Embed presentation
Download to read offline




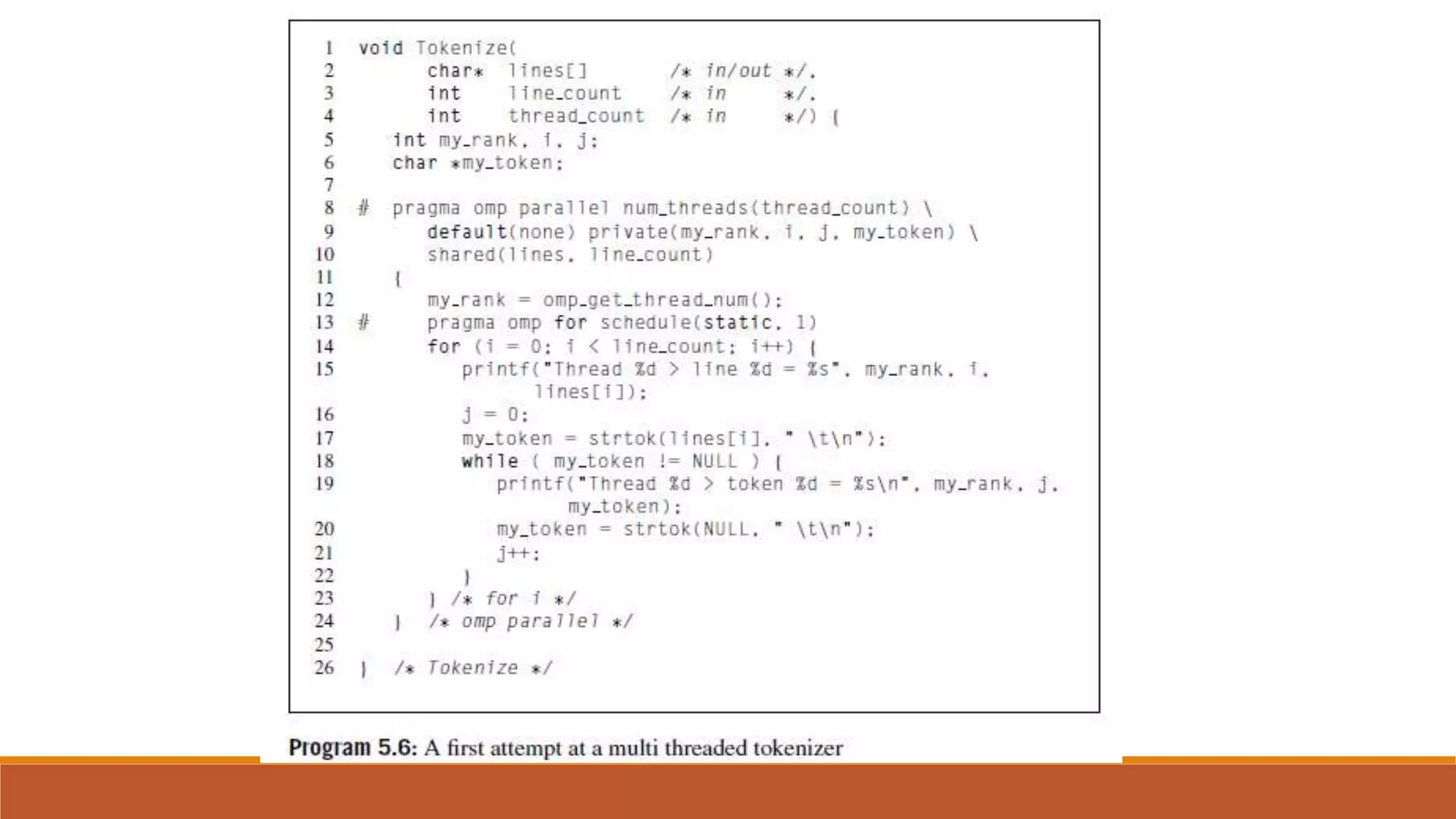


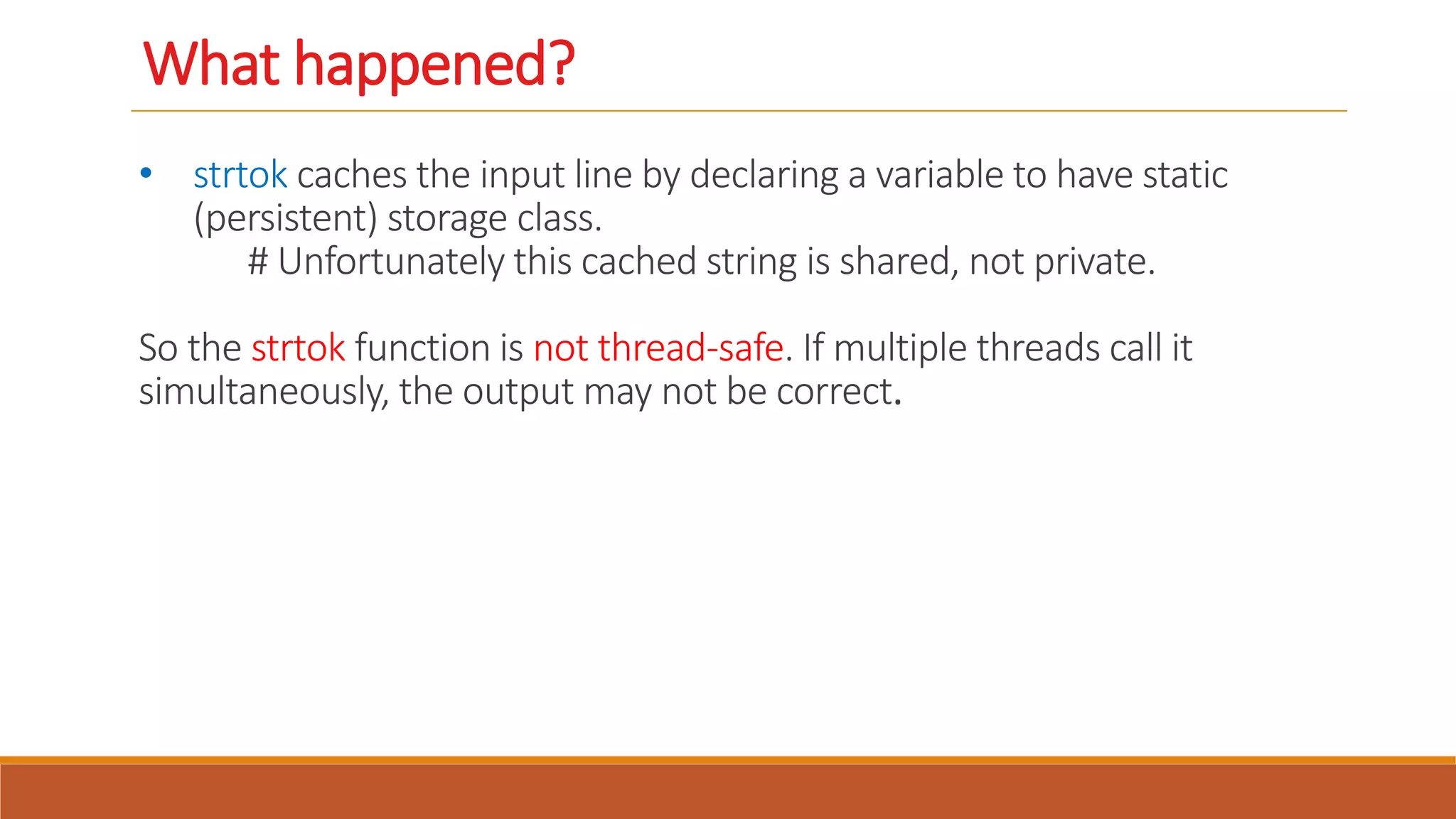
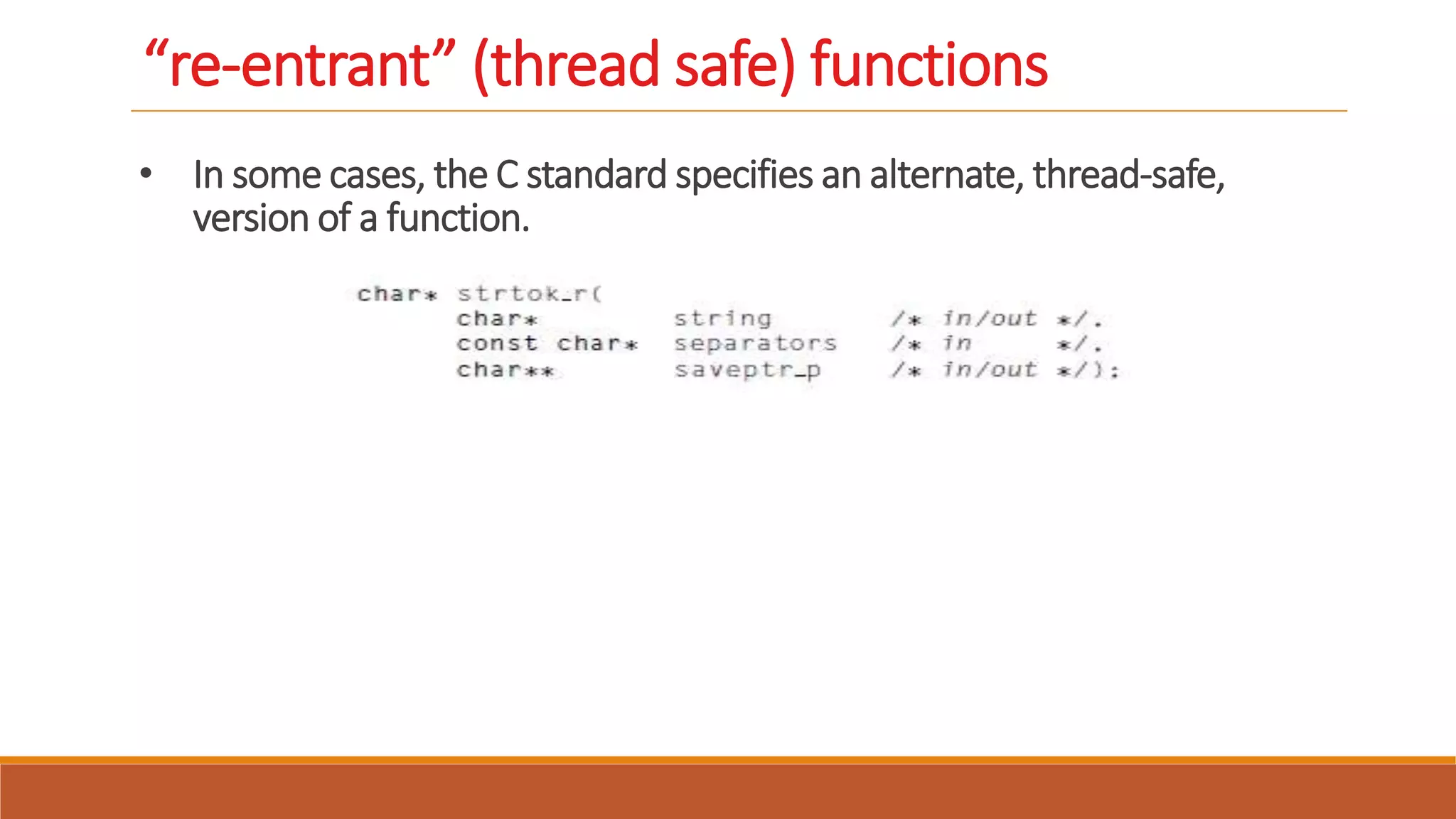

Thread-safety refers to whether a block of code can be executed simultaneously by multiple threads without errors. While functions written by a programmer can be identified as thread-safe or not, system library functions may not be thread-safe. The strtok() string function from the C standard library, for example, is not thread-safe because it caches input in a static variable that is shared across threads, leading to unpredictable results when called simultaneously from multiple threads. Making functions re-entrant by avoiding shared static variables can make them thread-safe.









