This document provides an overview of HIPAA/HITECH compliance training. It begins with an introduction to the topics that will be covered, including the HIPAA foundation, major players, transactions and identifiers, privacy rule, security rule, and breach notification. It then discusses the historical facts around HIPAA, including what it stands for, when it was passed, who it applies to such as covered entities and business associates. Key aspects of HIPAA are summarized, like the administrative simplification title, electronic data interchange standards, privacy and security rules, individual rights, and breach response requirements.



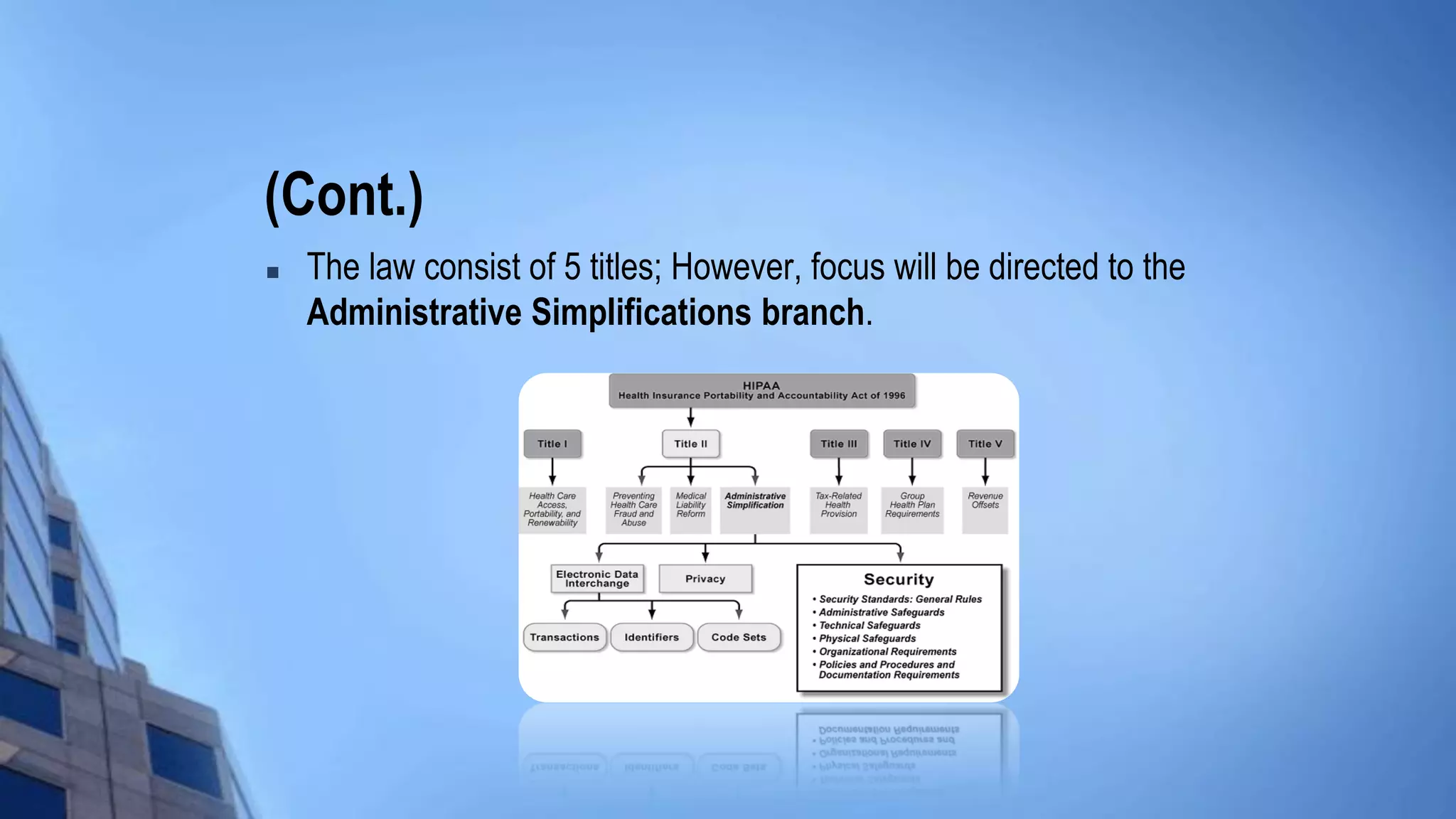
![Historical facts:
So what exactly is HIPAA?
HIPAA stands for the Health Insurance Portability and Accountability Act.
The federal act was passed on Aug. 21, 1996.
Often times – referred to as Public Law 104.191 [H.R. 3103] or the
Kennedy – Kassebaum Bill.
The 1st law to address confidentiality or privacy, security and
standardization of data (especially electronic data) in the health care
industry.](https://image.slidesharecdn.com/3da739b1-25f8-4dec-9a21-bfbc07fe5b97-160428115115/75/Welcome-to-HIPAA-Training-4-2048.jpg)