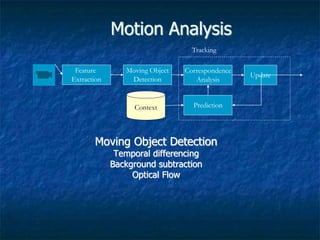
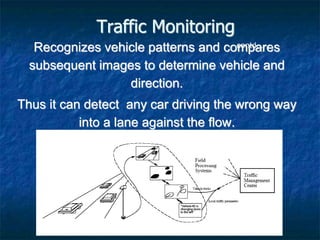
Video analysis and surveillance systems are increasingly important for high-level security applications like monitoring airports, oil refineries, military sites, and traffic. Modern solutions use centralized management of high-resolution cameras, wireless networking, storage of video for over a year, and features like object detection, motion analysis, and alert generation. This allows real-time and offline search of video based on parameters. Case studies demonstrate how these solutions improve security for airports by detecting unattended baggage or intruders, oil refineries by monitoring perimeter fences, and traffic by analyzing congestion and vehicle classification.