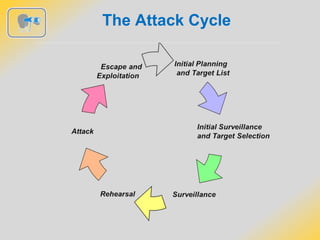
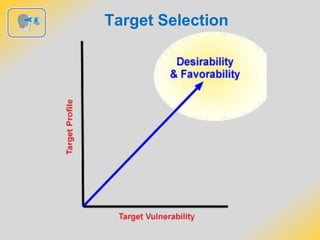
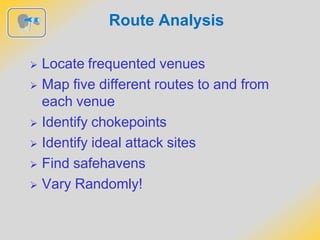
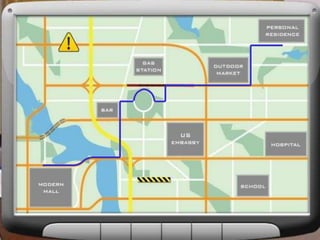
The document outlines strategies for detecting and avoiding surveillance, detailing methods of attack, the distinction between hard and soft targets, and techniques for route analysis. It emphasizes the importance of being aware of one’s surroundings, recognizing behavioral cues, and varying travel patterns to enhance personal security. Practical recommendations for responding to potential attacks include creating distance from threats and notifying security personnel.