Our Assurance on IT Controls’ Adequacy . Effectiveness . Efficiency
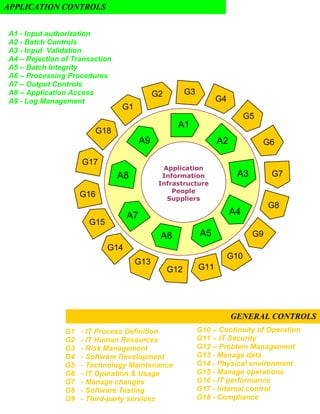
The document discusses Techserv's application systems audit process and methodology. It provides an overview of the audit objectives related to source data preparation, collection, accuracy checks, processing integrity, output handling and transaction authentication. It also outlines the application and general controls that are assessed. The audit methodology involves four phases - engagement scoping, control assessment, audit reporting and follow up to verify findings closure.