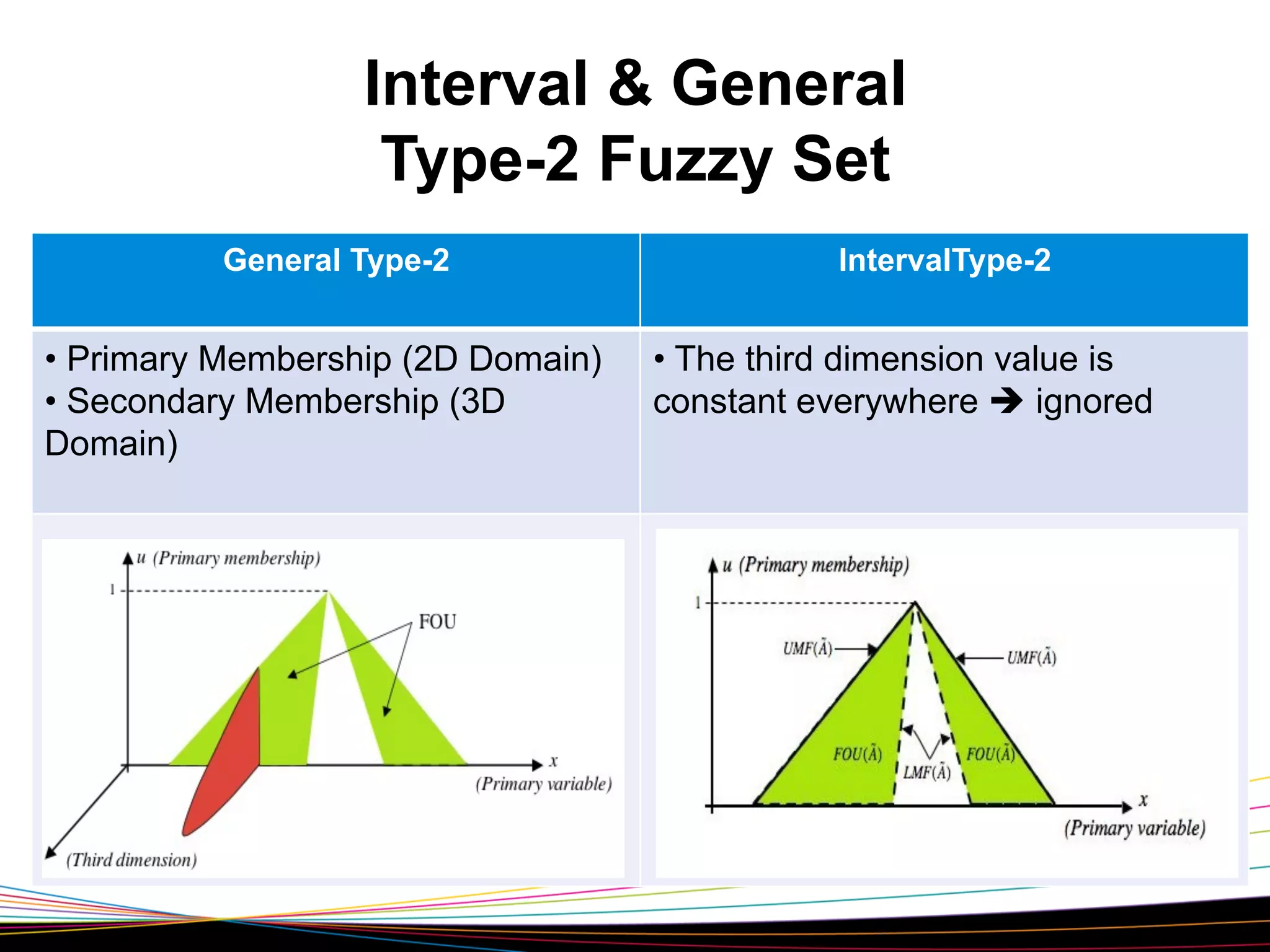
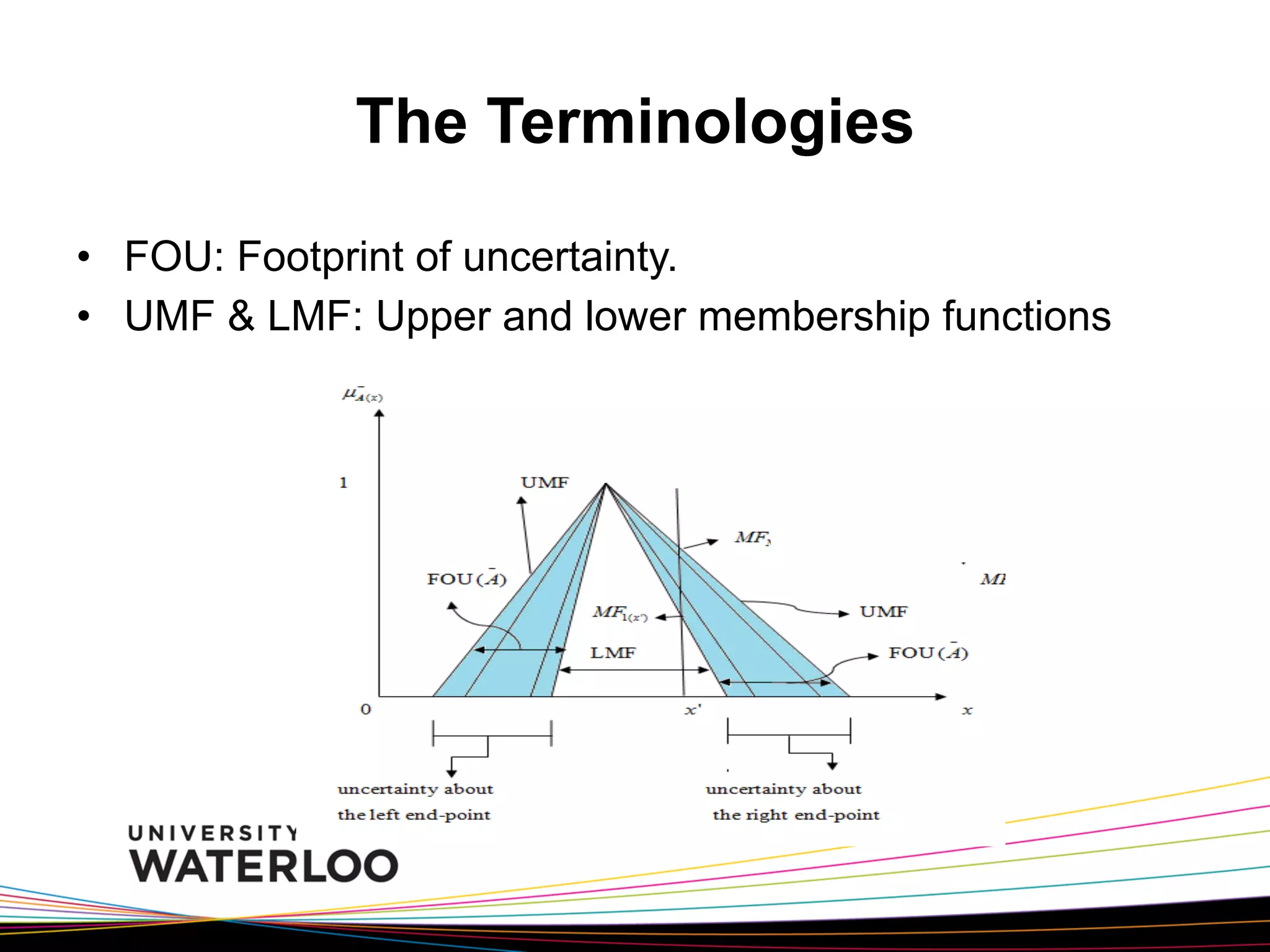
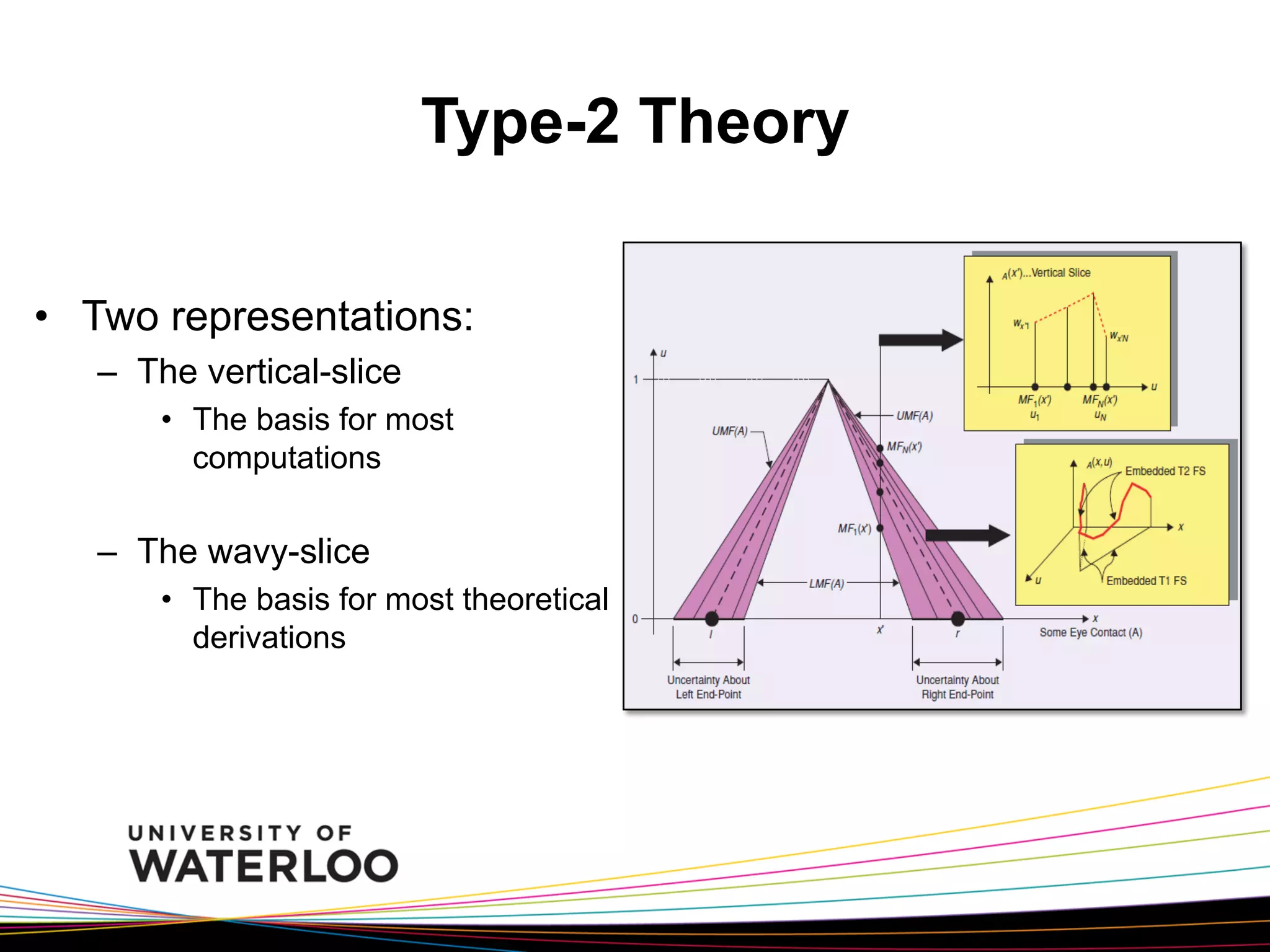
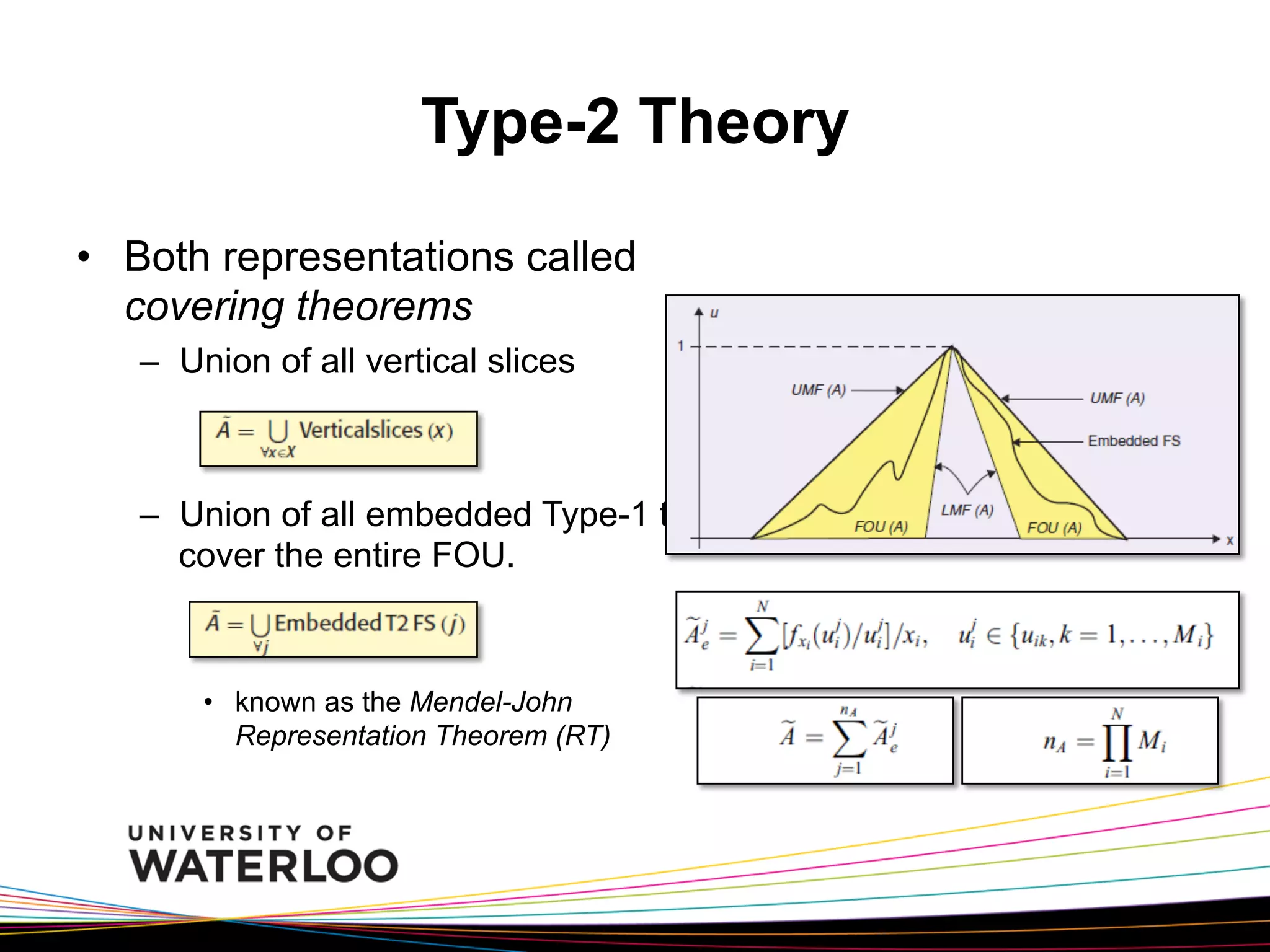
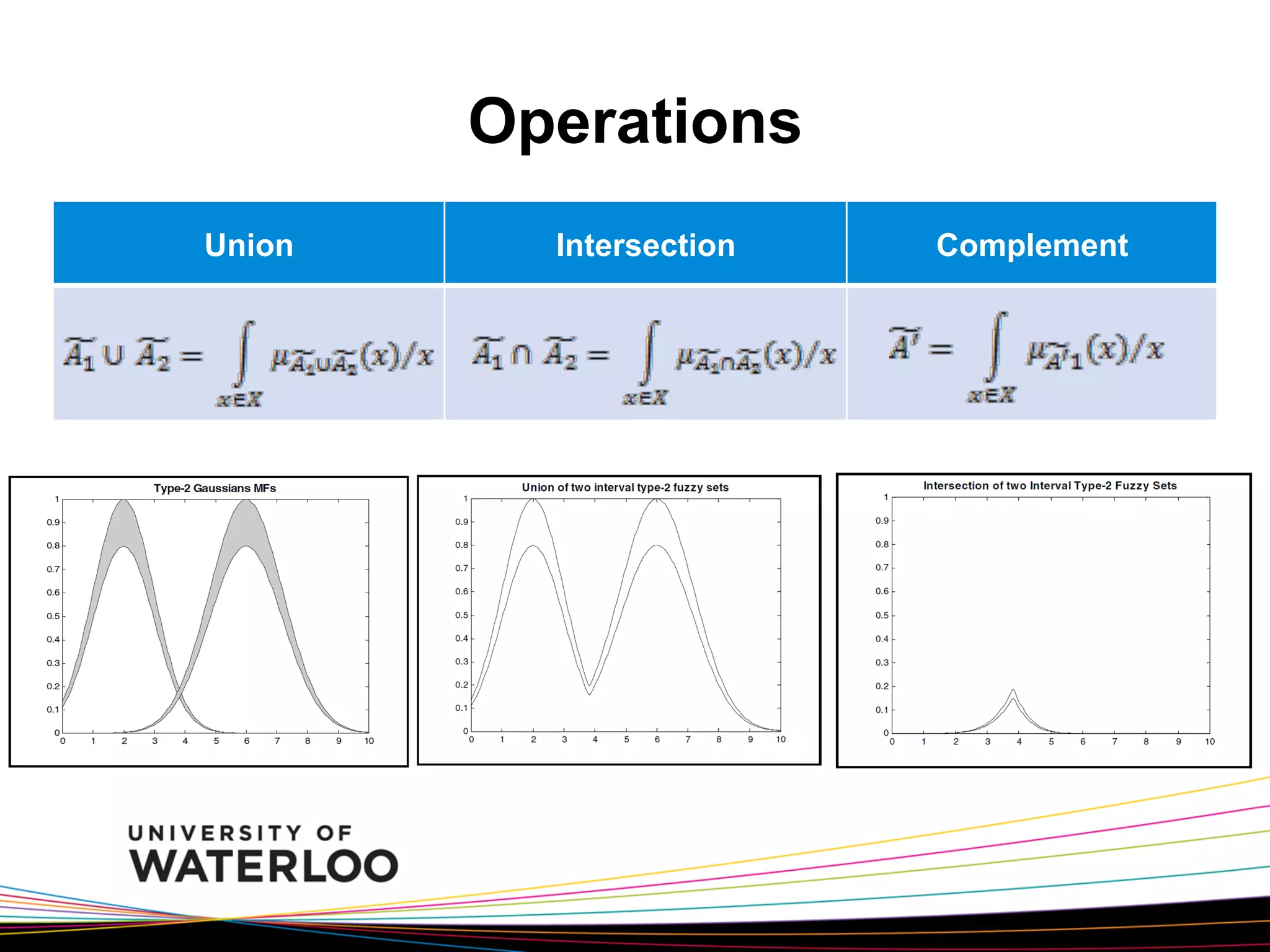
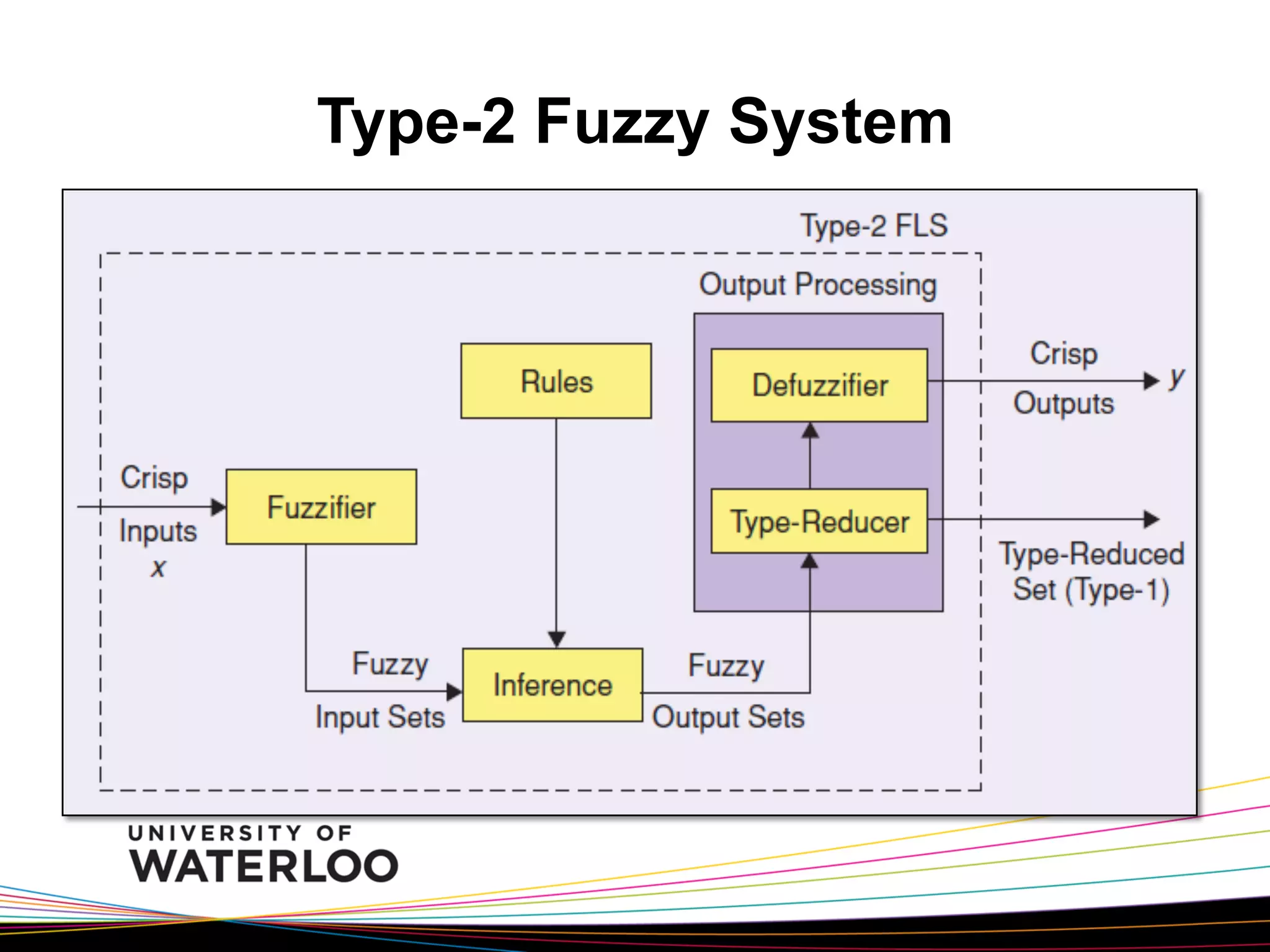
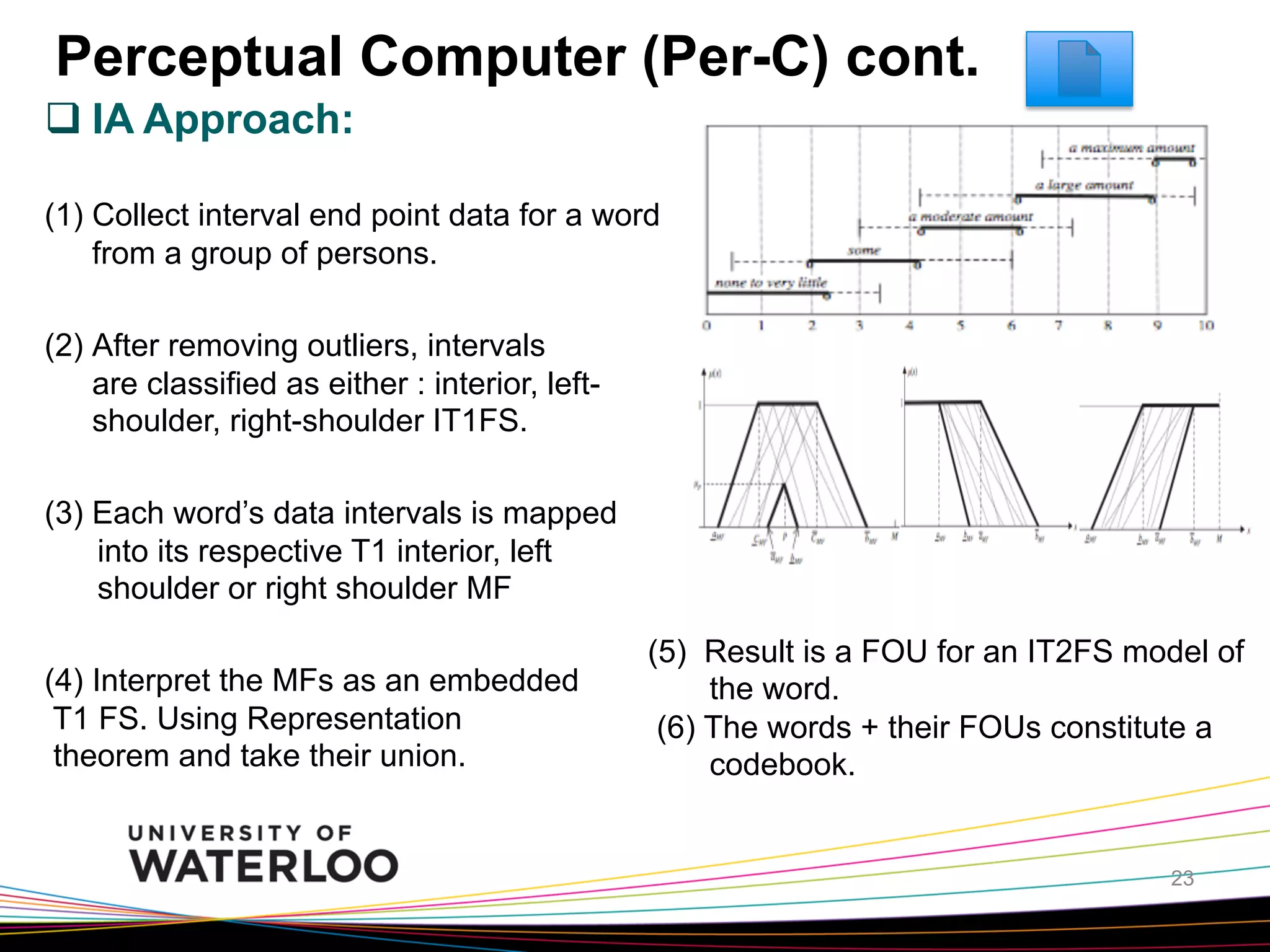
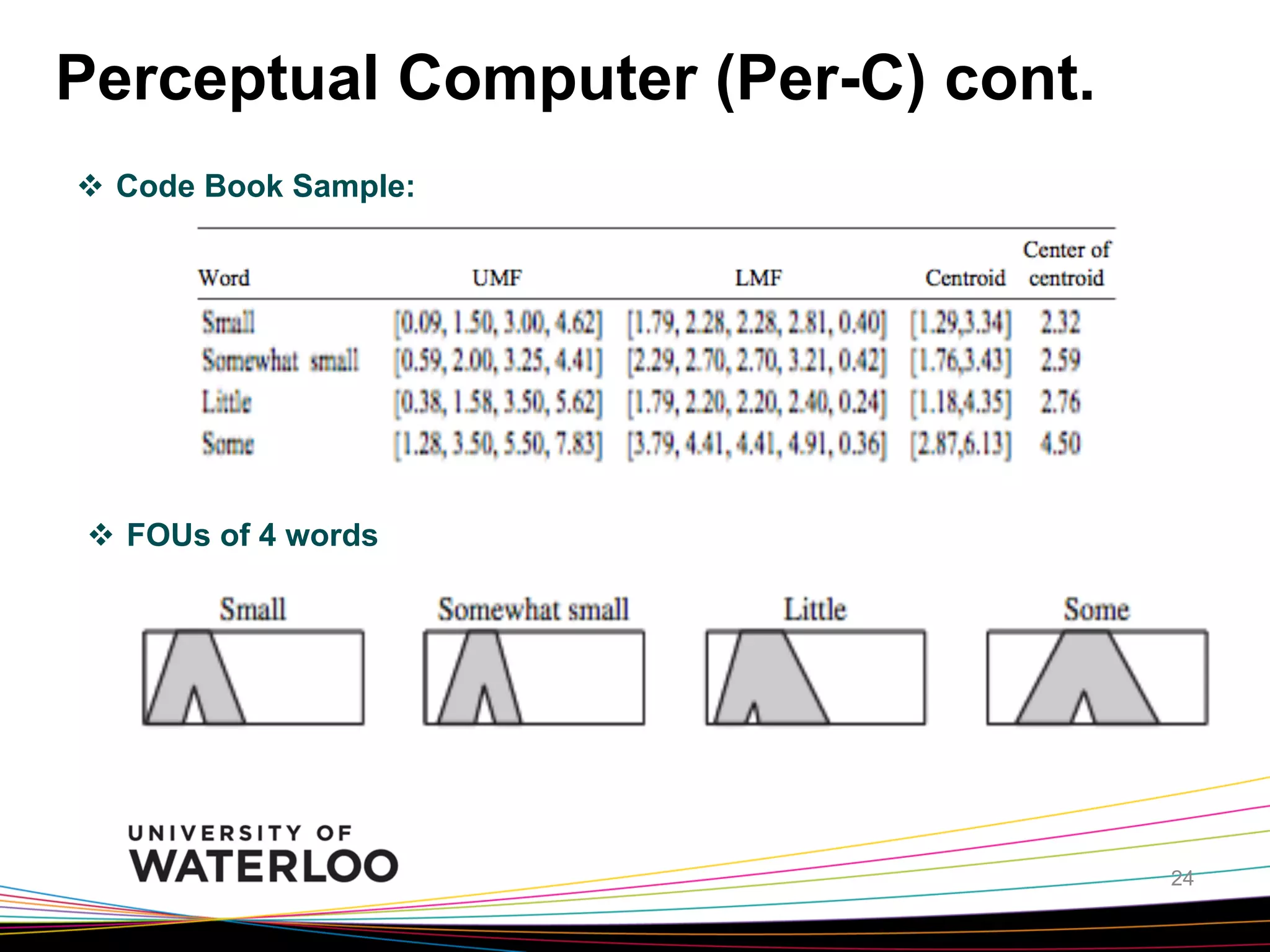
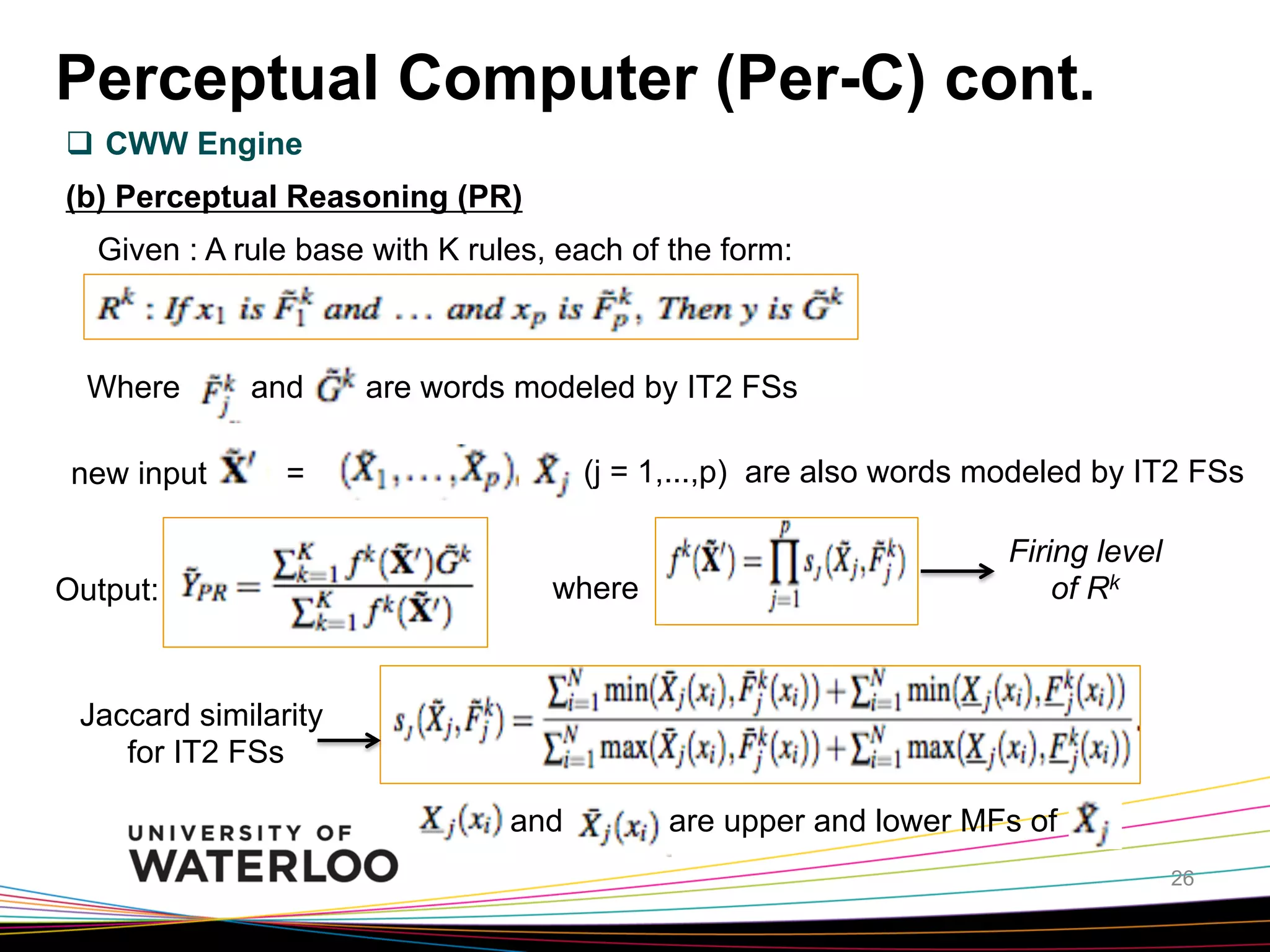
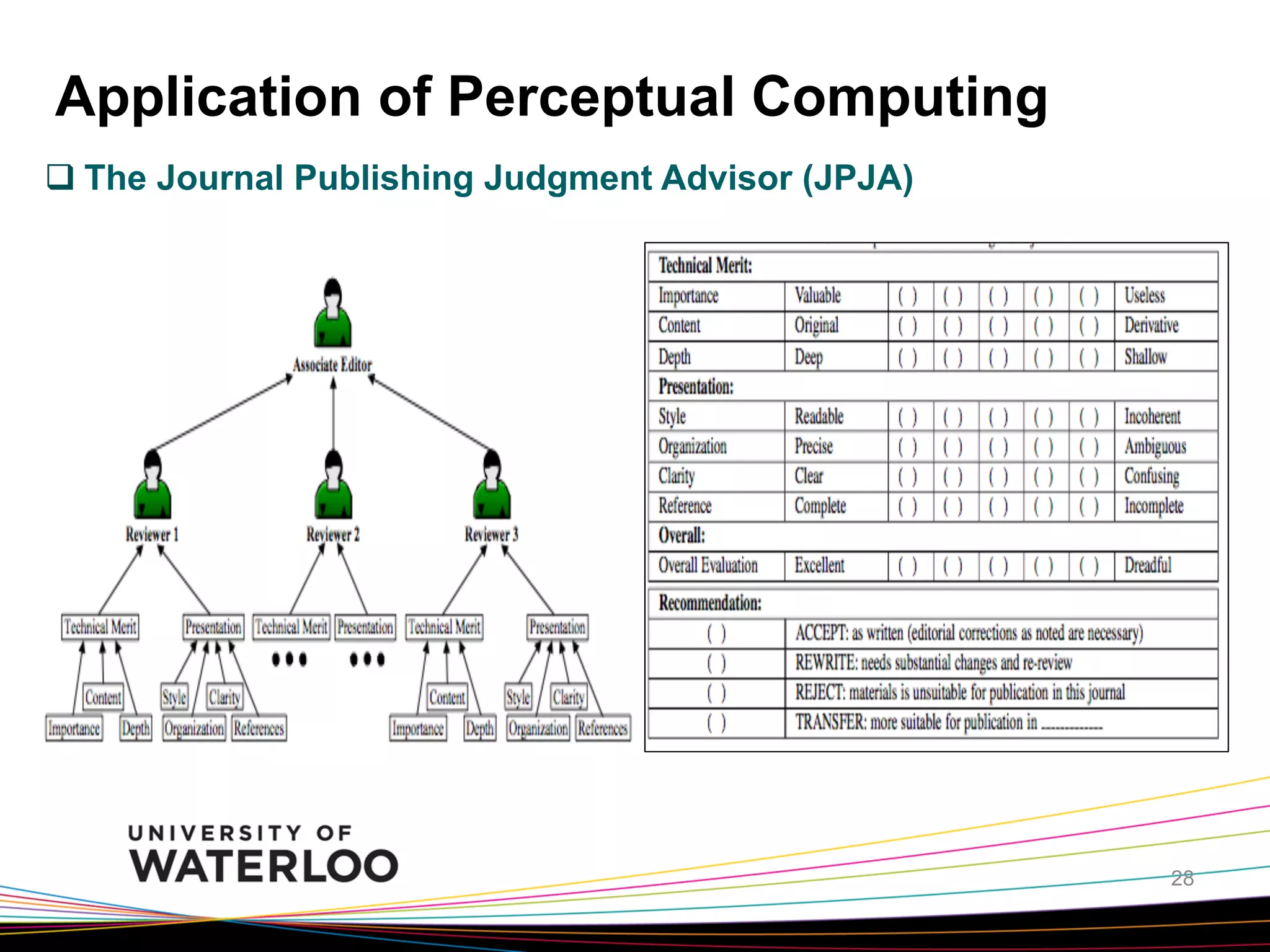
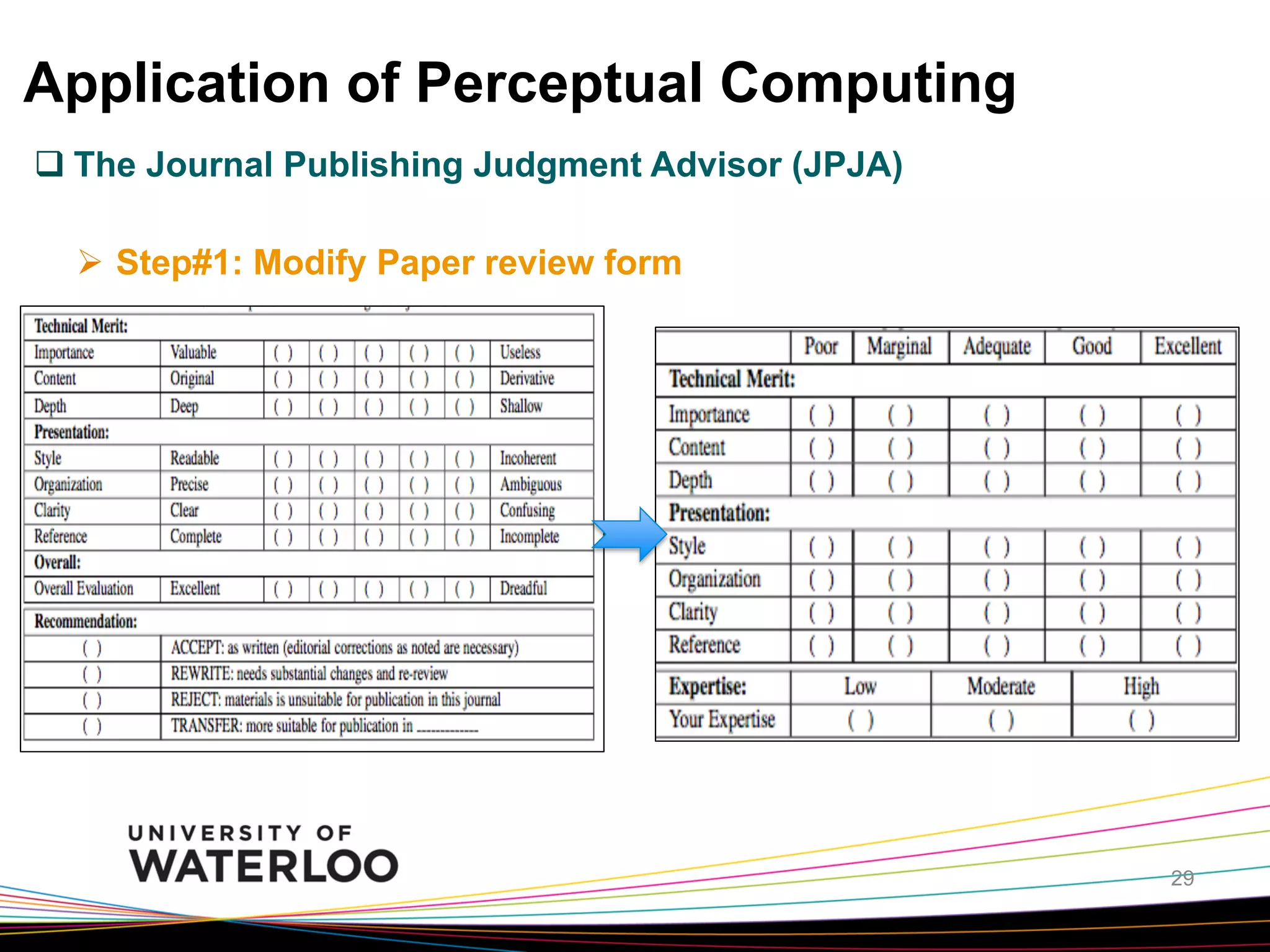
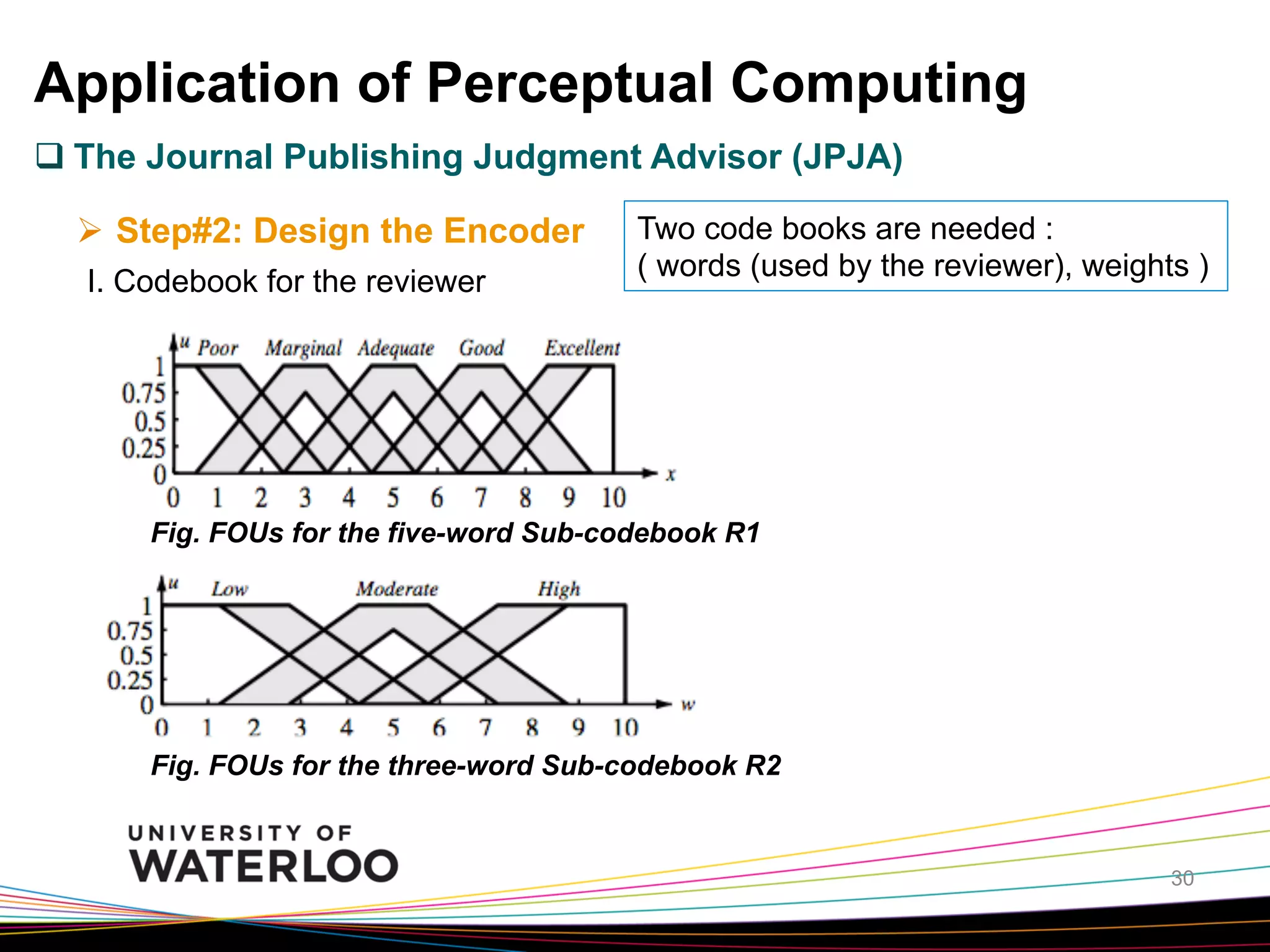
The document introduces type-2 fuzzy sets, which can model uncertainty, and their applications in perceptual computing. It discusses interval and general type-2 fuzzy sets, type-2 fuzzy set theory and operations, type-2 fuzzy systems, and an example of using type-2 fuzzy logic for image edge detection. It then explains computing with words, perceptual computing using type-2 fuzzy logic to model linguistic uncertainty, and presents an example application of a journal publishing judgment advisor that uses perceptual computing.








![Computing with Words (CWW)
CWW
is
:
“A
methodology
in
which
words
are
used
in
place
of
numbers
for
compu7ng
and
reasoning..”
(Zadeh, 1996- Ref[4])
Distance
=
500
Ann
lives
near
Mary
Example:
consider
the
proposi<ons:
p1
=
Ann
lives
near
Mary
p2
=
Mary
lives
near
Clara.
Query
:
“How
far
is
Ann
from
Clara?,”
Answer:
Ann
lives
not
far
from
Clara.
Fig. Compute with numbers vs.
compute with words
20](https://image.slidesharecdn.com/t2fstalk-131231115128-phpapp01/75/T2-fs-talk-20-2048.jpg)
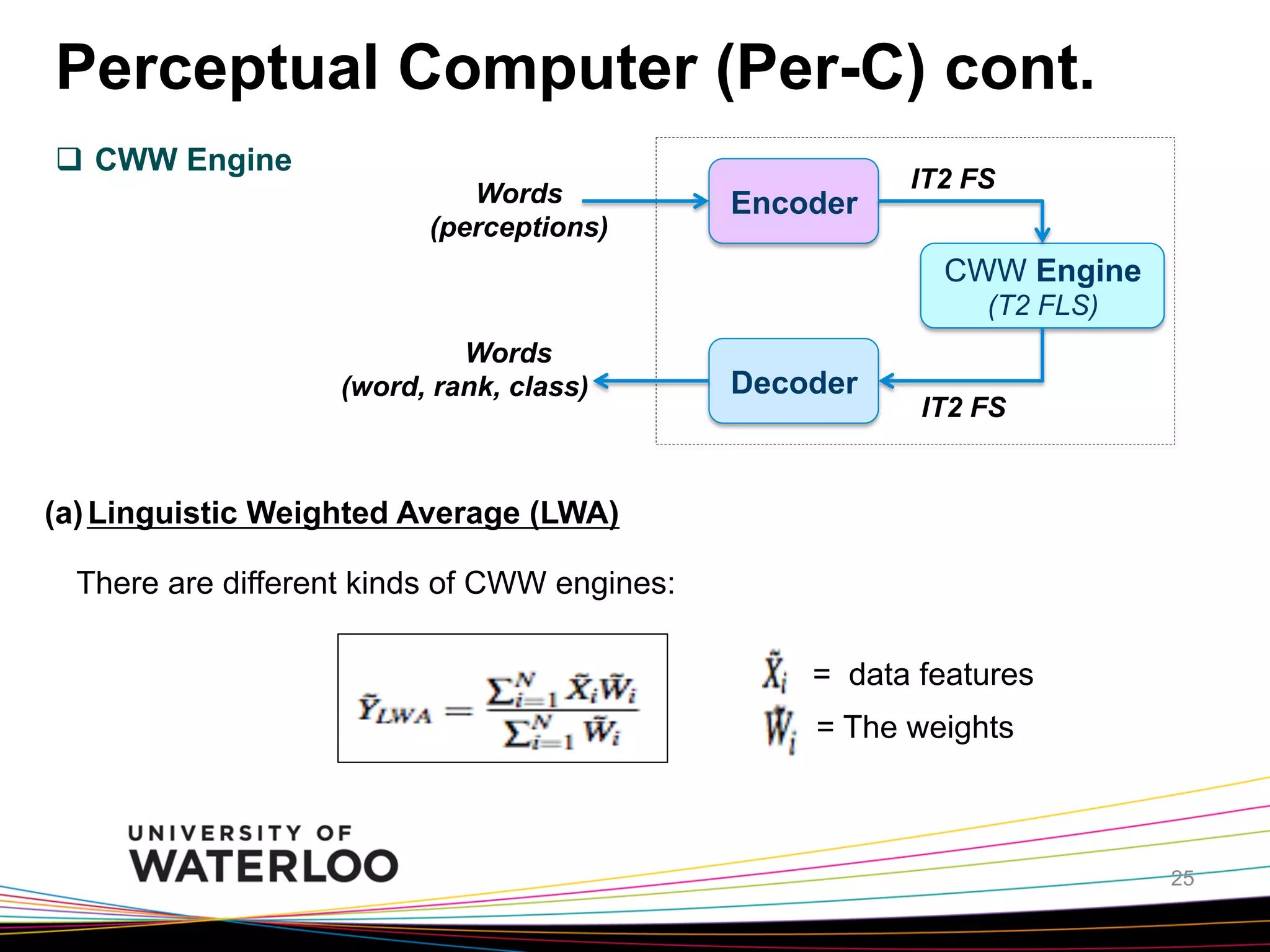
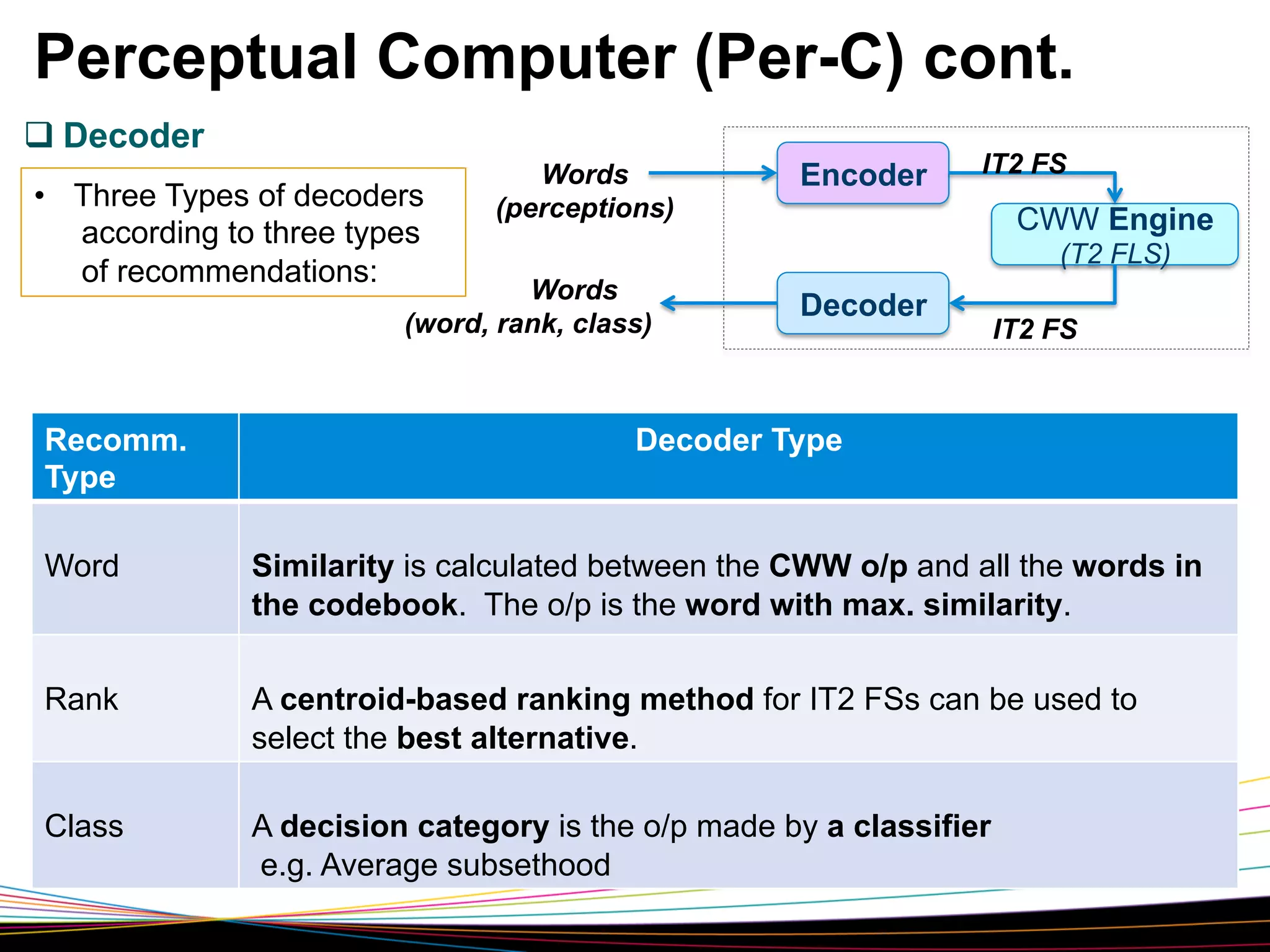
![Perceptual Computer (Per-C)
Words
(perceptions)
Encoder
IT2 FS
CWW Engine
(T2 FLS)
Words
(word, rank, class)
Decoder
IT2 FS
Fig. Architecture of a Per-C (Mendel Ref[5],2002)
•
•
•
Words mean different things to different People = uncertainty in words = FL
Uncertainty a person has about the meaning of a word (intra-personal
uncertainty)=> T1 FL
Uncertainties that a group of people have about the meaning of the word
(inter-personal uncertainty) => T2 FL
[Ref 6]
21](https://image.slidesharecdn.com/t2fstalk-131231115128-phpapp01/75/T2-fs-talk-21-2048.jpg)

![References
•
[1] Oscar Castillo and Patricia Melin. Type-2 Fuzzy Logic: Theory and Applications. 223, 2008
Springer-Verlag Berlin Heidelberg. July 2007.
•
[2] Jerry M. Mendel and Robert I. Bob John. Type-2 Fuzzy Sets Made Simple. IEEE
TRANSACTIONS ON FUZZY SYSTEMS, VOL. 10, NO. 2, APRIL 2002.
•
[3] Jerry M Mendel. Type-2 fuzzy sets and system: an overview. IEEE computational intelligent
magazine, vol 2, no. 1, pp. 20-29. February 2007.
•
[4] L.A. Zadeh, Fuzzy logic = computing with words, IEEE Trans. on Fuzzy Systems 4 (1996)
103-111.
•
[5] J.M. Mendel, An architecture for making judgments using computing with words, Int. J. Appl.
Math. Comput. Sci. 12 (3) (2002) 325–335.
•
[6] J.M.Mendel, Perceptual Computing, Willey, 2010.
37](https://image.slidesharecdn.com/t2fstalk-131231115128-phpapp01/75/T2-fs-talk-37-2048.jpg)