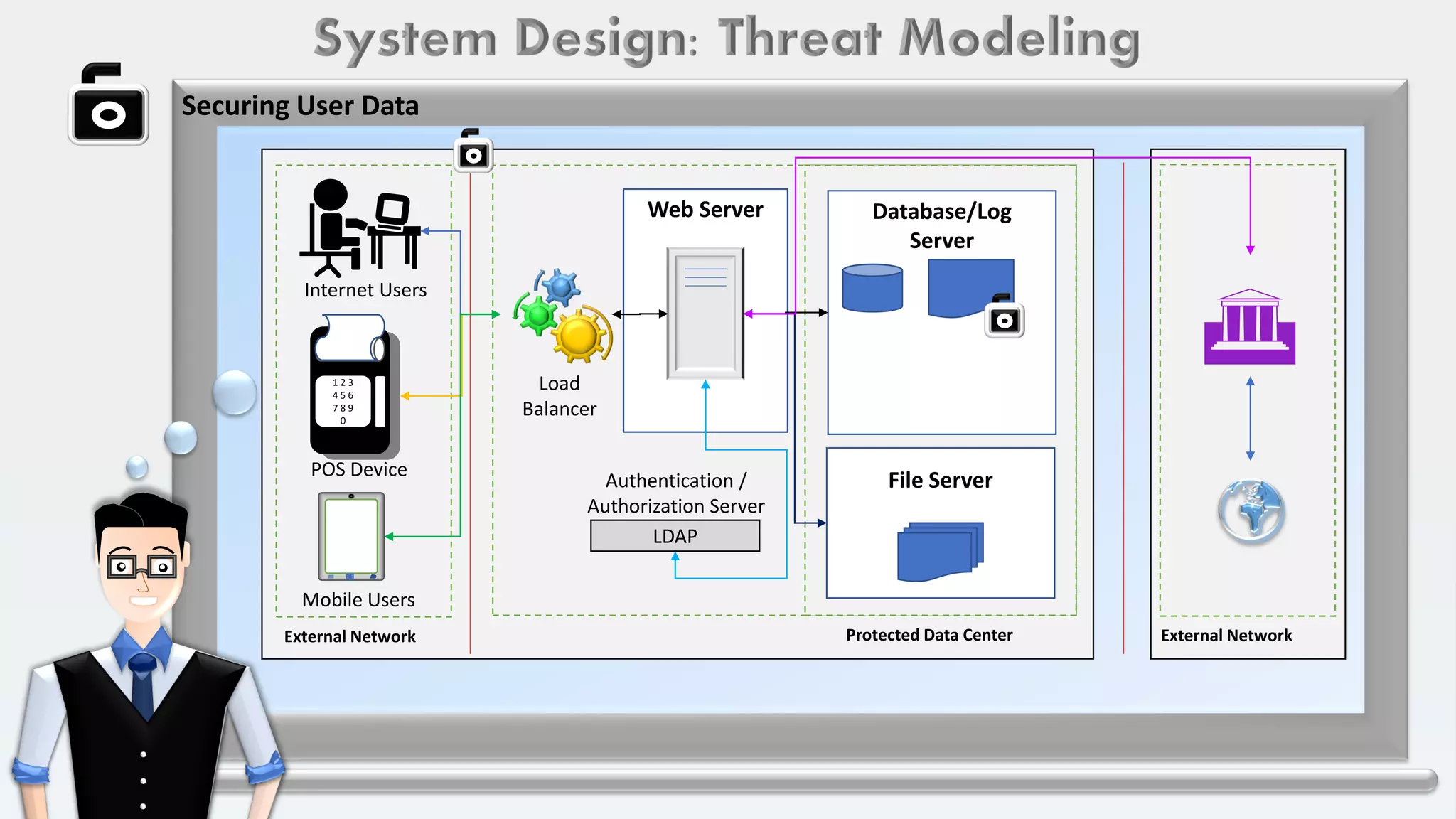
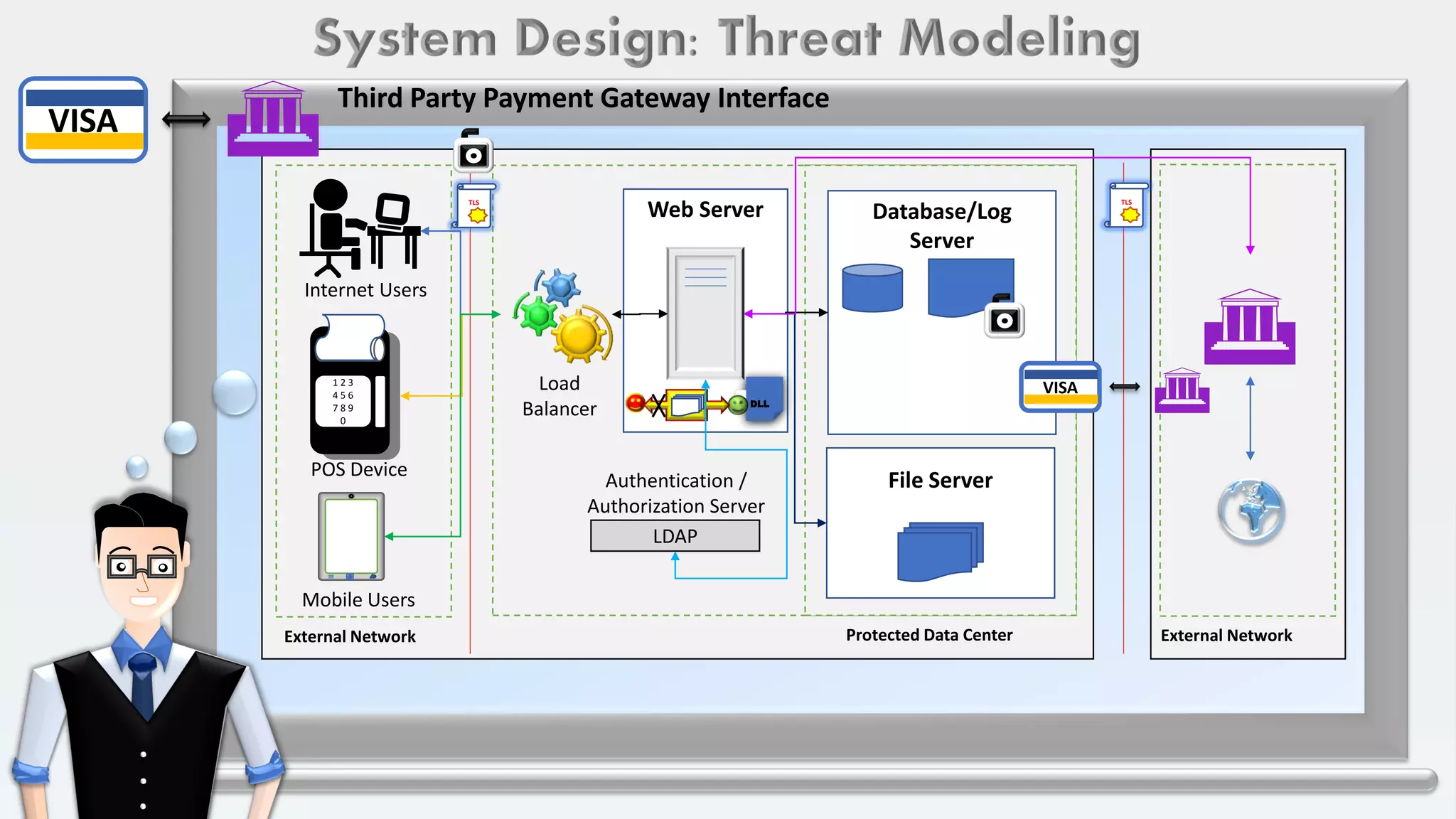
The document outlines a system design for threat modeling focused on securing user data in internet and intranet applications involving point-of-sale and mobile device users. It emphasizes the importance of TLS connections, authentication, authorization processes, and risk ranking of potential threats while recommending architectural updates for improved security. The primary goal is to identify missing security controls and enhance overall system protection.