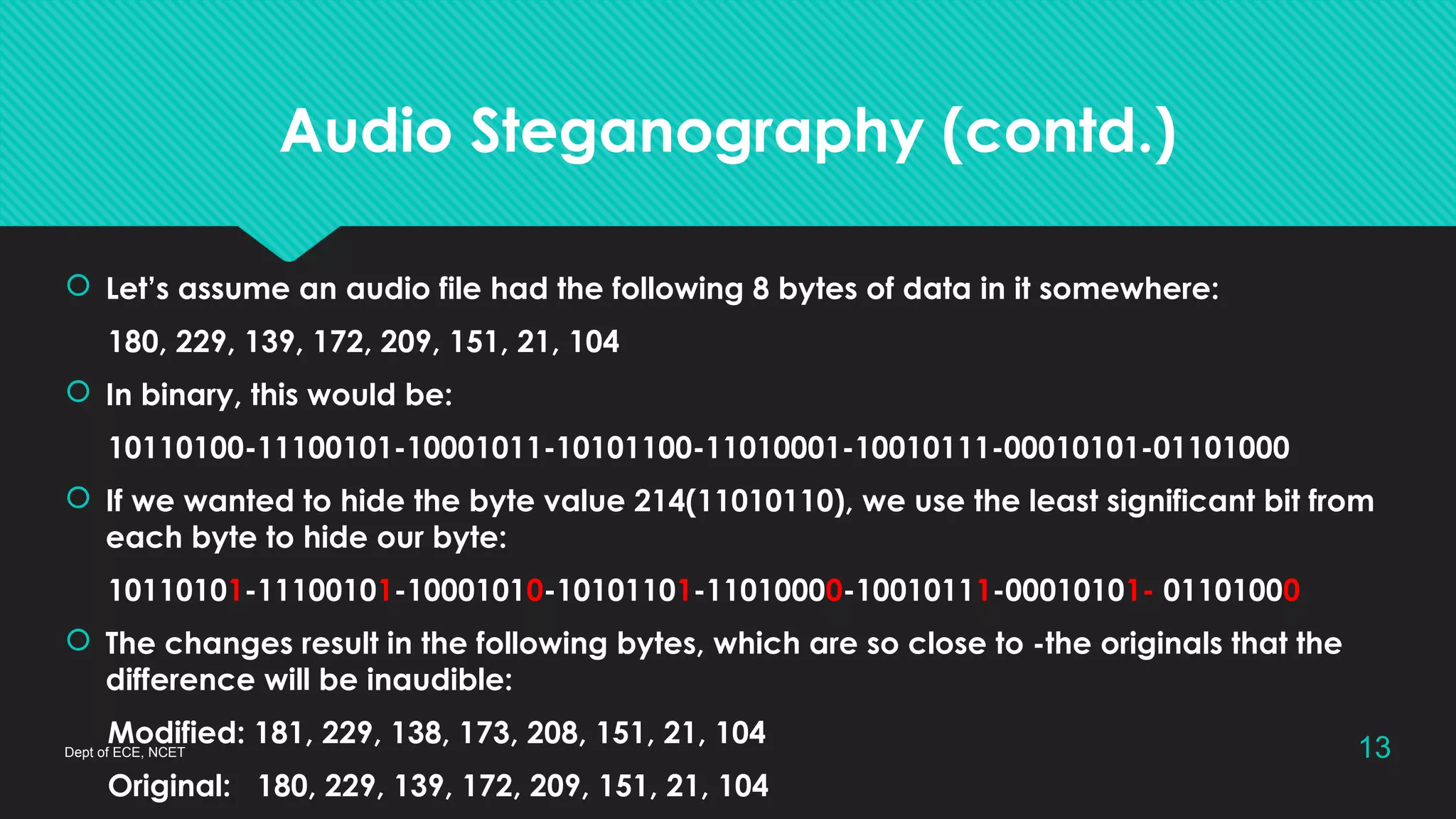
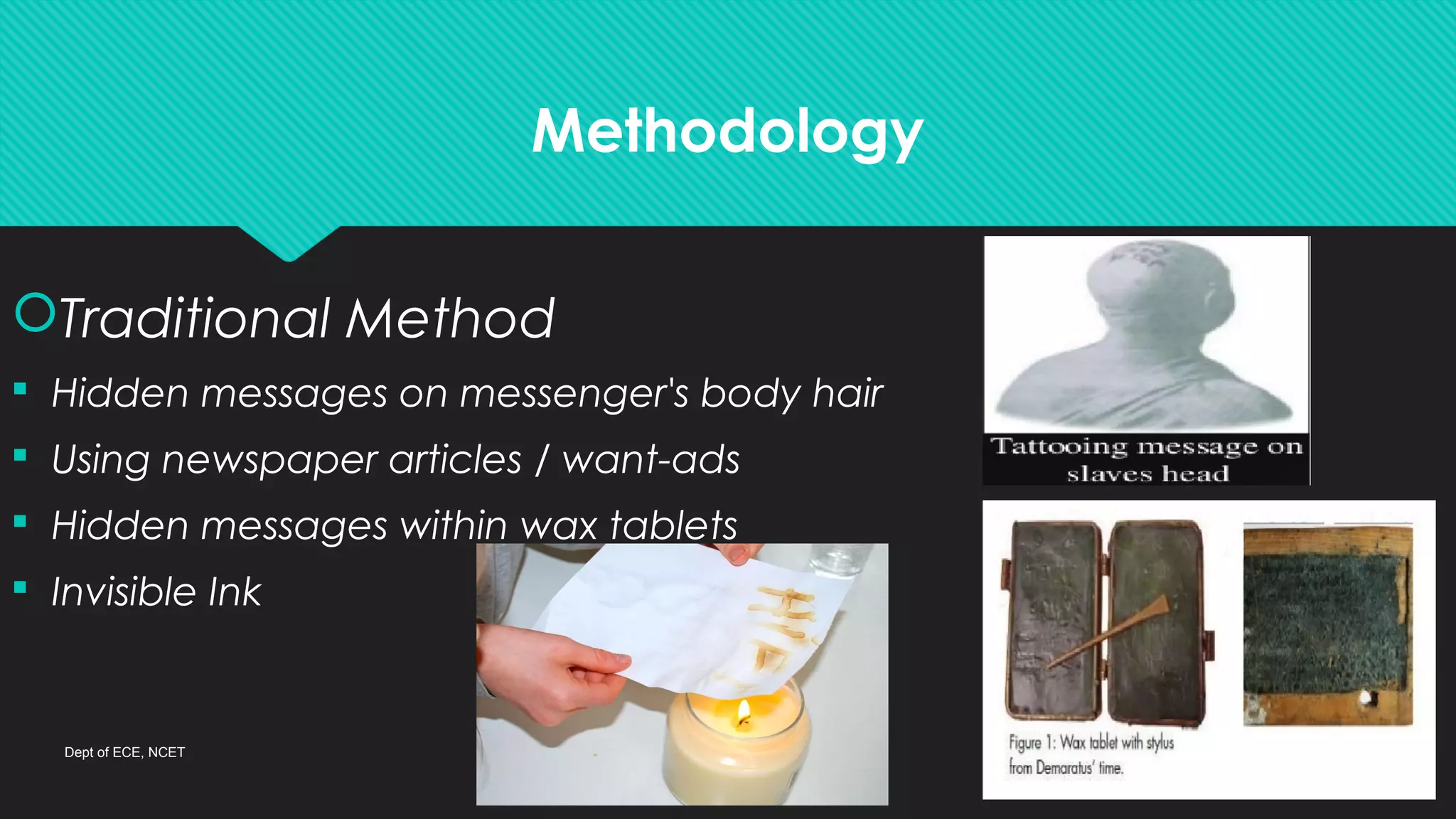
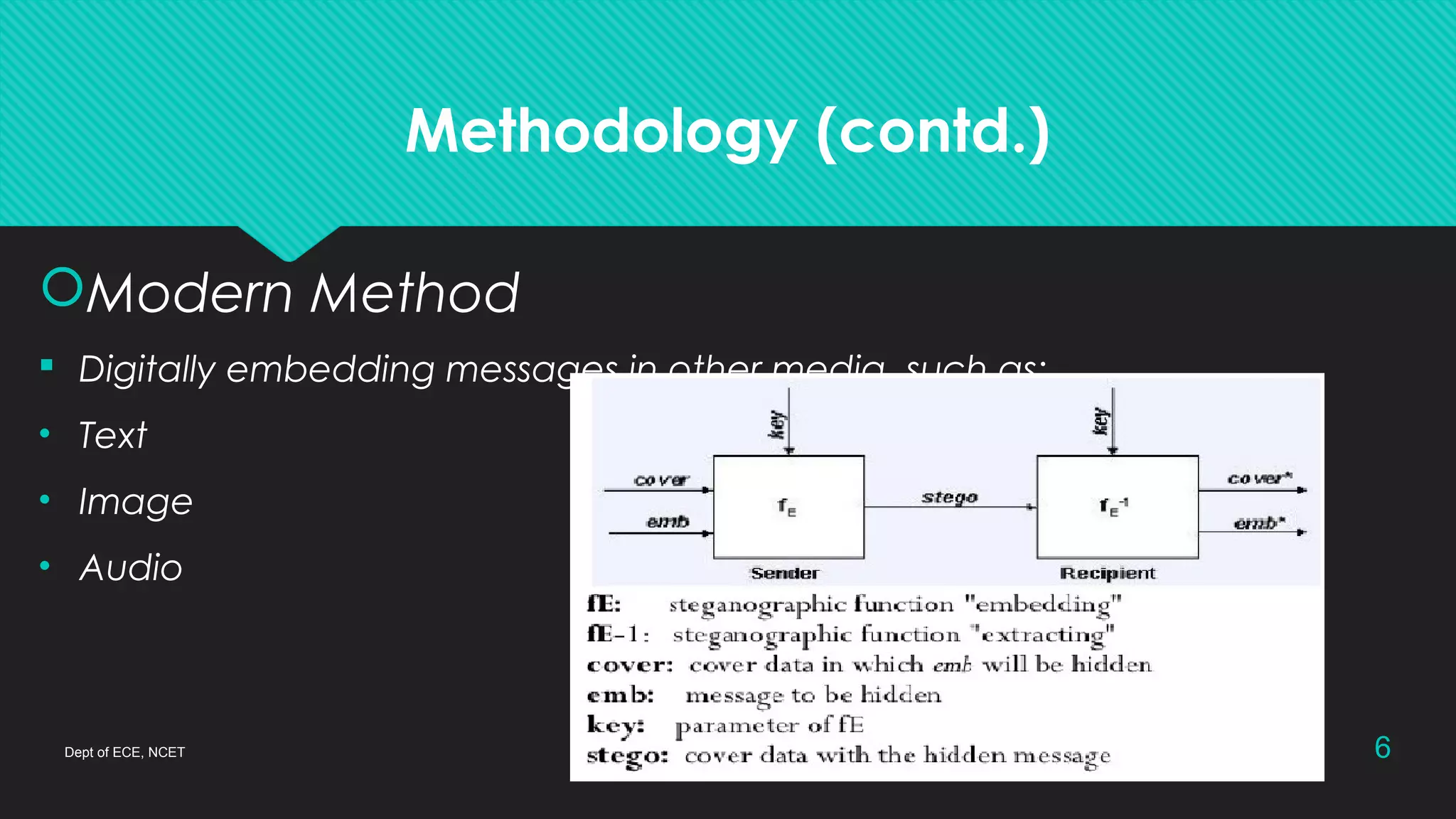
This document discusses steganography, which is the practice of concealing a secret message within another message or file. Modern steganography methods digitally embed messages in text, images, or audio files. The document explains how the least significant bit method works to hide messages in image and audio files by replacing the least significant bits of bytes with message bits. While steganography provides secure communication, it also has the drawbacks of increasing data size and requiring a complex encoding process.


![Image Steganography
Dept of ECE, NCET 8
Using LSB [Least Significant Bit] Method
Replaces least significant bits with the message to be
encoded
Most popular technique when dealing with images
It is best to use images with “noisy areas” – areas with
ample/enough color variation and without large areas of
solid color](https://image.slidesharecdn.com/steganographyslide-140403064347-phpapp02/75/Steganography-Presented-By-Prajwal-Shrestha-8-2048.jpg)

![LSB Insertion’s Example
Dept of ECE, NCET 10
An image may have the following three pixels (9 bytes) in it somewhere:
(01010010, 10010110, 10100100)
(10110100, 10010001, 01001110)
(10110110, 00101110, 11010001)
If we wanted to hide [131 or 10000011], we would use/replace the least-
significant bits of each byte:
(01010011, 10010110, 10100100)
(10110100, 10010000, 01001110)
(10110111, 00101111, 11010001)](https://image.slidesharecdn.com/steganographyslide-140403064347-phpapp02/75/Steganography-Presented-By-Prajwal-Shrestha-10-2048.jpg)