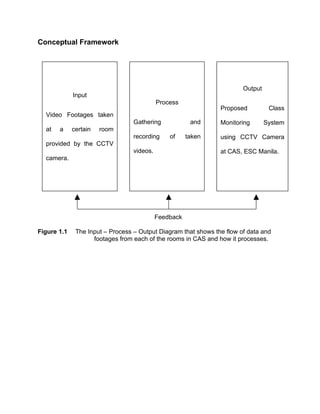
The proposed study aims to develop a class monitoring system using surveillance cameras for the College of Arts and Sciences at the Eulogio 'Amang' Rodriguez Institute of Science and Technology. The system would monitor classrooms to (1) improve security and awareness on campus, (2) track faculty attendance, and (3) observe classrooms. The researchers assume the system is needed to ensure classrooms are kept orderly and professors are attending classes as scheduled. If implemented, the monitoring system could provide useful information to analyze situations, identify problems, and ensure activities are carried out properly. The scope is limited to CAS classrooms, students, faculty and staff.