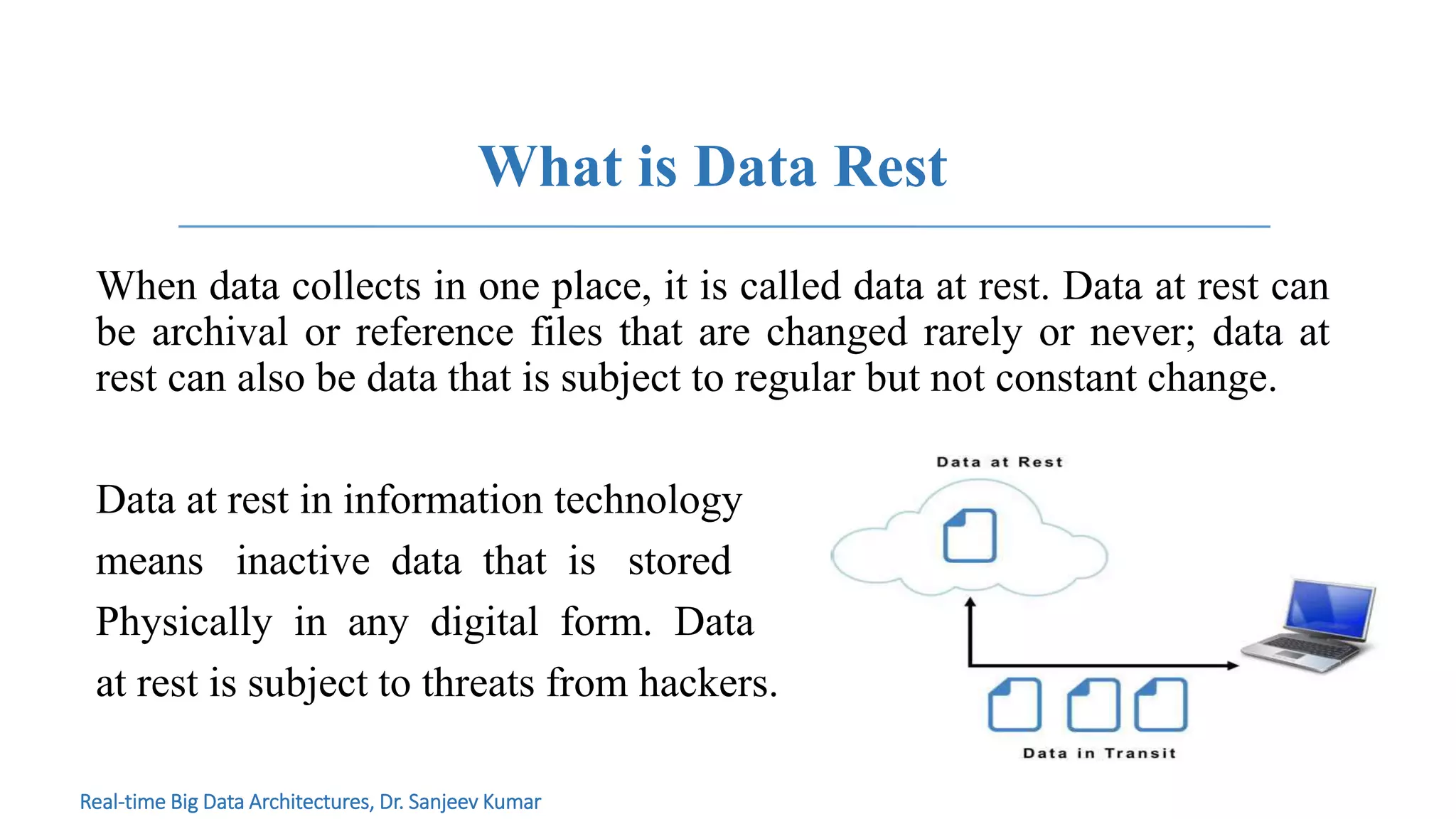
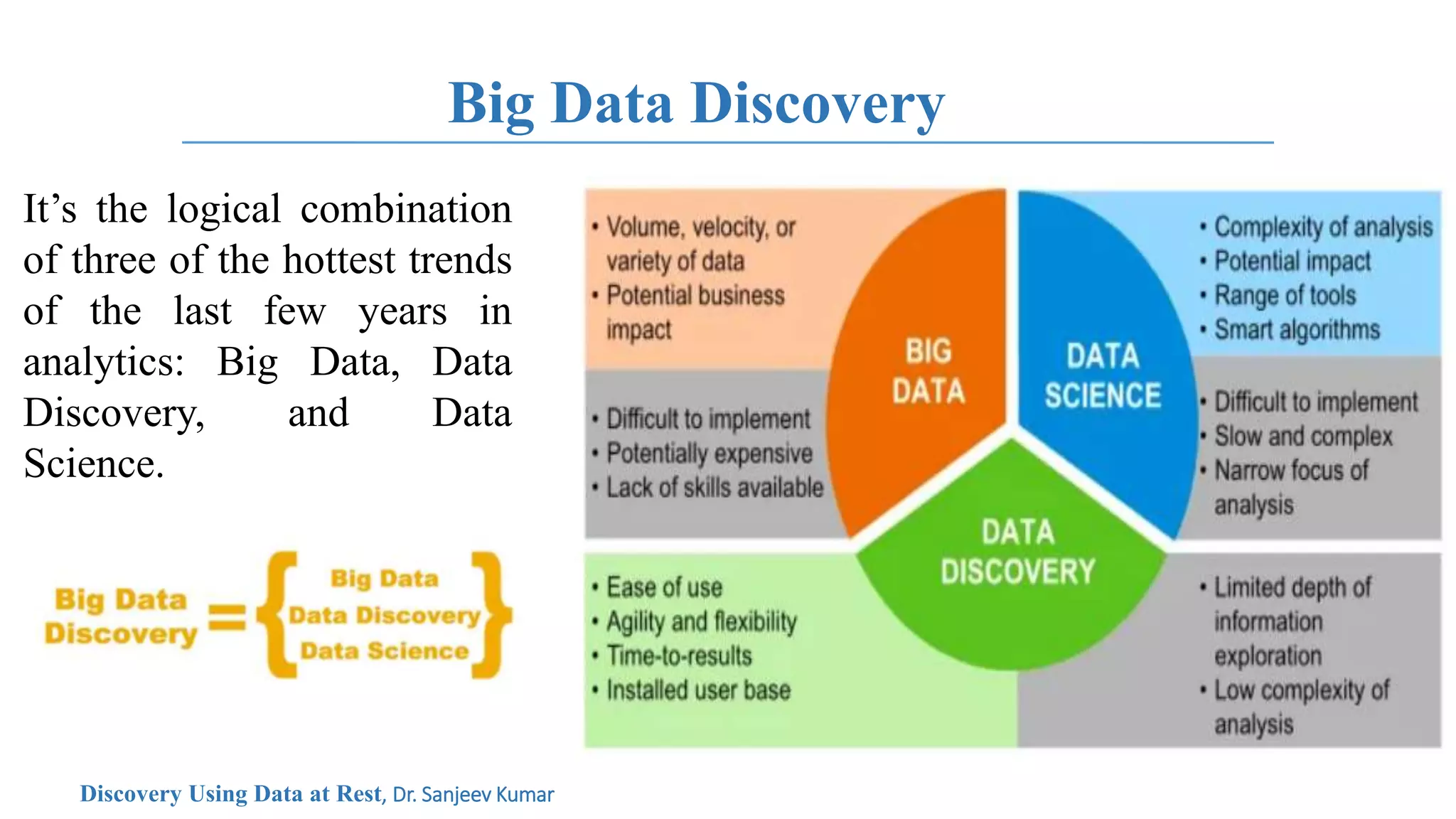
The document discusses the concept of data at rest, emphasizing its susceptibility to security threats and the importance of protecting inactive data stored across various platforms. It highlights the role of encryption and outlines best practices for safeguarding data, including proactive security measures and systematic classification of data. The conclusion advises careful evaluation of cloud service providers' security measures when storing data.