Three key points:
1. The document discusses privacy concerns in the information age, noting increased data collection by both government and private organizations and the lack of adequate legal protections and oversight.
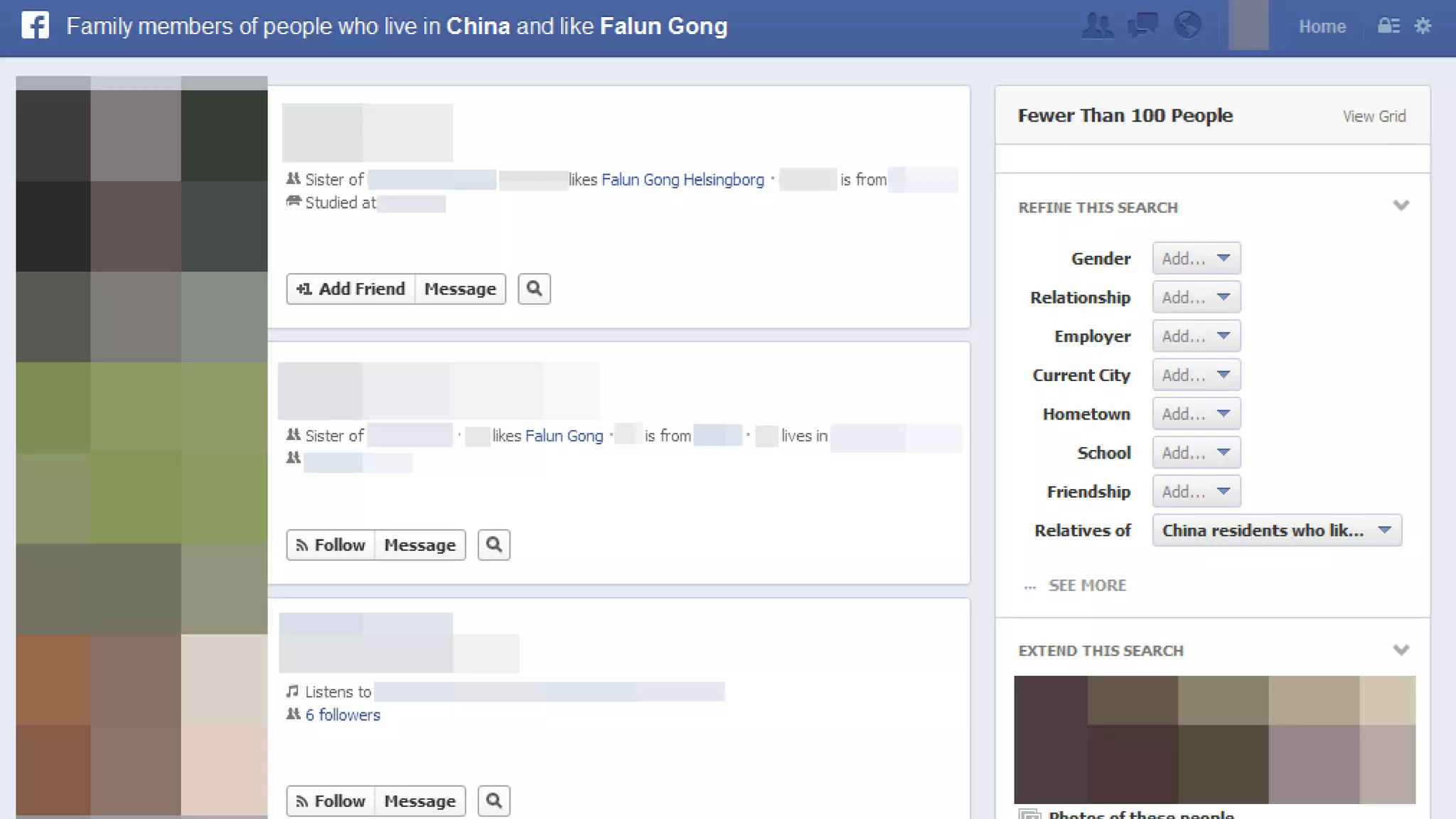
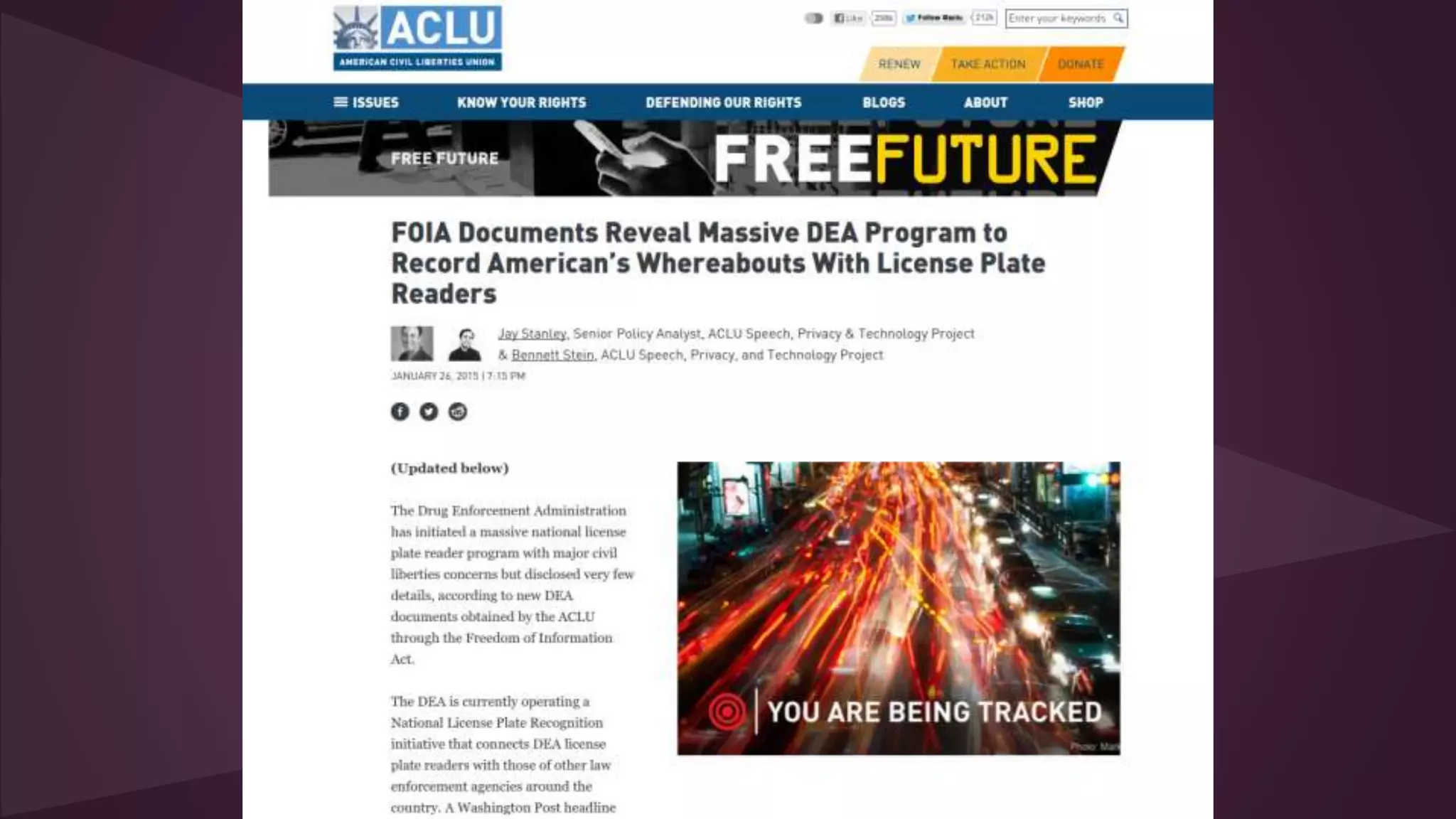
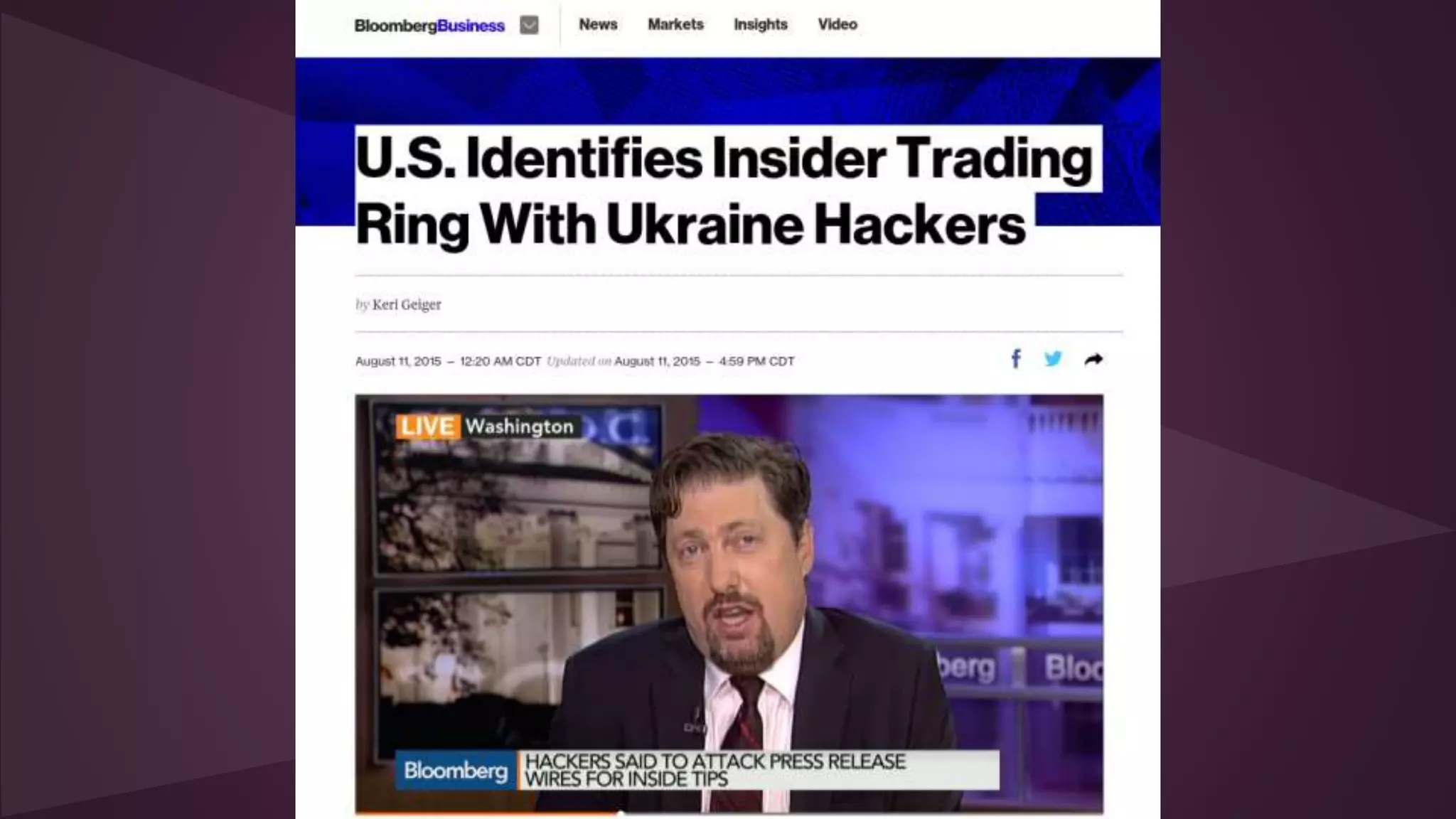
2. Issues addressed include mass surveillance programs, vulnerabilities in internet infrastructure, lack of security practices, and implications for privacy internationally. Countries like the US, China, and Russia are described as major cyber actors.
3. Potential solutions proposed include reforming US surveillance laws, establishing international privacy agreements, incentivizing better security by companies, and consumers practicing layered personal security strategies, though individual options are limited against structural issues. Overall the document outlines growing threats to privacy from inadequate policy responses.




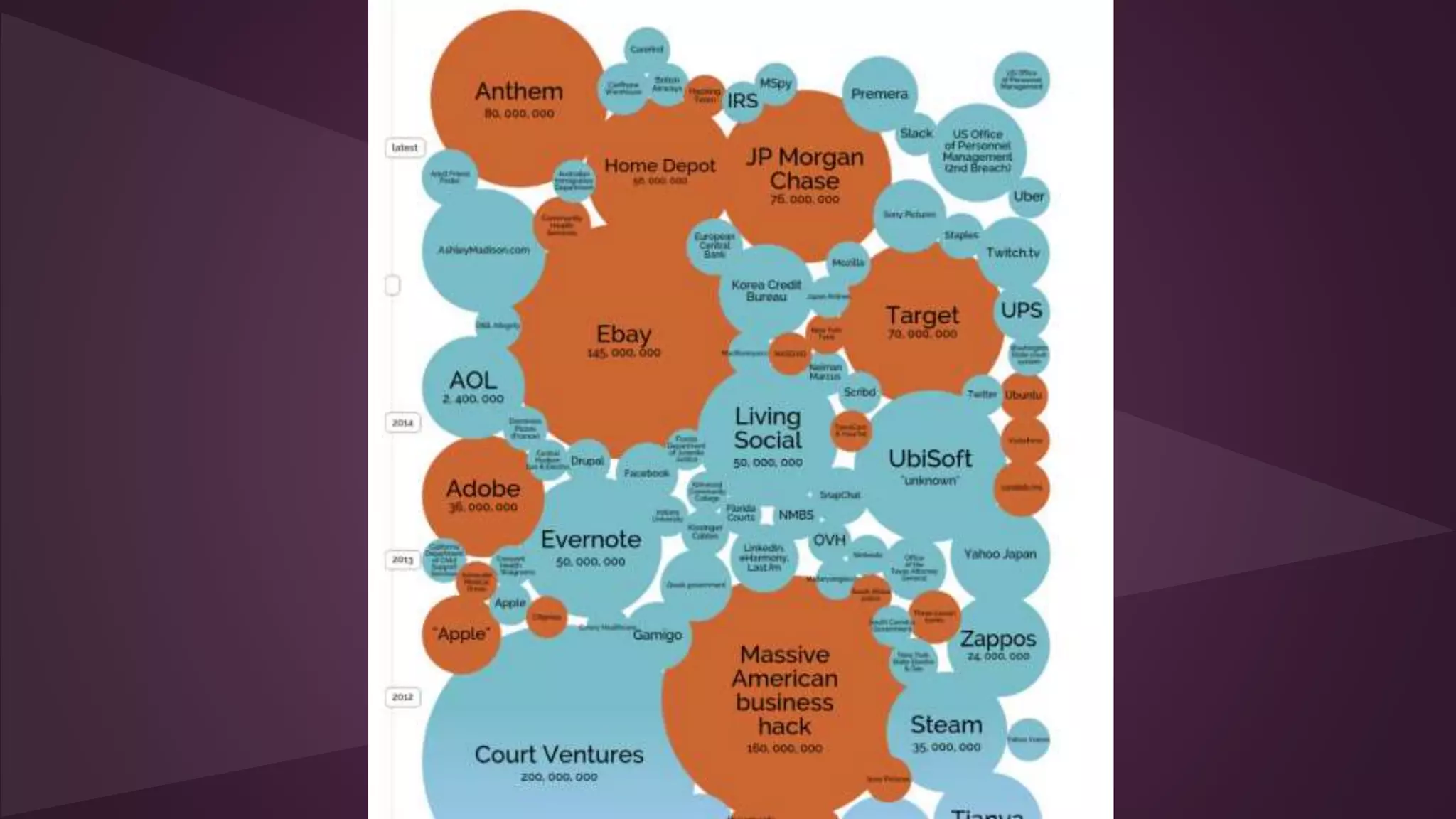


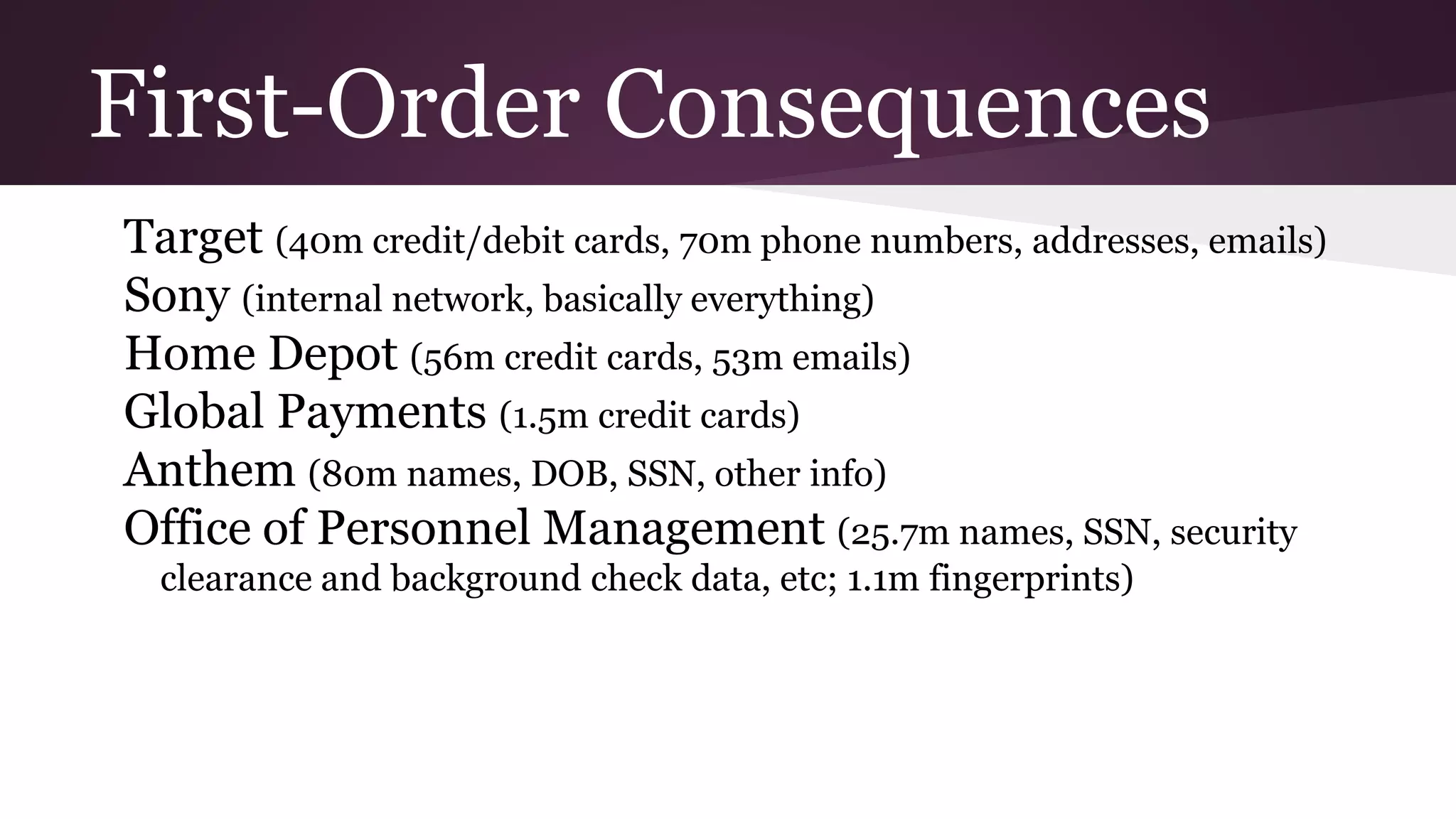
![Negligence and bad norms
Social Security numbers stored by the OPM were not
encrypted due to the networks being “too old.”
—Director Katherine Archuleta admitted in testimony
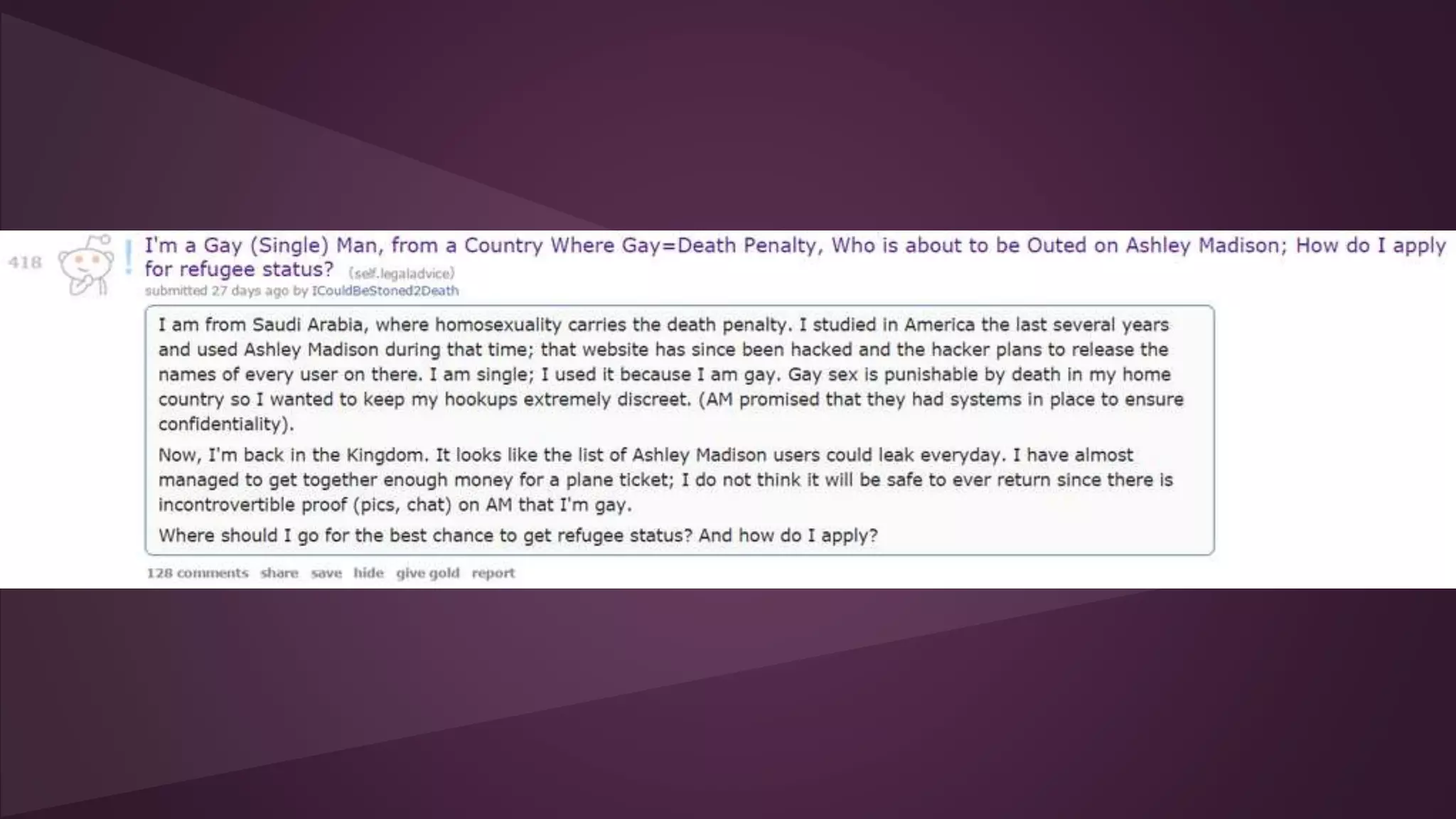
If you paid $19 to delete [your Ashley Madison account,]
[...] your GPS coordinates would not be removed, nor
would your city, state, country, weight, height, date of
birth, whether you smoke and/or like a drink, your
gender, your ethnicity, what turns you on, and other bits
and pieces. And if you didn't pay the 19 bucks,
everything was eventually leaked online by the website's
hackers.
—The Register
Some Samsung smart TVs are sending users’ voice
searches and data over the internet unencrypted,
allowing hackers and snoopers to listen in on their
activity.
—The Guardian](https://image.slidesharecdn.com/privacyintheinformationagev3-150913203647-lva1-app6891/75/Privacy-in-the-Information-Age-Q3-2015-version-10-2048.jpg)



![New York Times: In a six-month period — from Aug 31, 2009, to Feb. 28, 2010, Deutsche Telekom had recorded and
saved [German politican Malte Spitz’s] longitude and latitude coordinates more than 35,000 times. It traced him from a
train on the way to Erlangen at the start through to that last night, when he was home in Berlin.](https://image.slidesharecdn.com/privacyintheinformationagev3-150913203647-lva1-app6891/75/Privacy-in-the-Information-Age-Q3-2015-version-20-2048.jpg)


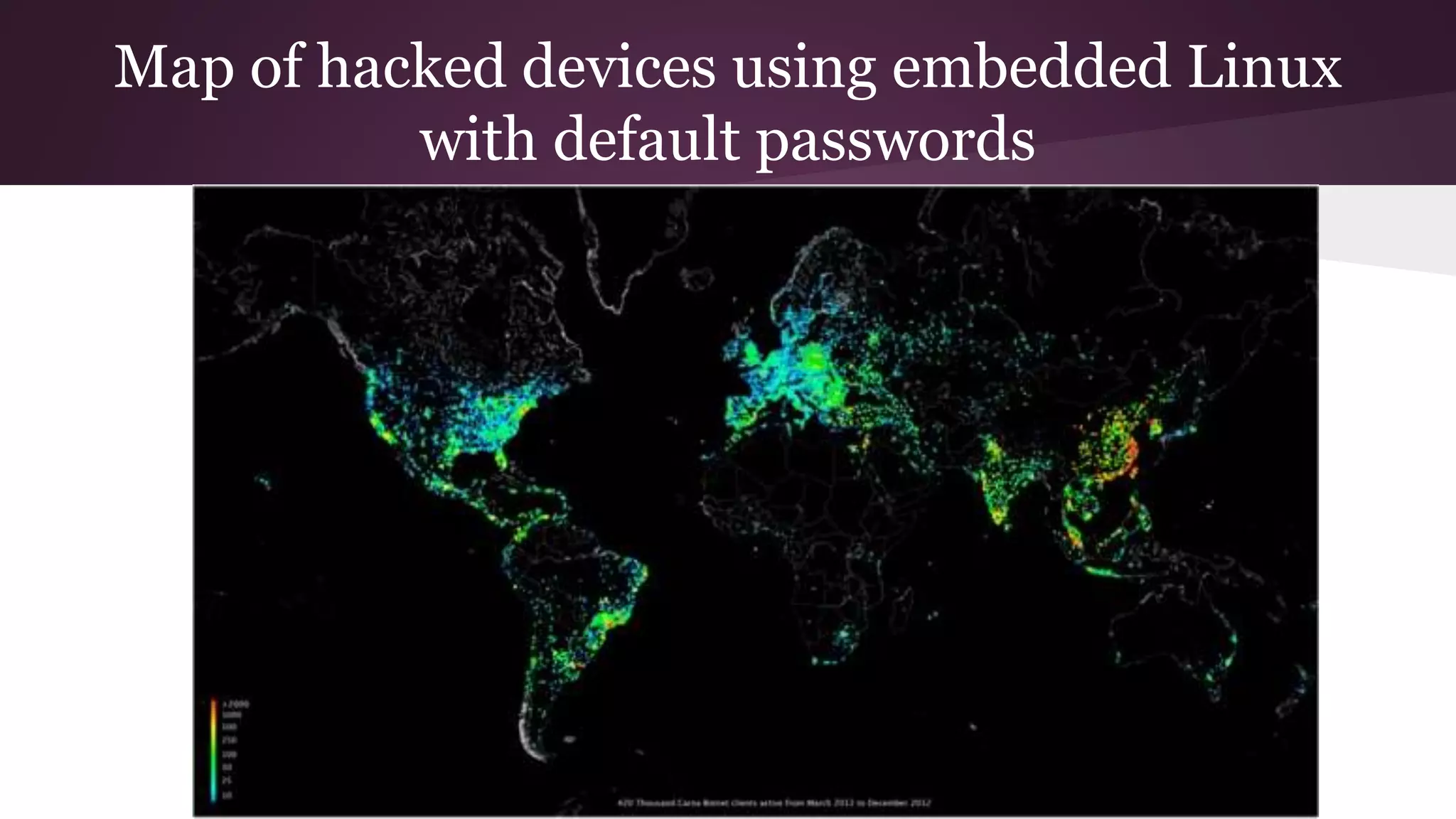
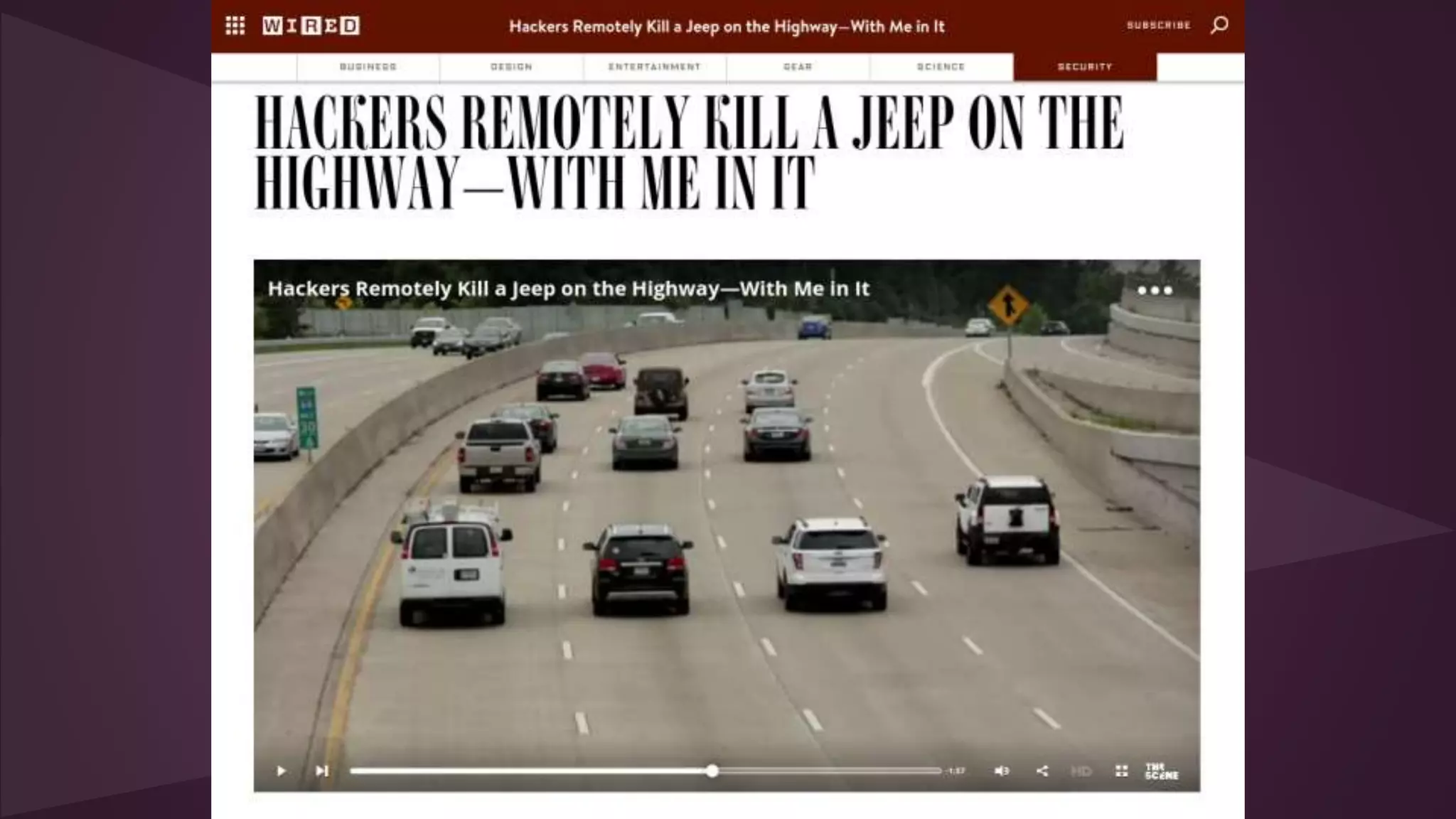


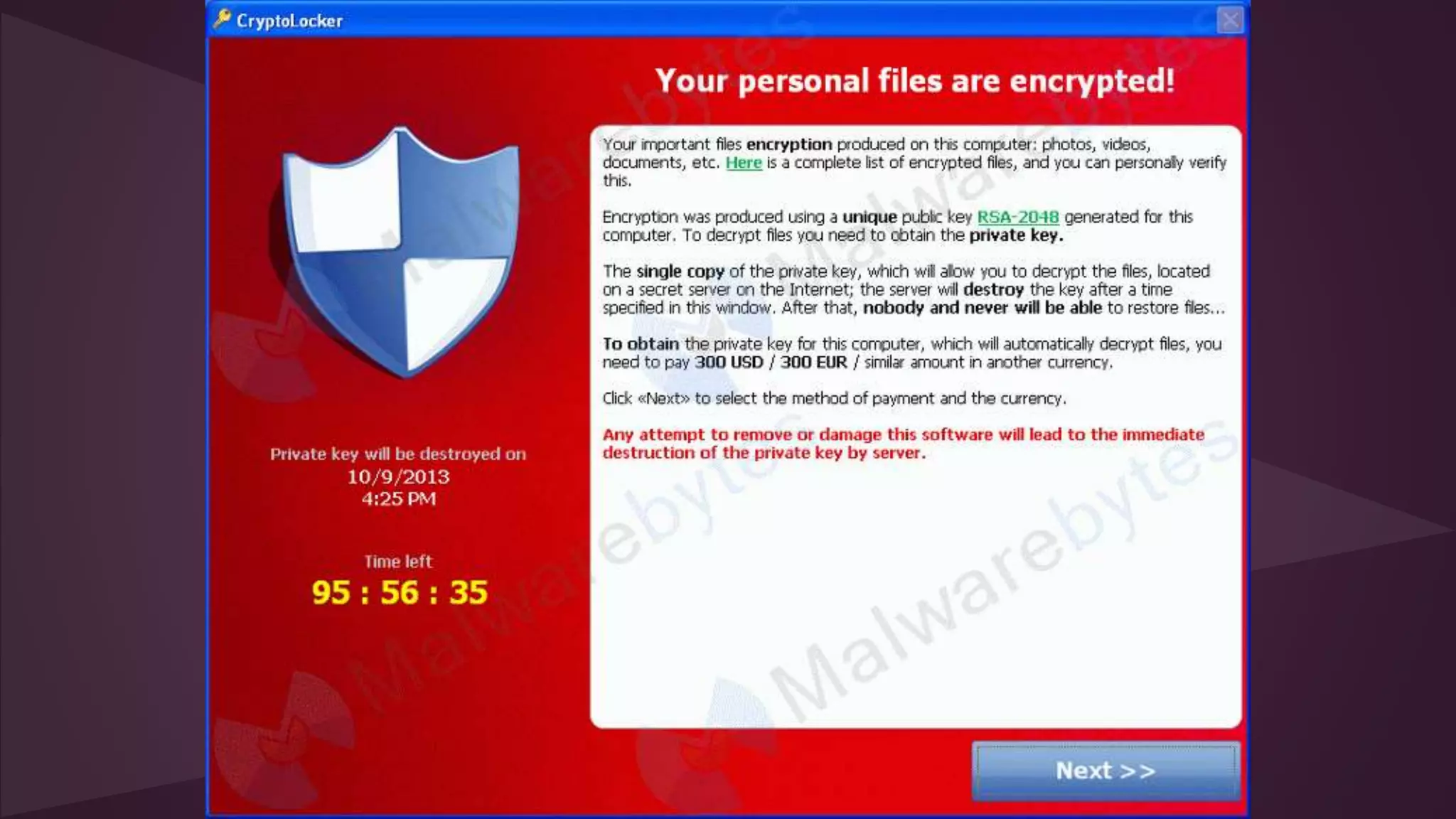
![Technology cuts both ways
Western do-gooders may
have missed how [the
internet]… entrenches
dictators, threatens
dissidents, and makes it
harder – not easier –to
promote democracy.
—Evgeny Morozov](https://image.slidesharecdn.com/privacyintheinformationagev3-150913203647-lva1-app6891/75/Privacy-in-the-Information-Age-Q3-2015-version-31-2048.jpg)


![Costs to Security
Falling behind the rapid development of Internet technology and
applications, our current management of the Internet is
seriously flawed and cannot function properly. [...] How to
strengthen oversight within a legal framework and guide public
opinion and how to ensure the orderly dissemination of online
information, while at the same time safeguarding national
security and social stability, have become pressing problems for
us.
- Xi Jinping, Explanatory Notes to the “Decision of the CPC
Central Committee on Some Major Issues”](https://image.slidesharecdn.com/privacyintheinformationagev3-150913203647-lva1-app6891/75/Privacy-in-the-Information-Age-Q3-2015-version-34-2048.jpg)

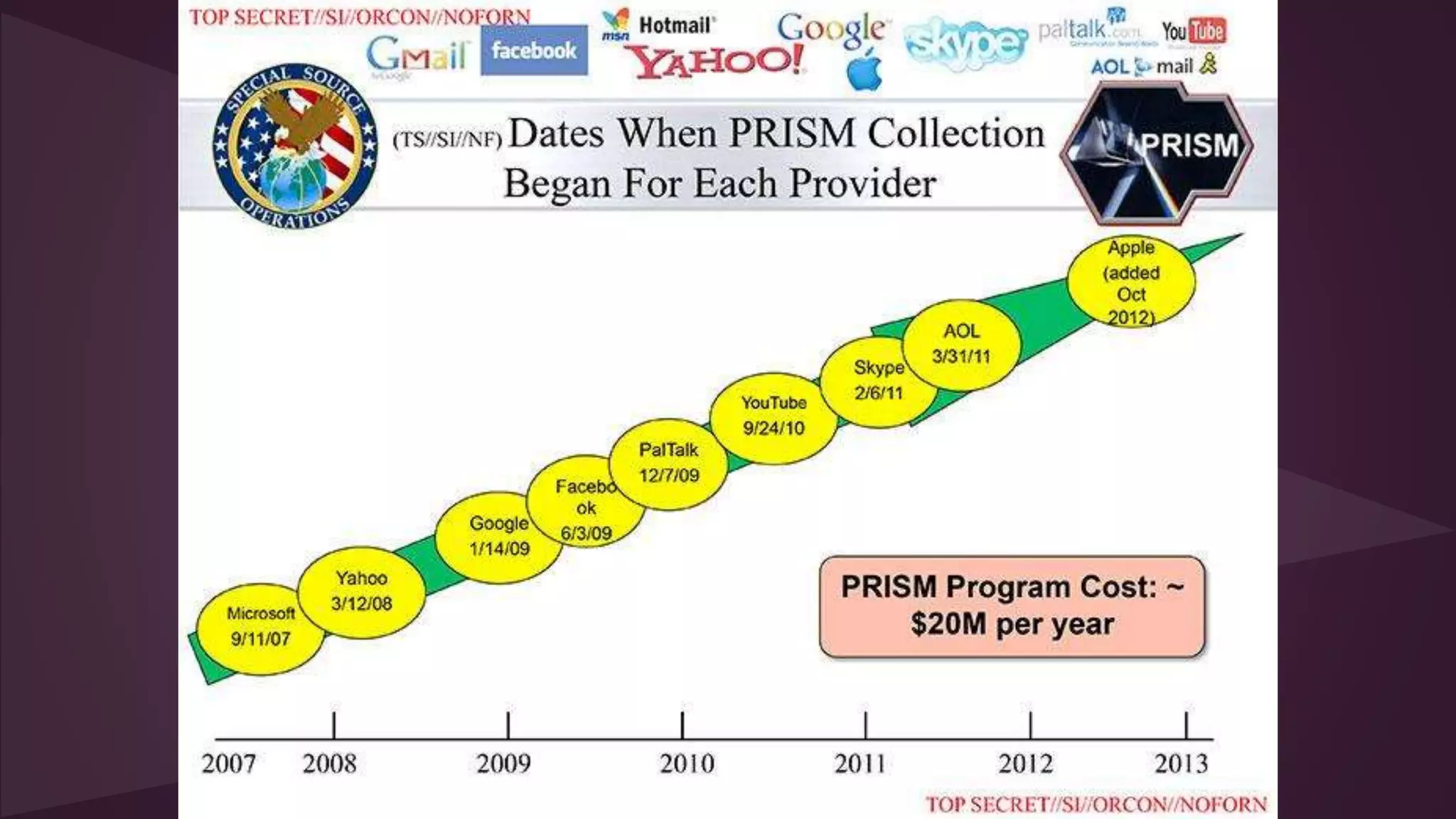


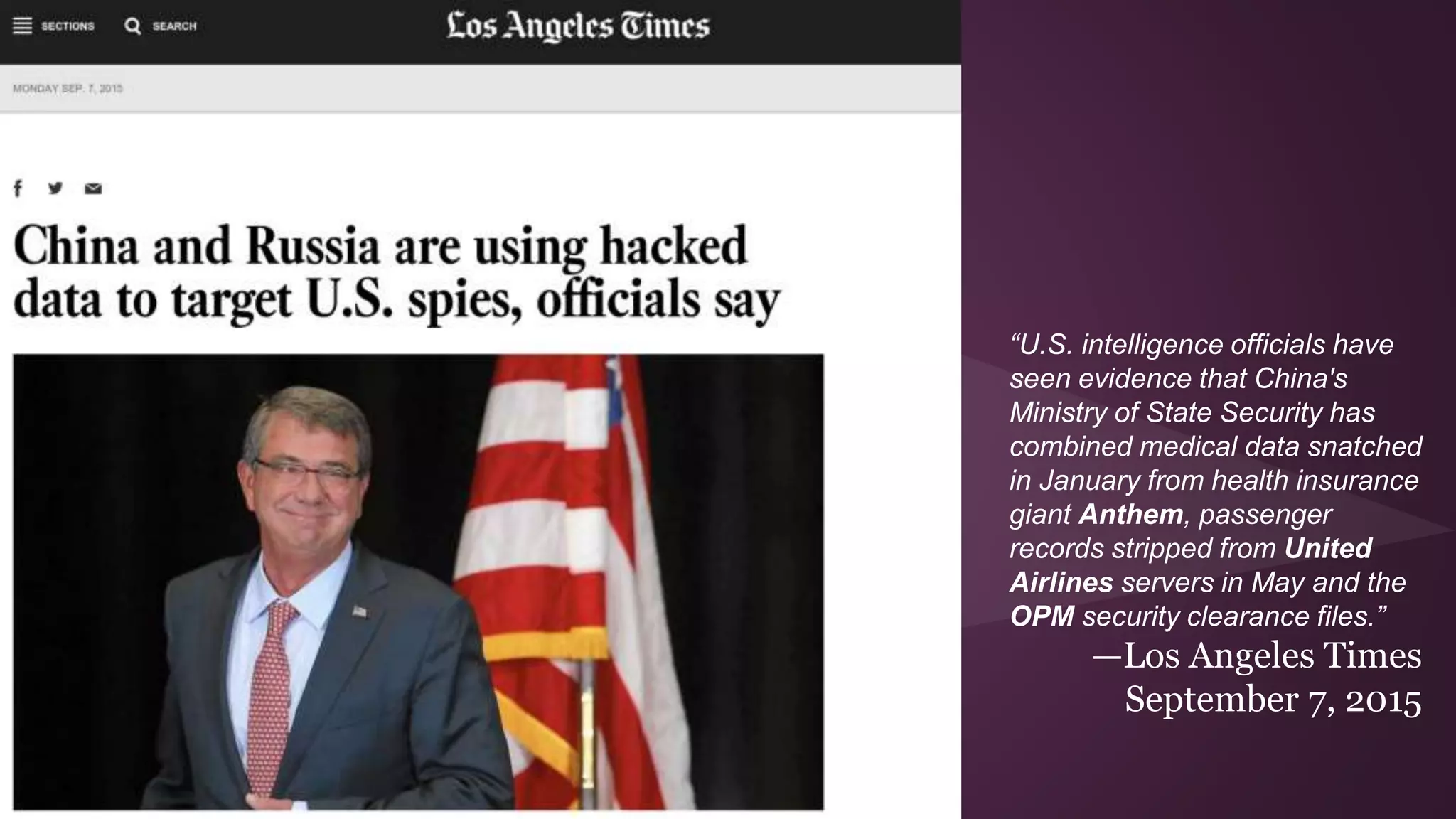
![Executive Order 12333
Status: 1981 Executive Order under Reagan, Currently Active
What it was supposed to do: Gives the NSA broad authorities to conduct surveillance
outside the United States and collect data on Americans.
How it was misused: No protections for U.S. citizens whose information is held outside of
the United States.
At least in 2007, the president believed he could modify or ignore [Executive Order 12333] at
will and in secret. As a result, we know very little about how Executive Order 12333 is being
interpreted inside the NSA.
- Bruce Schneier](https://image.slidesharecdn.com/privacyintheinformationagev3-150913203647-lva1-app6891/75/Privacy-in-the-Information-Age-Q3-2015-version-40-2048.jpg)