This document presents a proposed improved LSB steganography system for hiding text and images. The system uses the least significant bit and pseudo-random encoding techniques to embed secret data into cover images. The proposed system was able to achieve a peak signal-to-noise ratio of 49.32 and 94% accuracy when tested on different image sets, outperforming existing LSB substitution methods. The document describes the embedding and extracting algorithms of the proposed system and compares its performance to other steganography techniques based on imperceptibility and robustness.

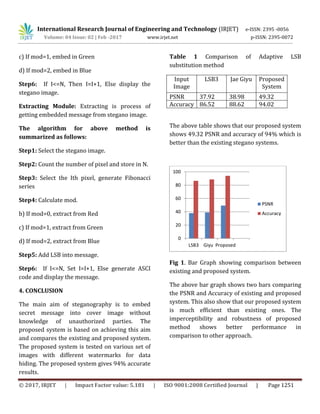
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395 -0056
Volume: 04 Issue: 02 | Feb -2017 www.irjet.net p-ISSN: 2395-0072
© 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal | Page 1252
5. REFRENCES
[1] Vijay Kumar Sharma, Vishal Shrivastavaa,
Steganography Algorithm for Hiding Image In
Image By Improved LSB Substitution By
Minimize Detection.
[2] Gurpreet Kaur, Kamaljeet Kaur, Image
Watermarking Using LSB (Least Significant Bit).
[3] Amit Singh, Susheel Jain, Anurag Jain, Digital
watermarking method using replacement of
second Least Significant Bit(LSB) with inverse of
LSB
[4] Nayan K. Dey, Suman K. Mitra, Ashish N.
Jadhav, Hybrid Scheme for Robust Digital Image
Watermarking Using Dirty Paper Trellis Codes.
[5] Lahouri Ghoti, Ahmed Bouridane,
Mohammad K. Ibrahim, and Said Boussakta,
Digital Image Watermarking Using Balanced
Multiwavelets.
[6] Amir Houmansadr, Shahrokh
Ghaemmaghami, A Digital Image Watermarking
Scheme based on Visual Cryptography.
[7] Neil F. Johnson2, Zoran Duric1, and Sushil
Jajodia2, recovery of Watermarks from Distorted
Images.
[8] Henri Bruno Razafindradina and Attumani
Mohamed Karim, Blind and Robust Images
watermarking based on Wavelet and Edge
Insertion.
[9] Prabhishek Singh, R S Chadha, A survey of
Digital Watermarking Techniques, Applications
and Attacks.
[10]Vinita Gupta, Mr. Atul Barve, A Review on
Image Watermarking and its Techniques.](https://image.slidesharecdn.com/irjet-v4i2244-171118100842/85/Steganography-System-for-Hiding-Text-and-Images-Using-Improved-LSB-Method-4-320.jpg)