Embed presentation
Download to read offline





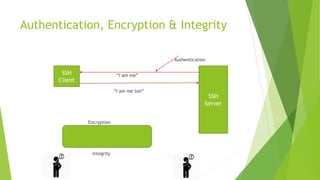


The SSH protocol specifies how to securely communicate over a network by providing authentication of users, encryption of data, and integrity checks to ensure data is not altered. It authenticates users through digital identity proofs, encrypts data to scramble it so it is unintelligible to anyone but the intended recipients, and guarantees data traveling over the network arrives unaltered through integrity checks.






