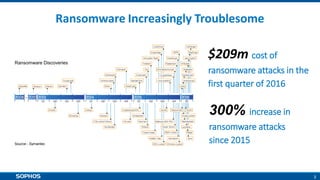
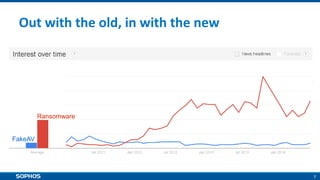
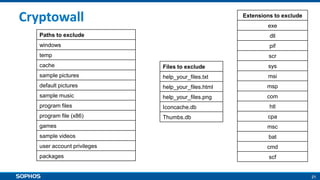
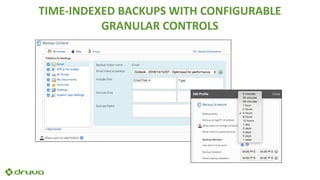
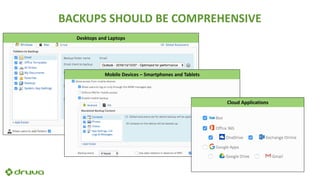
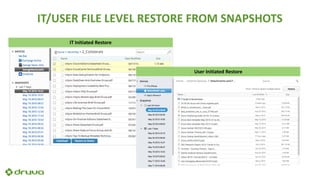
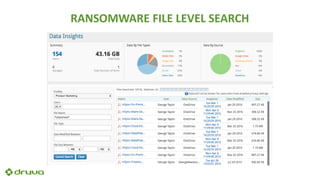
Ransomware attacks have surged by 300% since 2015, costing businesses and public agencies significantly, with a notable example being the Kansas Heart Hospital attack in May 2016. To mitigate risks, organizations should implement preventive measures such as regular backups, employee training, and robust security protocols. The document emphasizes the importance of continuous updates and effective data protection strategies.













![Taking a Proactive Approach to Combat Ransomware [Druva Webinar]](https://image.slidesharecdn.com/takingaproactiveapproachtocombatransomware-druvawebinar-160526170043/85/Taking-a-Proactive-Approach-to-Combat-Ransomware-Druva-Webinar-31-320.jpg)