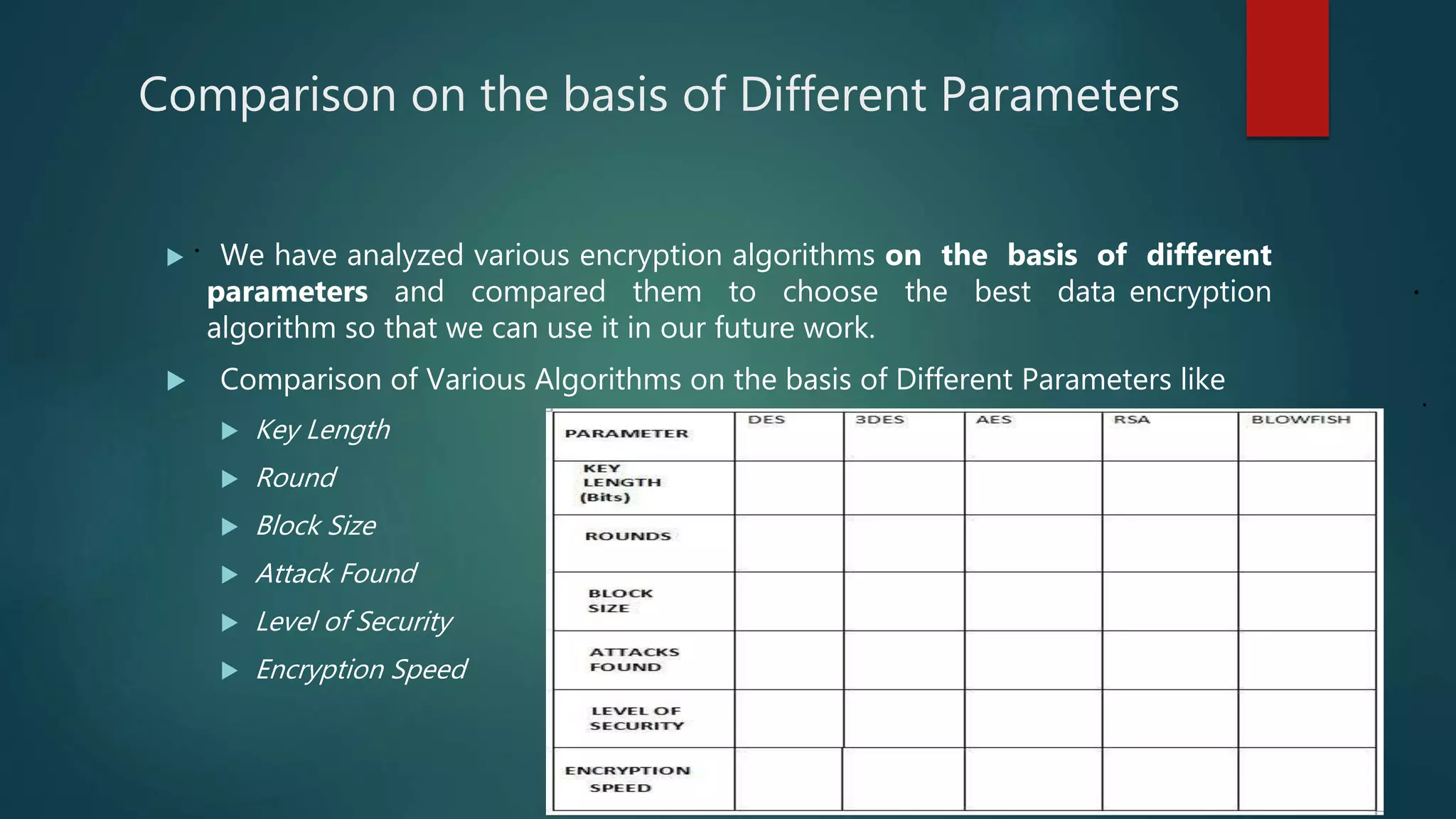
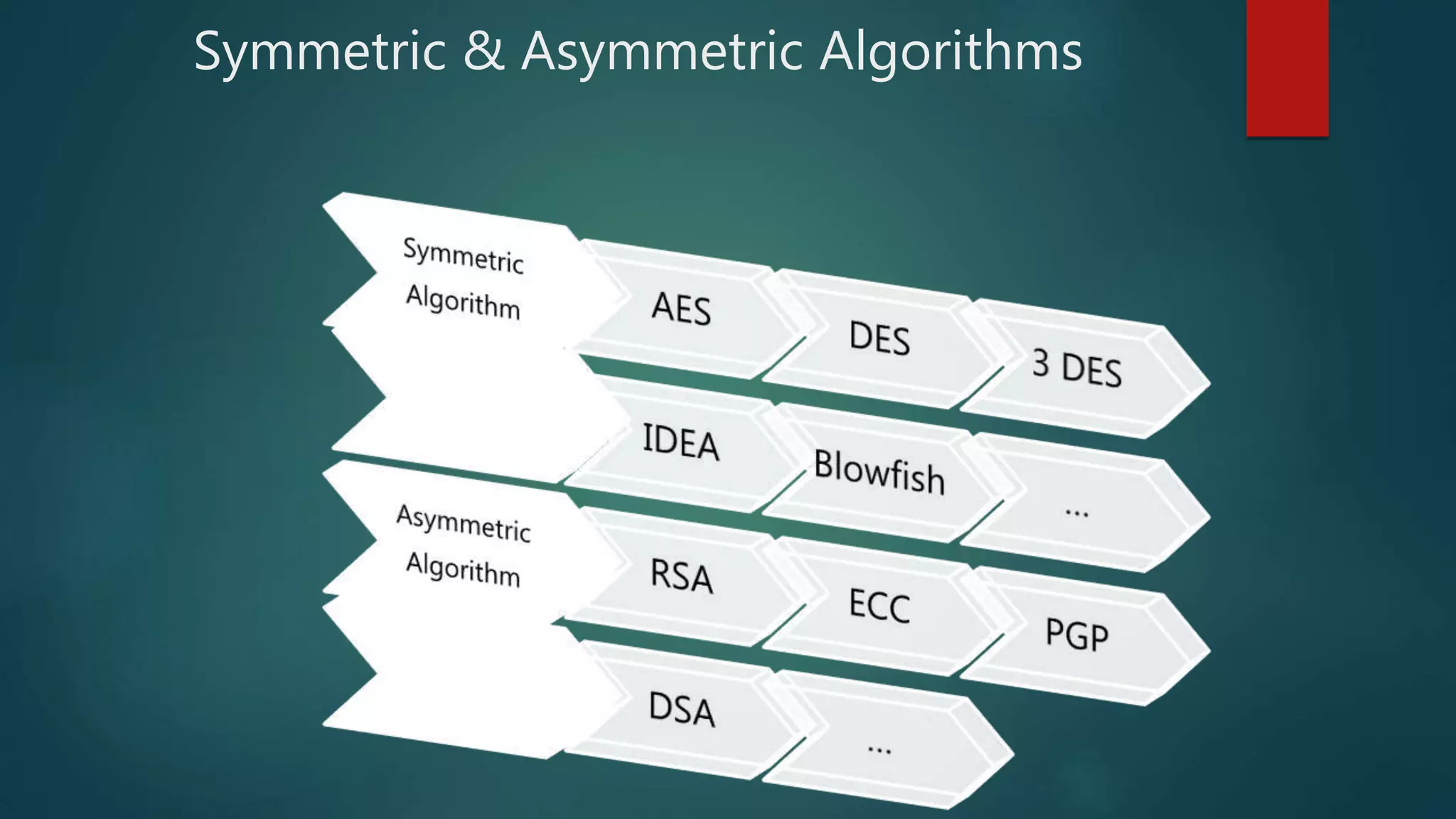
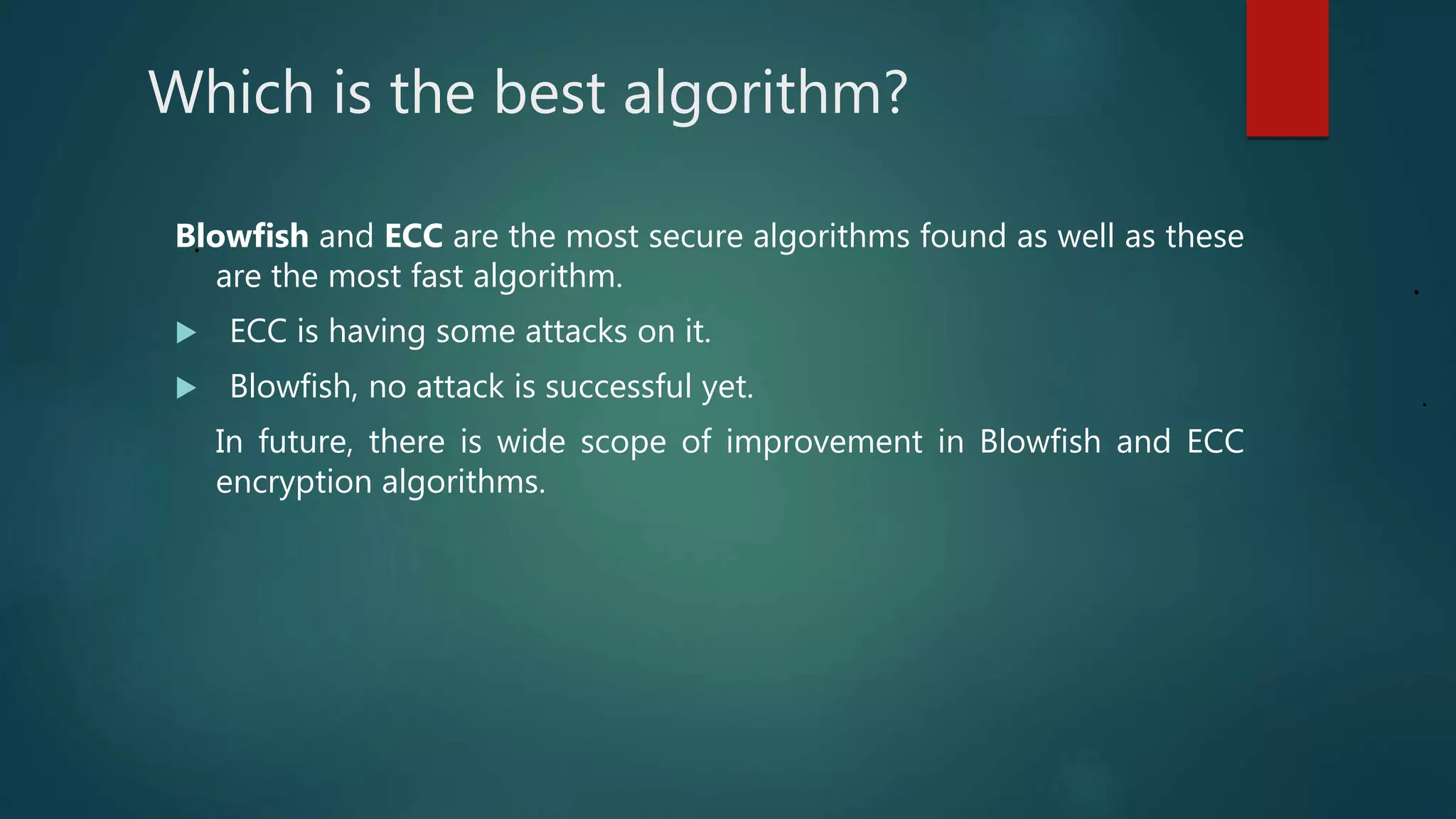
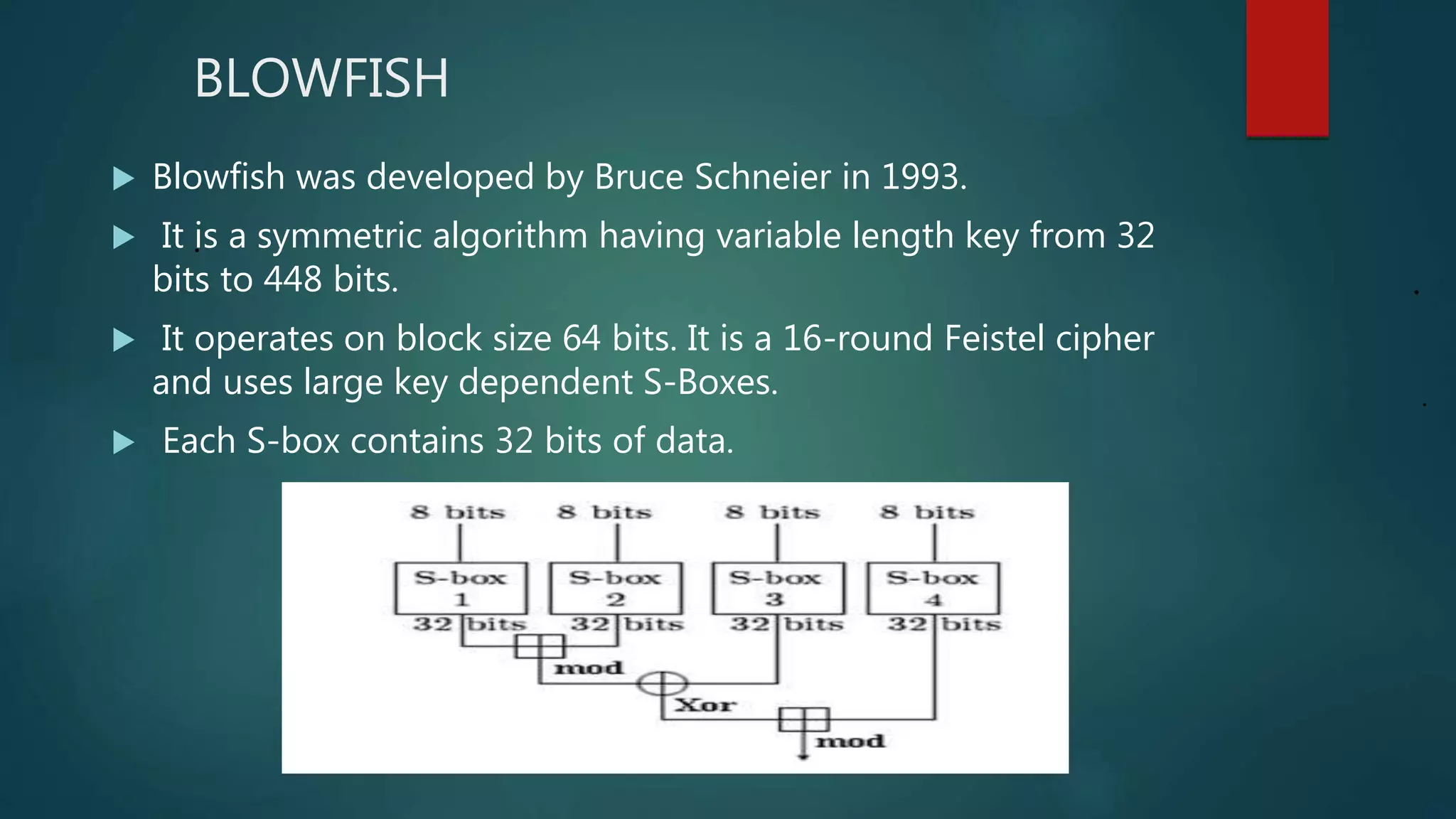
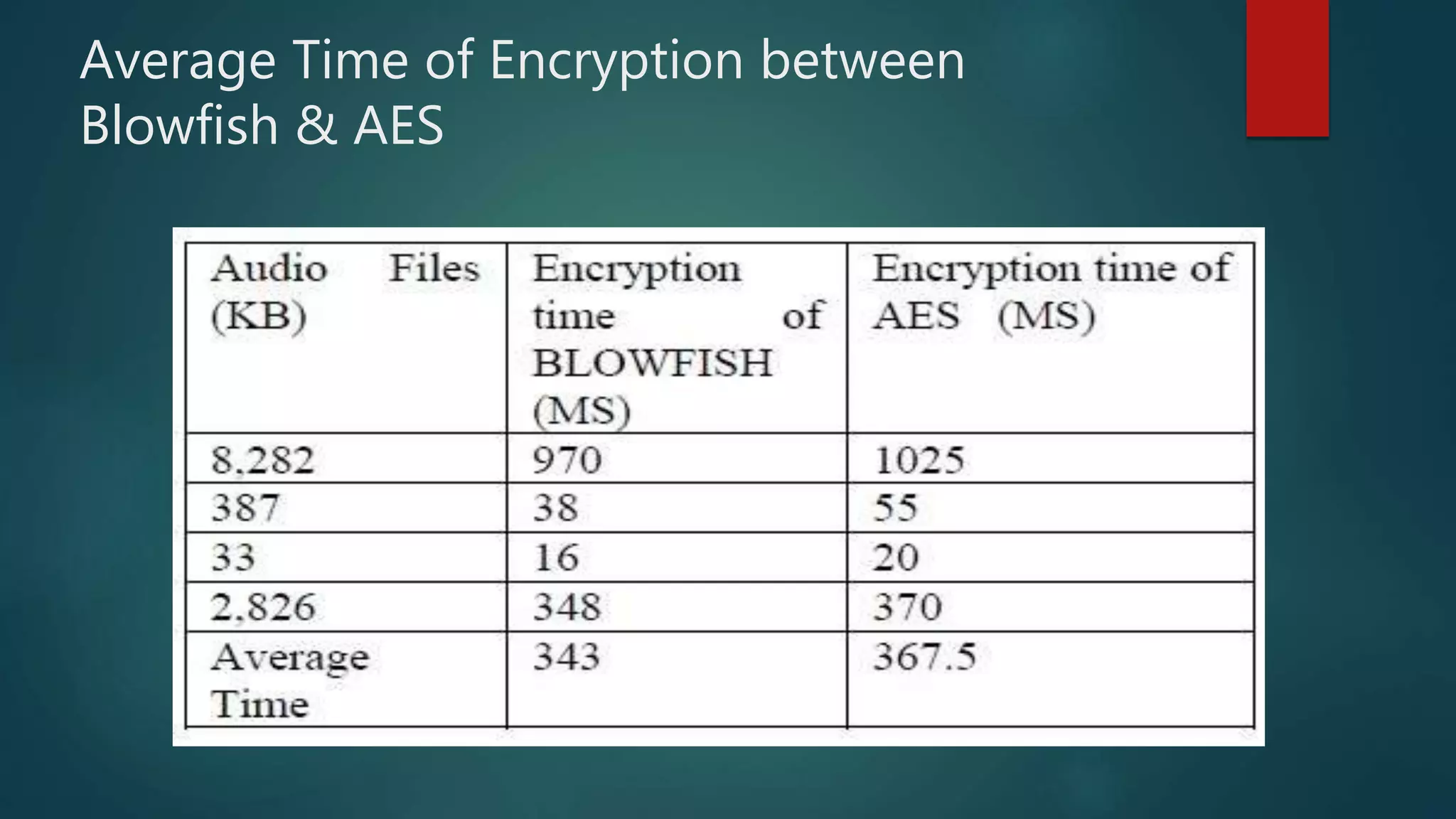
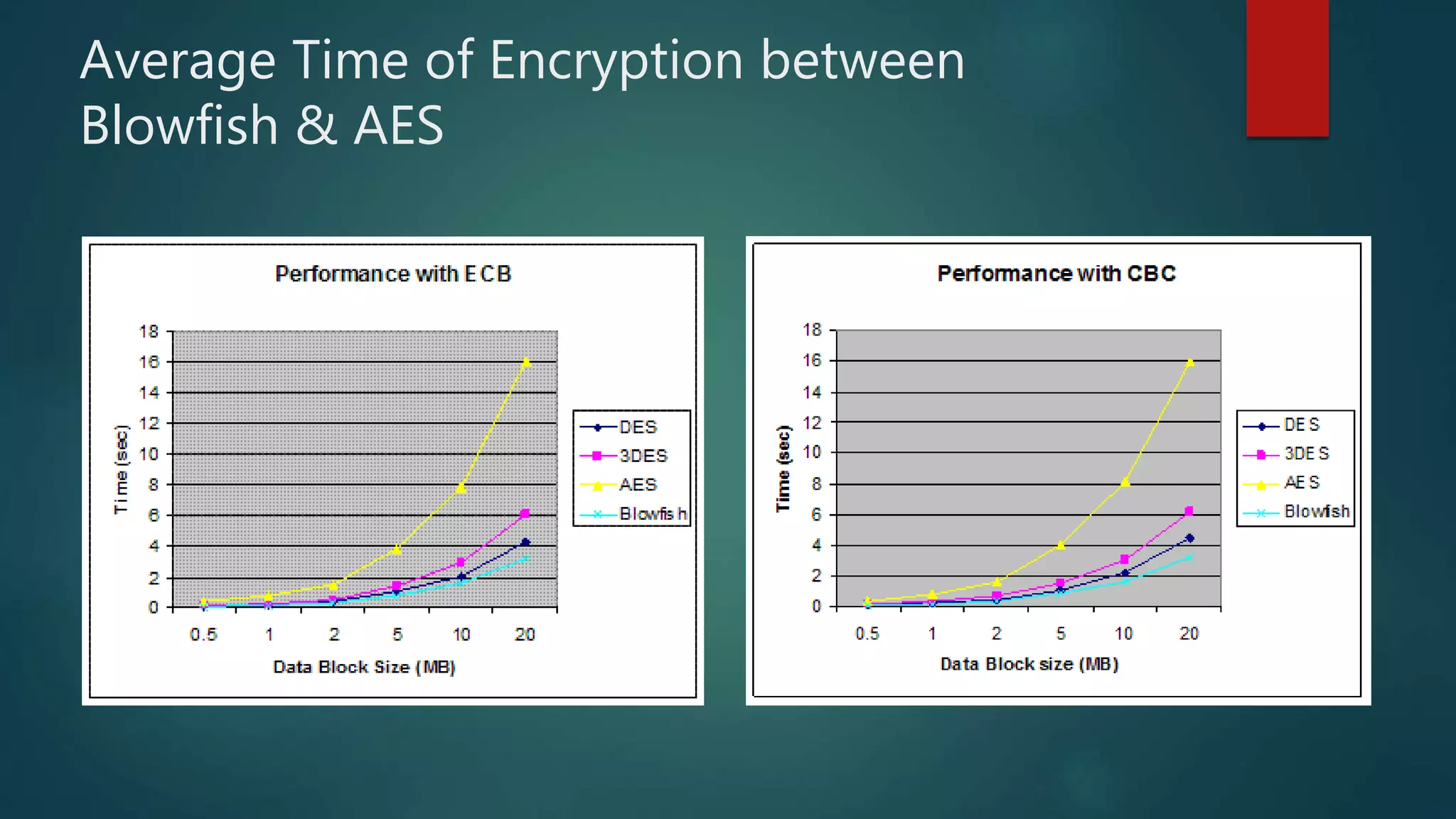
The document provides a comparative analysis of symmetric and asymmetric encryption algorithms, focusing on their efficiency and security levels. It identifies Blowfish and ECC as the most secure and fast algorithms, with Blowfish showing no successful attacks, while ECC has some vulnerabilities. The analysis also discusses parameters like key length, round, and encryption speed to determine the best algorithm for future applications.